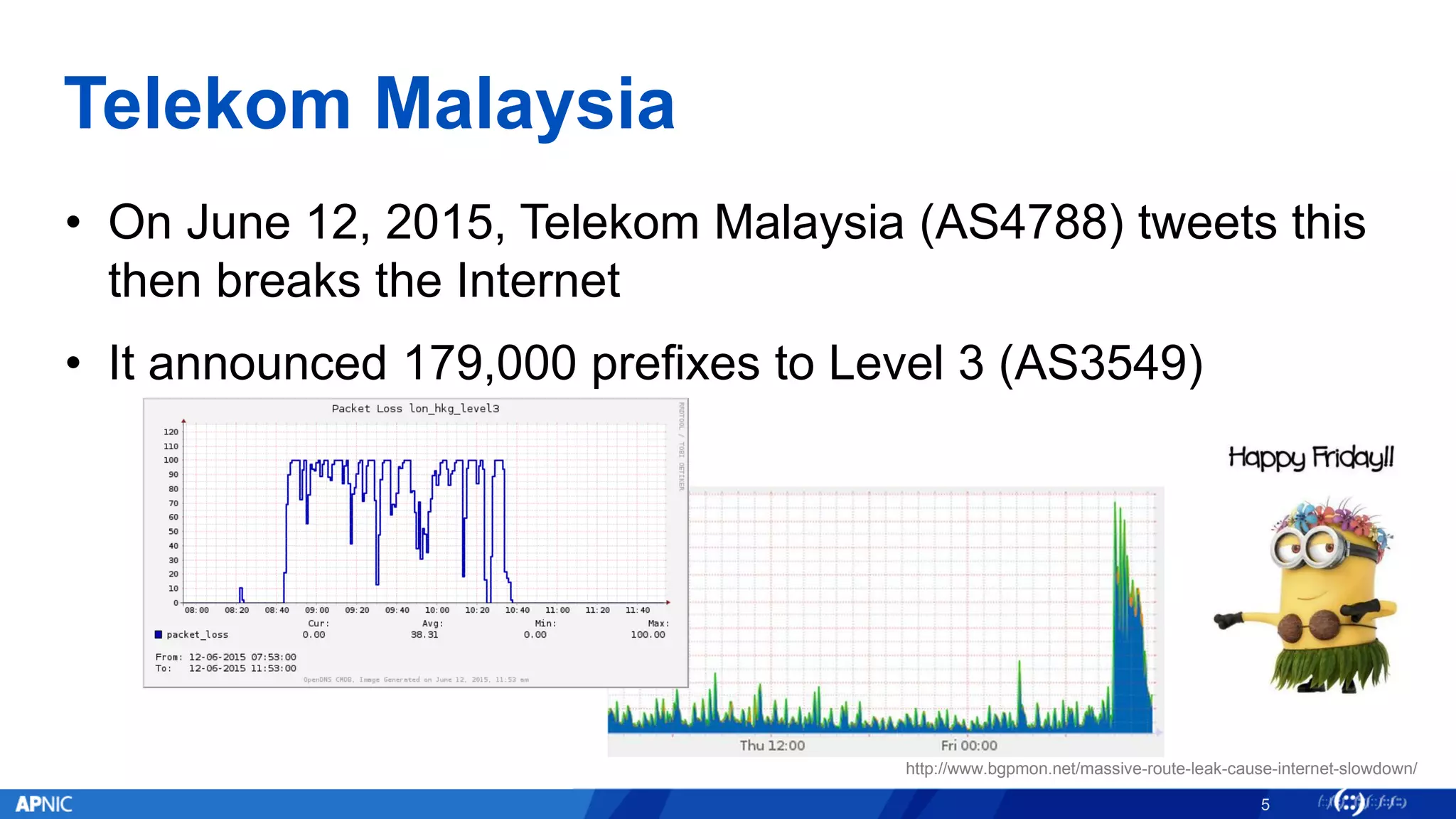
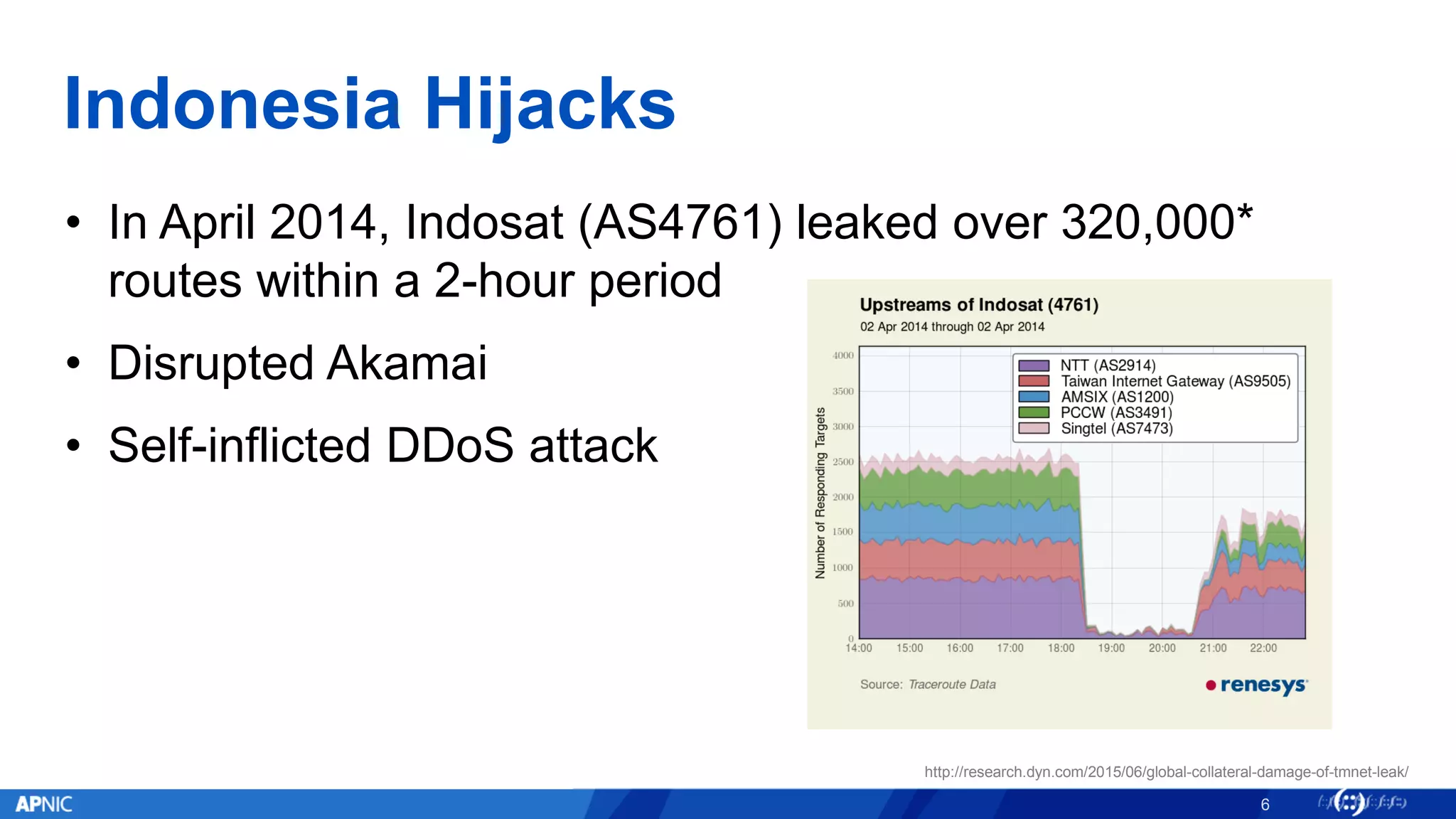
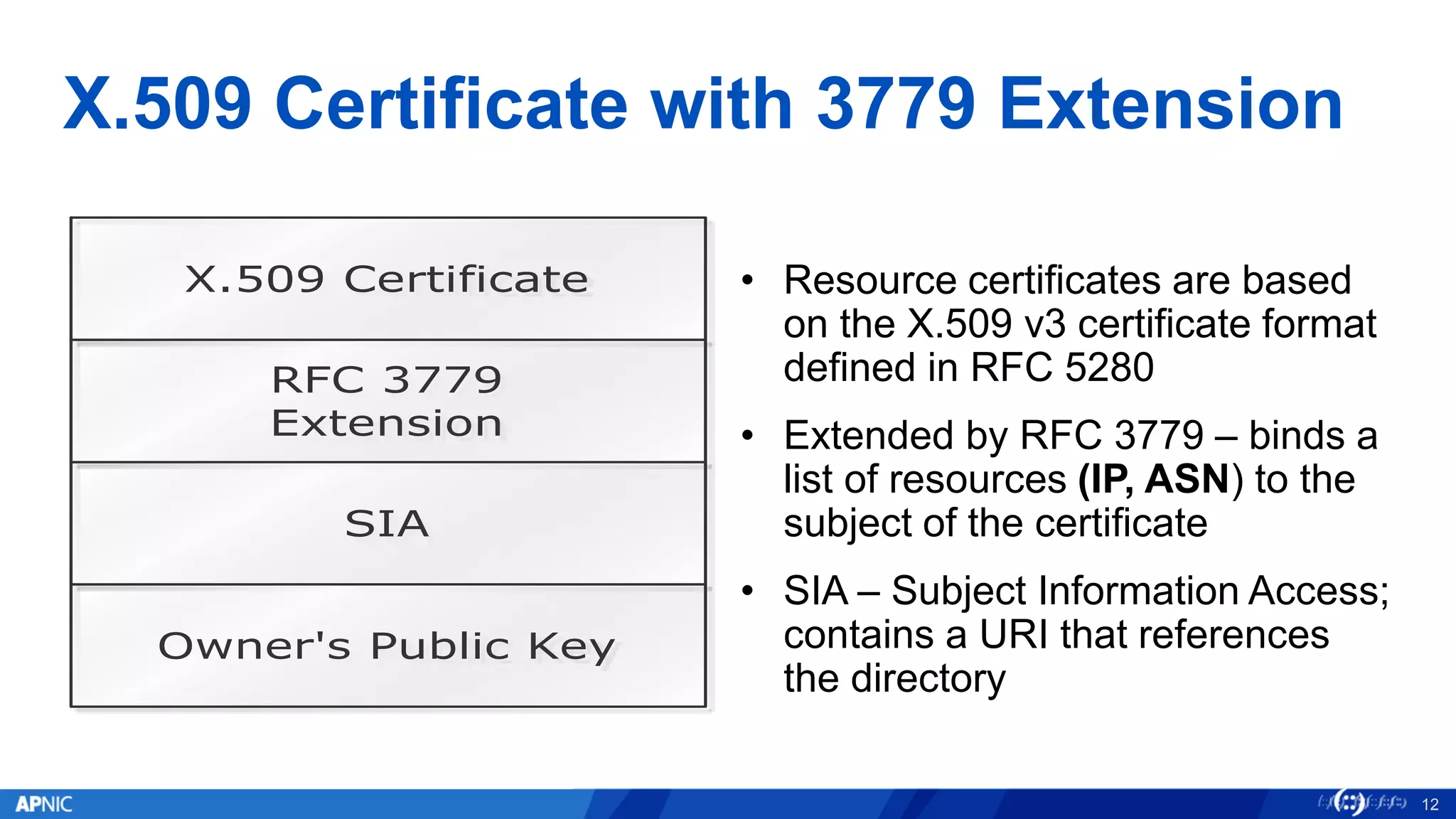
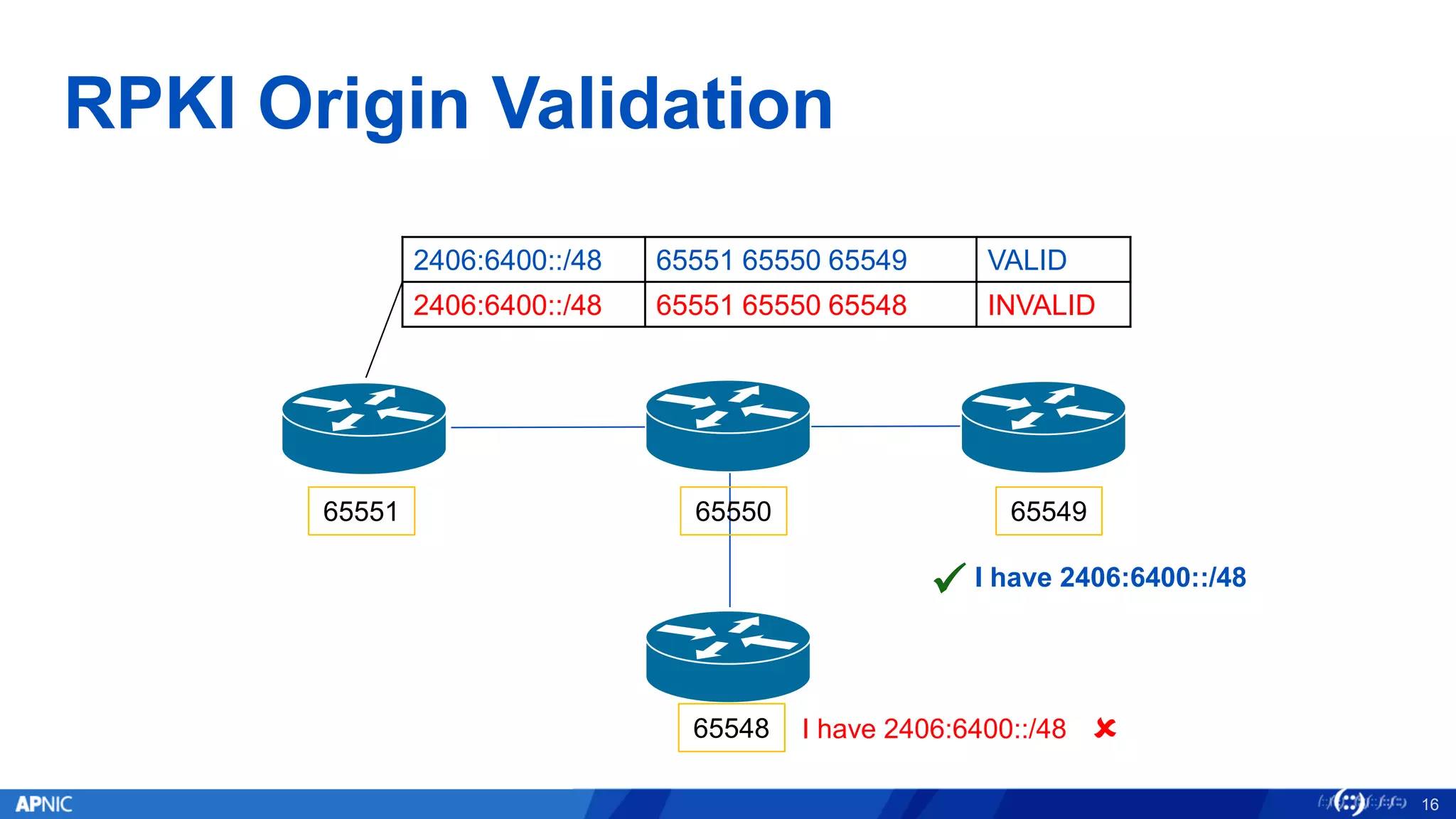
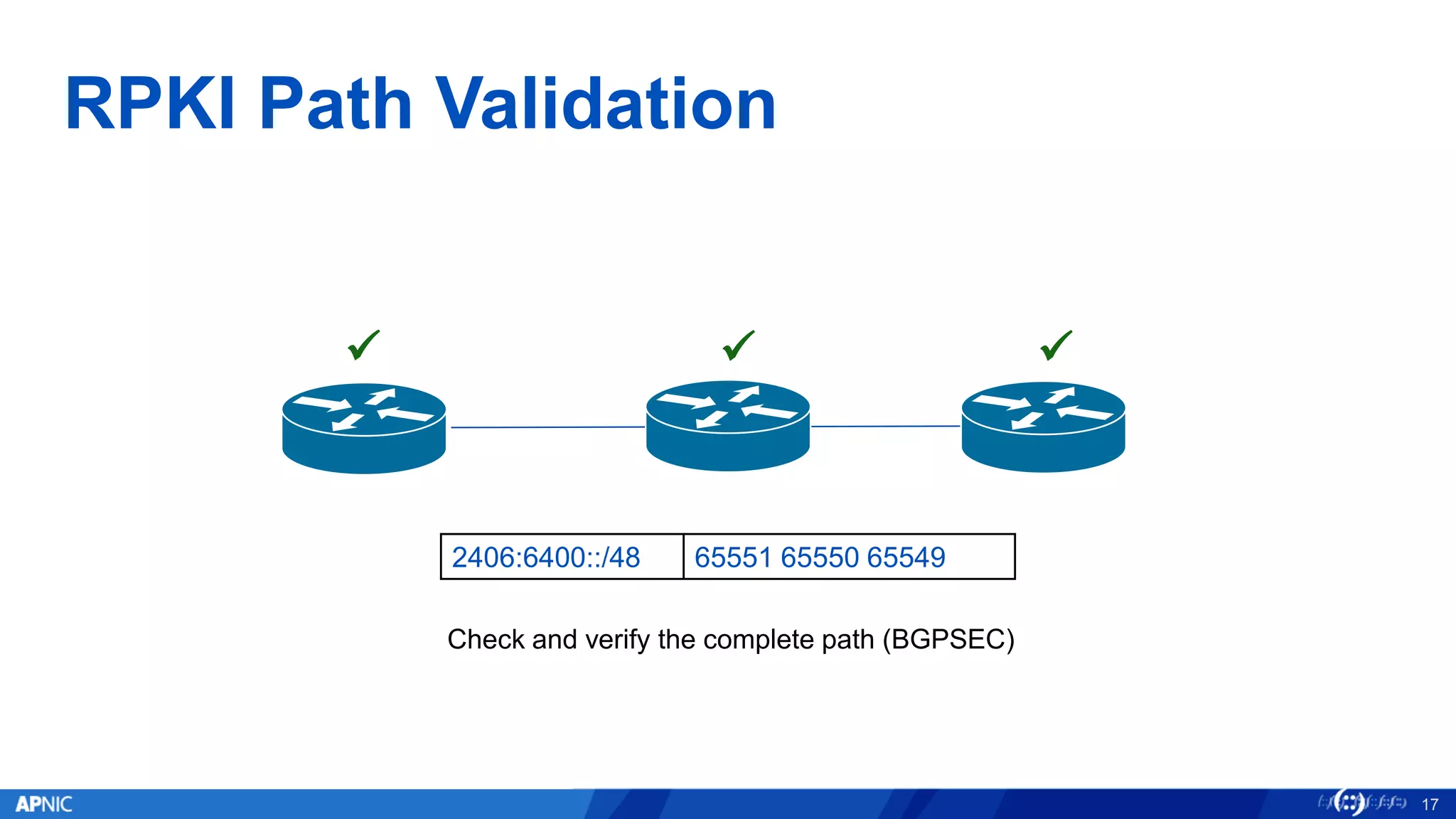
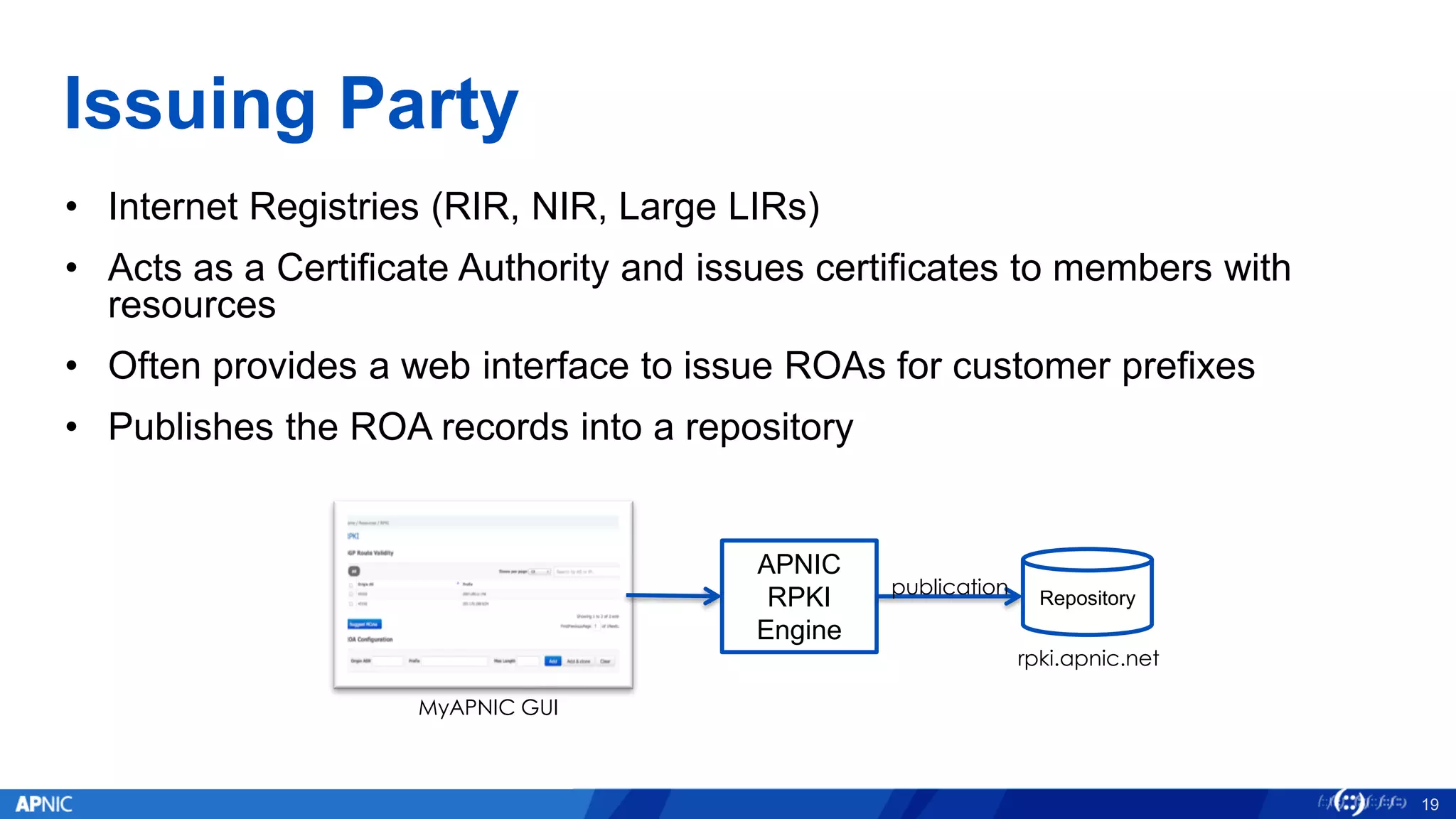
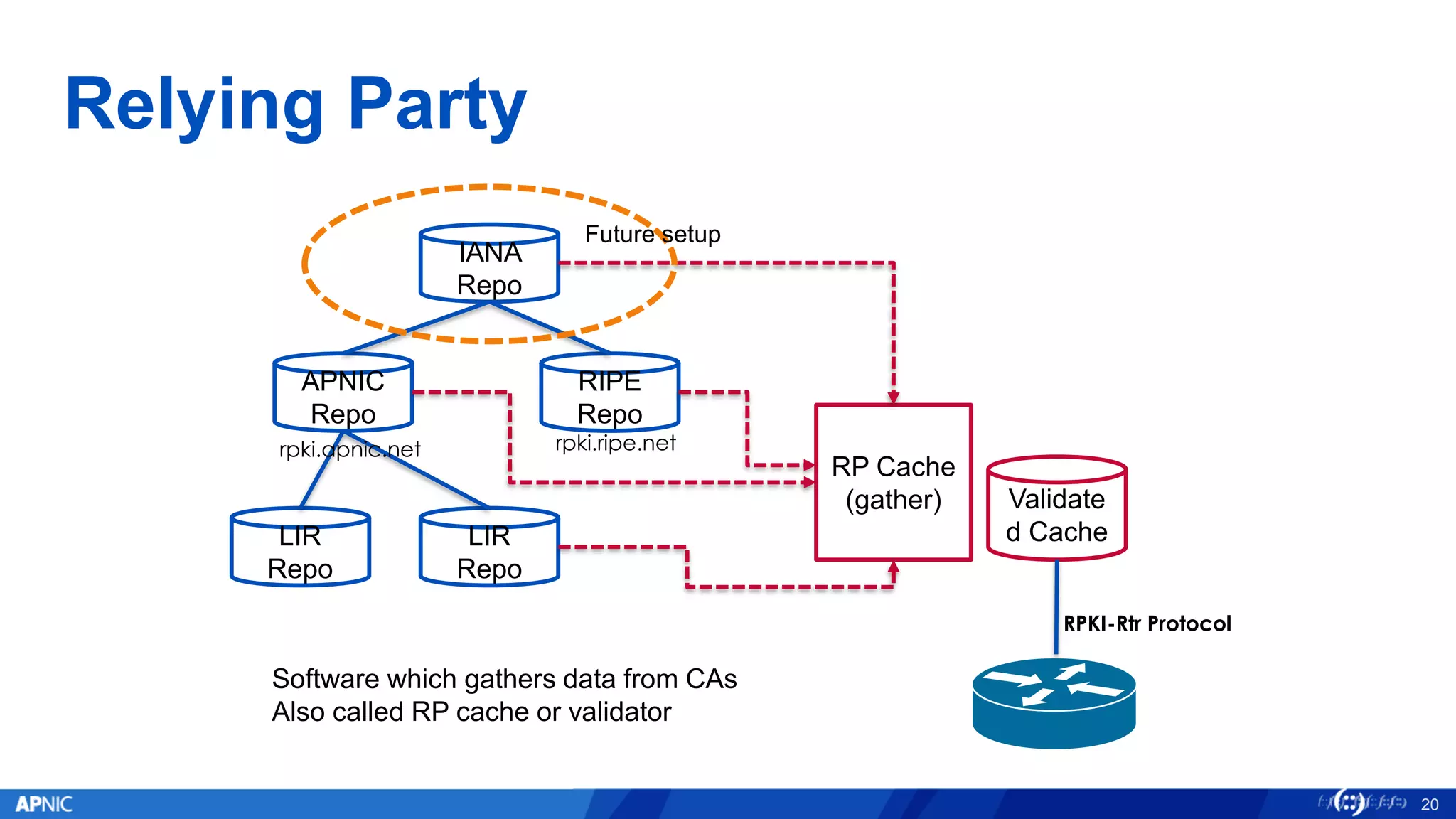
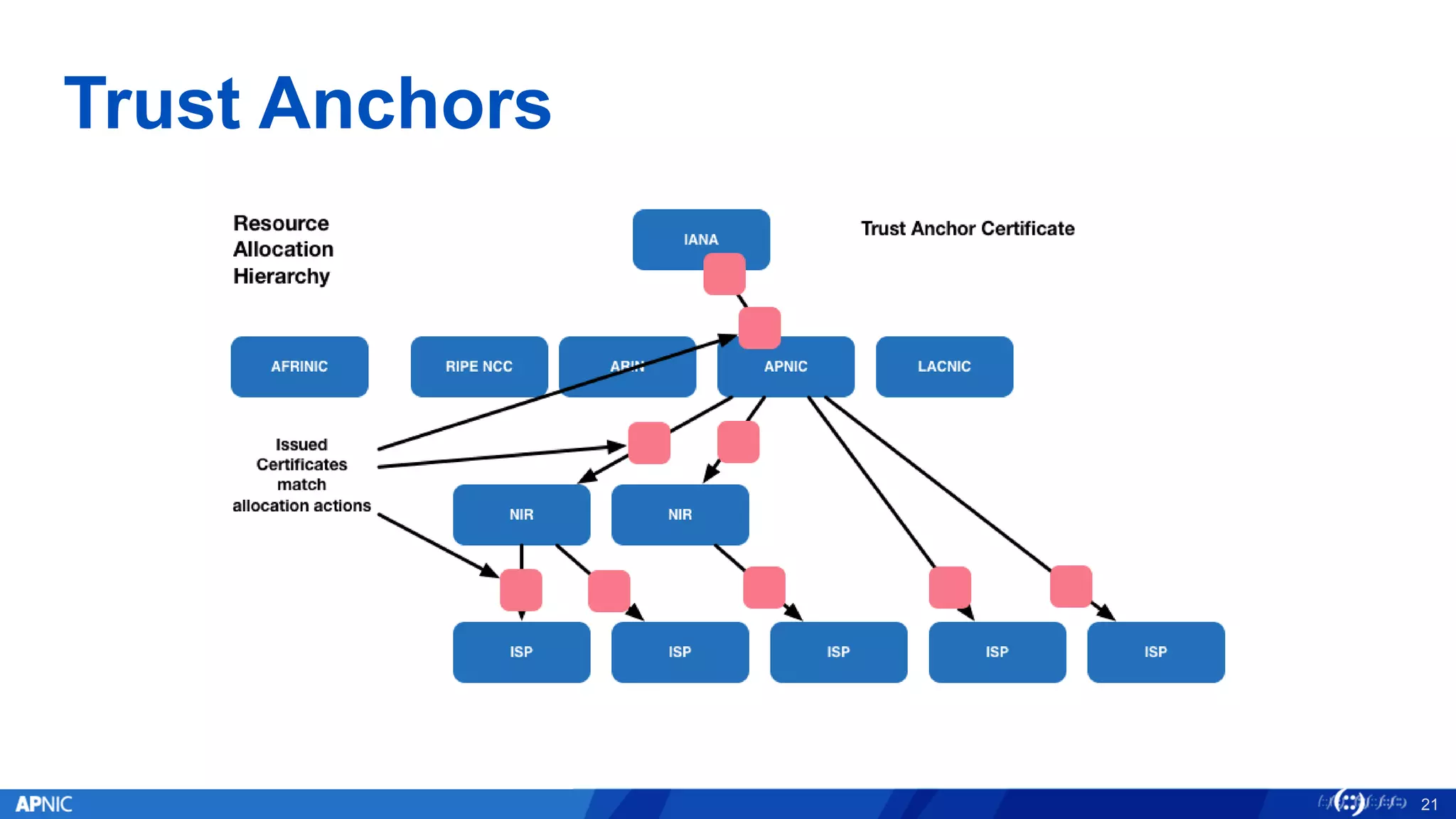
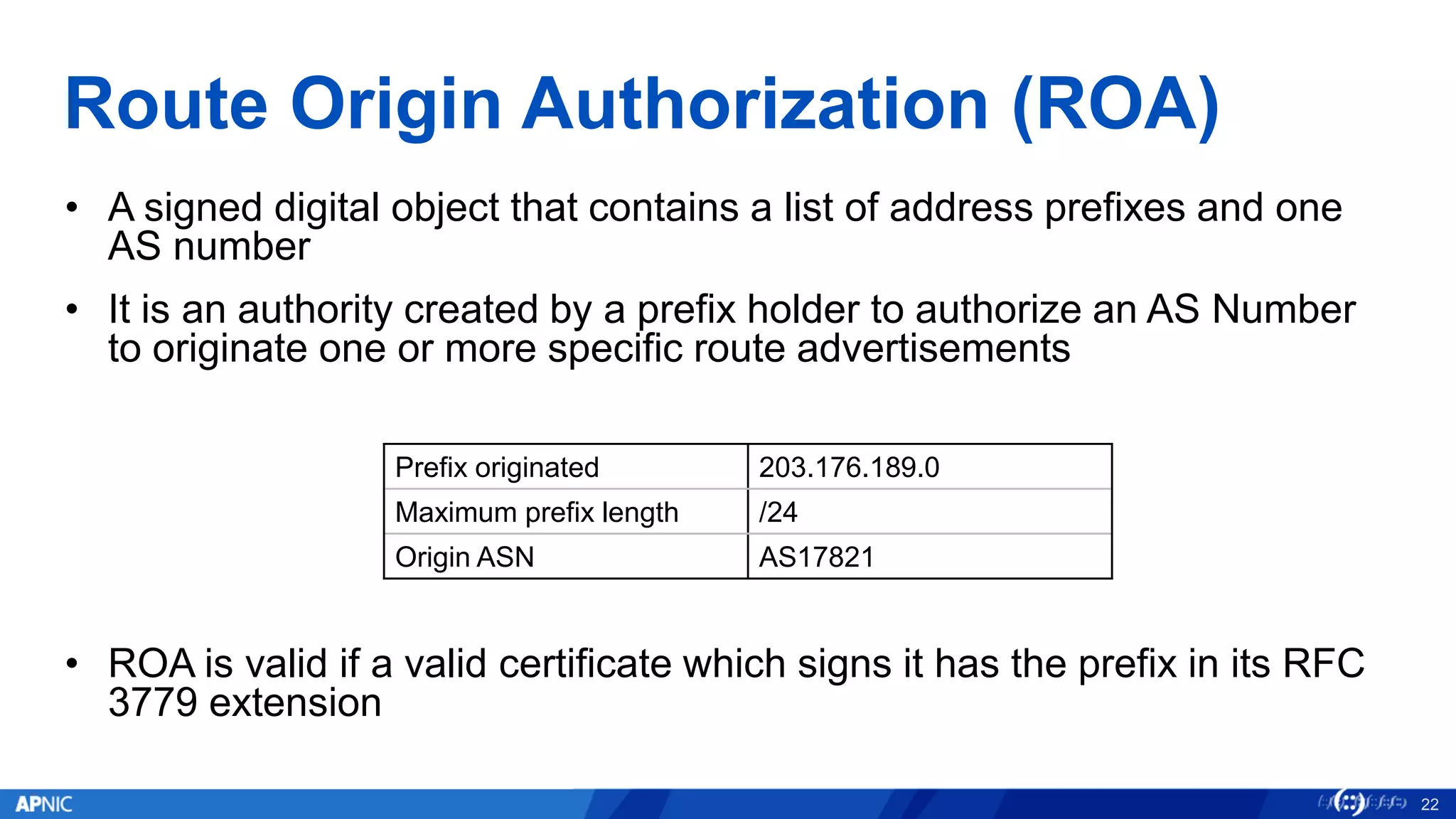
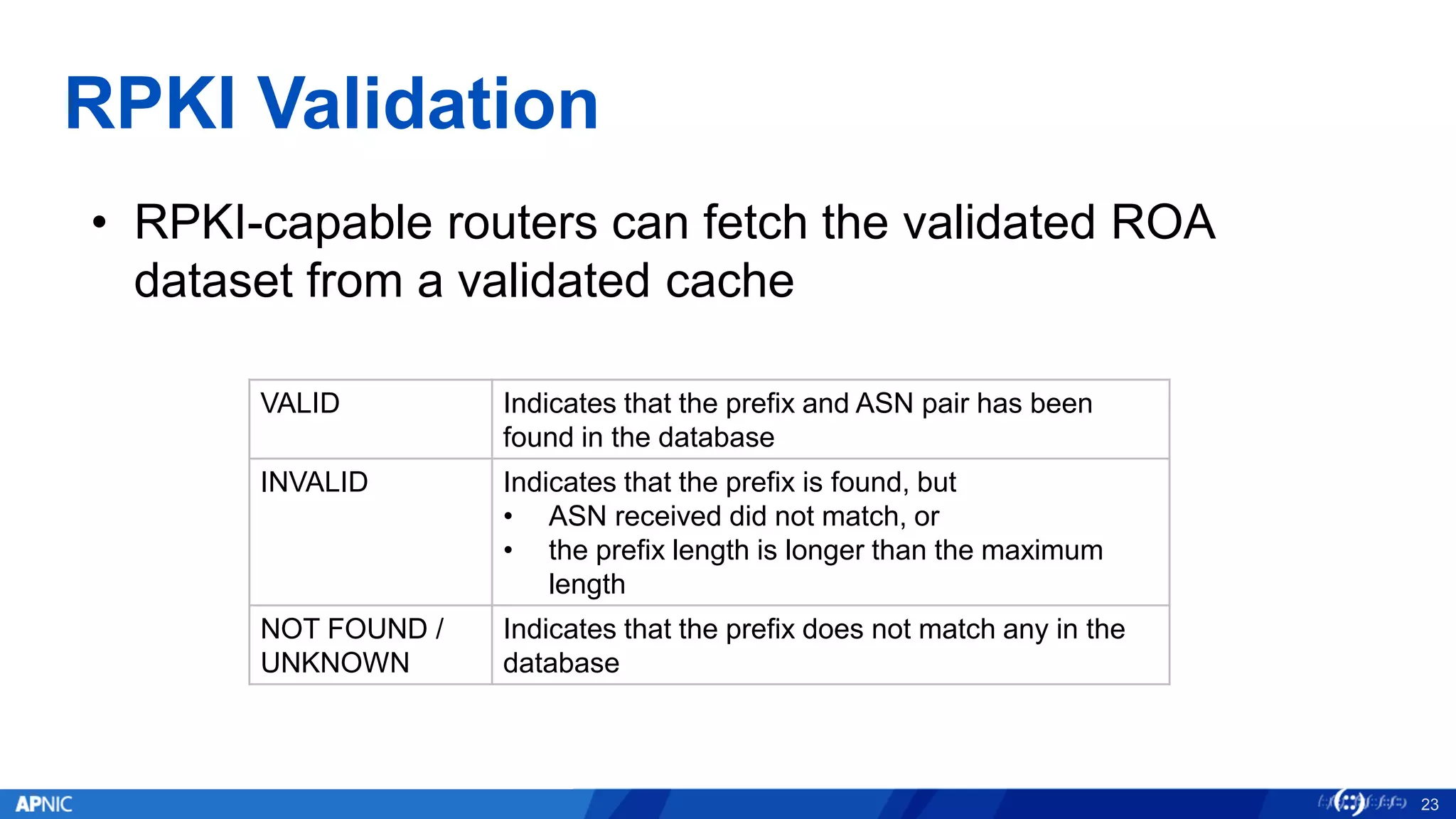
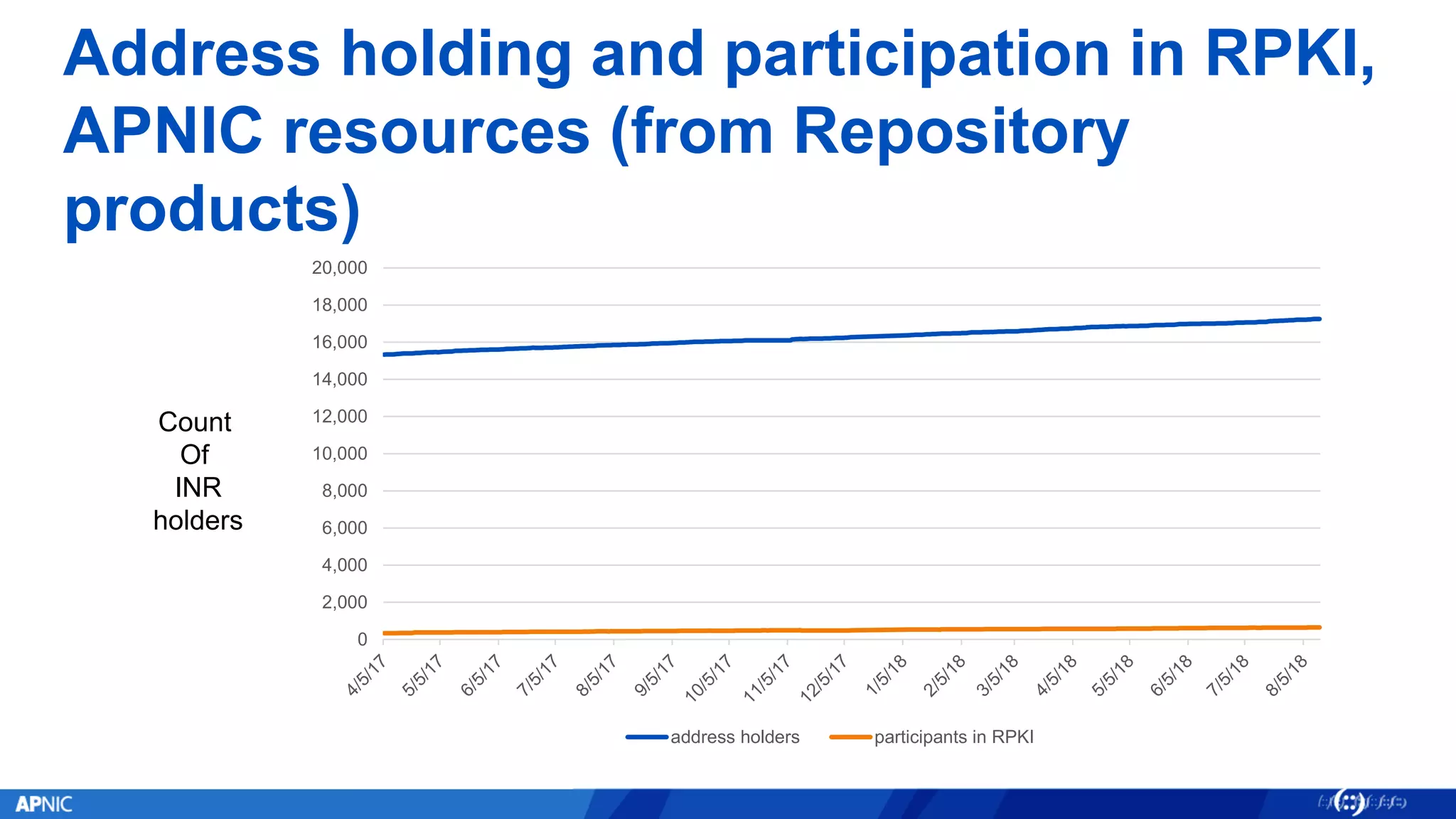
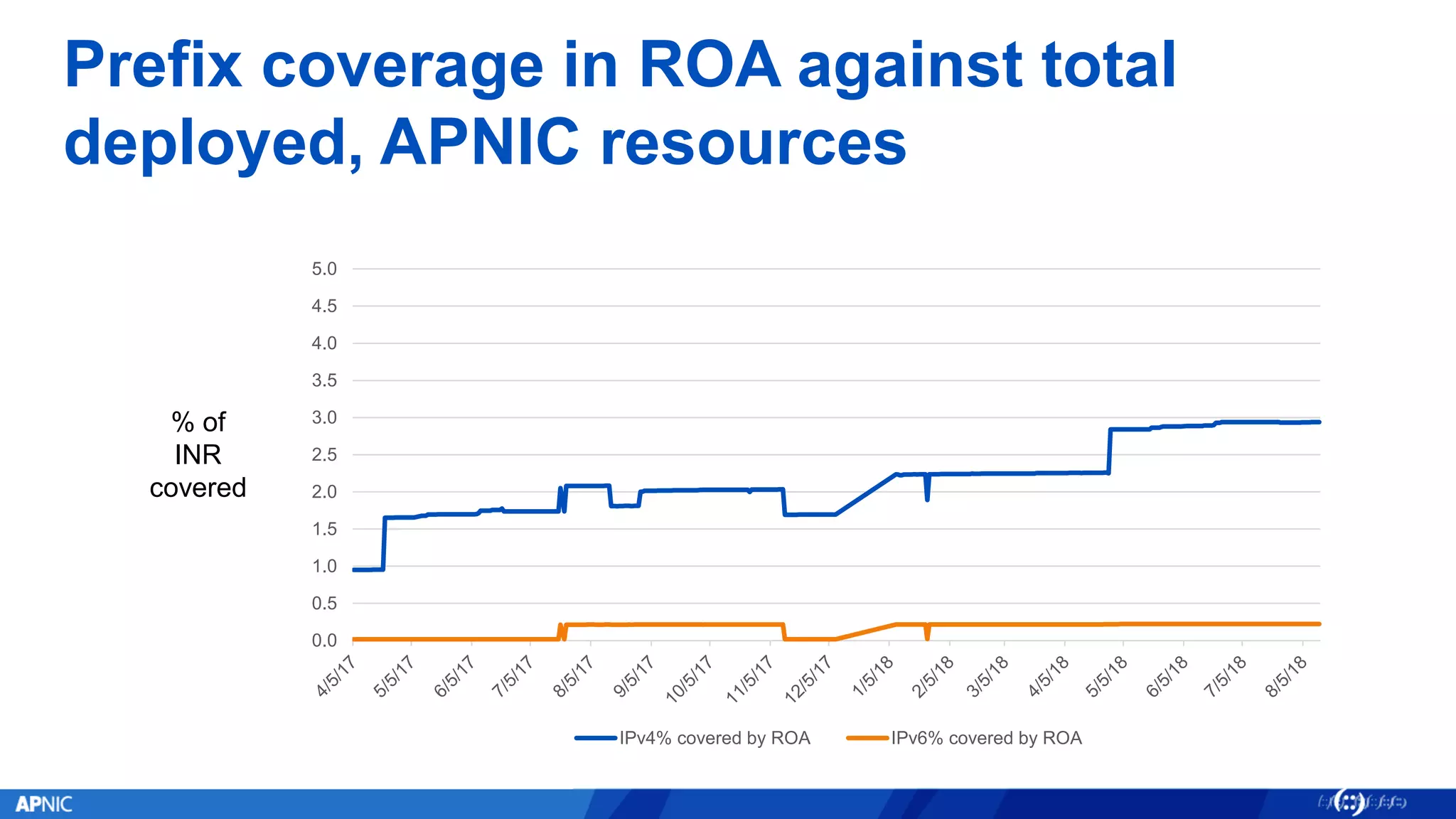
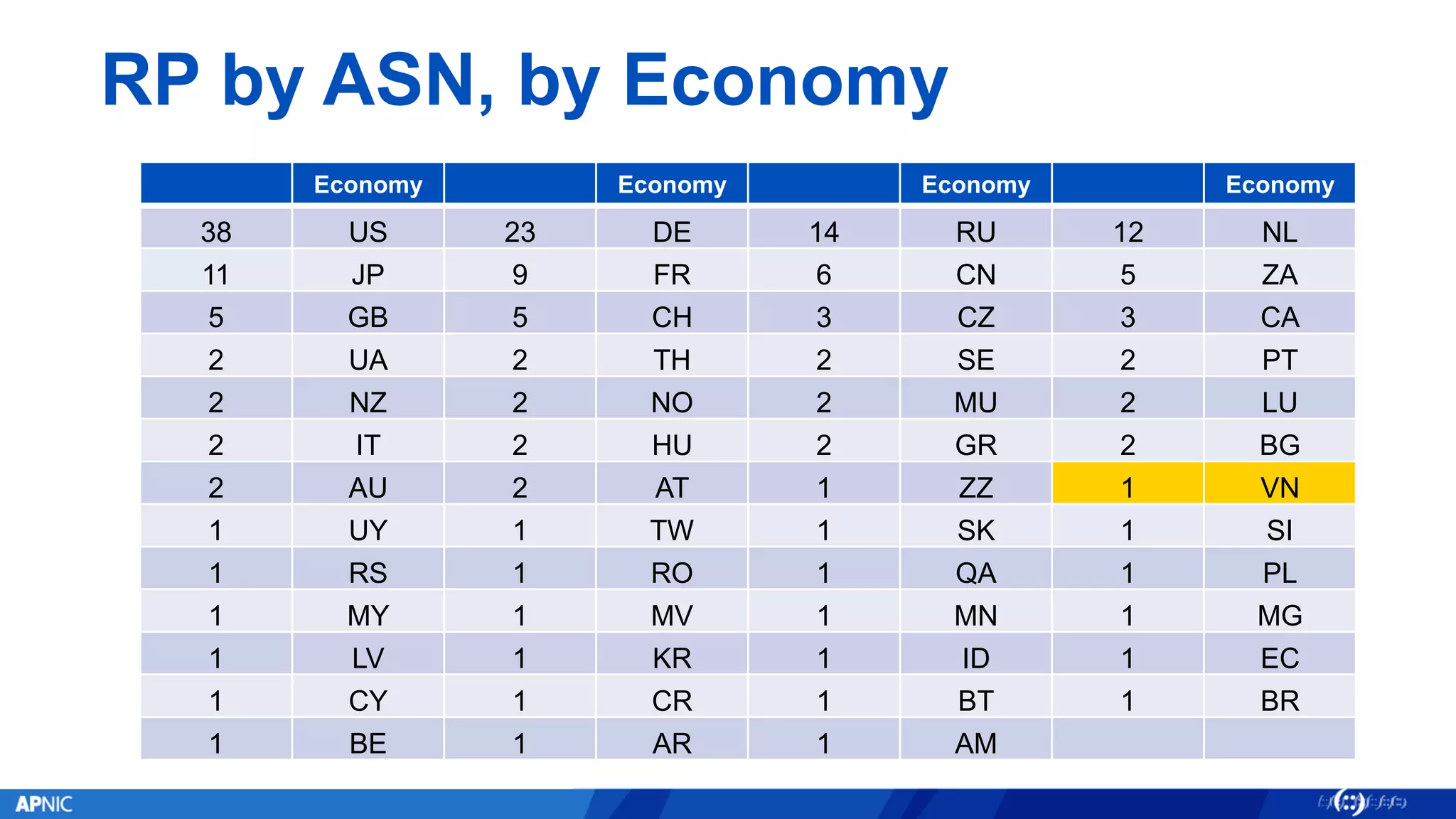
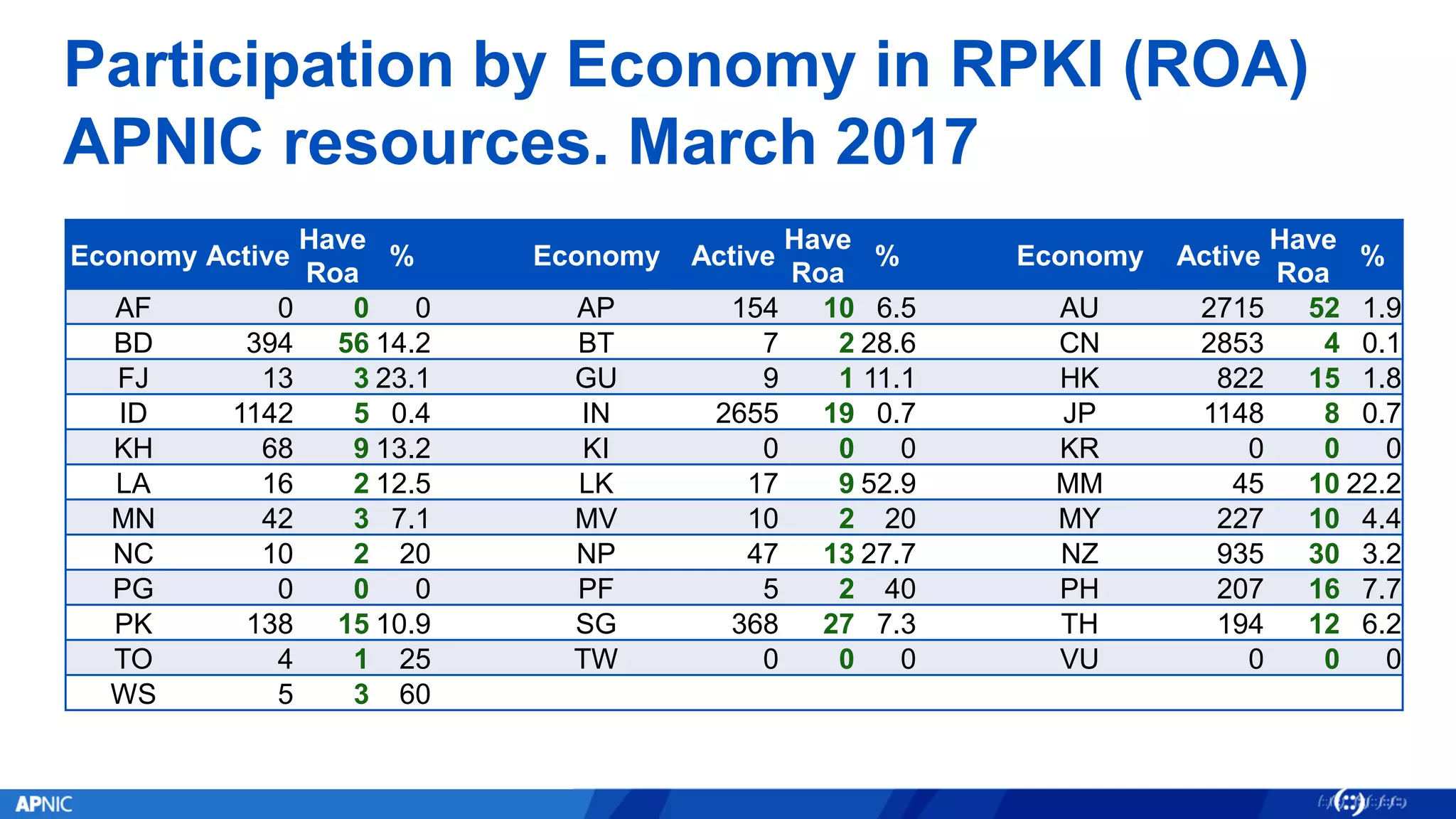
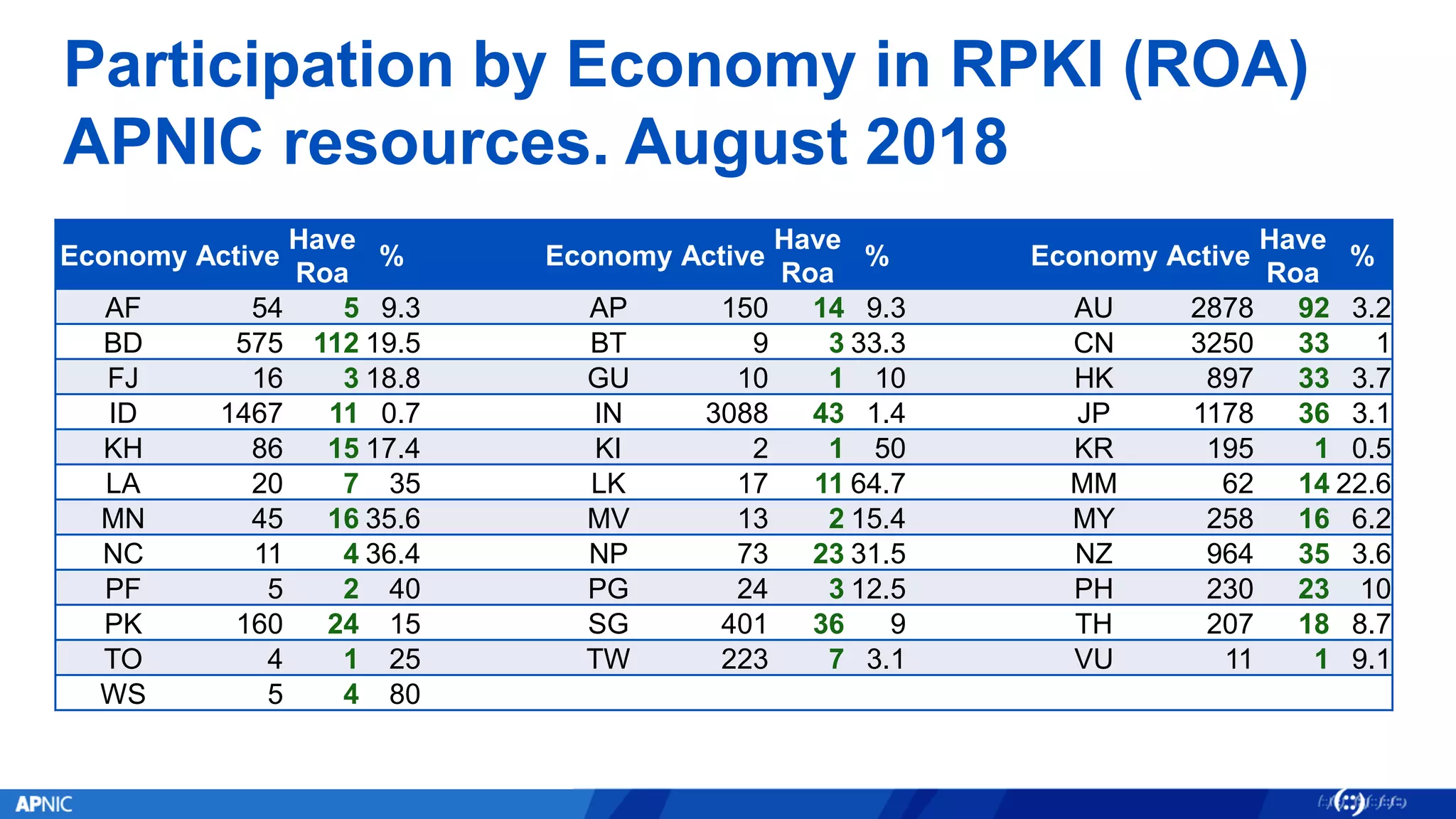
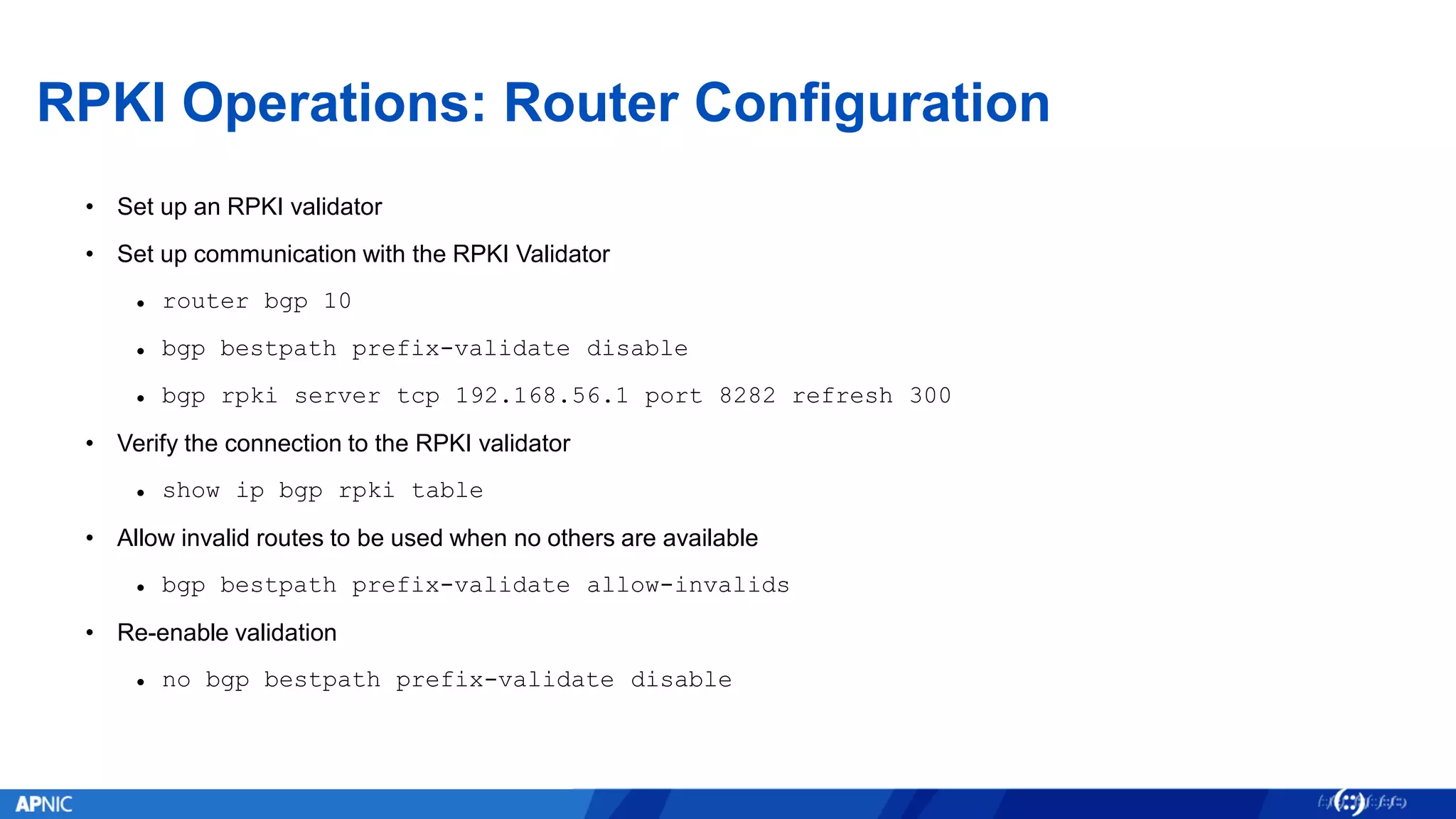
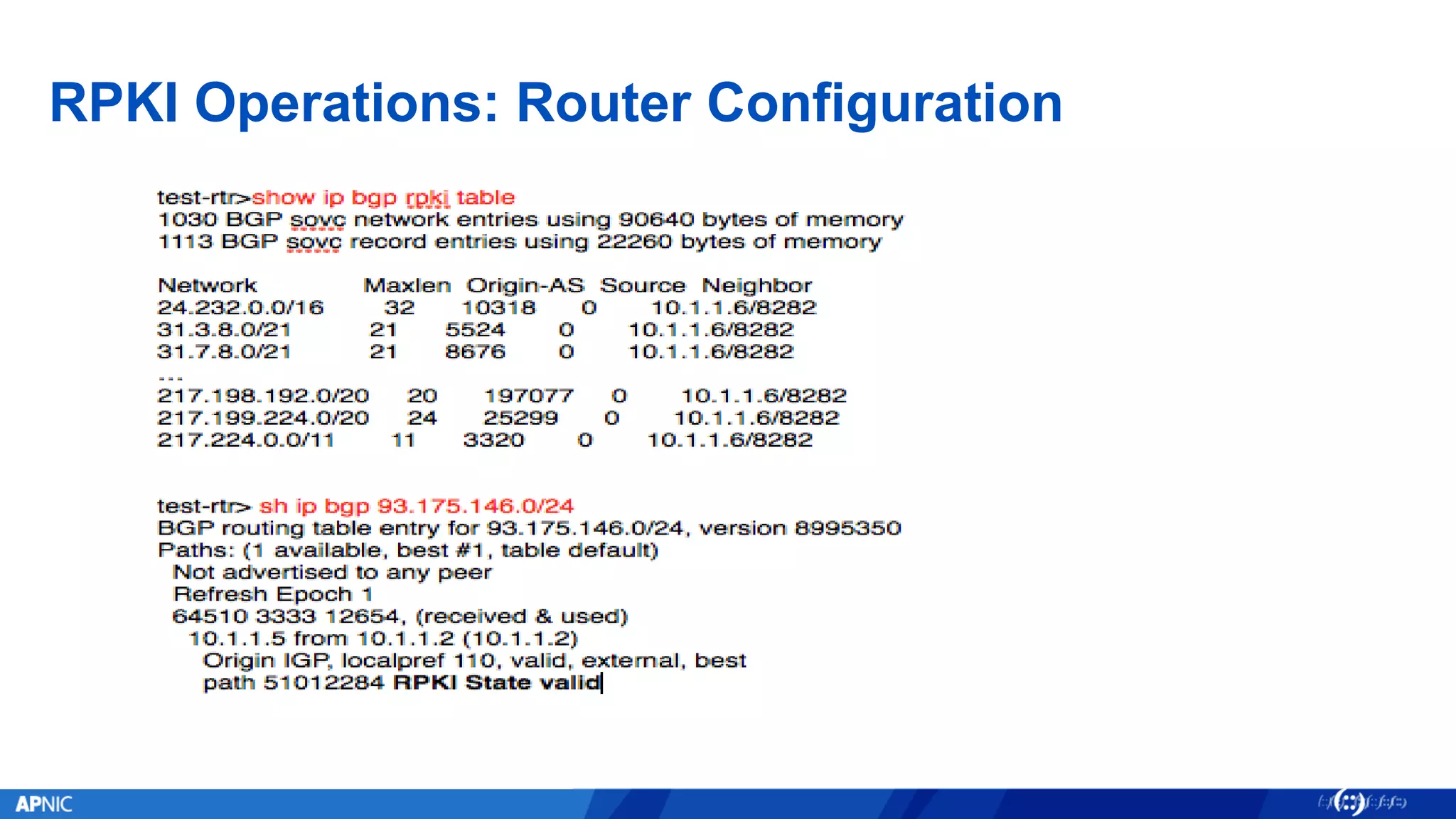
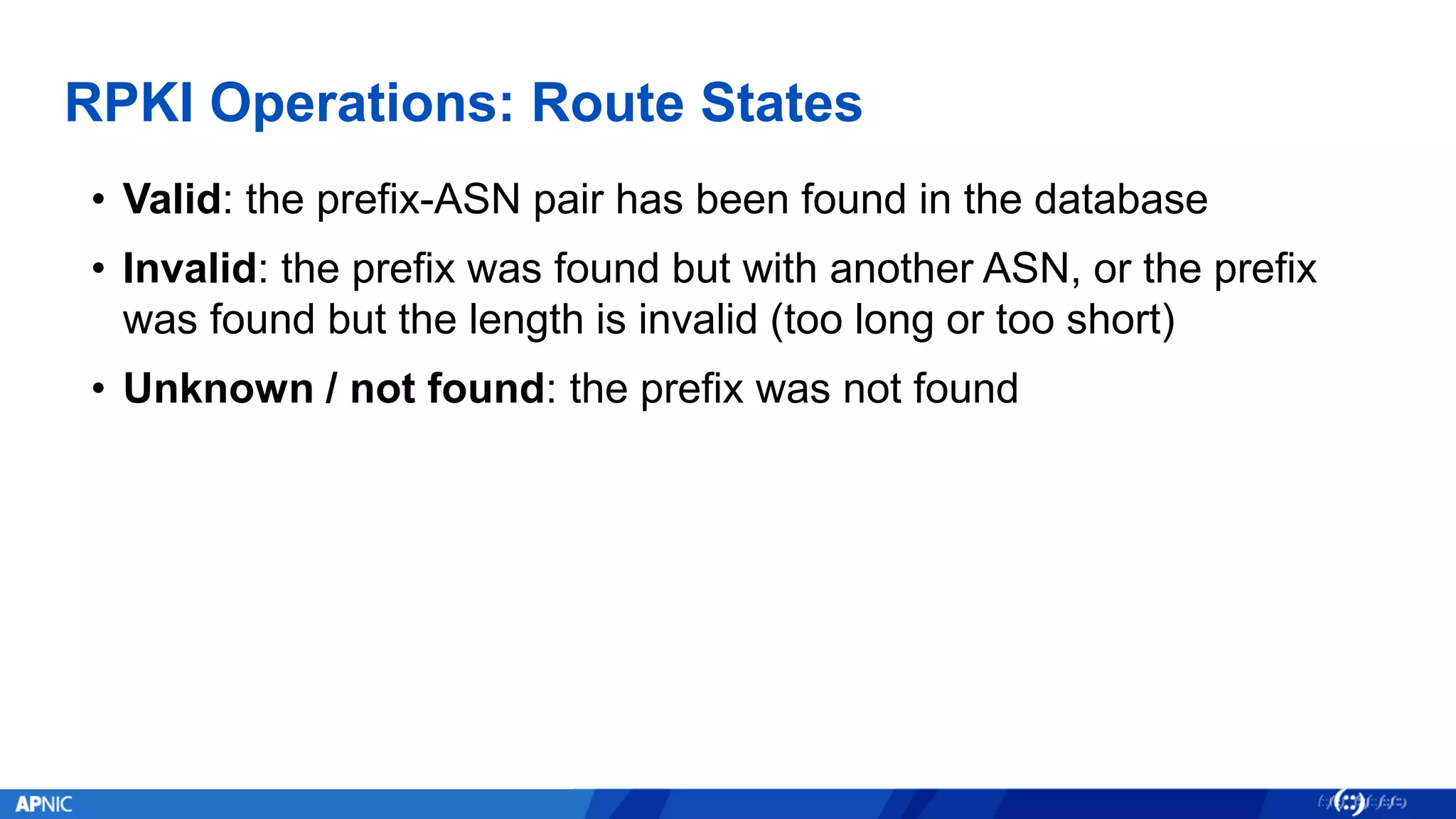
RPKI (Resource Public Key Infrastructure) is a framework that helps secure Internet routing by validating route origins and paths. It works by (1) having certificate authorities like regional internet registries issue certificates binding IP addresses and ASNs, (2) having address holders issue Route Origin Authorizations specifying which ASNs are authorized to originate which address ranges, and (3) having routers perform validation of routes based on this published data. While adoption is still in early stages, RPKI deployment is gradually increasing and provides benefits like preventing route hijacking and misorigination.