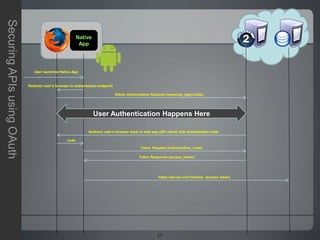
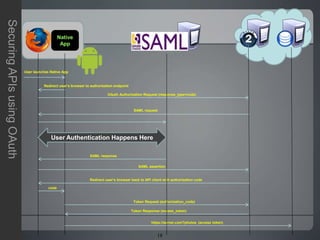
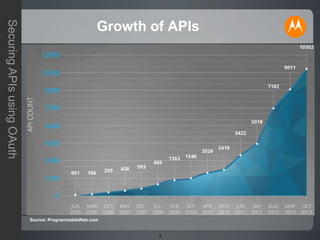
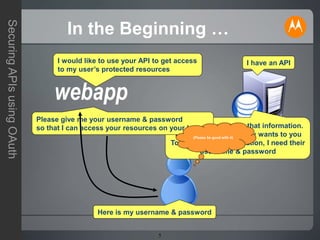
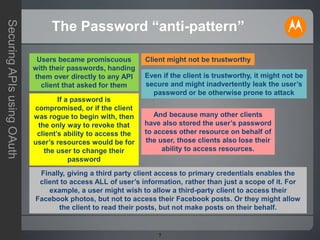
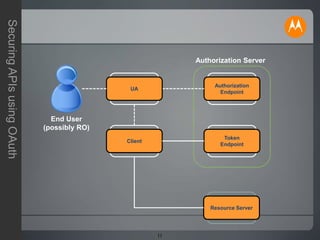
The document discusses securing APIs using OAuth 2.0. It begins by describing some of the issues with early methods of API access that involved directly sharing usernames and passwords. It then provides an overview of how OAuth addresses these issues by allowing users to authorize API clients to access specific resources without sharing credentials. The key stages of the OAuth authorization code and token flows are described, including how tokens are used to make API requests. The document also covers some additional OAuth topics like JSON Web Tokens, other grant types, and some limitations and challenges with OAuth. In closing, it invites any questions or comments.







![16
SecuringAPIsusingOAuth
JSON Web Tokens
{
"alg": "RS256",
"x5t": "eZsobkgyfNGOyVpjEHgS2i8QhKQ"
}.
{
"Username": “alice@domain.com",
"exp": 1432744471,
"scope": [
“calendar_api.read_only“,
“contacts.read_only”,
“email.all”
],
"client_id": "s6BhdRkqt3"
}.
U4cL9RFKu_CwdqlpGReAVGA5sxw8d8tLXM4_1Cx7l49KQxeHYkV2ARlv6Qo7sdUSv7k50yhNPR80wFx0WqqtoLY
AKSJ2sXhfqbVTEZrUdDFZUVVYeKOWEyZzZD1w3NCqRm6xhLWmOu05A4gLDUuC7jWagMYquZPywW06SFX
FTa5MN0Nyol3V-QfrFf-XdXTBBUko00ooQf6SsyTcAP08kLuWIl9M2oRLPF_N_f5j1I4oAk5LUMFhdNyGeQ32K-
aU_kLoGxzb20eUlsZVO82zm-94tEdeKZWtp6BtwLICc9wvR1DnMJje7O_dOql1L1DYXNrJ0s7rWRlLwAxthbytww](https://image.slidesharecdn.com/85ea70bb-03b7-4bfd-82c3-c82400e2a9b4-150527191452-lva1-app6891/85/Securing-APIs-using-OAuth-2-0-16-320.jpg)