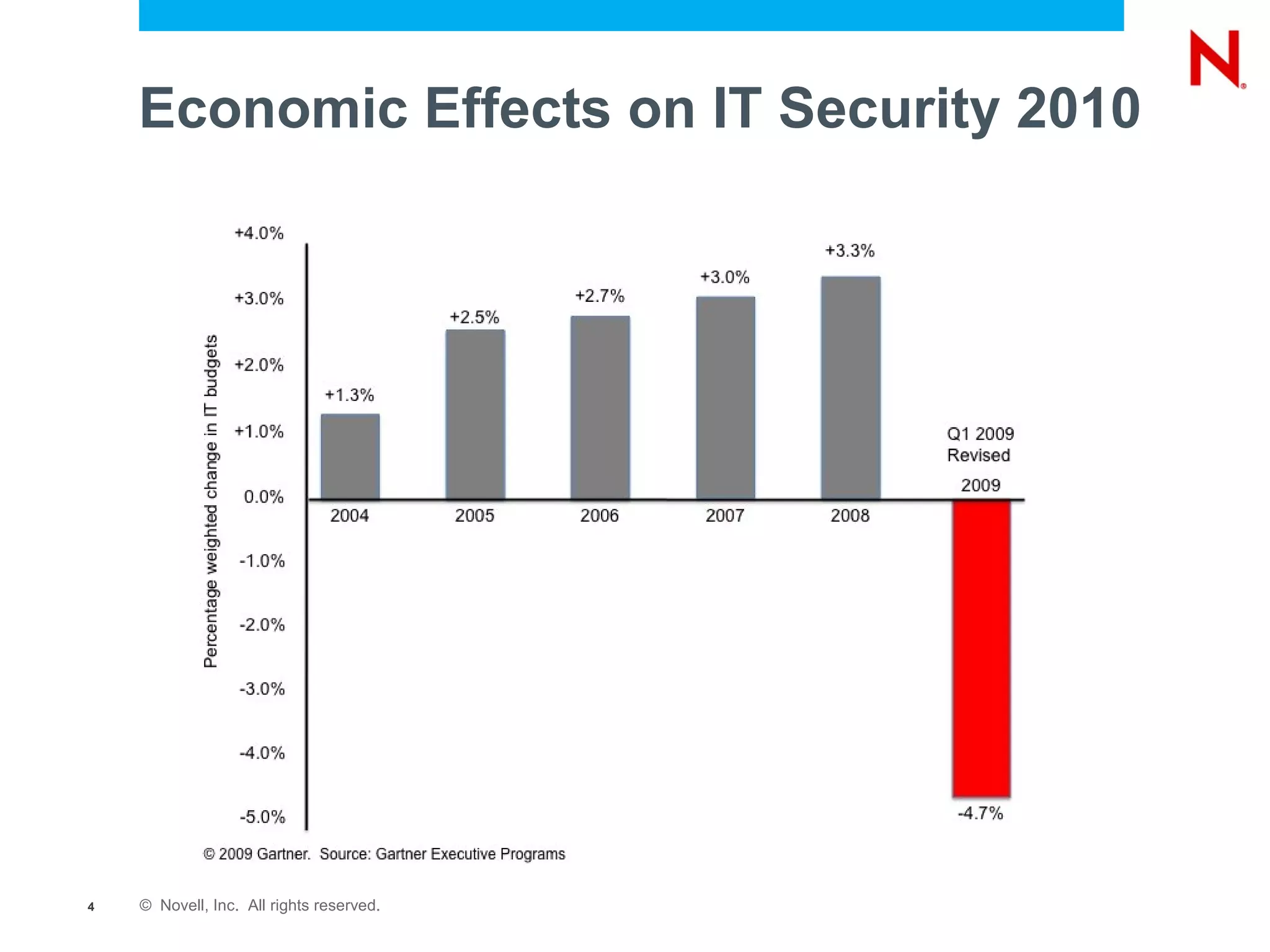
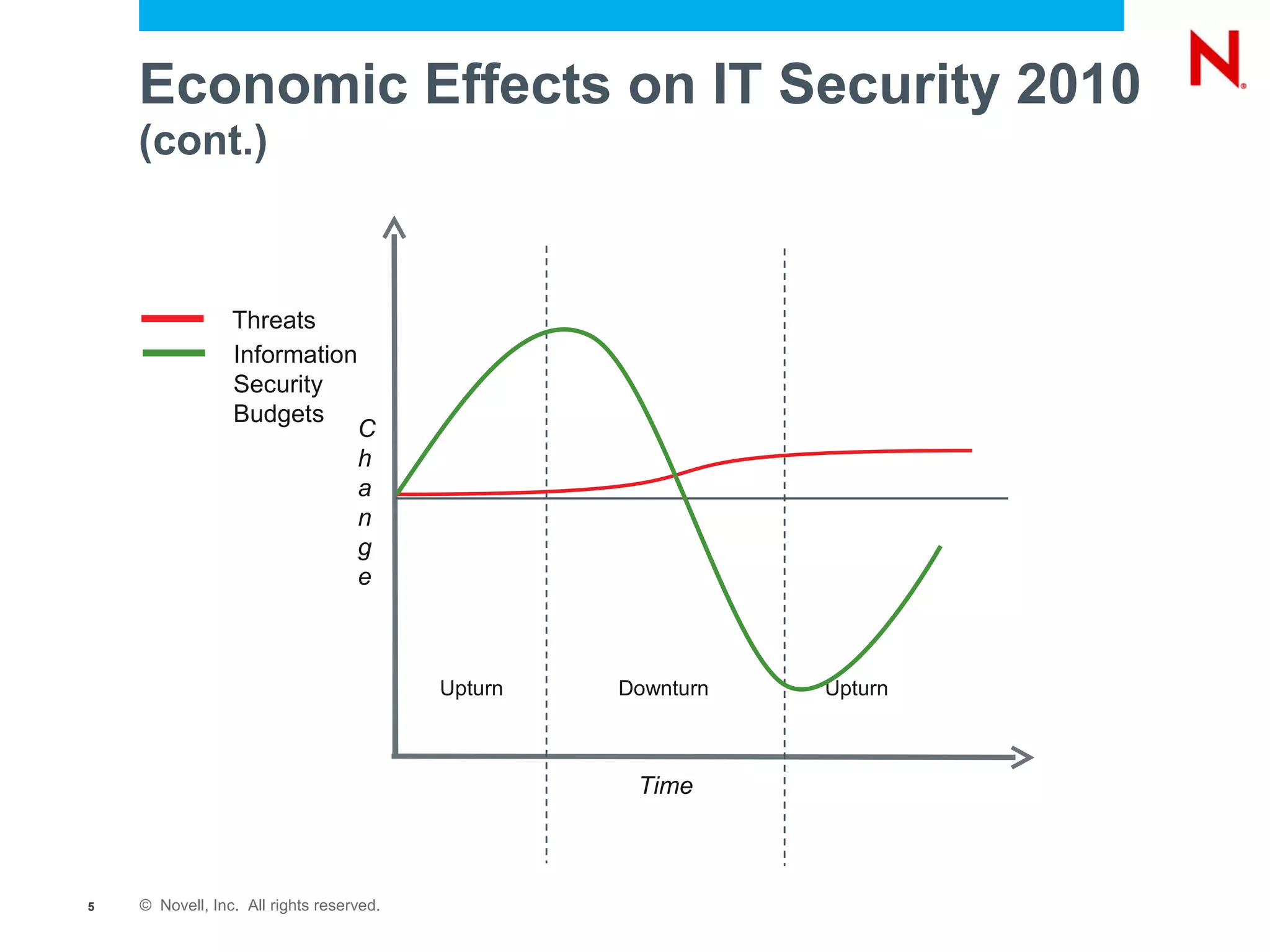
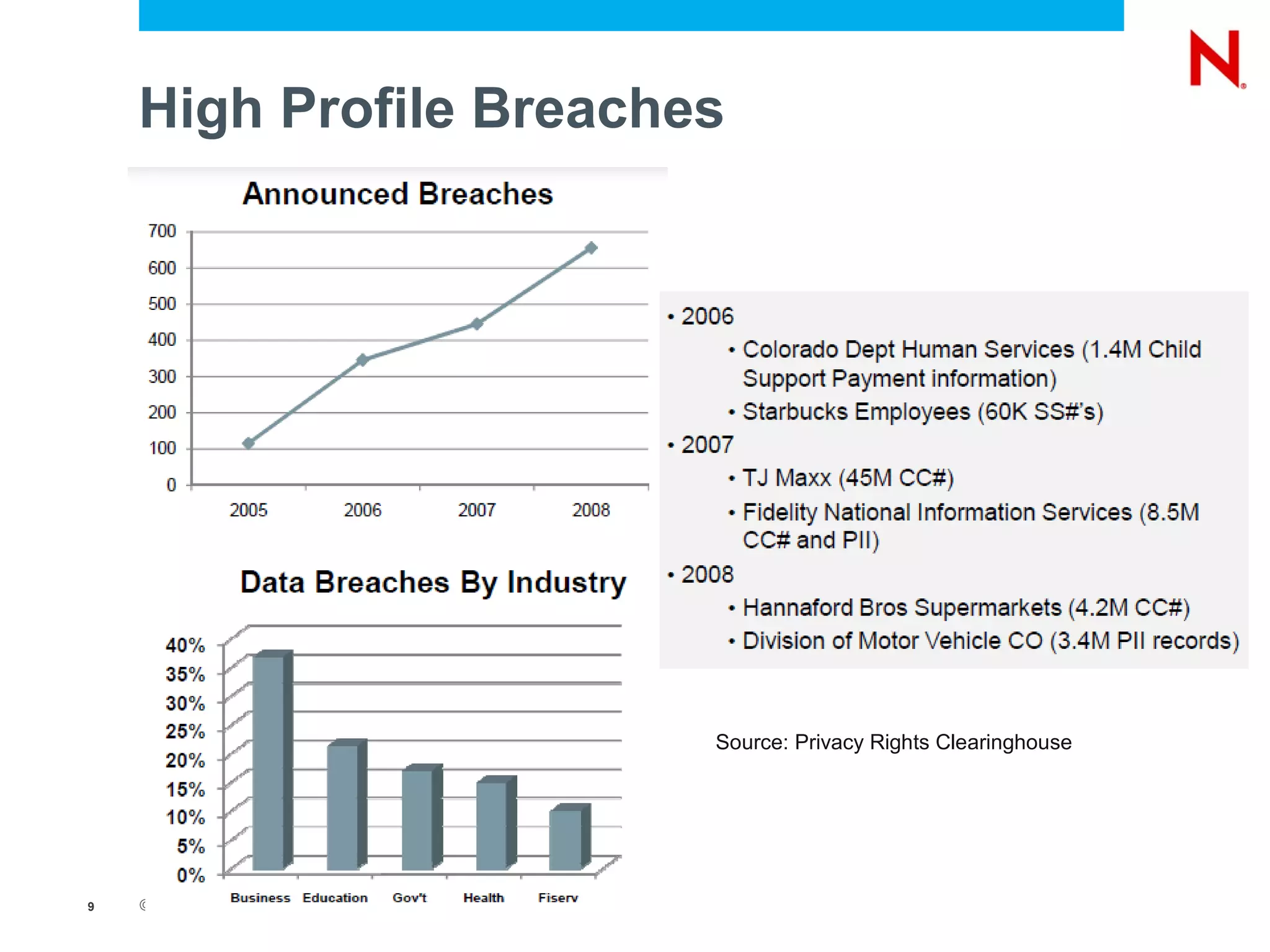
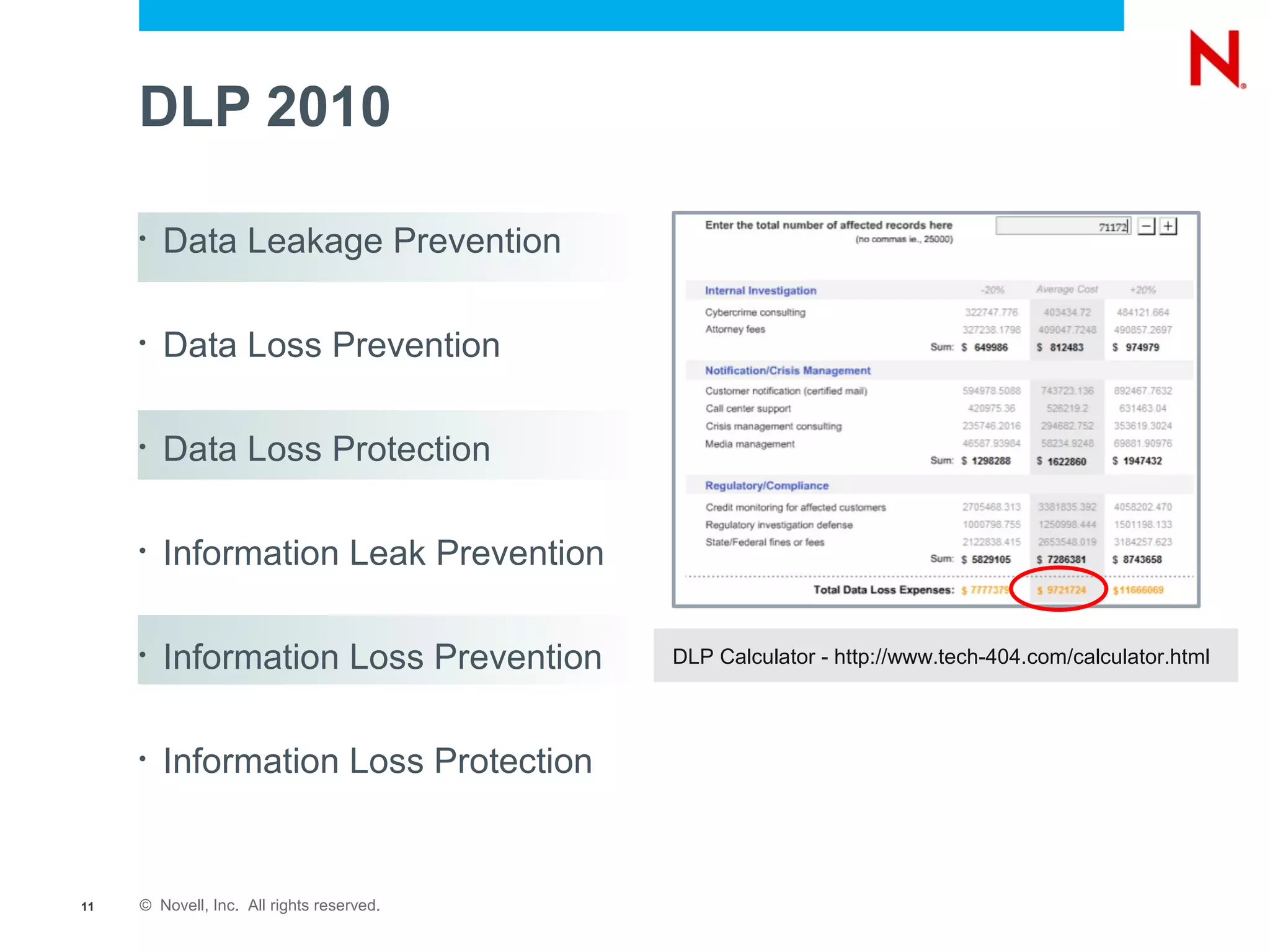
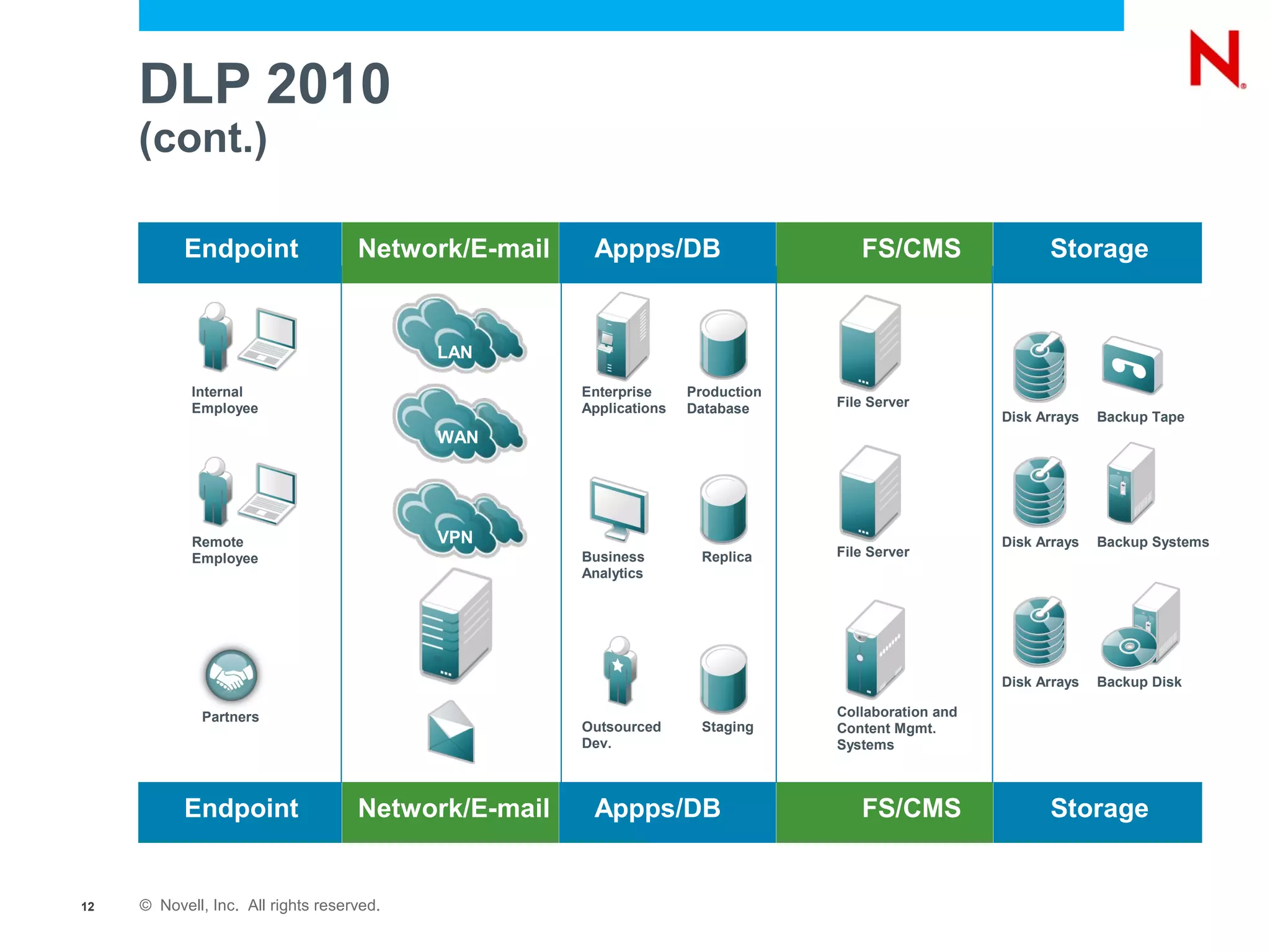
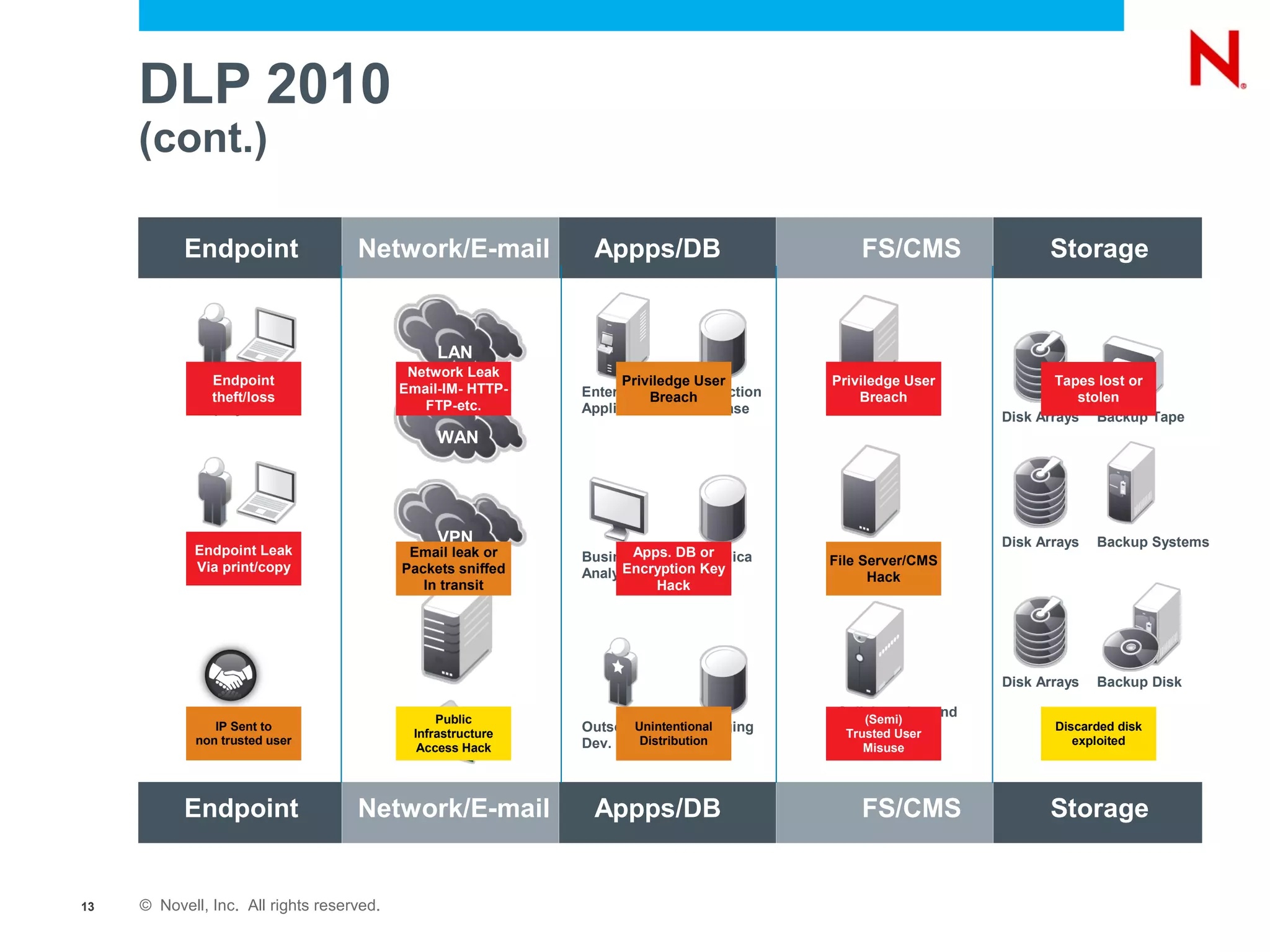
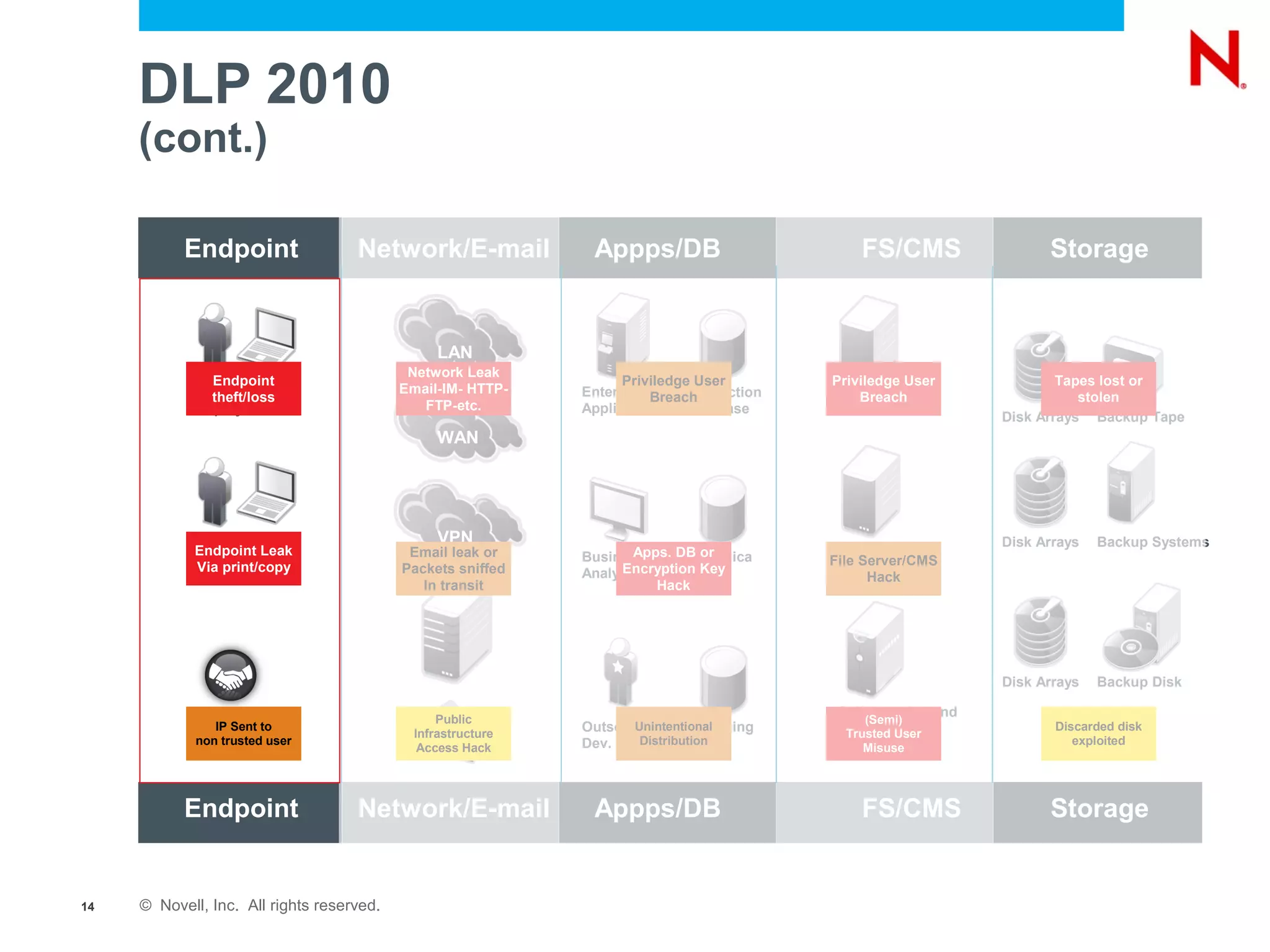
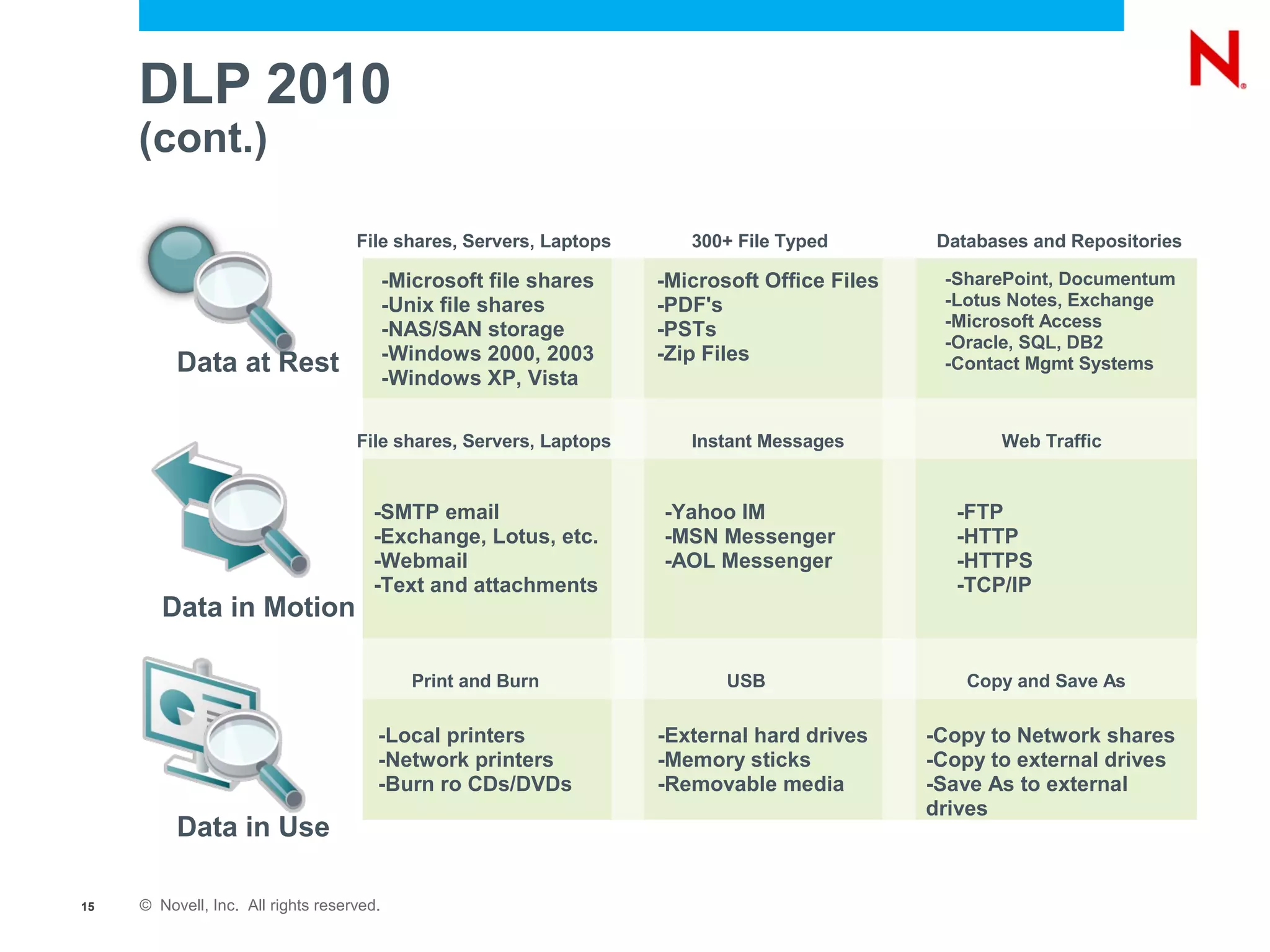
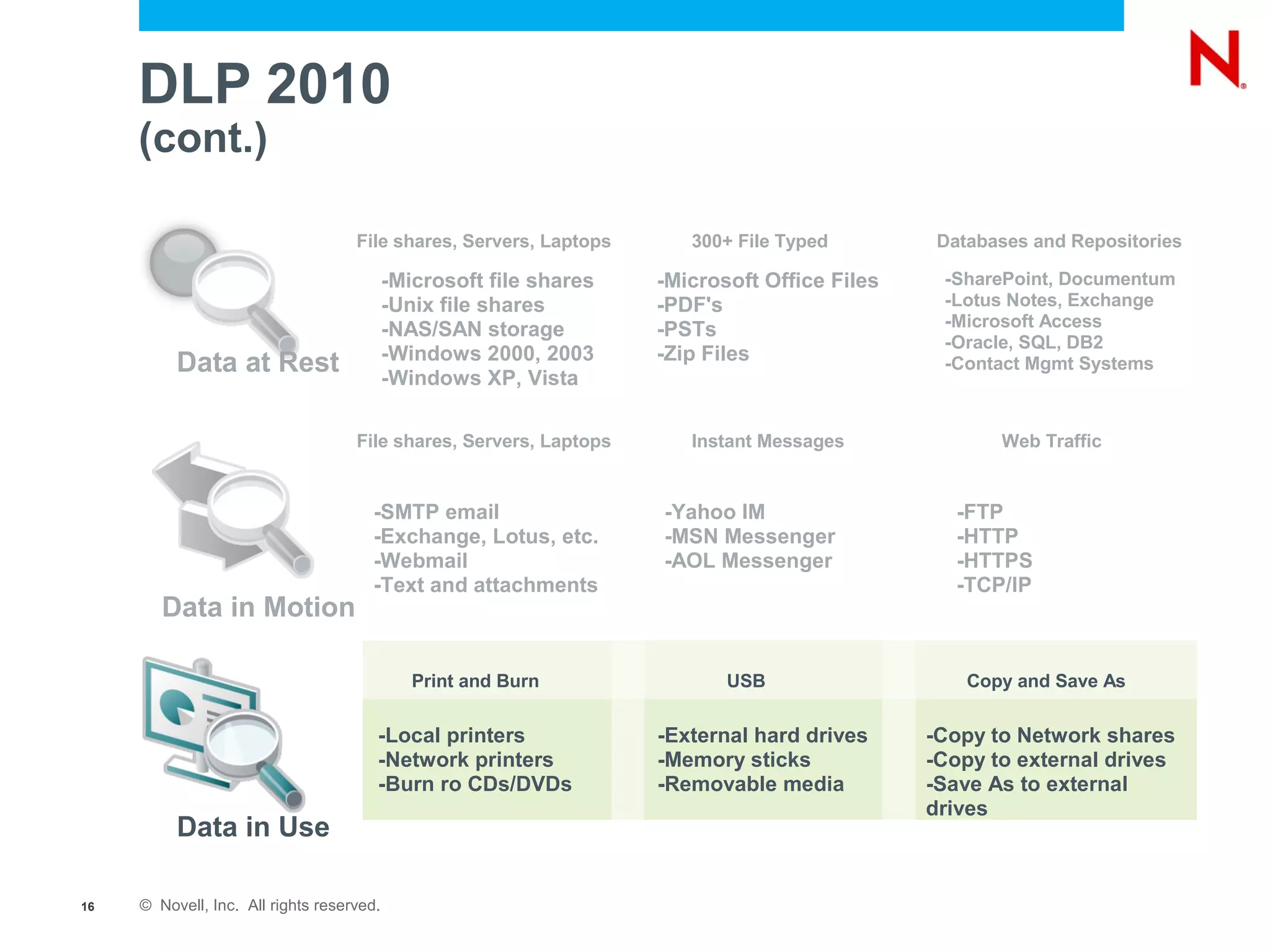
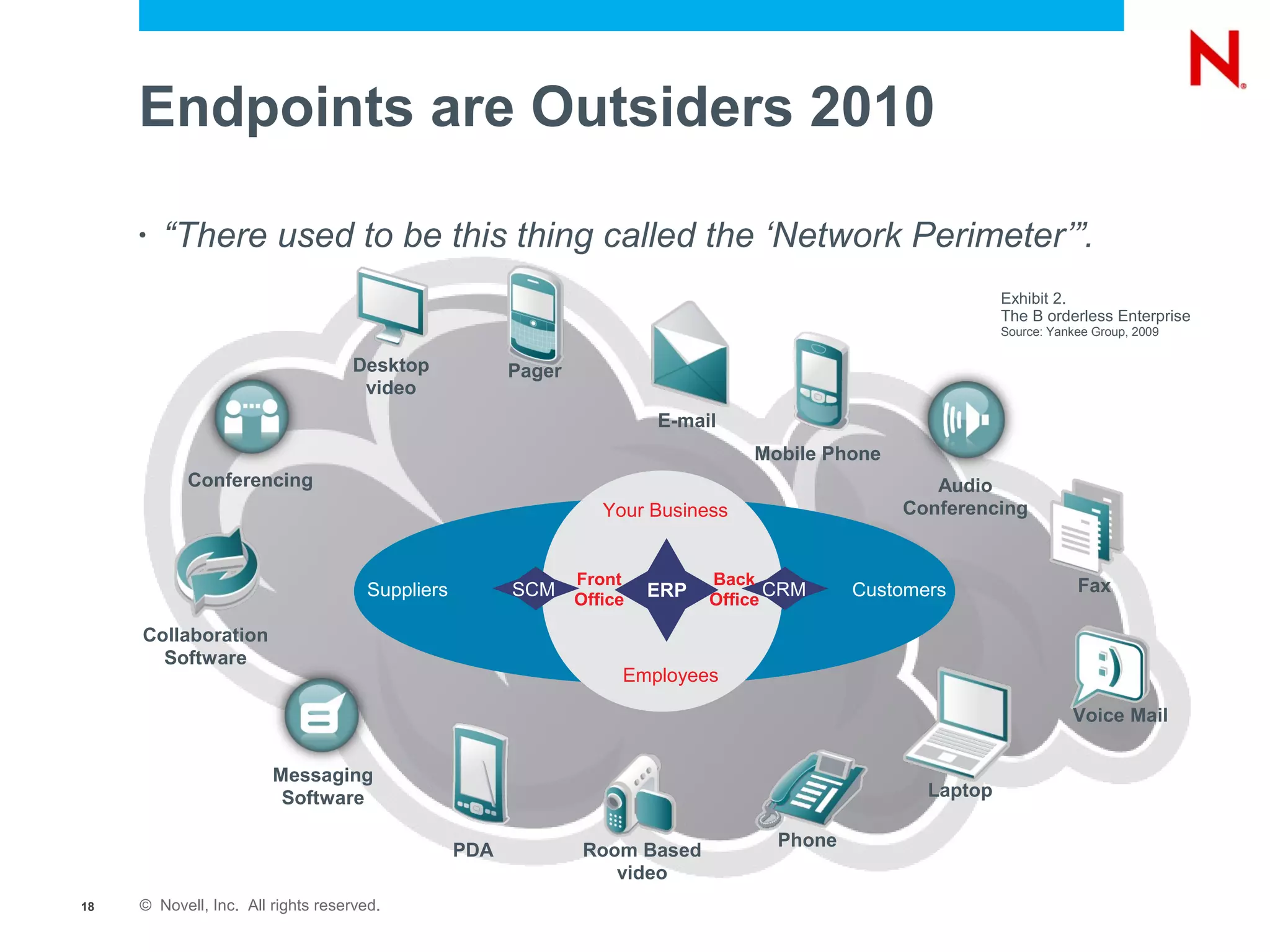
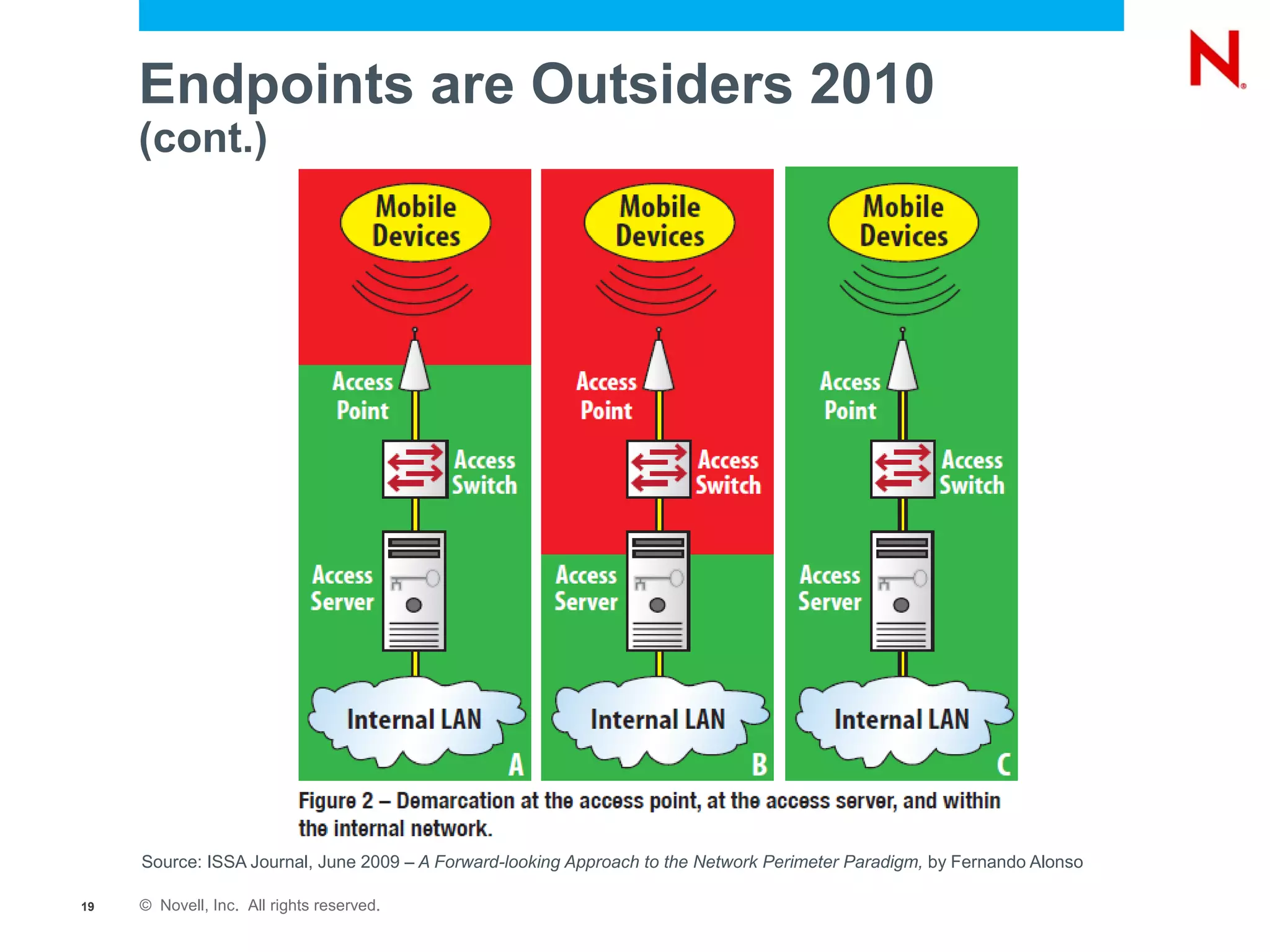
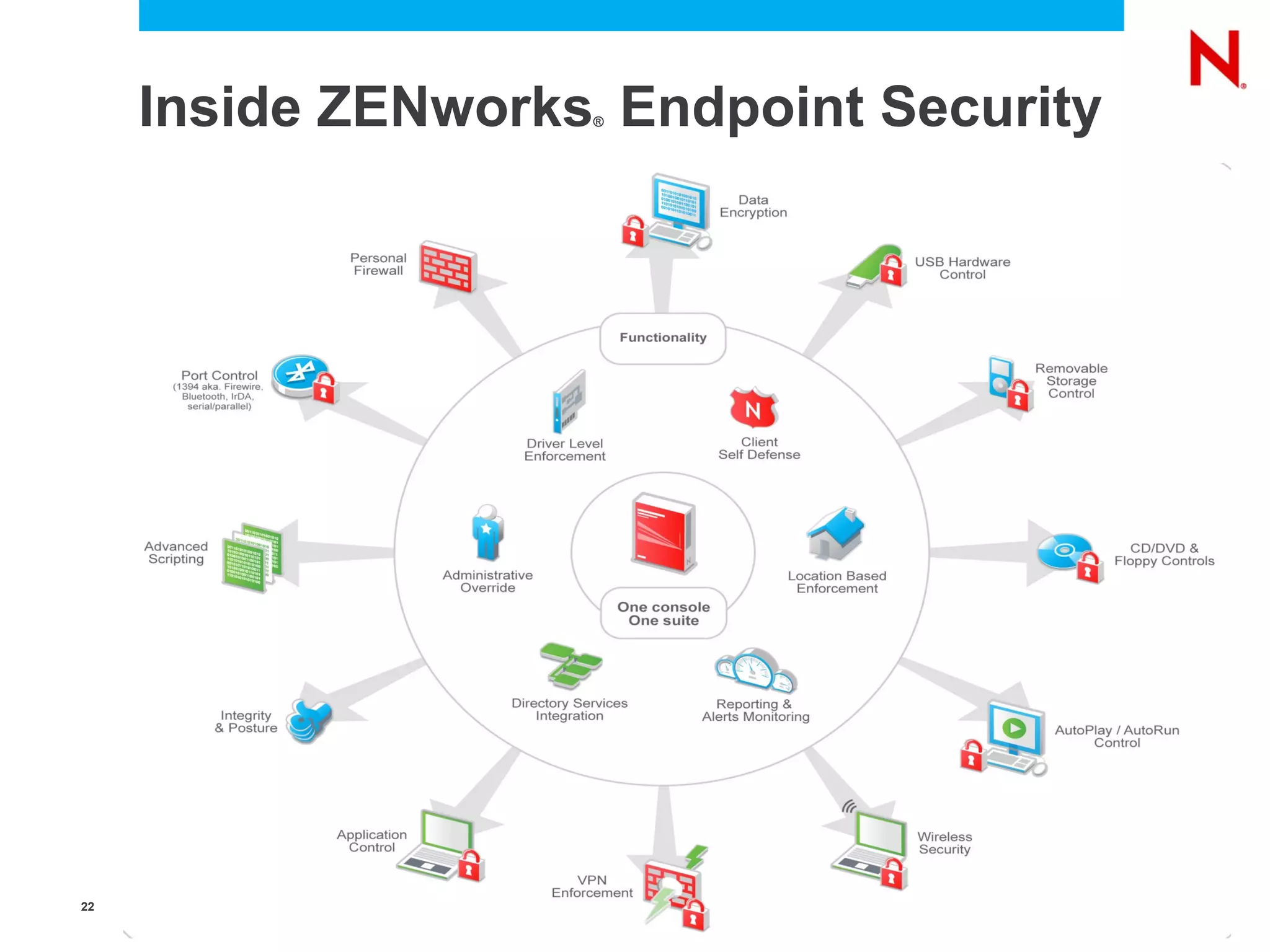
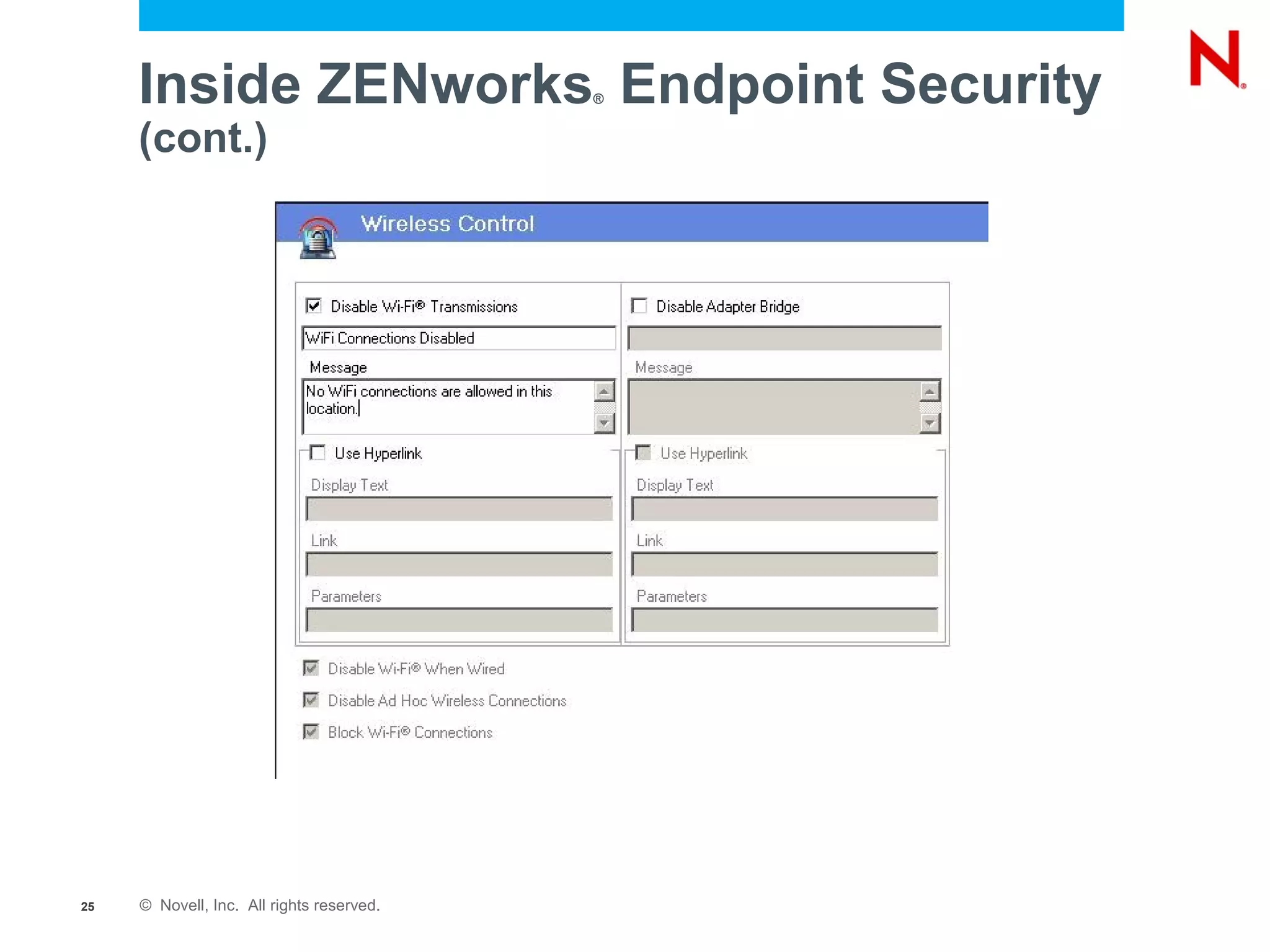
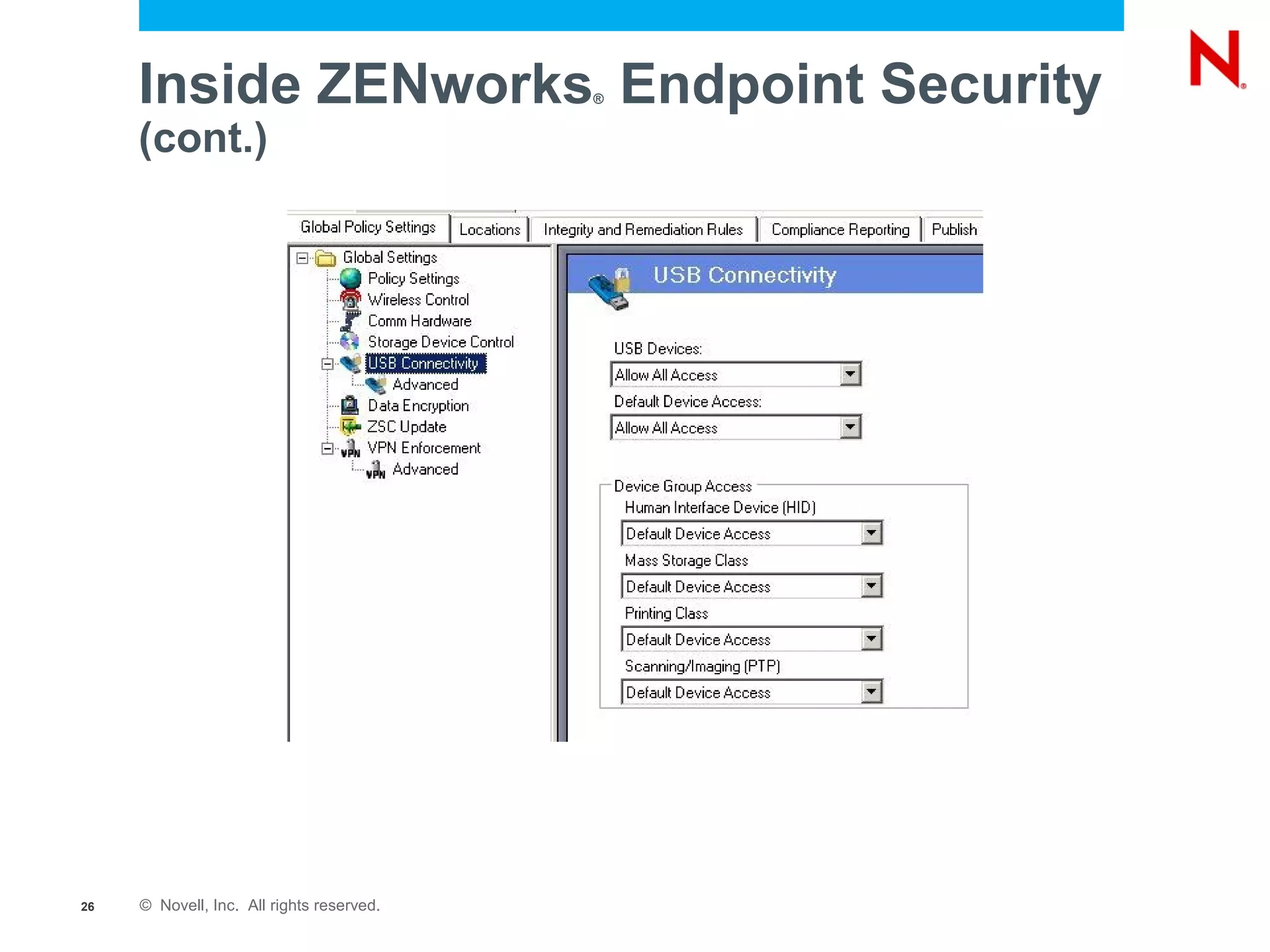
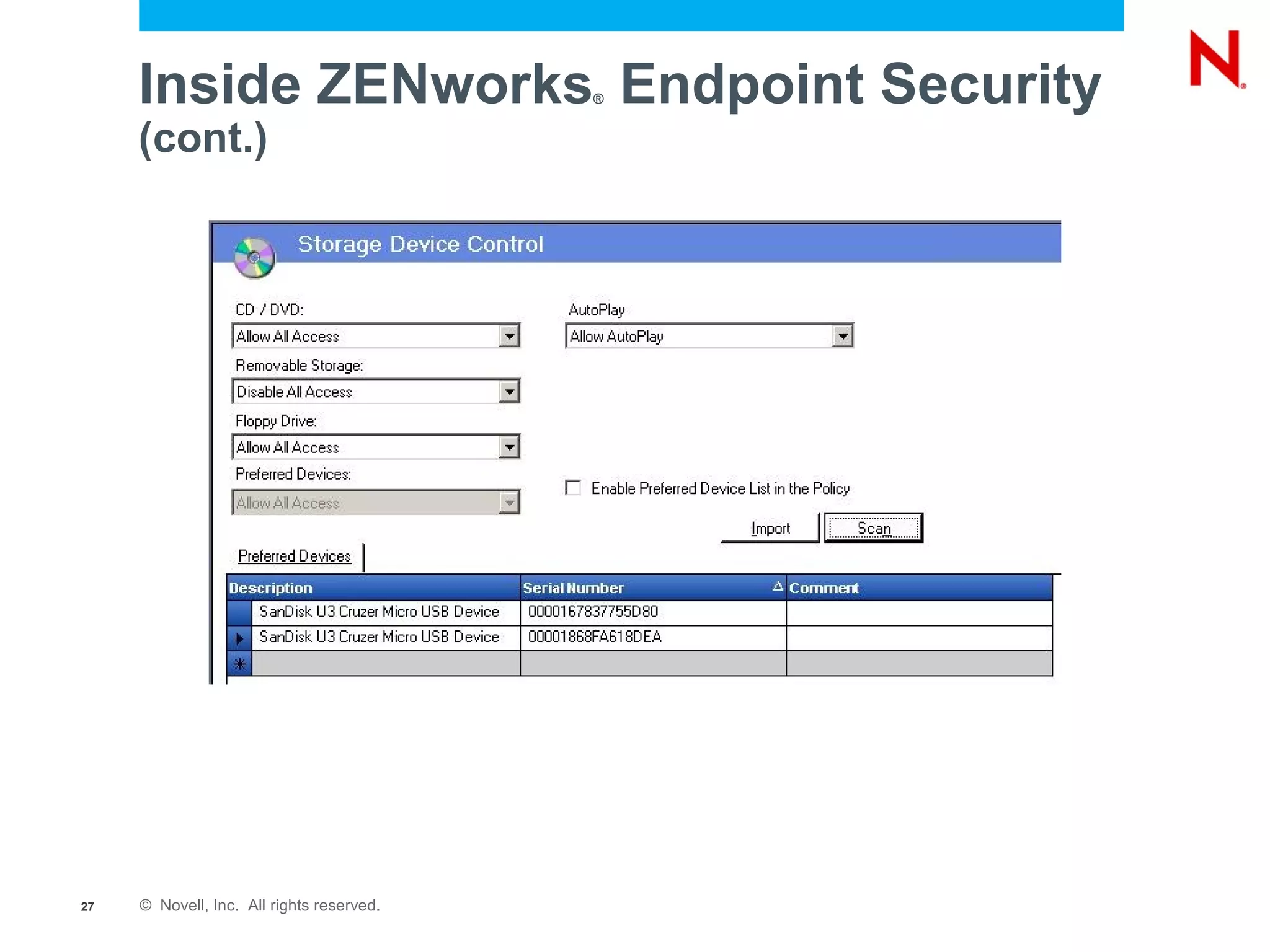
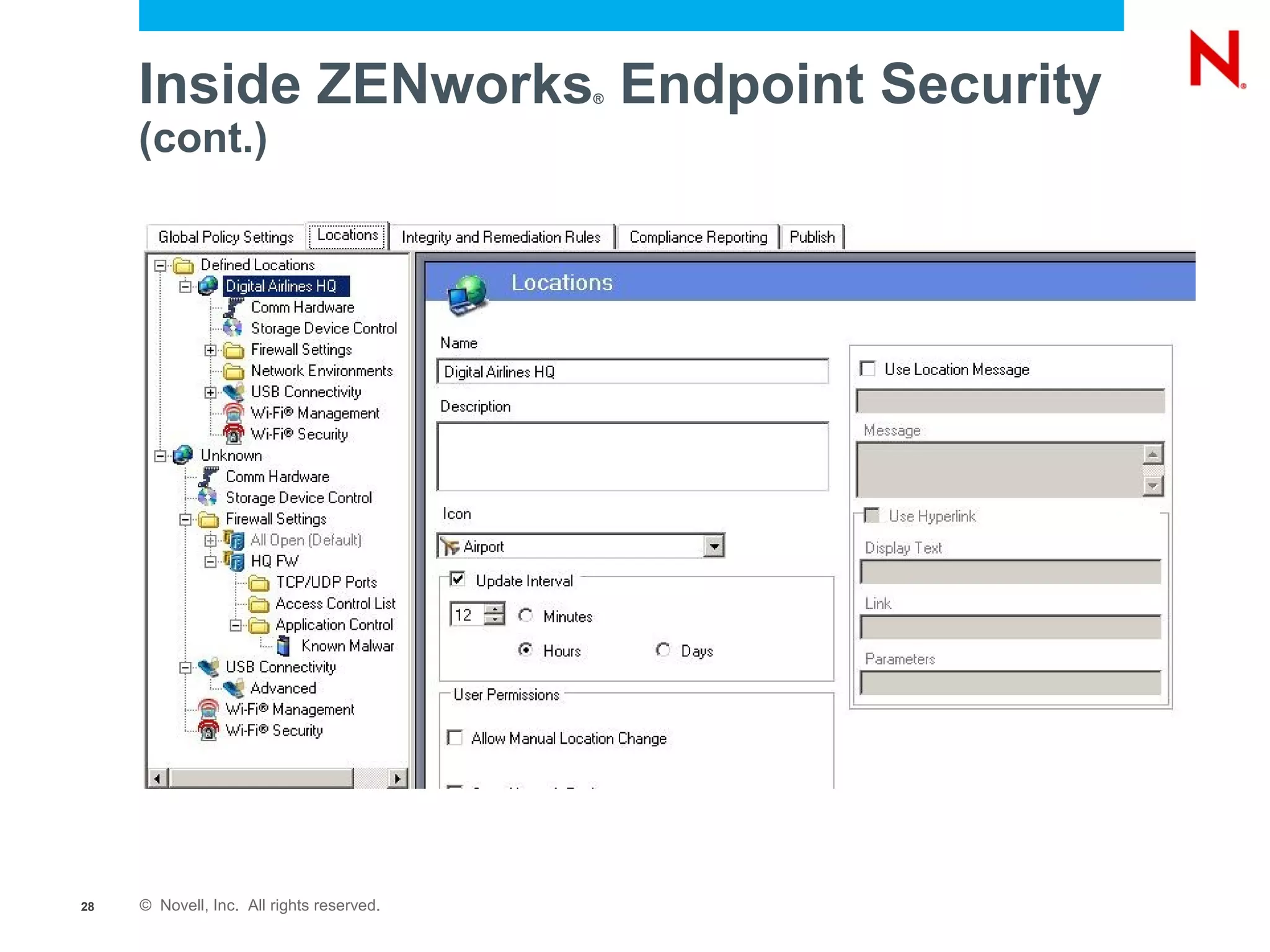
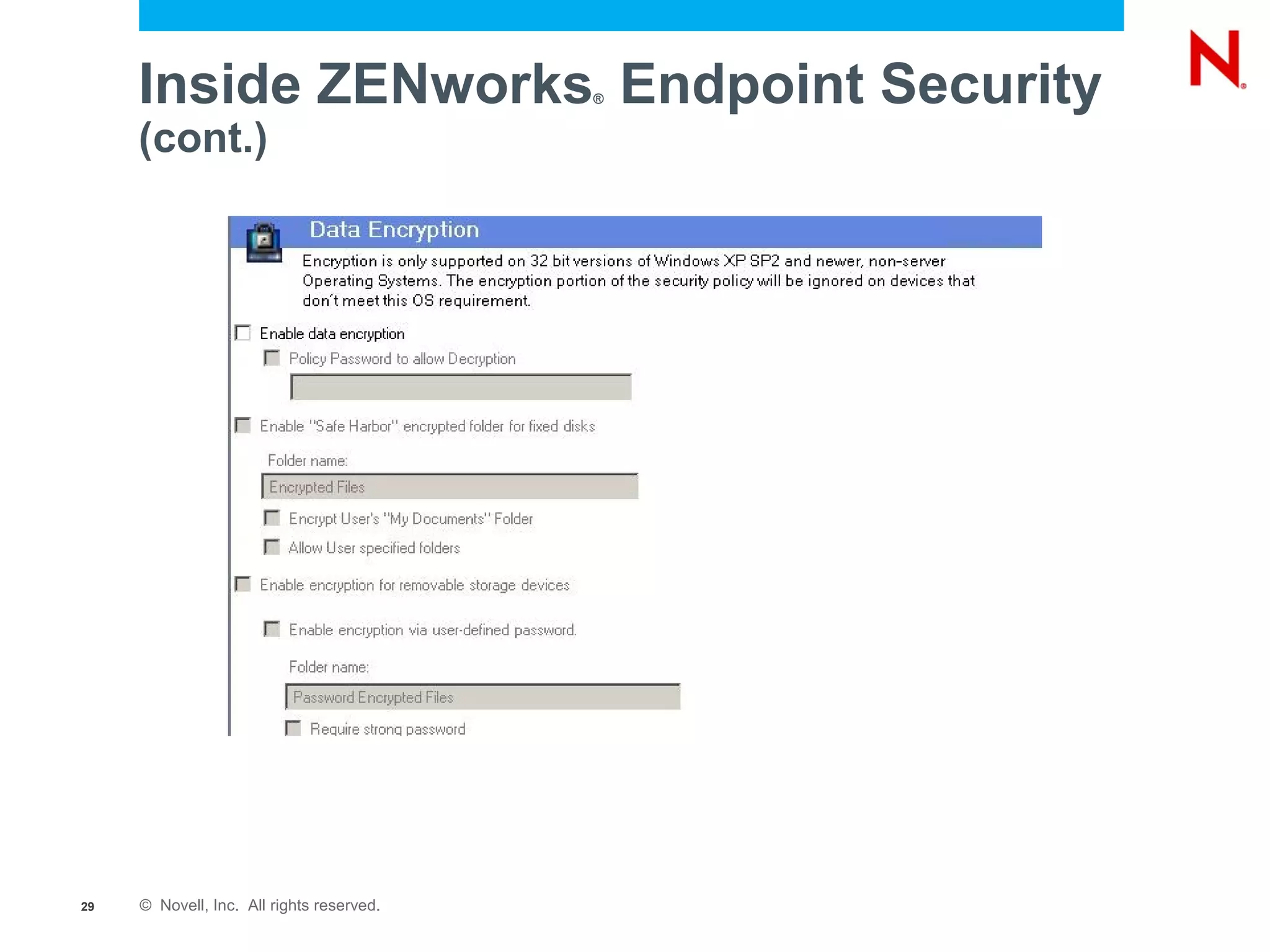
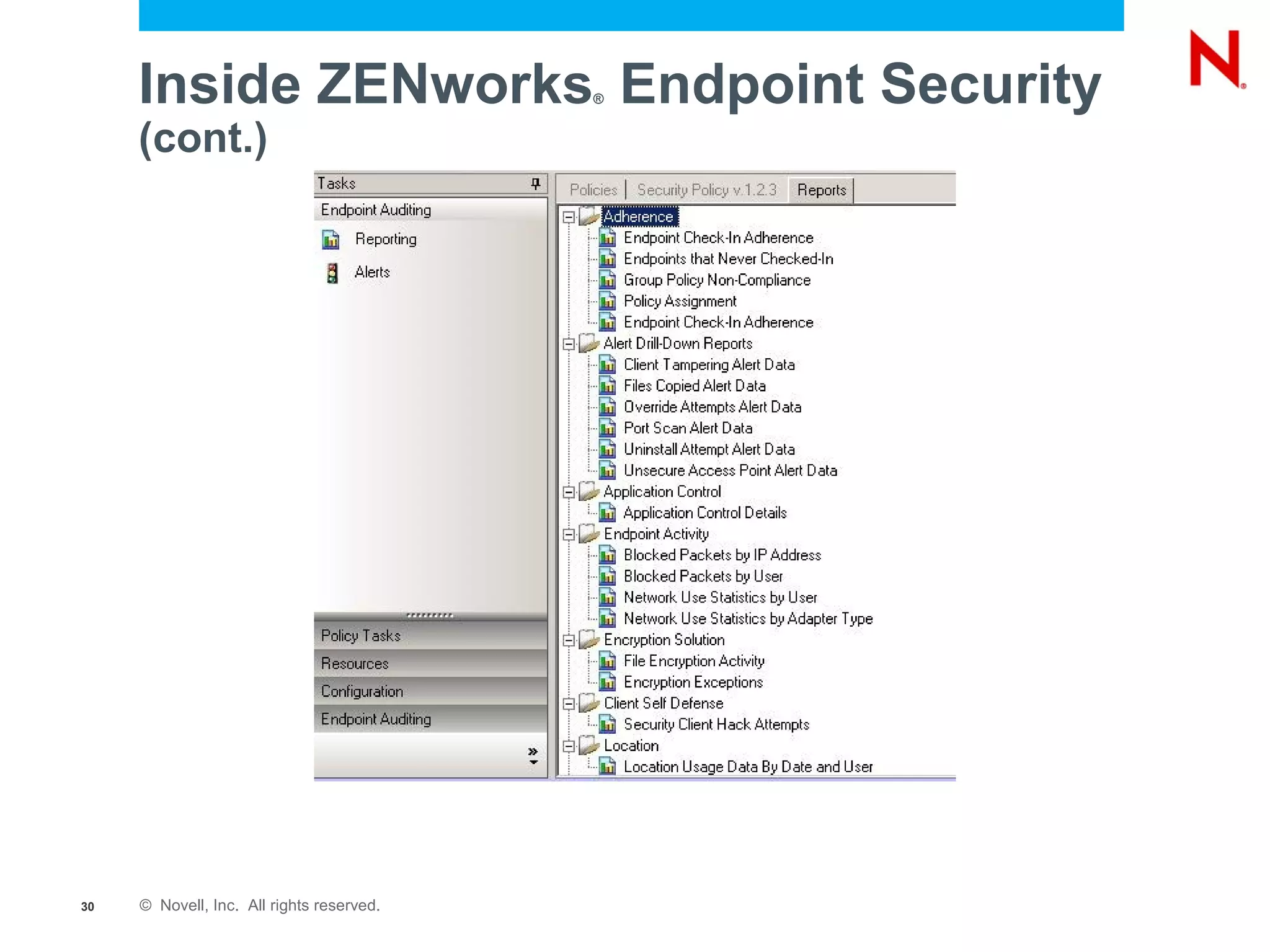
The document discusses securing endpoints using Novell Zenworks Endpoint Security Management, highlighting economic impacts on security, compliance with regulations like PCI and ISO 27002, and threats from data breaches. It emphasizes the importance of data loss prevention strategies and the challenges posed by the evolving nature of endpoints as external threats. The presentation includes a demonstration of Zenworks' security features and an invitation for questions and further discussion.