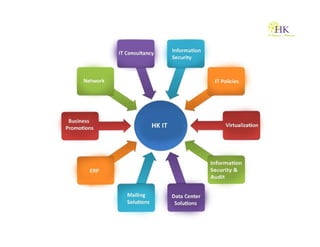
This document profiles an IT solutions company called HK IT Solution that provides optimized and secure IT infrastructure solutions. It offers a wide range of IT consultancy services including data management, network design, security services, and cloud/virtualization solutions. The company was founded with a goal of advising clients correctly from an application standpoint to optimize investment returns. It has experience working with a range of clients in India and overseas.