Secure Sharing PHI PCI PII -Android app_Content Provider
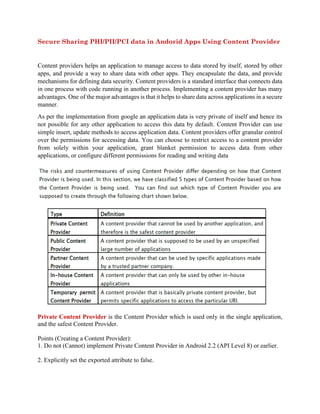
- 1. Secure Sharing PHI/PII/PCI data in Andorid Apps Using Content Provider Content providers helps an application to manage access to data stored by itself, stored by other apps, and provide a way to share data with other apps. They encapsulate the data, and provide mechanisms for defining data security. Content providers is a standard interface that connects data in one process with code running in another process. Implementing a content provider has many advantages. One of the major advantages is that it helps to share data across applications in a secure manner. As per the implementation from google an application data is very private of itself and hence its not possible for any other application to access this data by default. Content Provider can use simple insert, update methods to access application data. Content providers offer granular control over the permissions for accessing data. You can choose to restrict access to a content provider from solely within your application, grant blanket permission to access data from other applications, or configure different permissions for reading and writing data Private Content Provider is the Content Provider which is used only in the single application, and the safest Content Provider. Points (Creating a Content Provider): 1. Do not (Cannot) implement Private Content Provider in Android 2.2 (API Level 8) or earlier. 2. Explicitly set the exported attribute to false.
- 2. 3. Handle the received request data carefully and securely, even though the data comes from the same application. 4. Sensitive information can be sent since it is sending and receiving all within the same application. 5. Sensitive information can be sent since the destination provider is in the same application. 6. Handle received result data carefully and securely, even though the data comes from the same application. Public Content Provider is the Content Provider which is supposed to be used by unspecified Points (Creating a Content Provider): 1. Explicitly set the exported attribute to true. 2. Handle the received request data carefully and securely. 3. When returning a result, do not include sensitive information. 4. Do not send sensitive information. 5. When receiving a result, handle the result data carefully and securely. Attacks on Content Provider can lead to the following vulnerabilities: 1. SQL injections 2. Data leakage 3. Path Traversal 1. SQL Injections:- Protecting against malicious input- If the data managed by the content provider is in an SQL database, including external untrusted data into raw SQL statements can lead to SQL injection. When accessing a content provider, use parameterized query methods such as query(), update(), and delete() to avoid potential SQL injection from untrusted sources.
- 3. Consider this selection clause: // Constructs a selection clause by concatenating the user's input to the column name String mSelectionClause = "var = " + mUserInput; If you do this, you're allowing the user to concatenate malicious SQL onto your SQL statement. For example, the user could enter "nothing; DROP TABLE *;" for mUserInput, which would result in the selection clause var = nothing; DROP TABLE *;. Since the selection clause is treated as an SQL statement, this might cause the provider to erase all of the tables in the underlying SQLite database (unless the provider is set up to catch SQL injectionattempts). To avoid this problem, use a selection clause that uses ? as a replaceable parameter and a separate array of selection arguments. When you do this, the user input is bound directly to the query rather than being interpreted as part of an SQL statement. Because it's not treated as SQL, the user input can't inject malicious SQL. Instead of using concatenation to include the user input, use this selection clause: // Constructs a selection clause with a replaceable parameter String mSelectionClause = "var = ?"; Set up the array of selection arguments like this: // Defines an array to contain the selection arguments String[] selectionArgs = {""}; Put a value in the selection arguments array like this: // Sets the selection argument to the user's input selectionArgs[0] = mUserInput; A selection clause that uses ? as a replaceable parameter and an array of selection arguments array are preferred way to specify a selection, even if the provider isn't based on an SQL database. 2. Data Leakage Limit the accessibility of an app's sensitive content provider. Use signature permission to prevent other apps not developed by you from communicating with your app. If you are using a content provider for sharing data between only your own apps, it is preferable to use the android:protectionLevel attribute set to “signature” protection. If your content provider is just for your app’s use then set it to be android:exported=false in the manifest. If you are intentionally exporting the content provider then you should also specify one or more permissions for reading and writing.
- 4. Path Traversal By using the canonicalized path, directory traversal will be mitigated even when a doubly-encoded path is supplied. Applications should ensure that any URL received by a content provider is canonicalized to avoid a directory traversal attack. --X-X-X- Avinash Sinha: - Lead Security Penetration Tester with one of the largest Healthcare company Having a demonstrated history of working in the information technology and services industry. Skilled in Penetration Testing, Vulnerability Assessments, Project Management, Health Care, IoT, Payment Card Industry Data Security Standard (PCI DSS), Linux, HIPPA, FDA, Information Security, and Integration. Strong Emphasis on Enterprise Security and information technology with a Corporate-PGDBA focused in International Business from Symbiosis.
