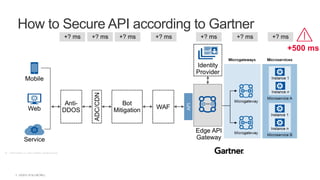
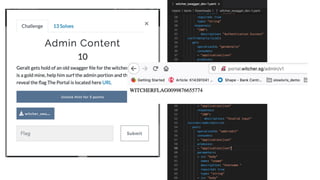
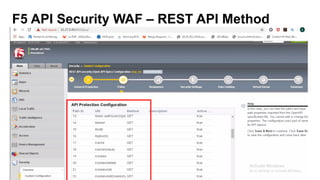
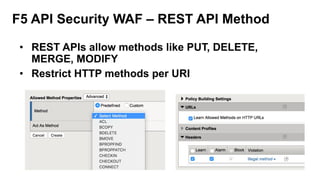
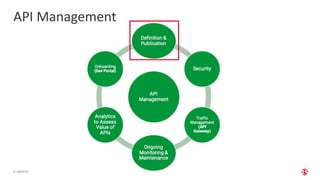
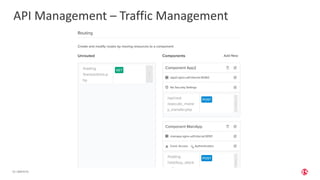
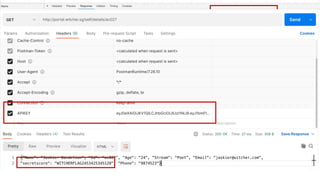
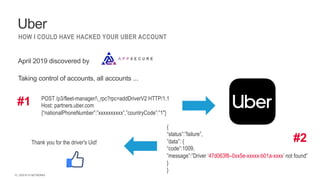
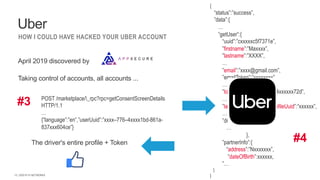
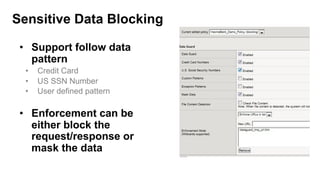
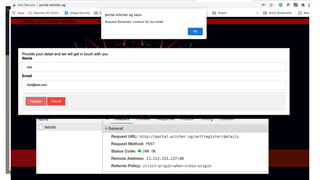
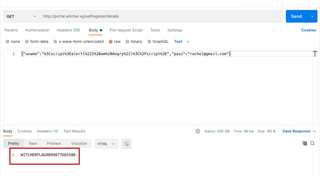
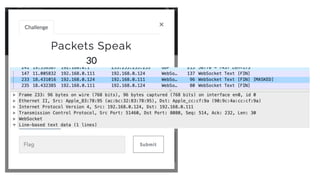
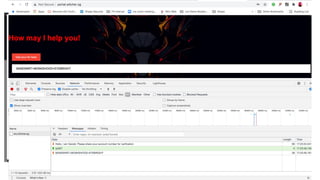
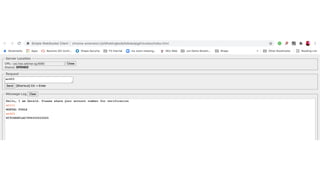
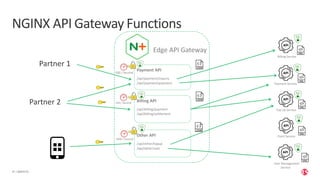
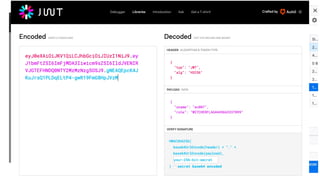
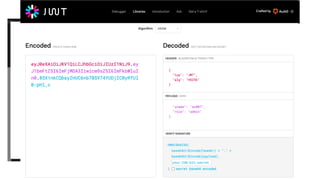
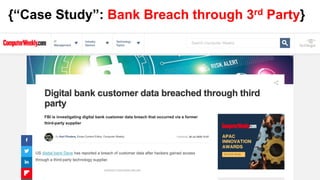
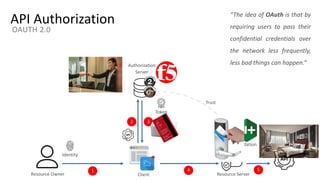
The document outlines the top API security challenges, including broken object level authorization, excessive data exposure, and security misconfiguration. It presents specific examples of vulnerabilities, such as a case involving Uber's API, and emphasizes the importance of proper authentication and authorization mechanisms. Additionally, it mentions strategies for securing APIs based on recommendations by industry experts.