The document analyzes the 2014 eBay cyberattack, where 145 million user accounts were compromised due to a breach by threat actors. It discusses various concepts of computer security, such as the CIA triad, cryptography, authentication methods, and network security, emphasizing the importance of robust security measures to prevent future attacks. Recommendations for improving security infrastructure and practices are also provided to help organizations combat cyber threats effectively.













![When the webserver and database server are installed in the demilitarized zones zone, then
chances of hackers gaining access to the databases is high. Therefore, separating servers with
different roles is crucial i.e webserver and database server should be separated. This will improve
the security of an organization’s web farm and limits the extent of damage in case of an attack.
The principle of least privilege is another security concept that should be adopted by IT
professionals working in organizations. This simply means that the webserver should have the
least possible privilege to access databases. In addition, it should not be granted administrative
rights to invoke changes to the databases structure e.g the drop table. This will go along way in
limiting the damage in case servers are compromised by an attack.
Limiting remote access is also another security concept that should be adopted by organizations
to protect all their server in the web farm. This means that webservers and database servers
should only be accessed locally from local area networks; admin interfaces must not be accessed
from the internet. Therefore, if remote access id unavoidable, a well-documented handful number
of IP addresses can be granted access to these administrative interfaces. This can be achieved
using whitelisting from the firewall. The other method remote access can be secure is by
employing the use of cryptographically secure mechanisms such as SSH or use virtual private
network. In a nutshell there are many security measures that can be employed by organizations to
protect their systems and other internal assets.
REFERENCES
1. Aggarwal, P., Arora, P., & Ghai, R. (2014). Review on cybercrime and
security. International Journal of Research in Engineering and Applied Sciences, 2(1),
48-51.
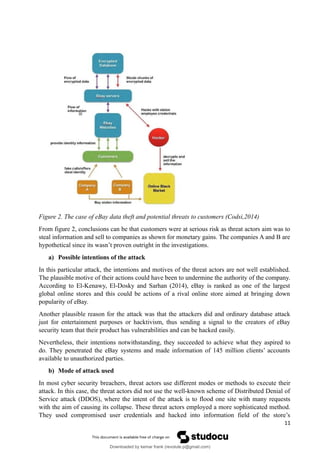
2. The case of eBay data theft and potential threat to customers [Image]. (2014). Web.
3. The damage that the Heartbleed bug caused [Image]. (2014). Web.
16
Downloaded by kemar frank (revolute.p@gmail.com)
lOMoARcPSD|1449381](https://image.slidesharecdn.com/casestudy-240210174750-61b3e16c/85/Case-Study-pdf-17-320.jpg)
![4. Gujrathi, S. (2014). Heartbleed bug: An OpenSSL heartbeat vulnerability. International
Journal of Computer Science and Engineering, 2(5), 61-64.
5. El-Kenawy, E. S. M. T., El-Desoky, A. I., & Sarhan, A. M. (2014). Bidder strategy system
for online auctions trust measurement. International Journal of Computer Science Issues
(IJCSI), 11(5), 76-82.
6. How hackers hack PayPal account in 2017 – Hack PayPal. (2017). Web.
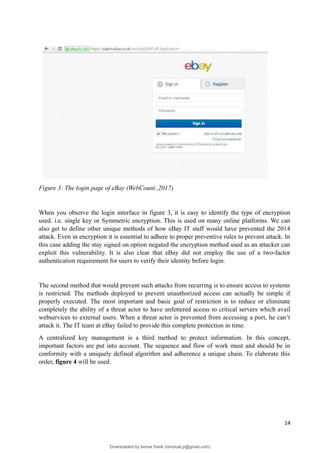
7. The login page of eBay [Image]. (2017). Web.
8. Meyer, C. (2017). Submitted to the Department of technology systems. Web.
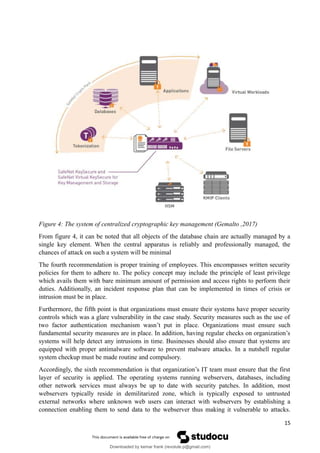
The system of centralized cryptographic key management [Image]. Web.
9. Sahib, S. (2015) Cyber terrorism: Policy and technical perspective. Melaka: Penerbit
University Teknikal Melaysia Melaka.
10. Andrade, R. et al. (2021) “Extending a trust model for energy trading with cyber-attack
detection,” Electronics, 10(16), p. 1975.
11. Butler, R. (2007) “A framework of anti‐phishing measures aimed at protecting
the online consumer’s identity,” Electronic library, 25(5), pp. 517–533.
12. Byrne, D. J. (2015) “Cyber-attack methods, why they work on us, and what to
do,” in AIAA SPACE 2015 Conference and Exposition. Reston, Virginia:
American Institute of Aeronautics and Astronautics.
17
Downloaded by kemar frank (revolute.p@gmail.com)
lOMoARcPSD|1449381](https://image.slidesharecdn.com/casestudy-240210174750-61b3e16c/85/Case-Study-pdf-18-320.jpg)