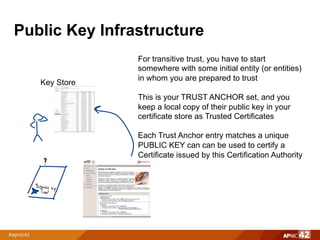
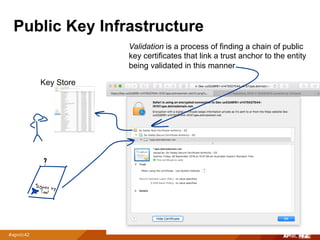
The document discusses trust anchors and public key infrastructure (PKI) in the context of the Resource Public Key Infrastructure (RPKI). It presents several models for establishing trust anchors for the RPKI, including:
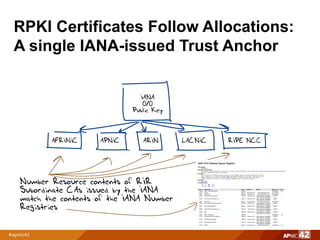
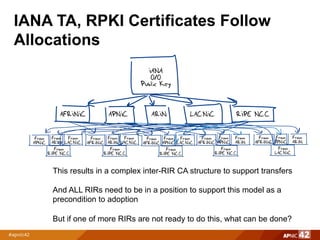
1) A single IANA-issued trust anchor with subordinate certificates issued by each Regional Internet Registry (RIR) matching their number resource allocations. This would not support transferred resources.
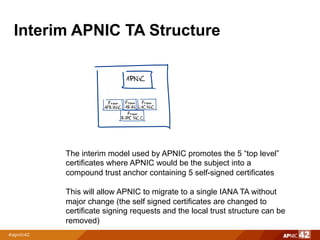
2) An interim APNIC trust anchor structure containing self-signed certificates from each RIR to allow migration to a single IANA trust anchor.
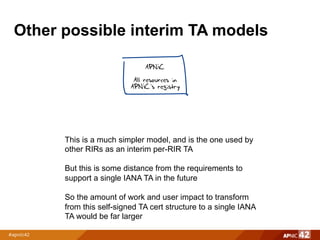
3) Individual per-RIR self-signed trust anchors, a simpler interim model but requiring more work to transition to a single IANA trust anchor.