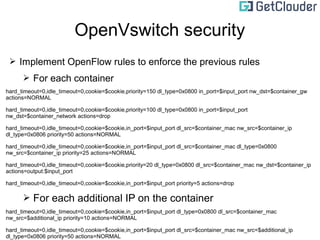
This document discusses secure LXC networking using various methods like MACVLAN, VETH, VLAN, and OpenVSwitch. It provides code samples for generating MAC addresses in Bash, PLPGSQL, and Python. Bridging with Linux bridge and OpenVSwitch is also covered. The document emphasizes securing network traffic within and between containers by limiting traffic to assigned IP/MAC addresses and enforcing rules with OpenFlow.




![generate MAC address in bash
function gen_mac() {
mac_vars=(0 1 2 3 4 5 6 7 8 9 a b c d e f)
mac_base='52:00:01:'
ret=''
for i in {1..6}; do
n=$RANDOM
let 'n %= 16'
ret="${ret}${mac_vars[$n]}"
if [ $i -eq 2 ] || [ $i -eq 4 ]; then
ret="${ret}:"
fi
done
echo "${mac_base}${ret}"
}](https://image.slidesharecdn.com/secure-lxc-networking-141103022732-conversion-gate01/85/Secure-LXC-Networking-5-320.jpg)

![generate MAC address in Python
#/usr/bin/python
import random
mac = [random.choice(range(256)) for i in range(6)]
mac[0] |= 0x02
mac[0] &= 0xfe
print ':'.join('%02x' % m for m in mac)](https://image.slidesharecdn.com/secure-lxc-networking-141103022732-conversion-gate01/85/Secure-LXC-Networking-7-320.jpg)






![MACVLAN
➢ If you want to manually setup the networking
ip link add link PARENT [NAME] type macvlan [address MAC]
➢ Auto generated MAC adresses
# ip link add link eth0 lxc0 type macvlan
➢ Manually assigned
# ip link add link eth0 lxc1 type macvlan address f0:de:f1:81:0a:2a
➢ Additional parameter: mode
➢ macvlan mode { private | vepa | bridge | passthru }](https://image.slidesharecdn.com/secure-lxc-networking-141103022732-conversion-gate01/85/Secure-LXC-Networking-14-320.jpg)