Embed presentation
Download to read offline





















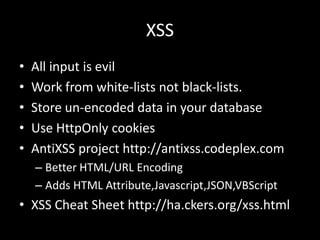




The document discusses the OWASP Top Ten Project, which focuses on improving application security. It provides an overview of the top 10 security risks, including failure to restrict URI access, insecure communications, insecure cryptographic storage, broken authentication/sessions, information leakage, cross-site request forgery, insecure direct object references, malicious file execution, injection flaws, and cross-site scripting. For each risk, it offers brief explanations and recommendations for mitigation.




























