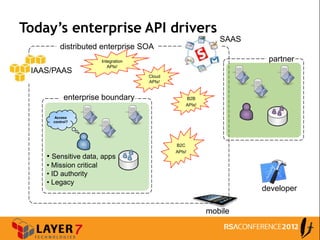
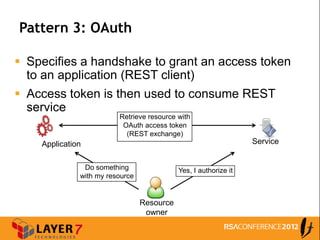
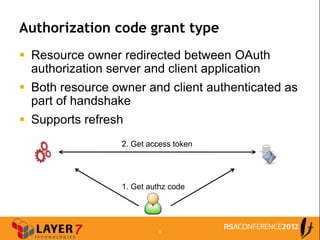
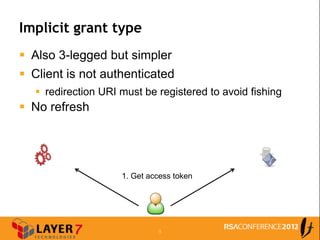
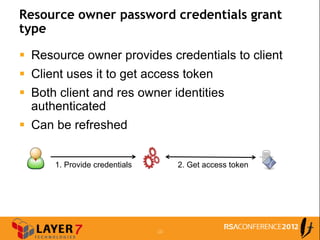
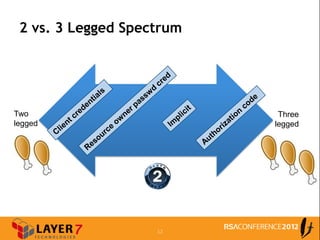
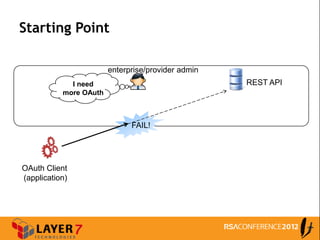
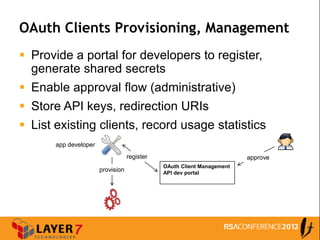
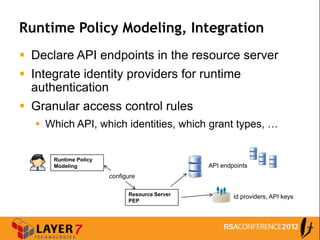
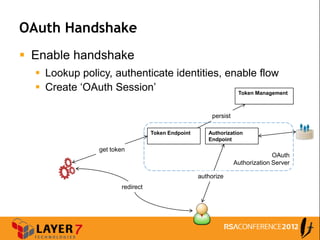
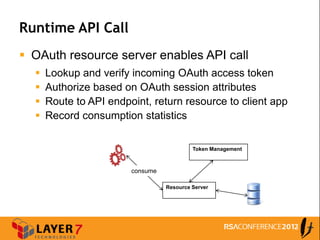
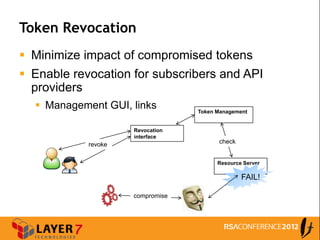
The document discusses enterprise access control patterns for REST and web APIs, highlighting the need for secure authentication and authorization mechanisms. It outlines three primary patterns: API keys in URI parameters, HMAC signatures, and OAuth 2.0, detailing their advantages and use cases. The piece emphasizes the importance of a comprehensive API access control infrastructure, incorporating token management and developer portals.