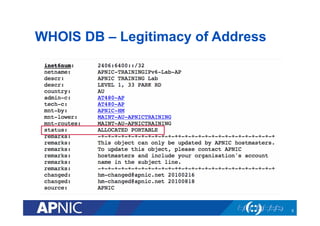
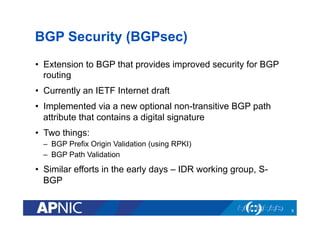
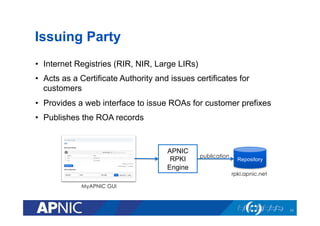
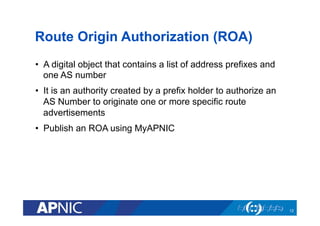
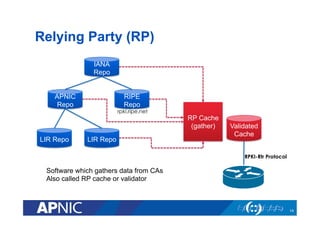
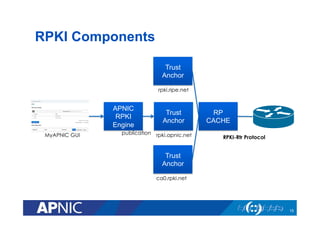
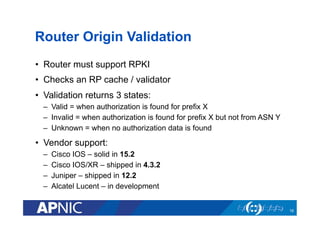
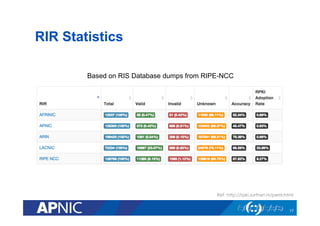
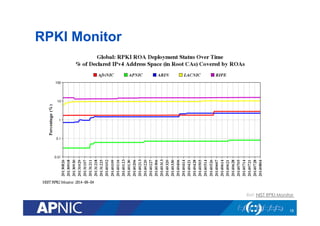
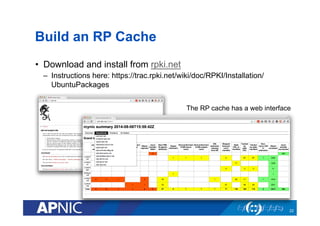
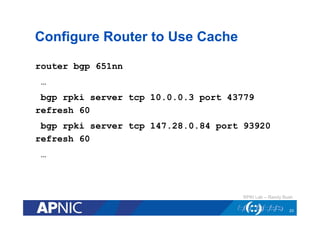
The document provides an overview of the Resource Public Key Infrastructure (RPKI) which aims to address routing incidents like hijacking and misdirection. It discusses how RPKI uses digital certificates and Route Origin Authorizations (ROAs) to validate that an Autonomous System is authorized to originate routes for specific IP address blocks. The key components of RPKI include Certificate Authorities, Relying Parties, and routers configured with RPKI support to filter routes based on validation of origin AS authorization. Deployment status at the Regional Internet Registries and an APNIC RPKI service are also covered.