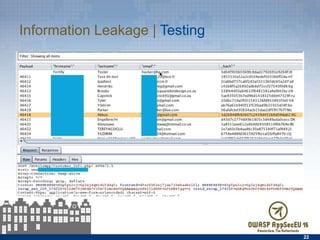
The document presents an API security assessment primer, outlining the importance of API security, common vulnerabilities, and effective assessment strategies. It emphasizes the need for comprehensive testing approaches and tools, as well as best practices to mitigate vulnerabilities like broken authentication, information leakage, and lack of access control. Additionally, it encourages developers to adopt an attacker mindset and provide resources for enhancing API security.