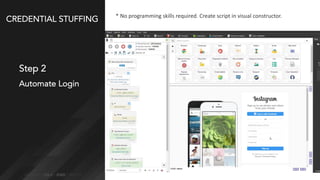
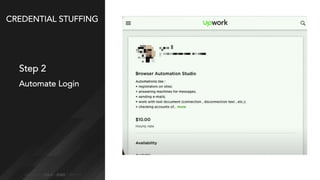
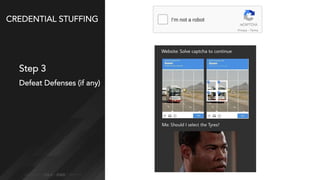
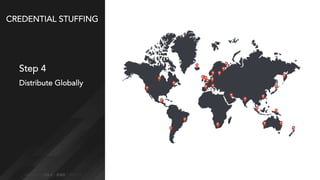
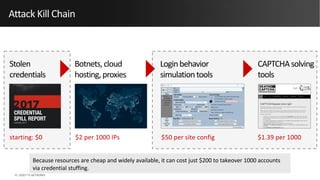
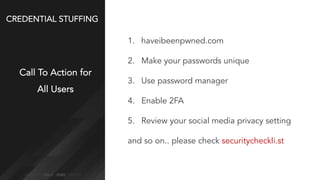
Credential stuffing involves using breached username and password pairs from one site to attempt to log in to other sites where users may have reused passwords. It occurs in four main steps: 1) obtaining credentials from data breaches, 2) automating the login process without human interaction, 3) defeating any login defenses, and 4) distributing the process globally through botnets and cloud hosting. While two-factor authentication prevents account takeovers, credential stuffing can still reveal valid user accounts. Users and organizations are encouraged to take steps like using unique passwords, password managers, and two-factor authentication to help mitigate credential stuffing risks.