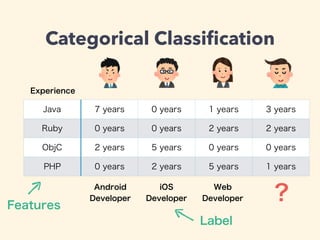
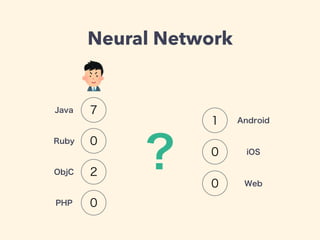
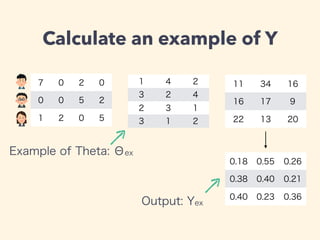
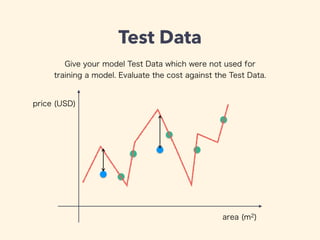
This document provides an introduction to machine learning concepts including linear regression, neural networks, and model evaluation. It discusses using machine learning for tasks like image recognition, text translation, and medical applications. Linear regression is demonstrated for predicting housing prices based on area. Neural networks are explained for classification problems with examples of predicting a developer type based on experience. The document outlines model training, calculating costs, tuning hyperparameters, and evaluating models on test vs. cross-validation data to avoid overfitting. Caveats are noted about omitted math details.