Embed presentation
Download as PDF, PPTX




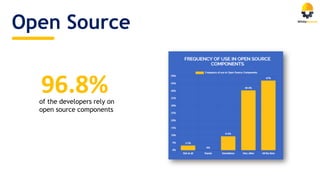


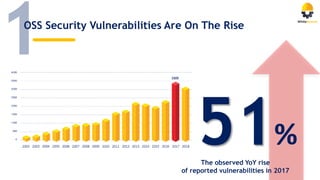






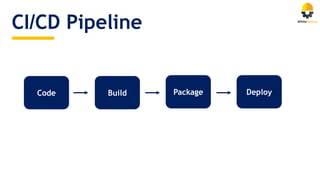
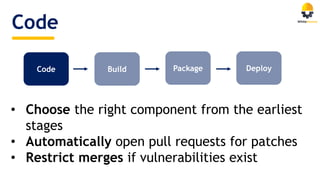
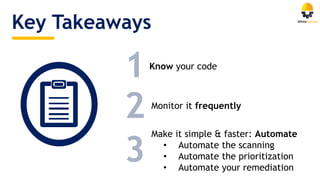


The document discusses the importance of managing open source security in DevOps, highlighting that 96.8% of developers use open source components. It emphasizes the rise in security vulnerabilities and the inefficient prioritization of fixes by companies. Key recommendations include automating scanning, prioritization, and remediation processes throughout the software development lifecycle.




















