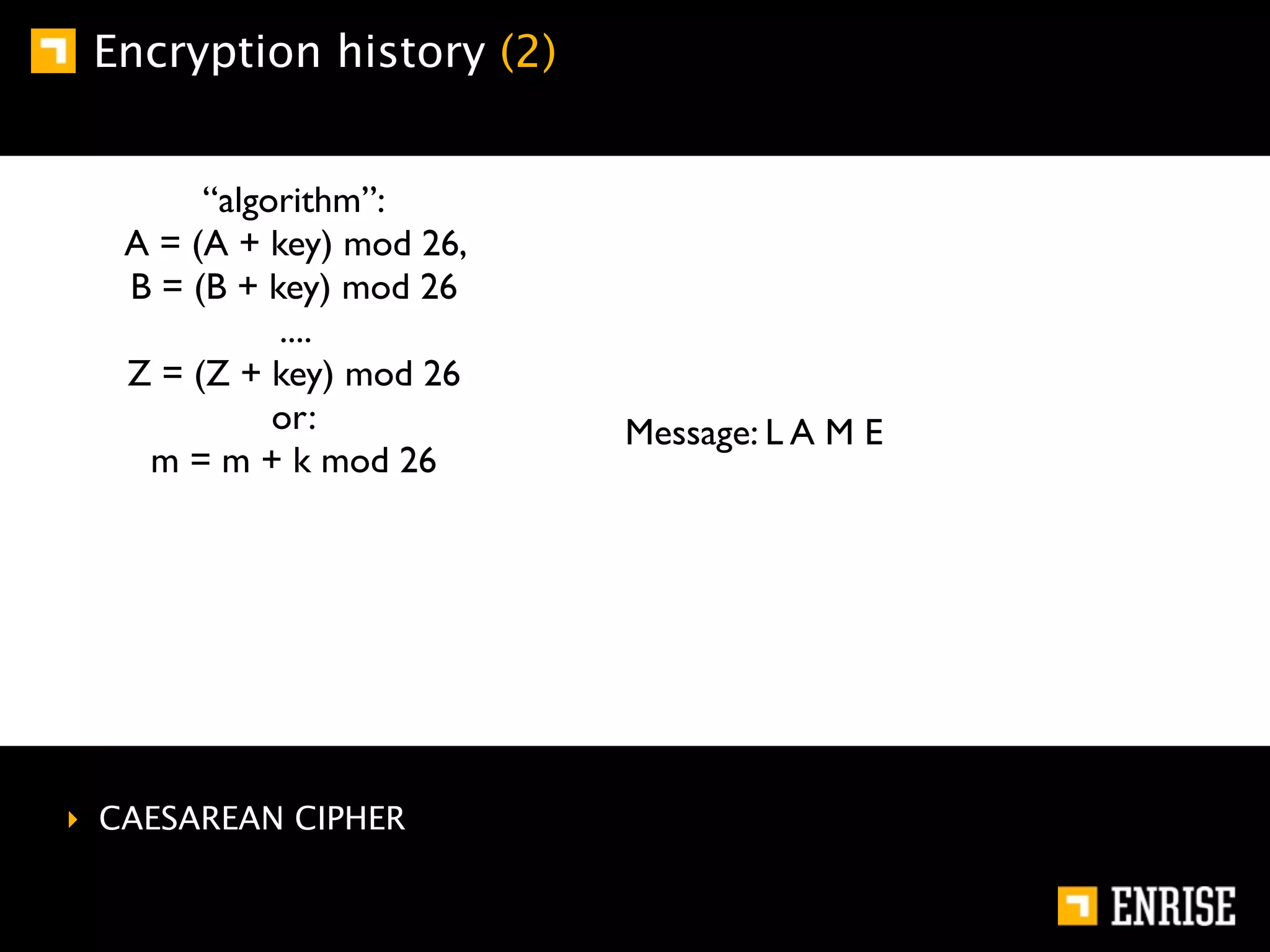
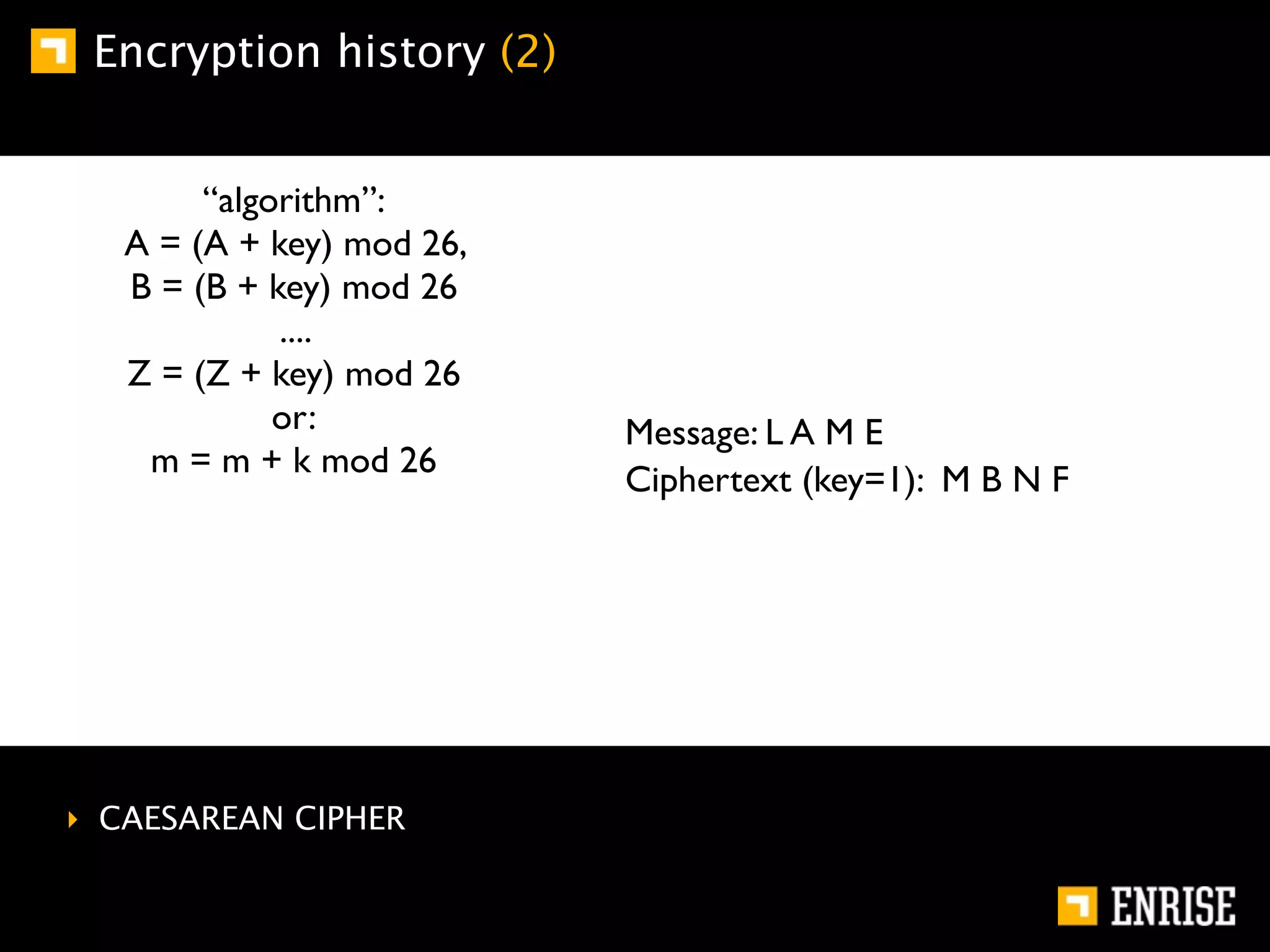
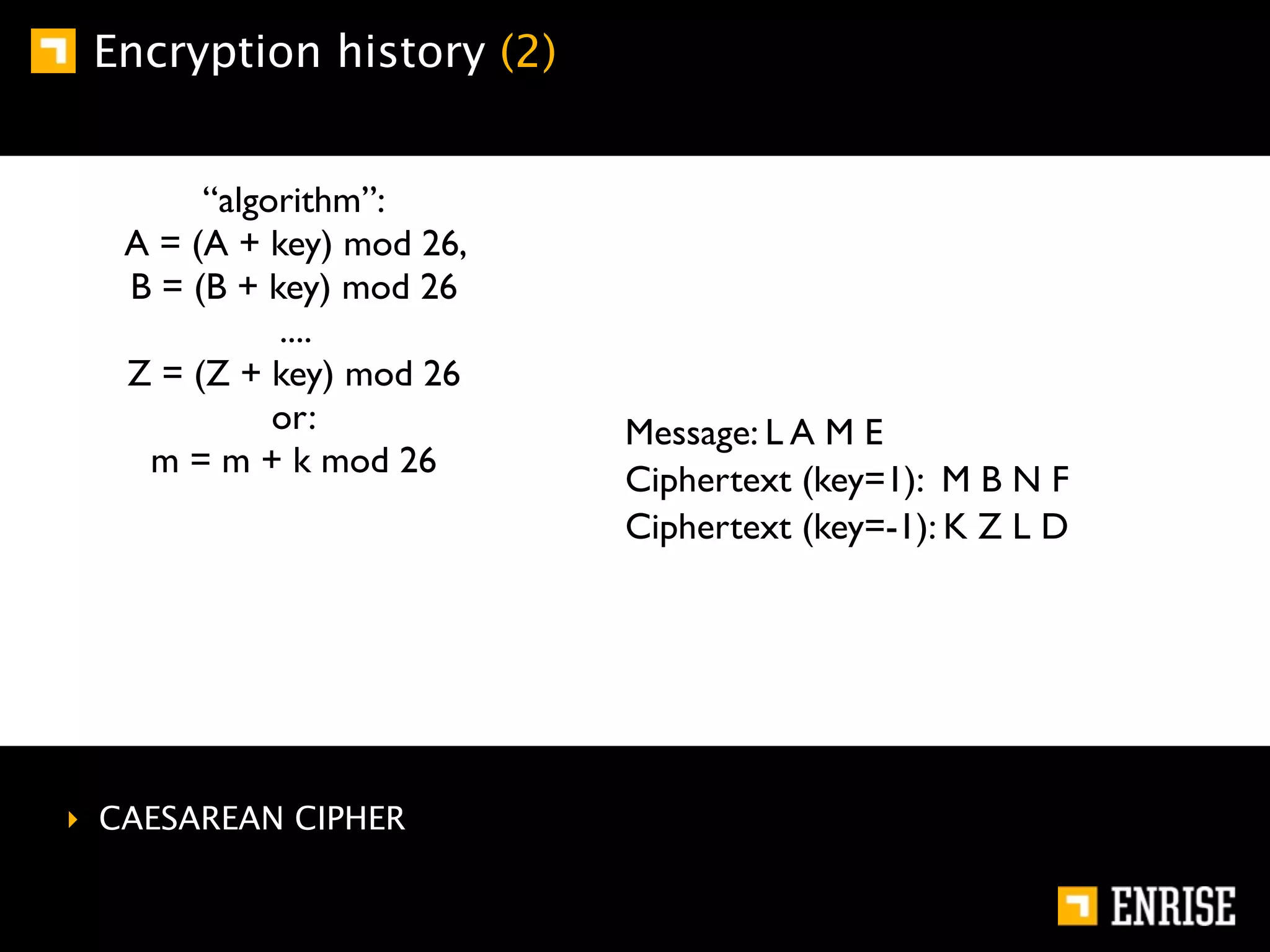
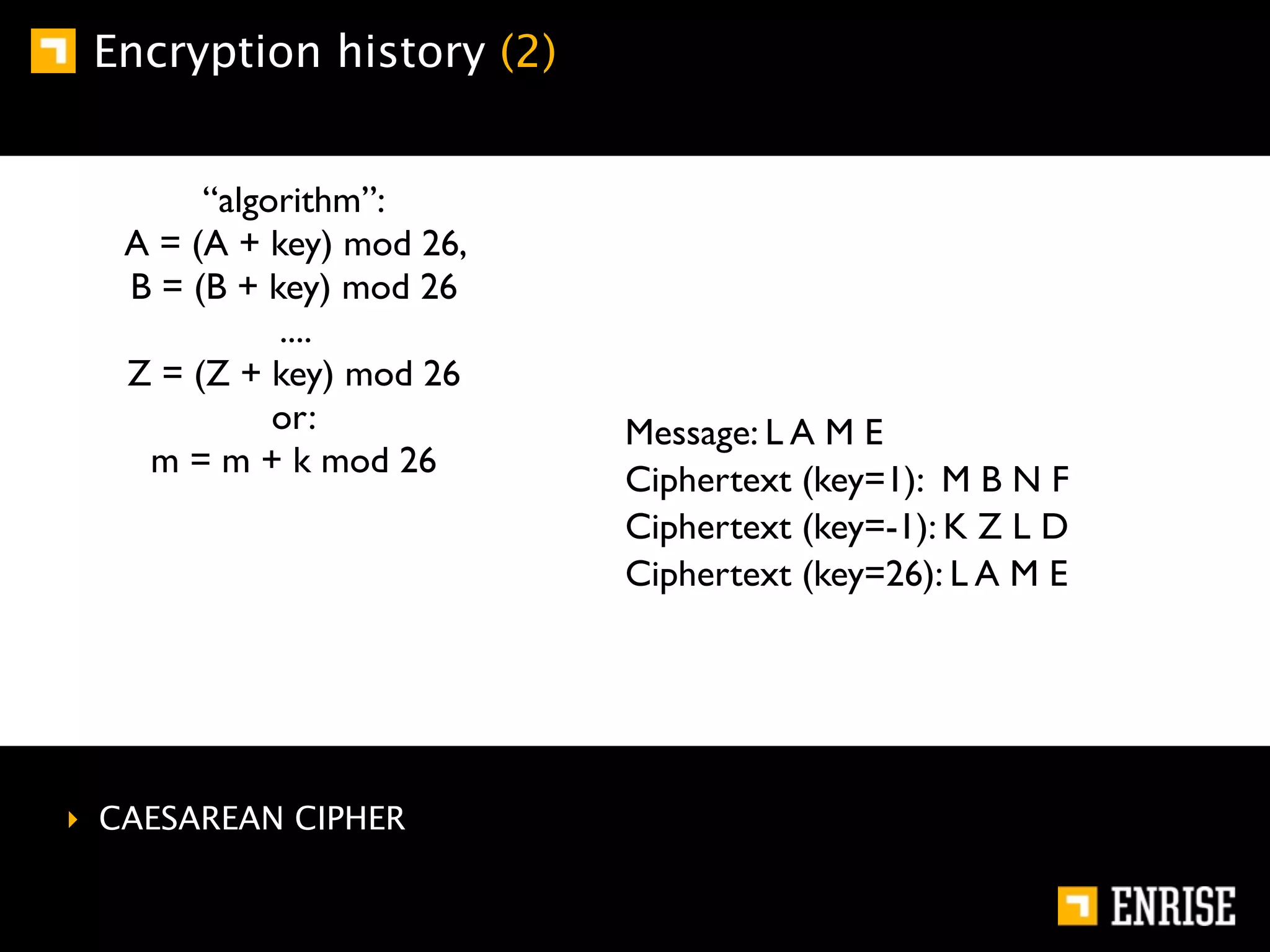
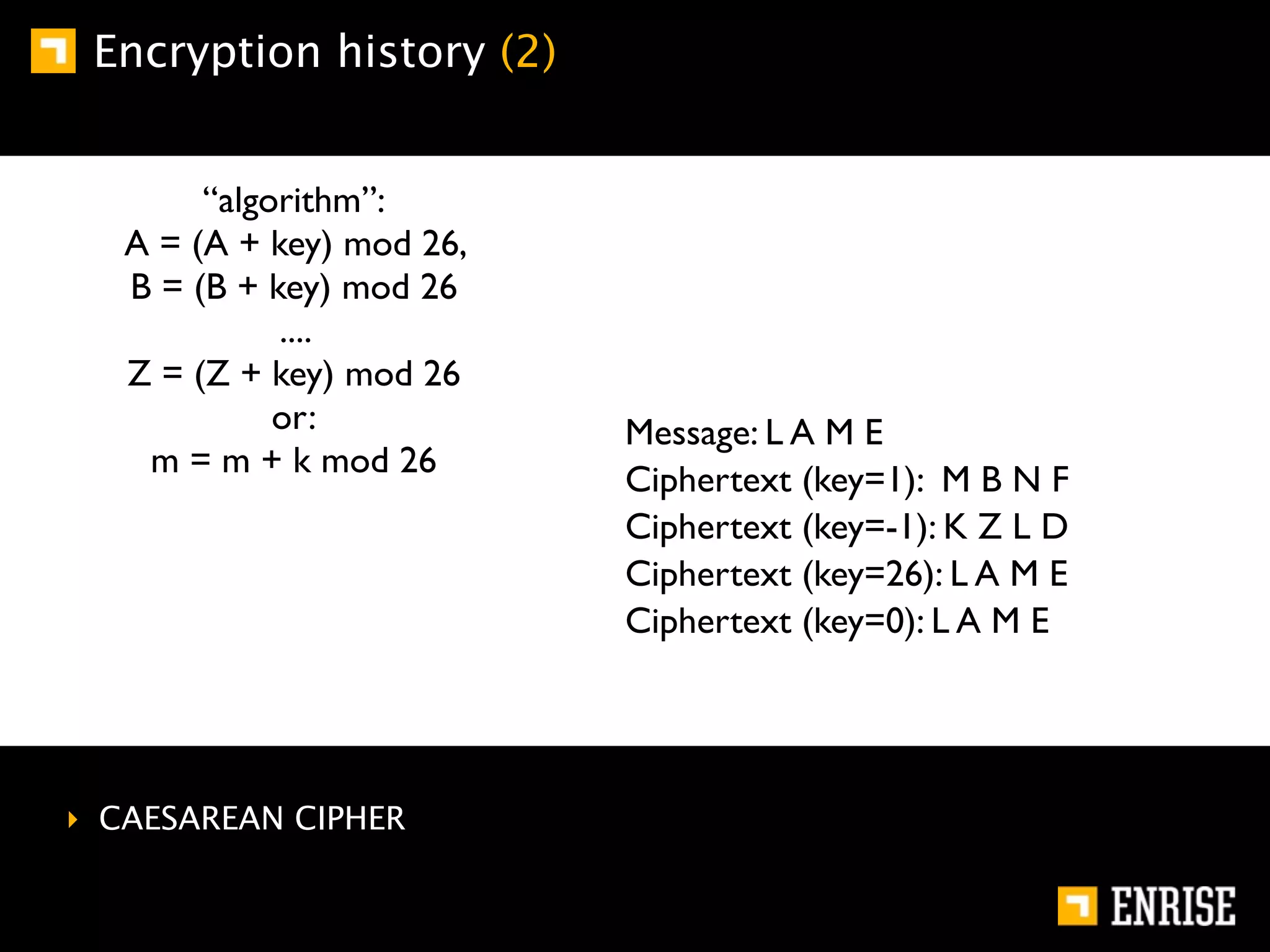
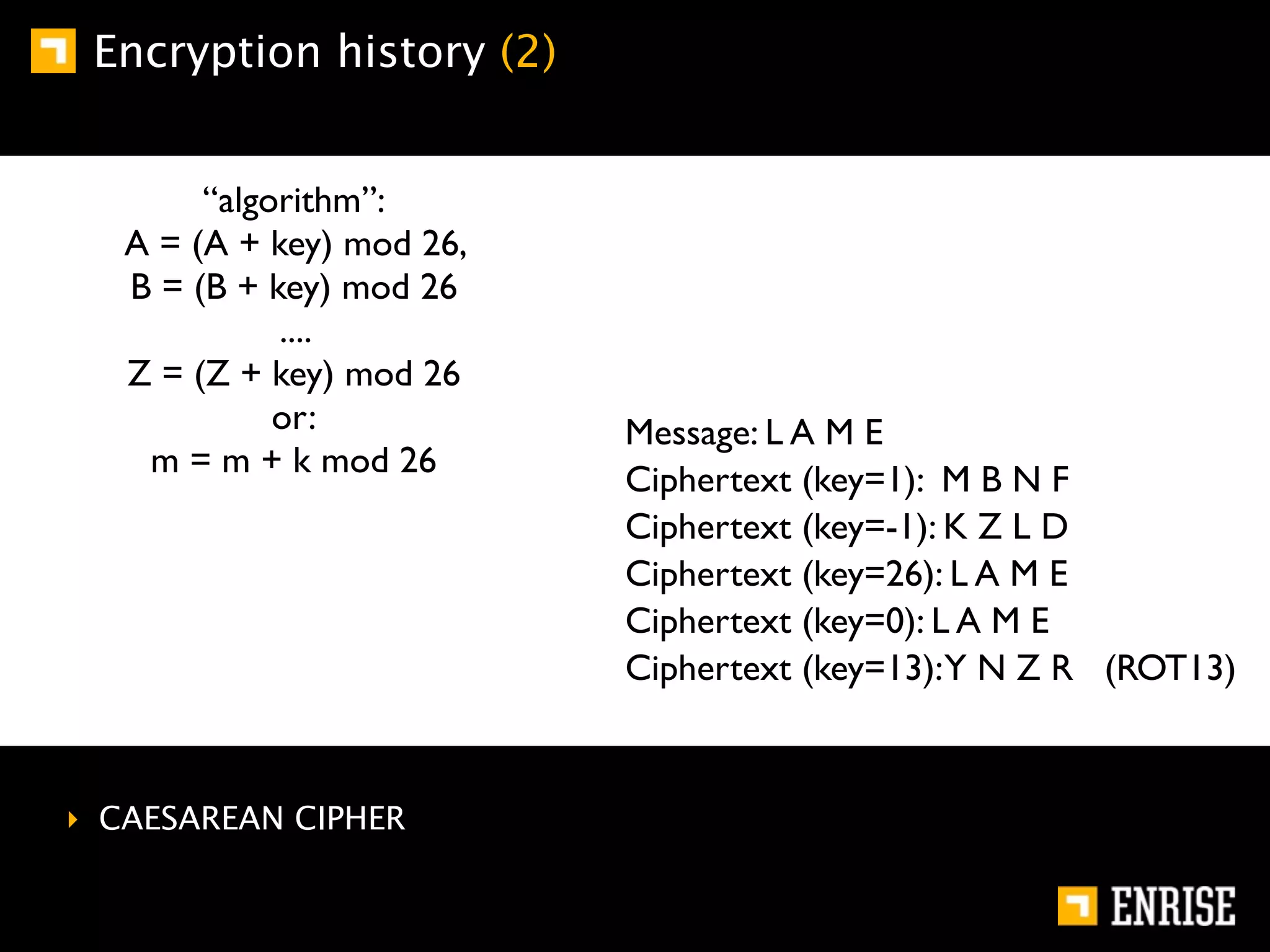
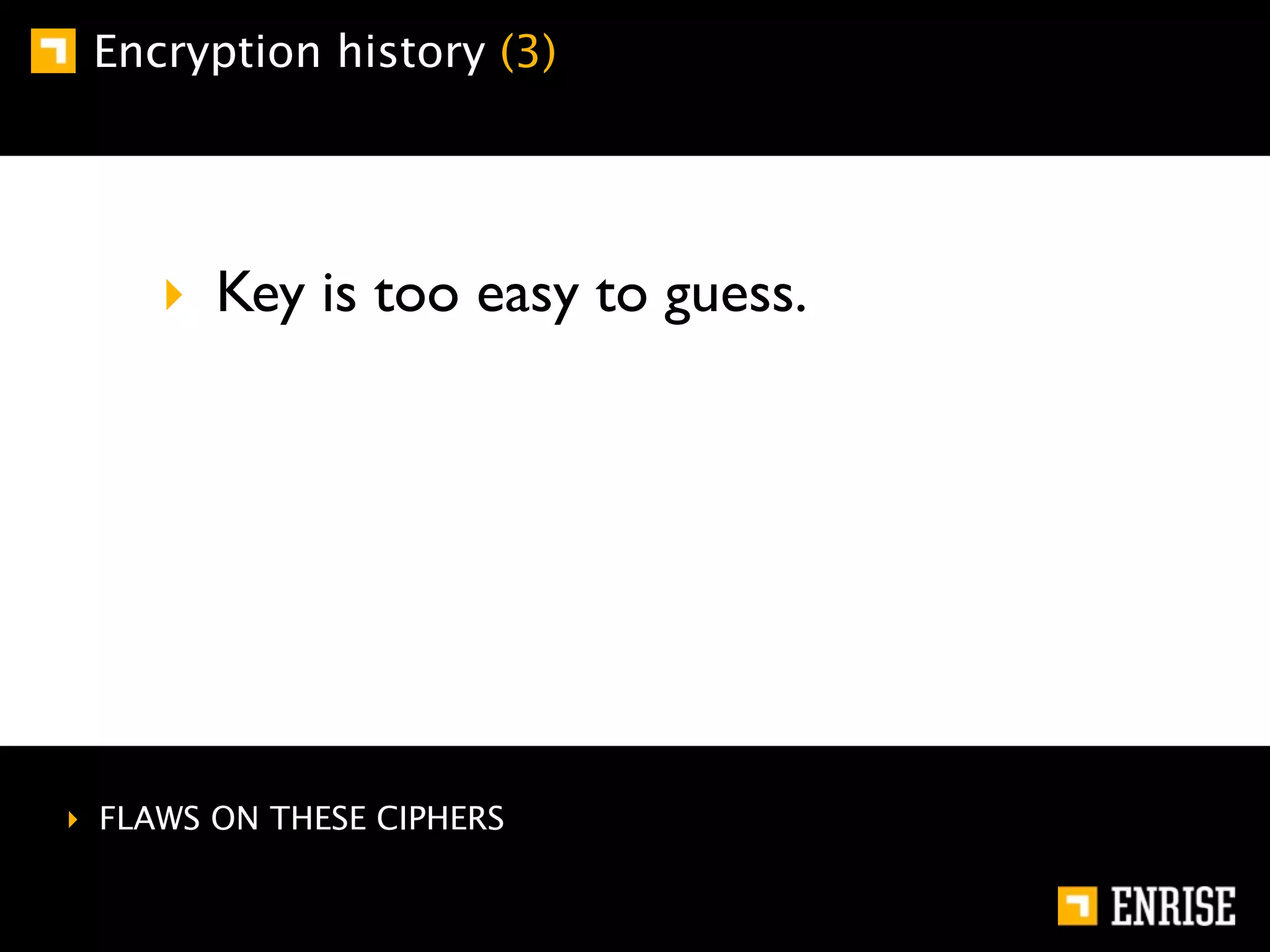
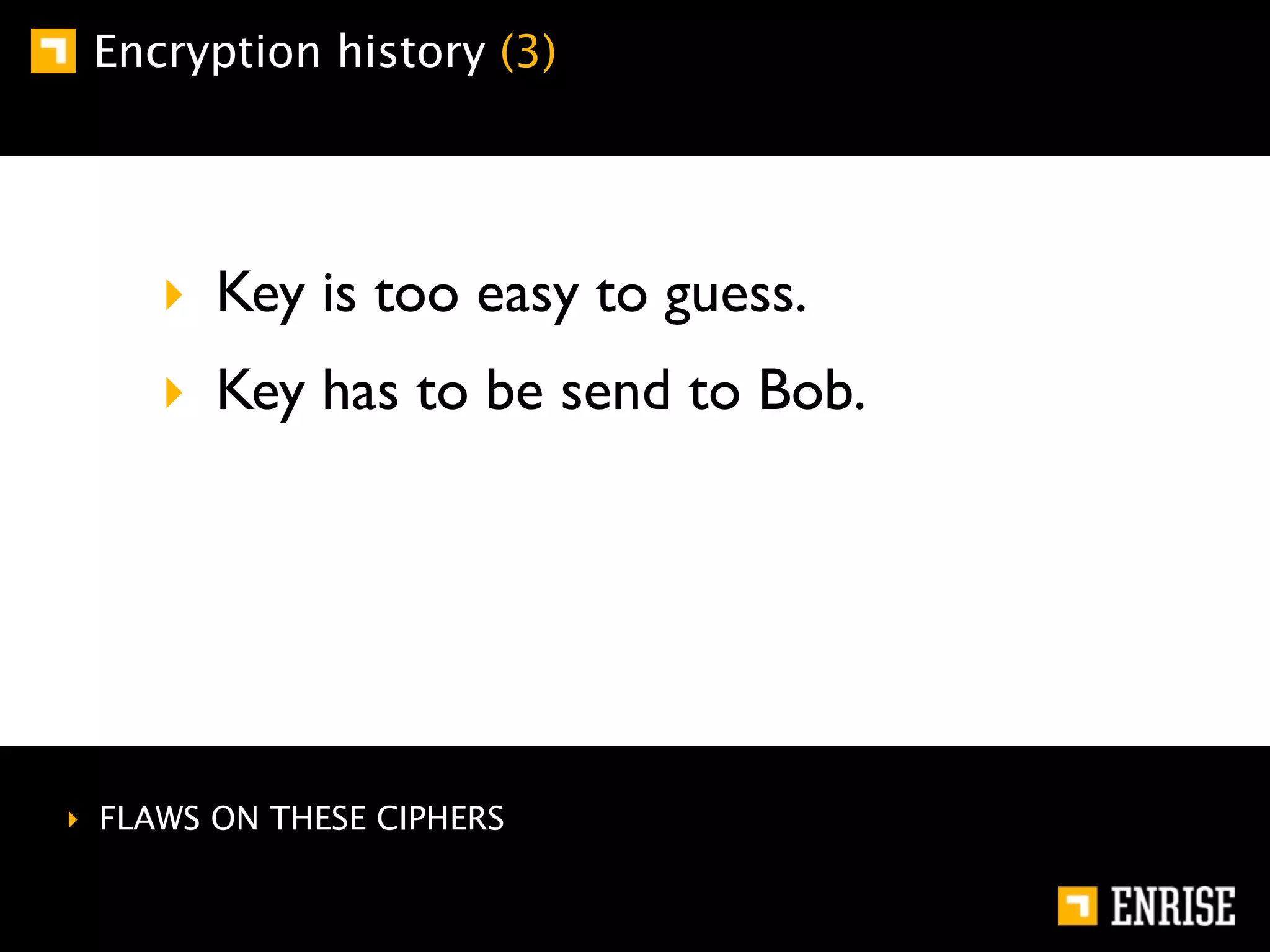
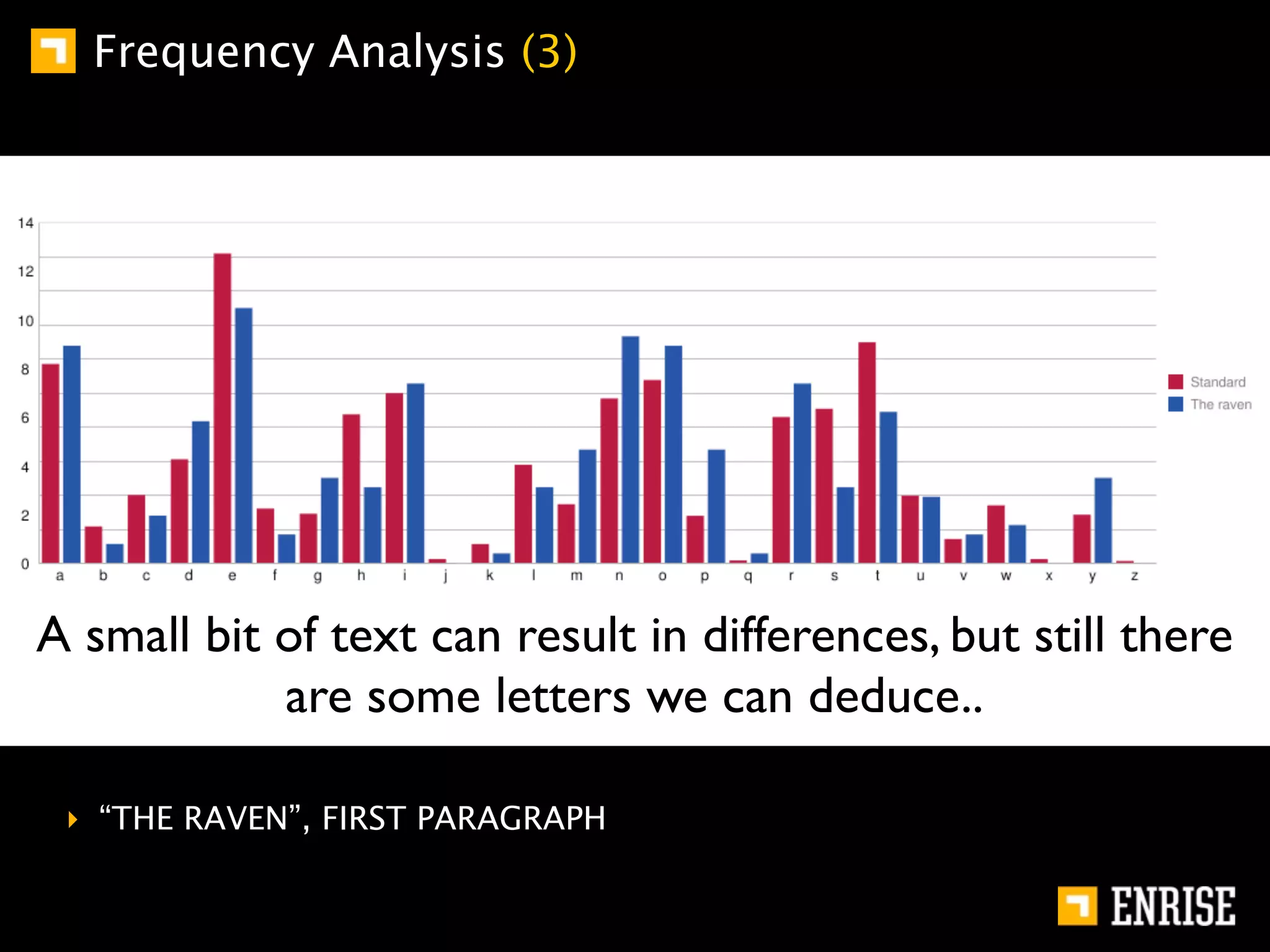
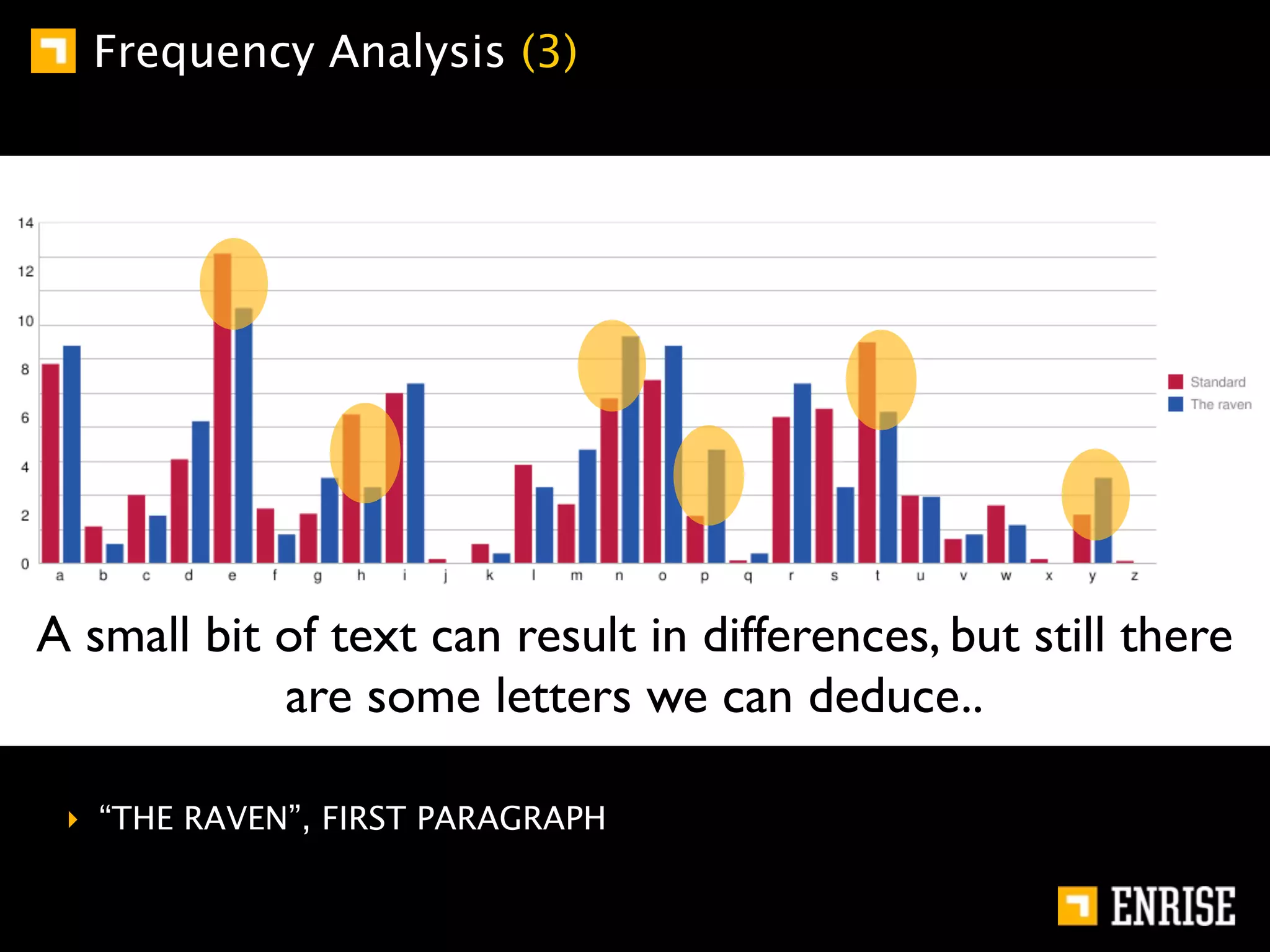
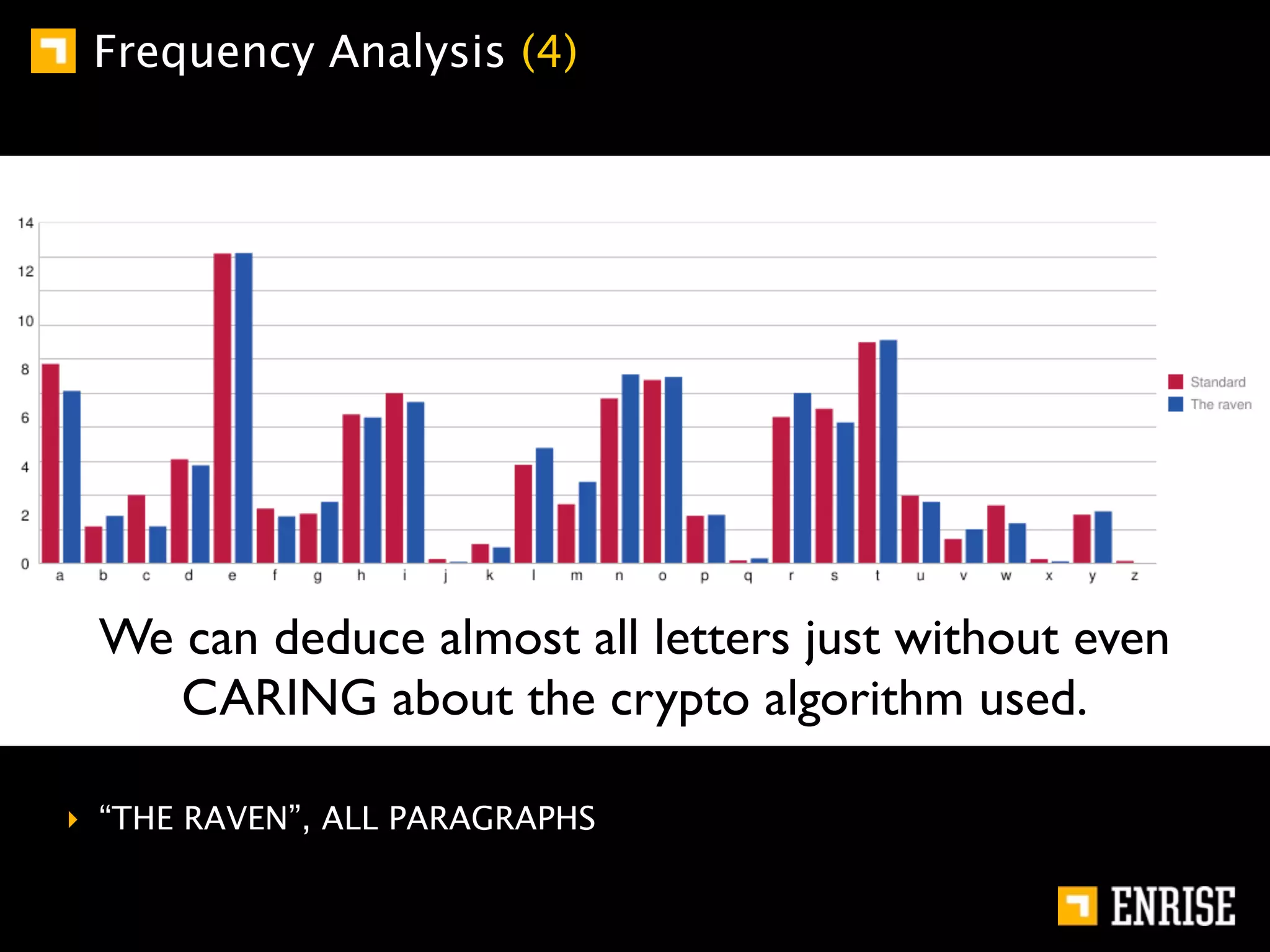
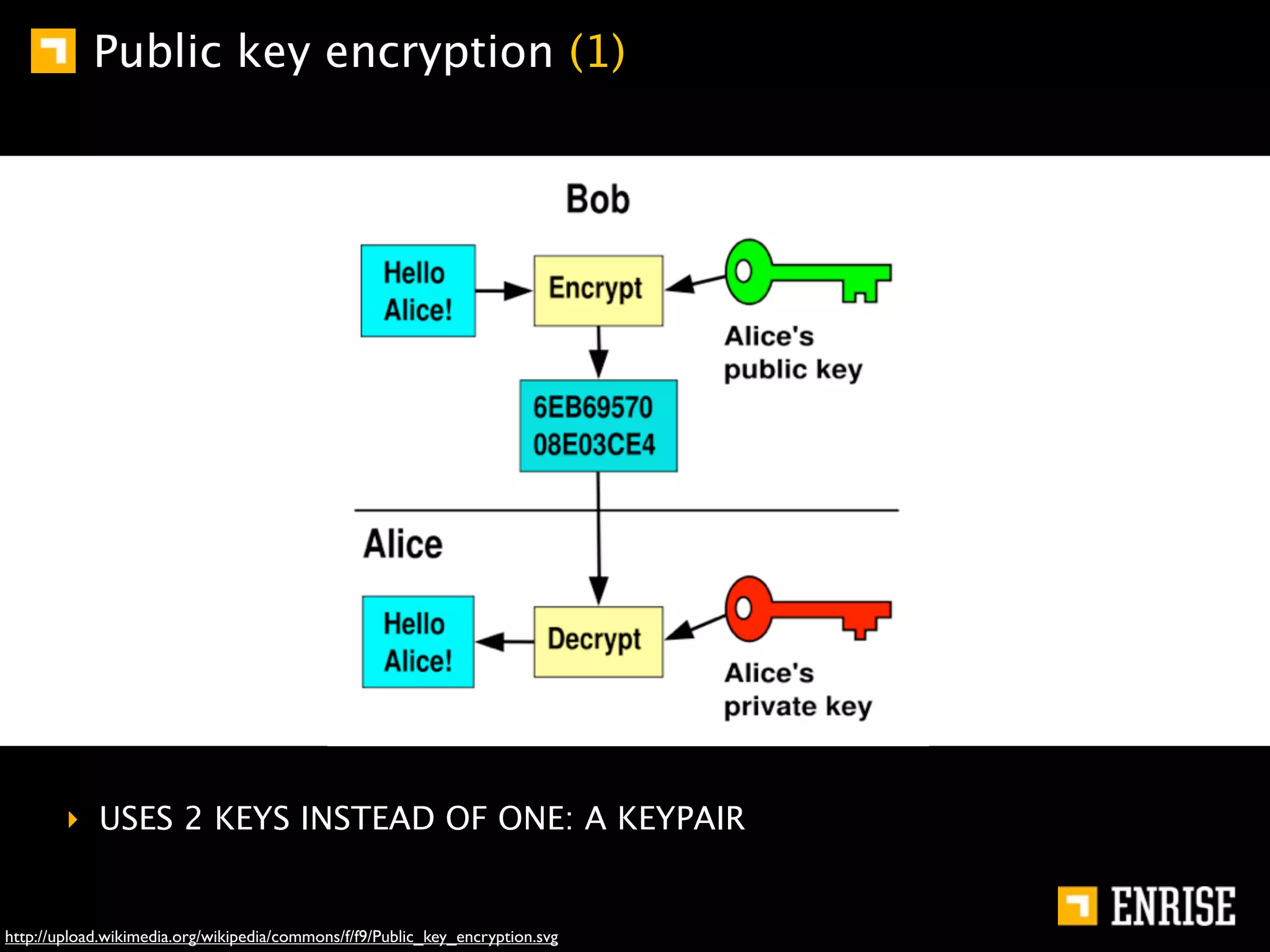
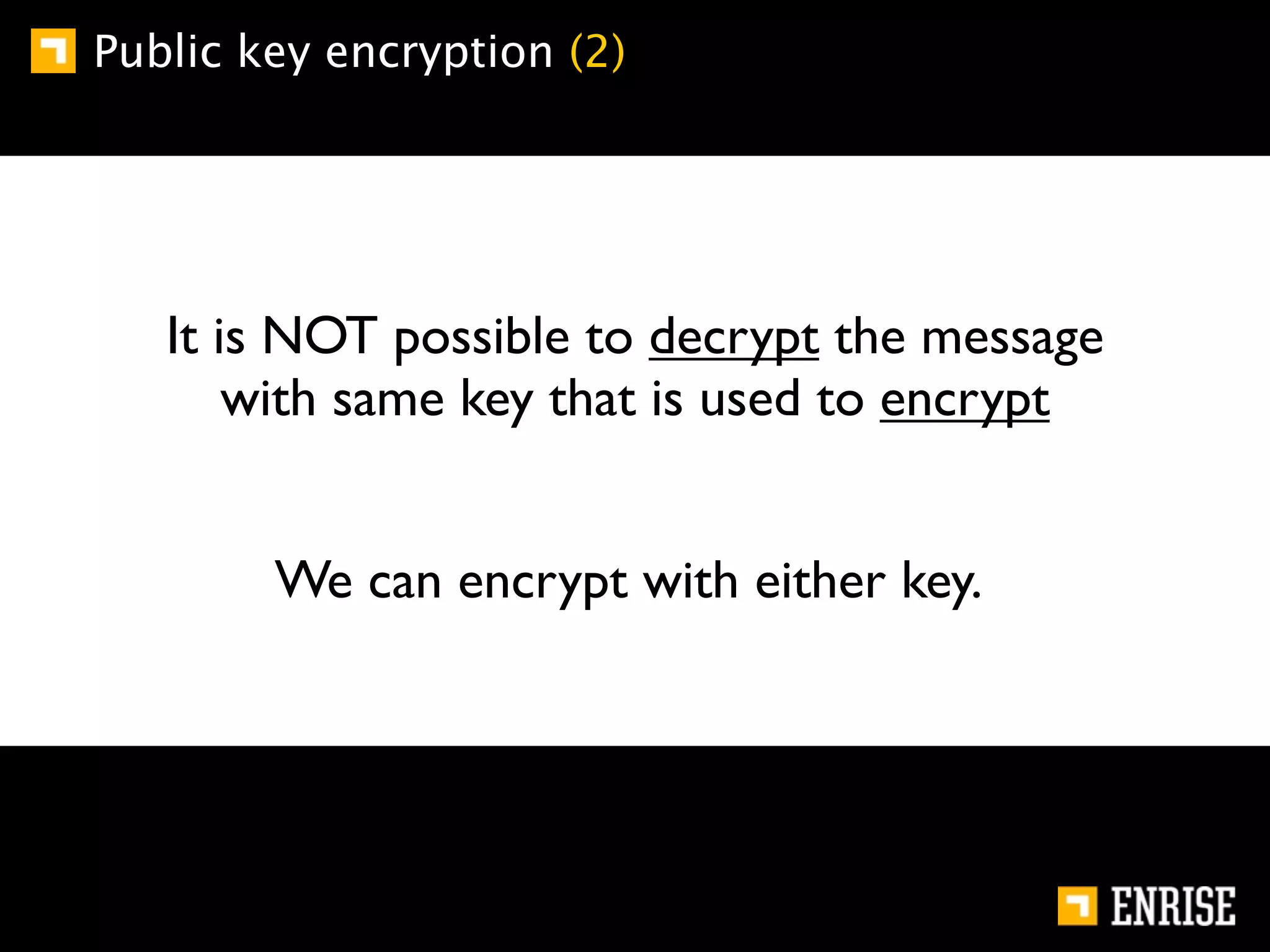
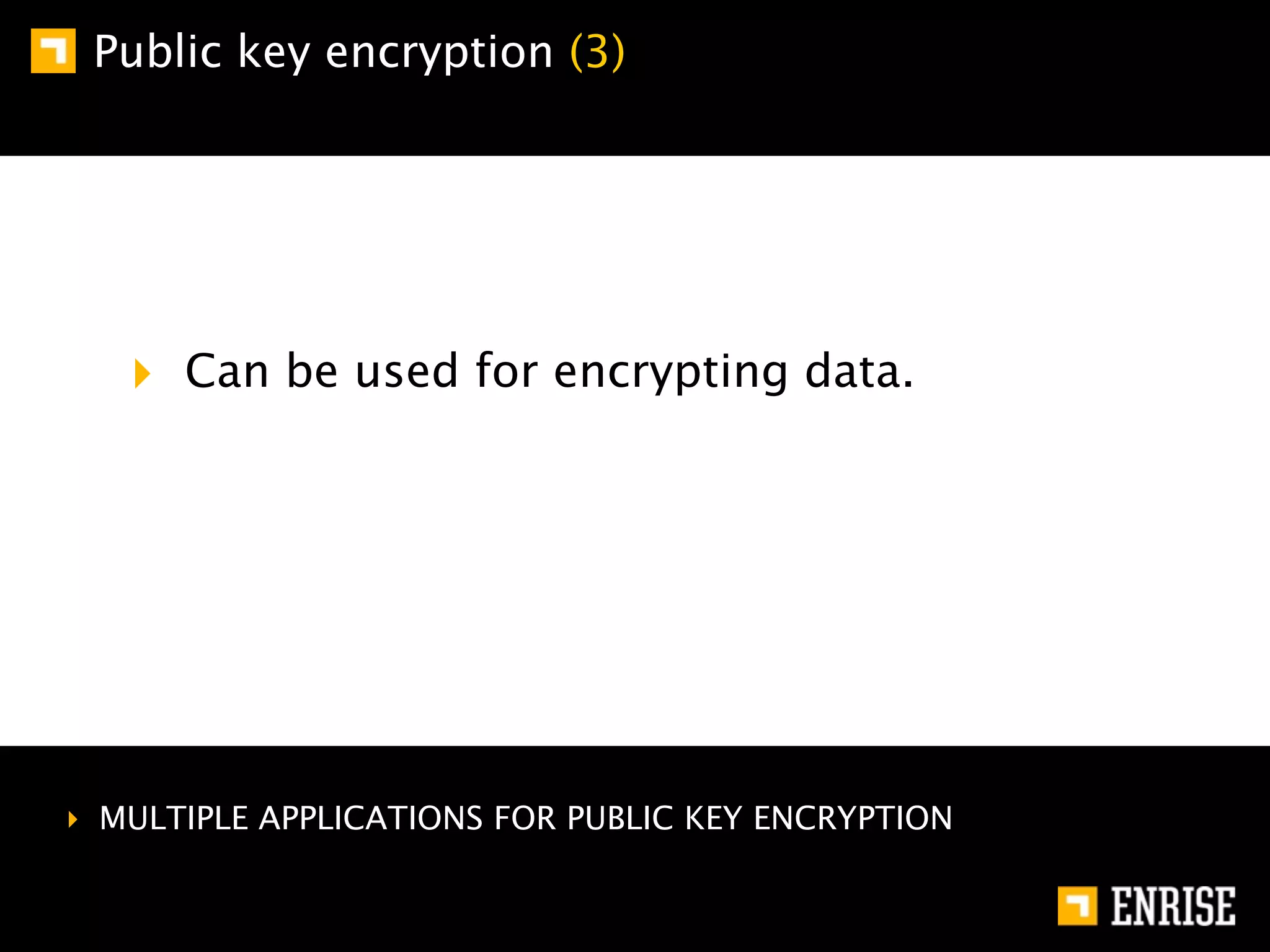
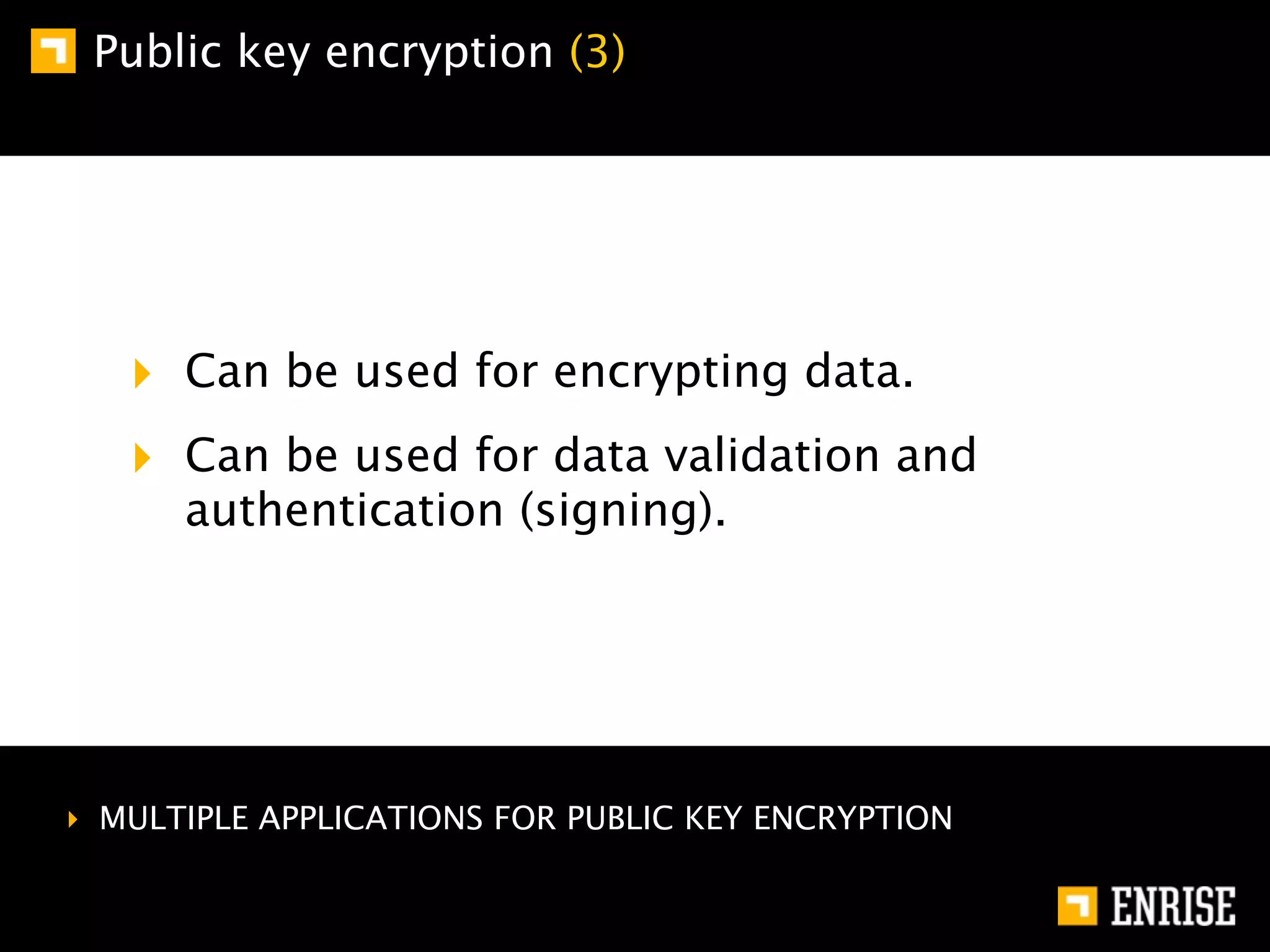
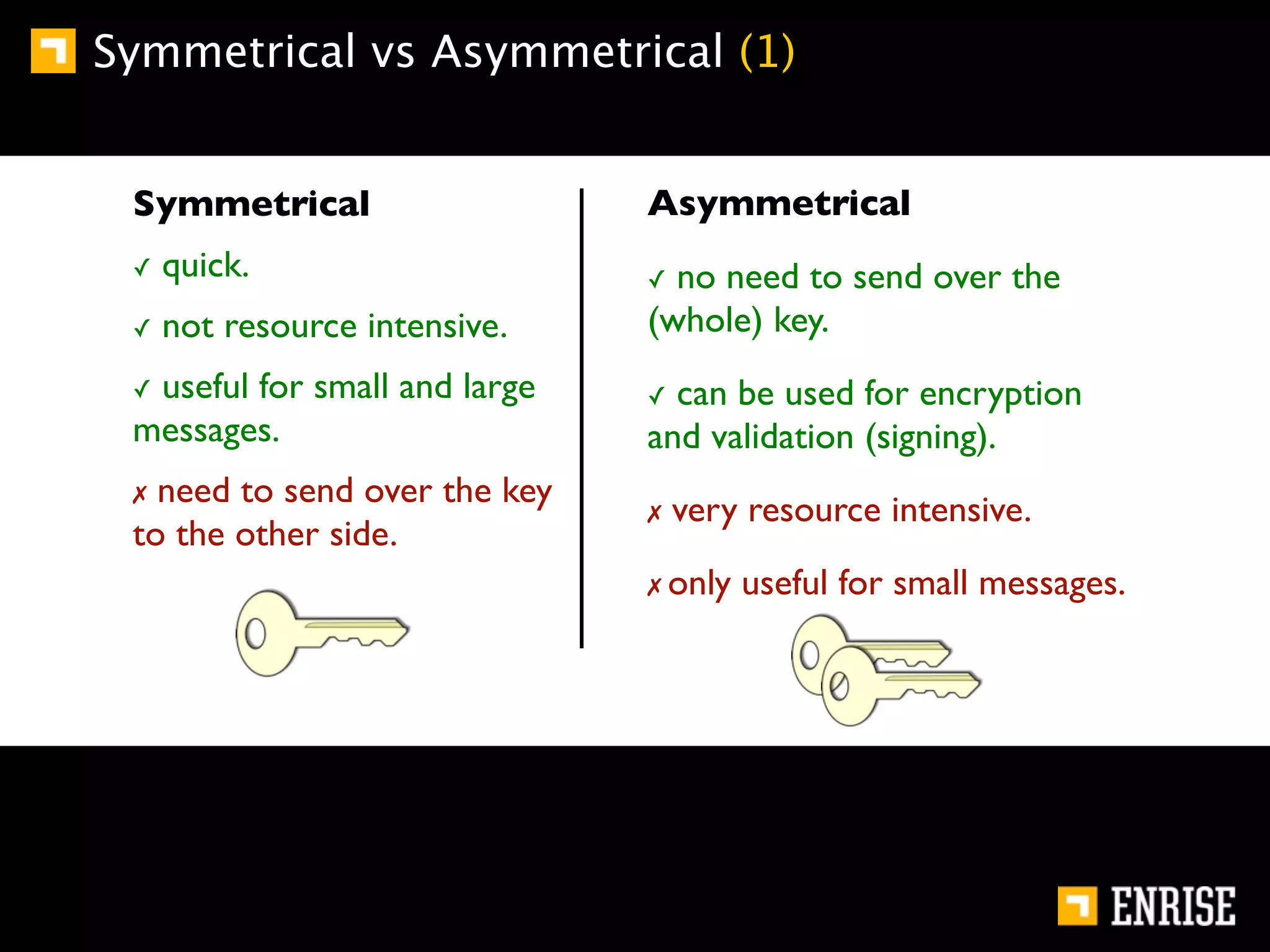
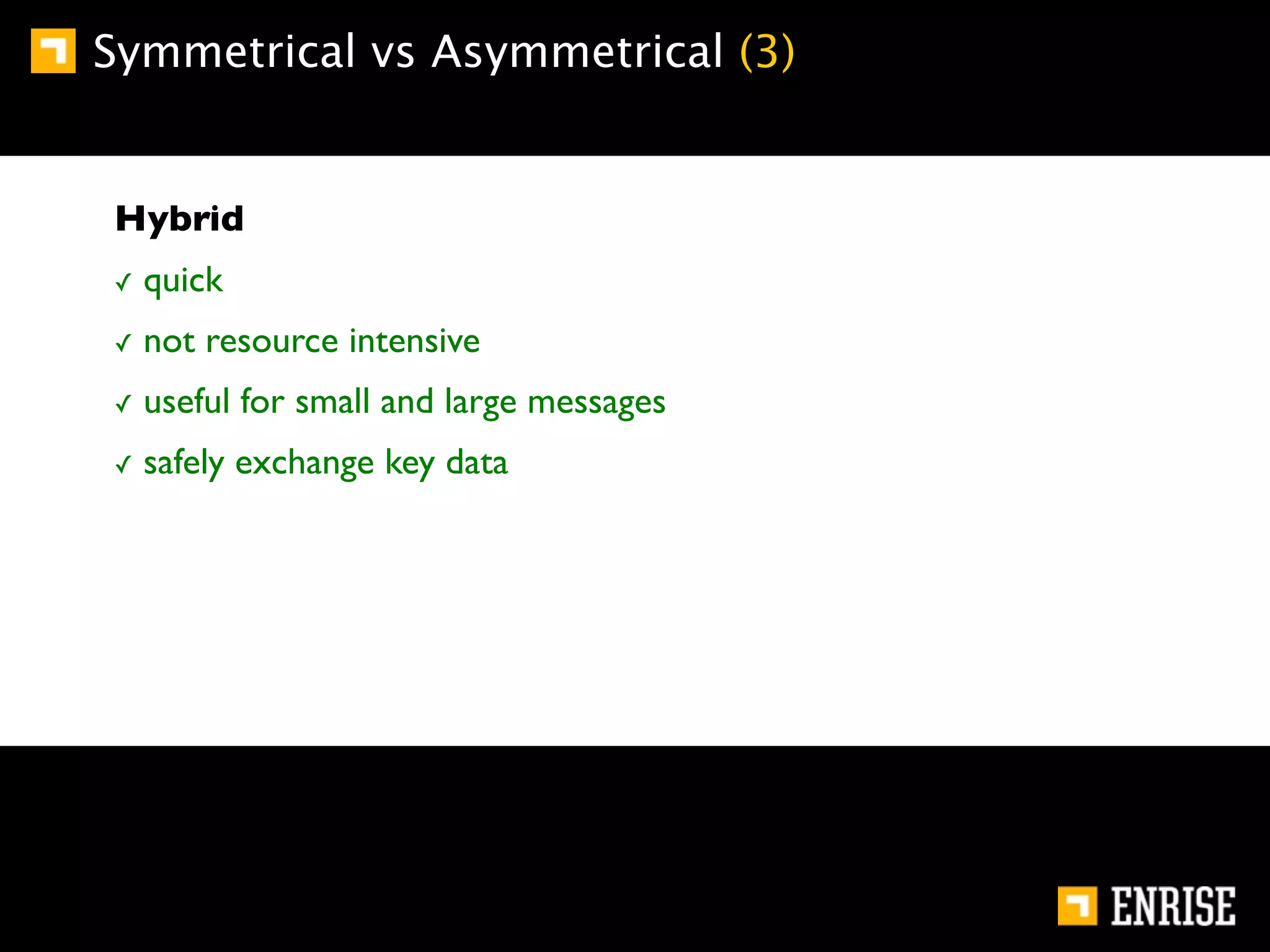
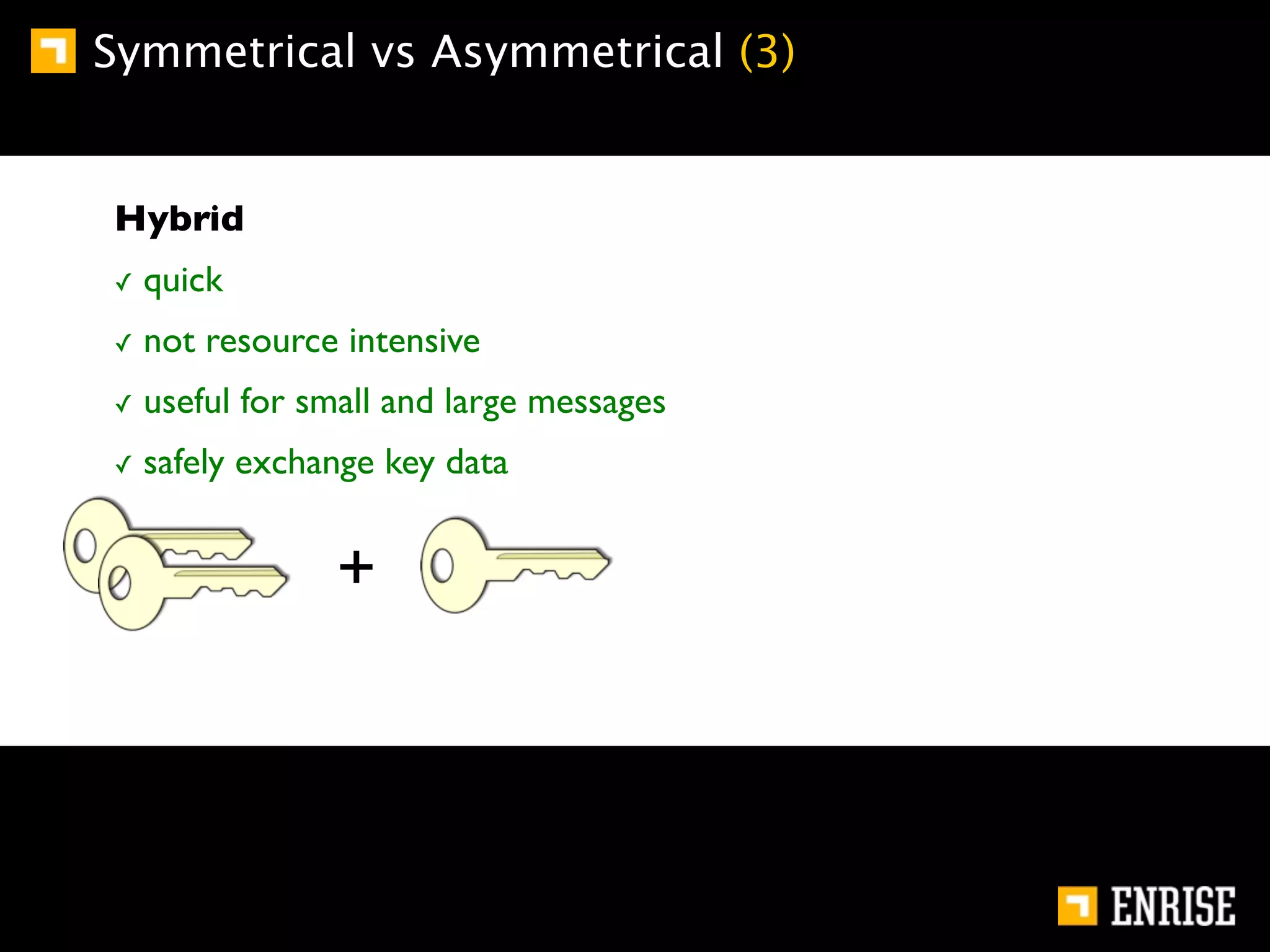
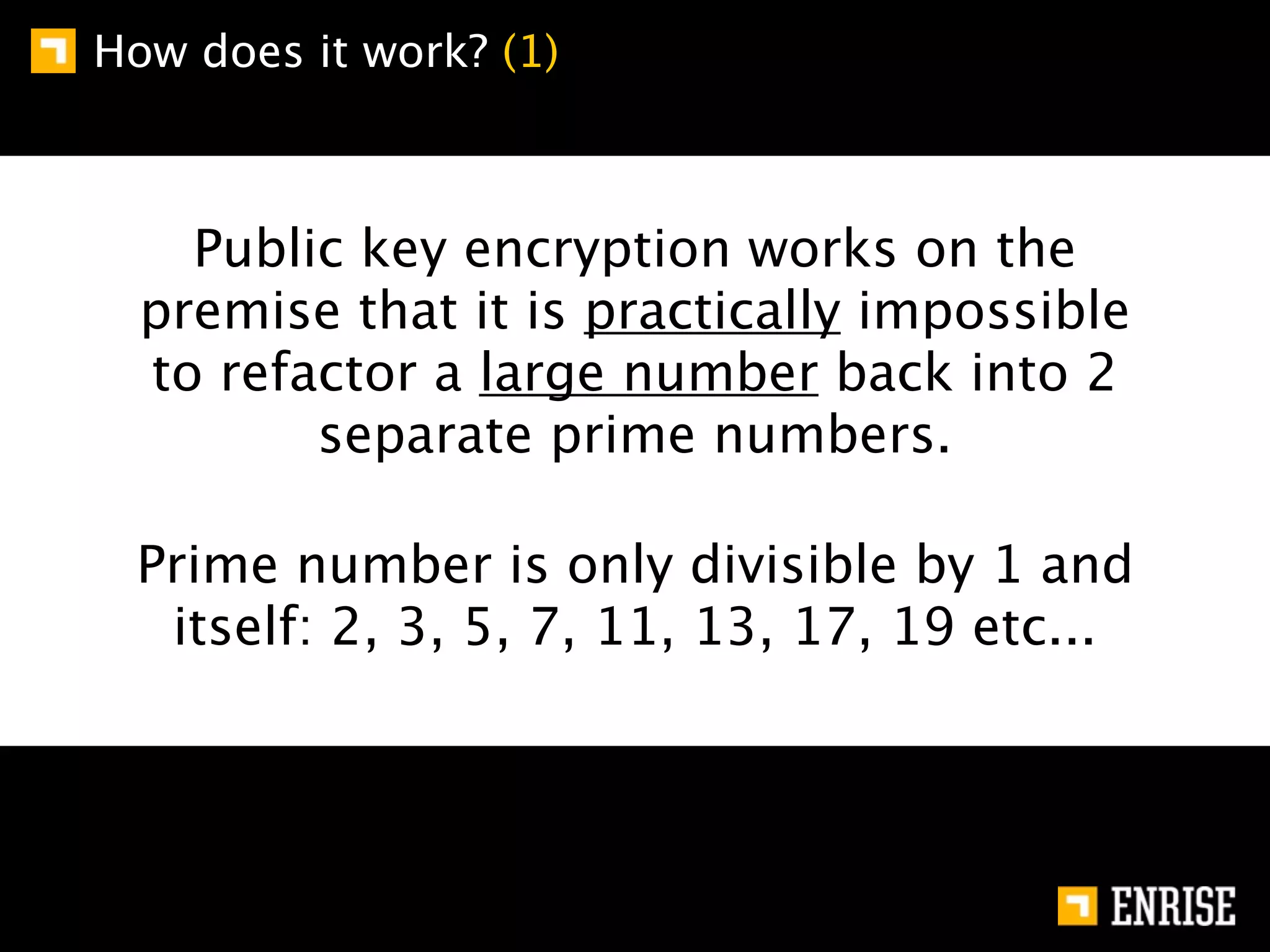
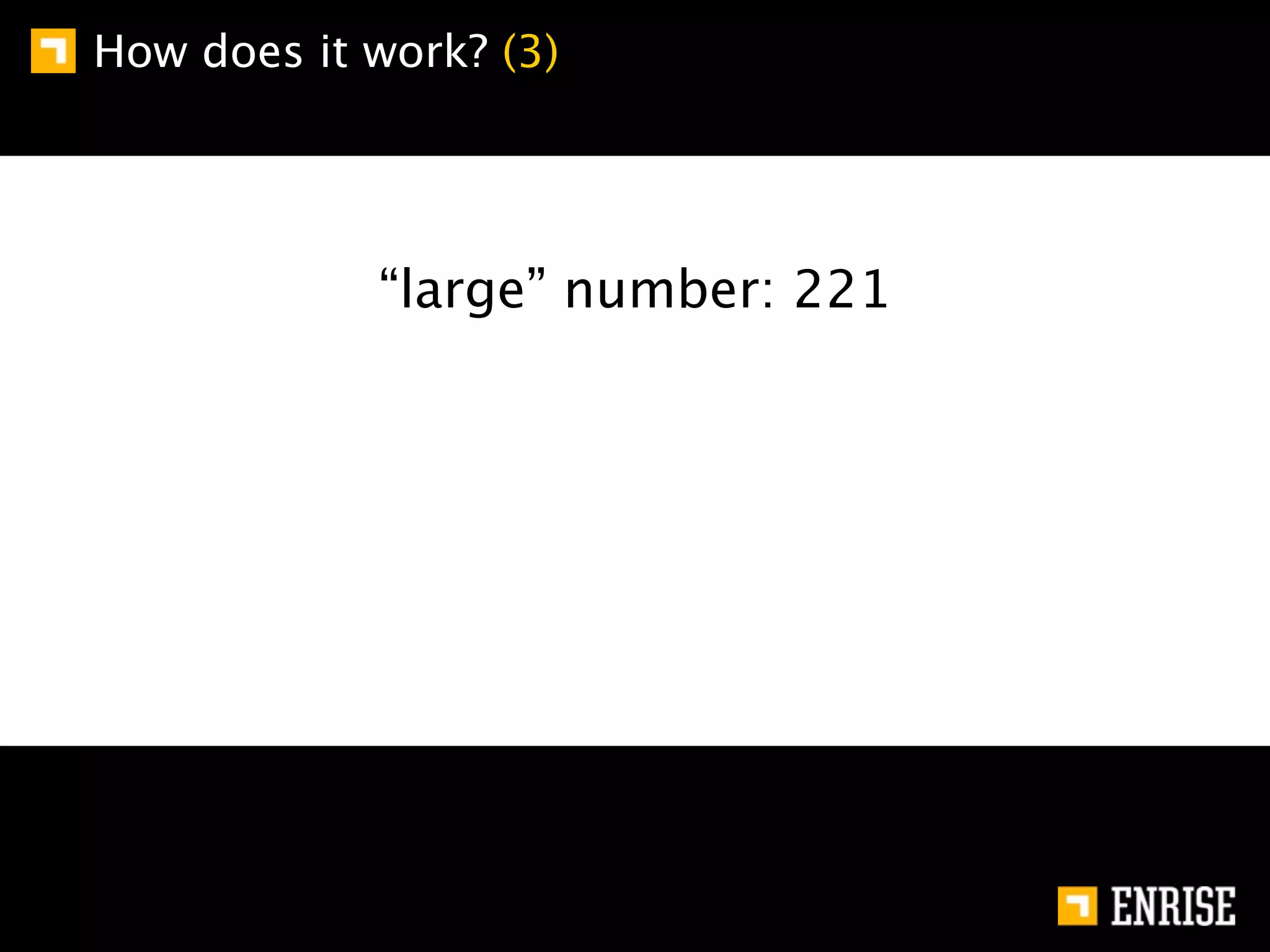
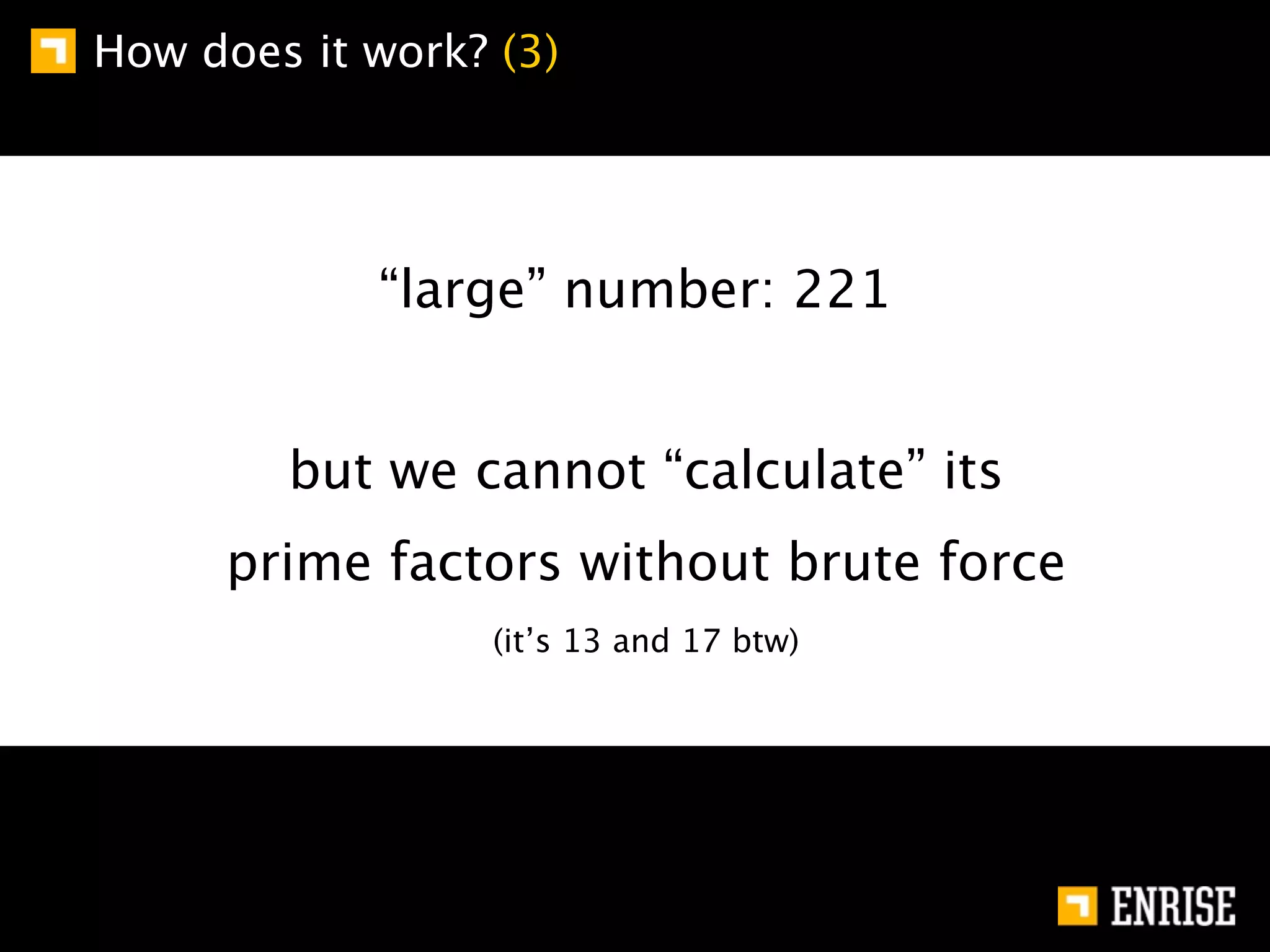
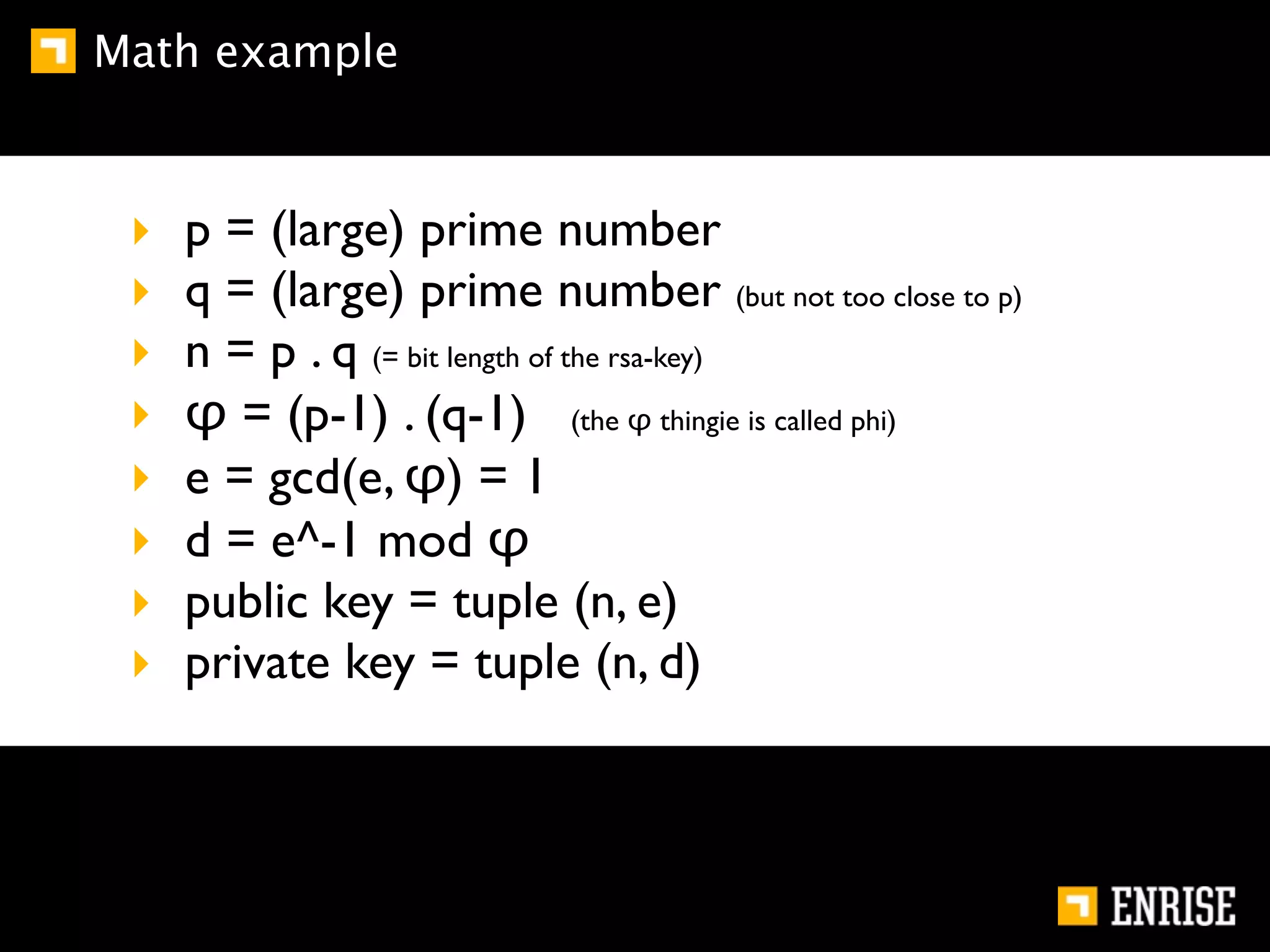
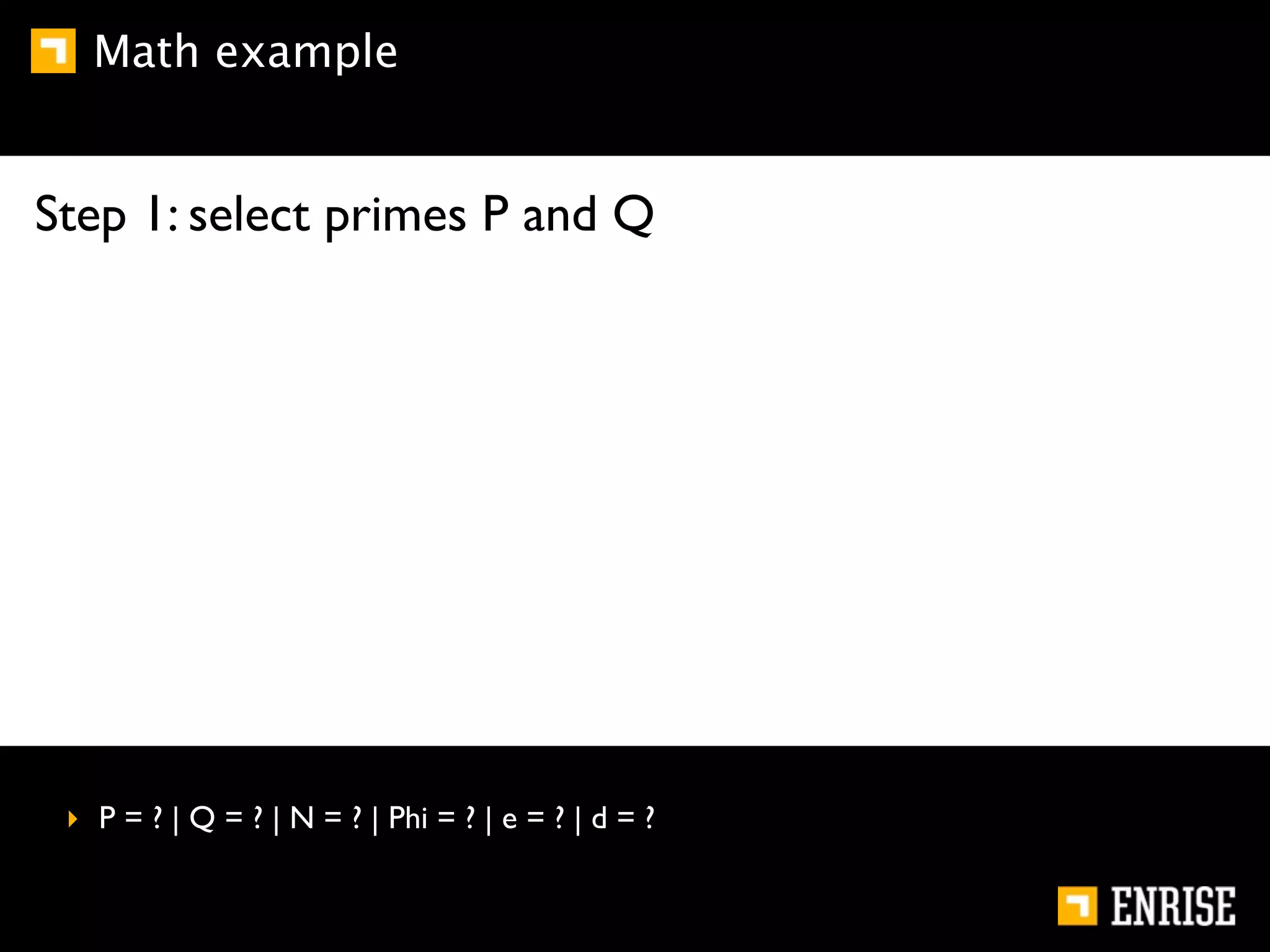
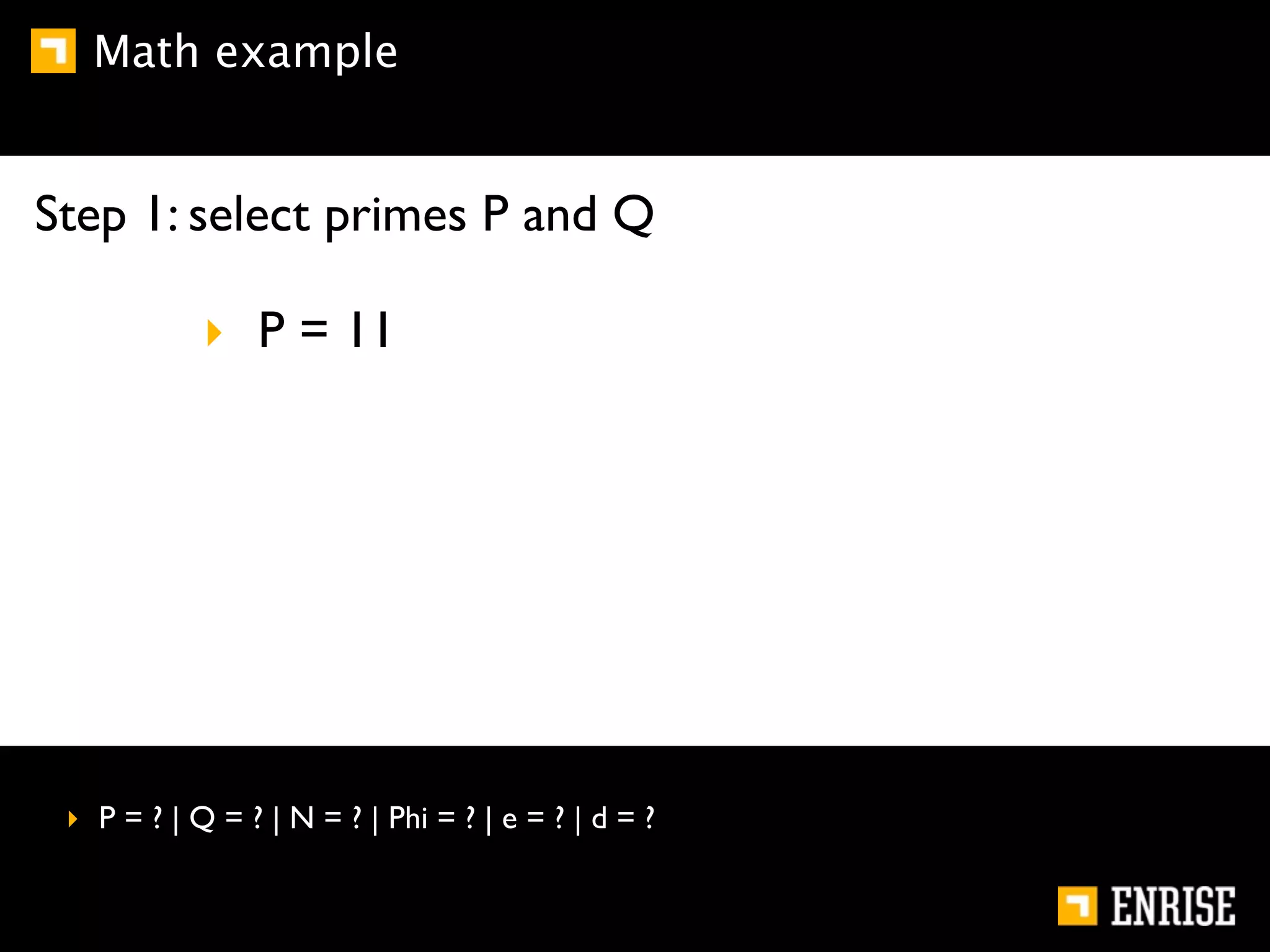
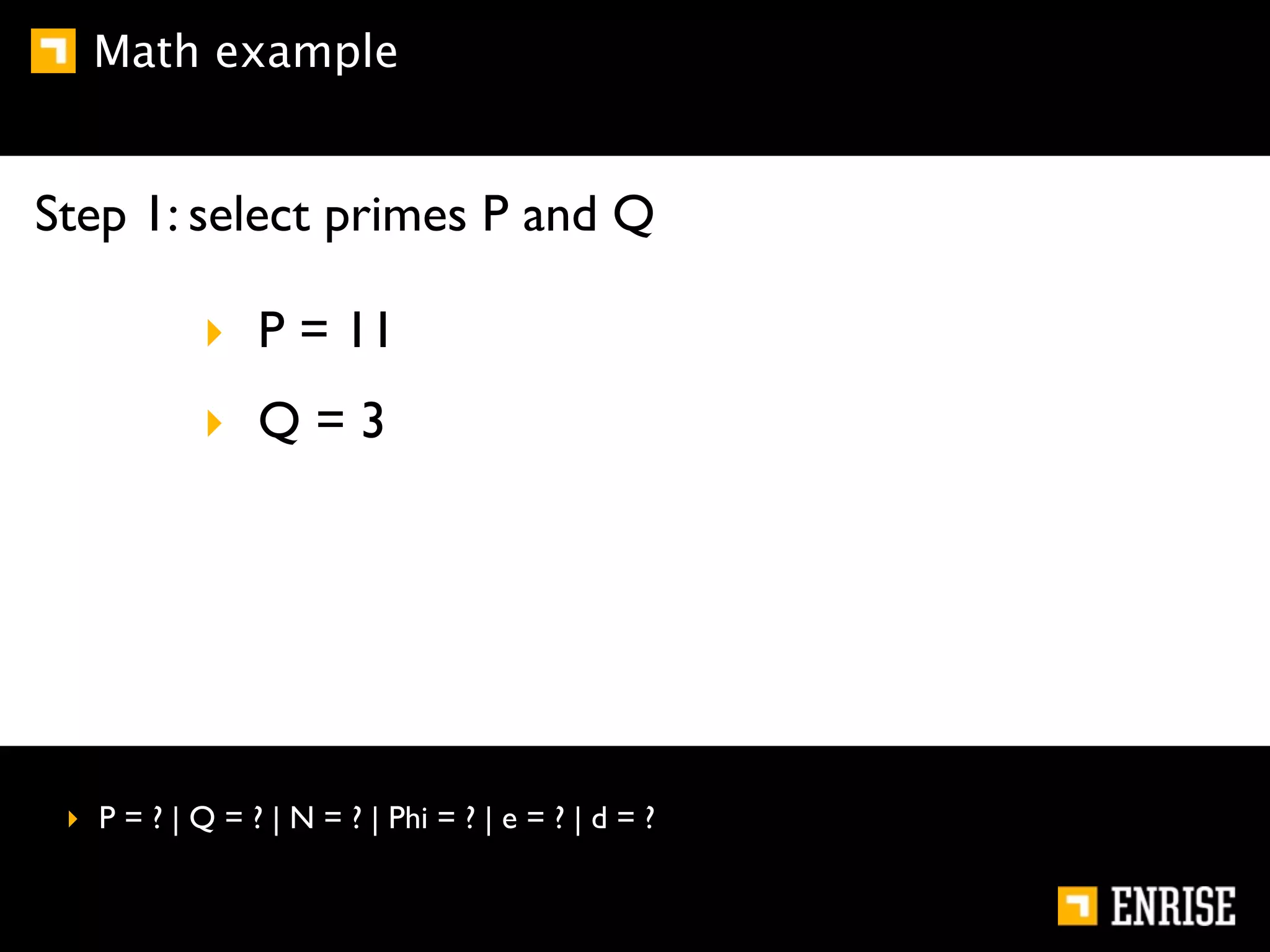
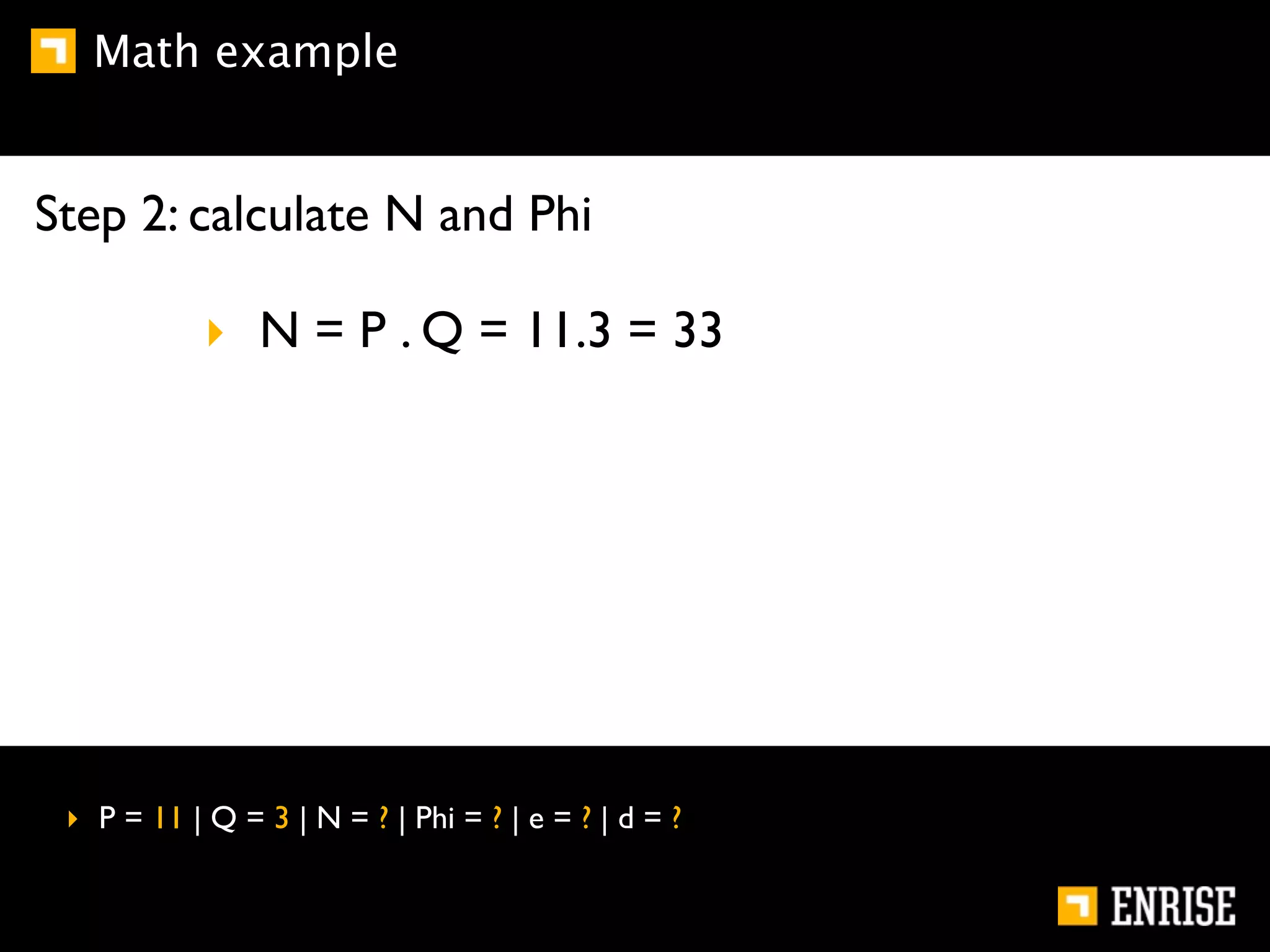
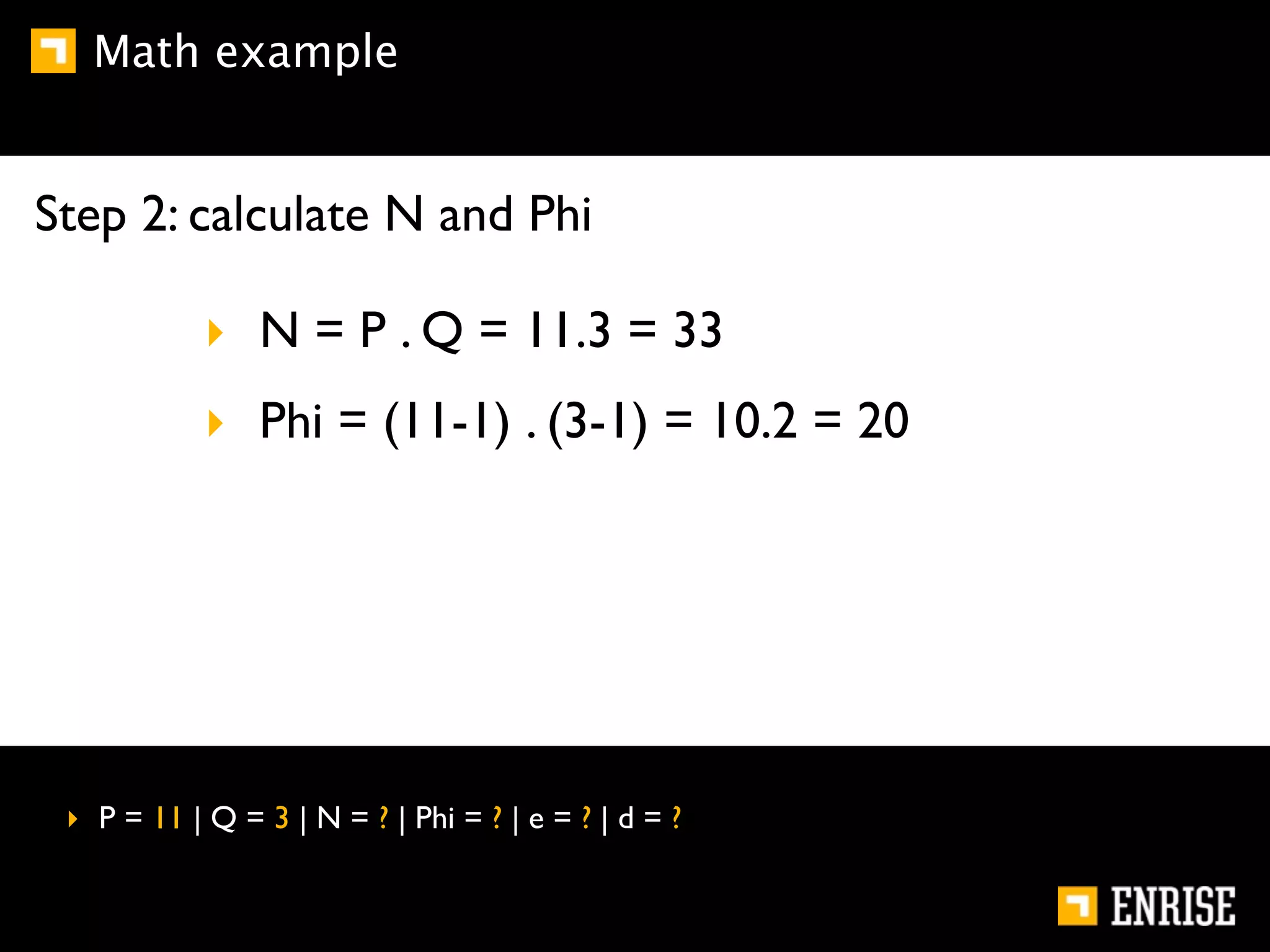
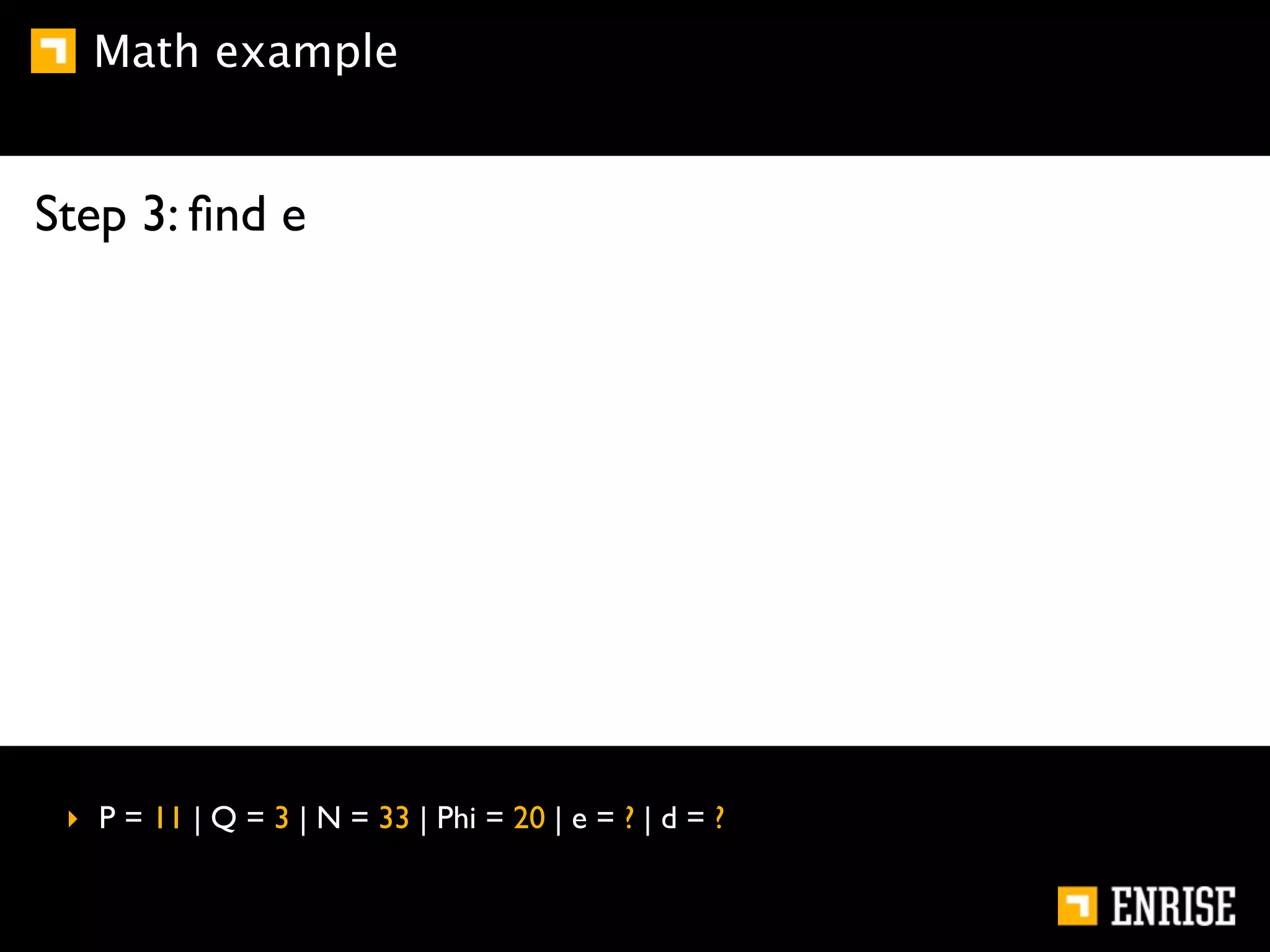
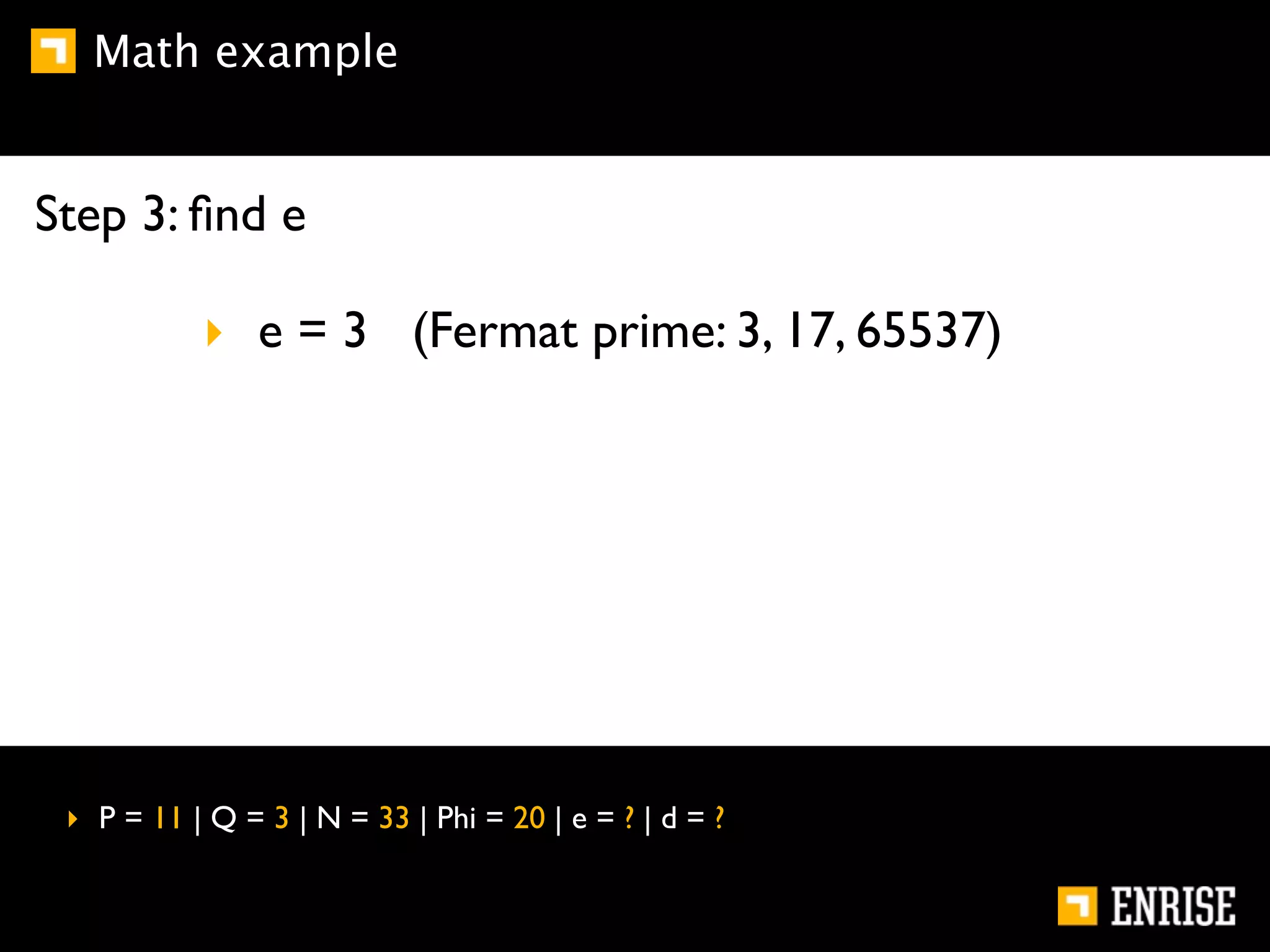
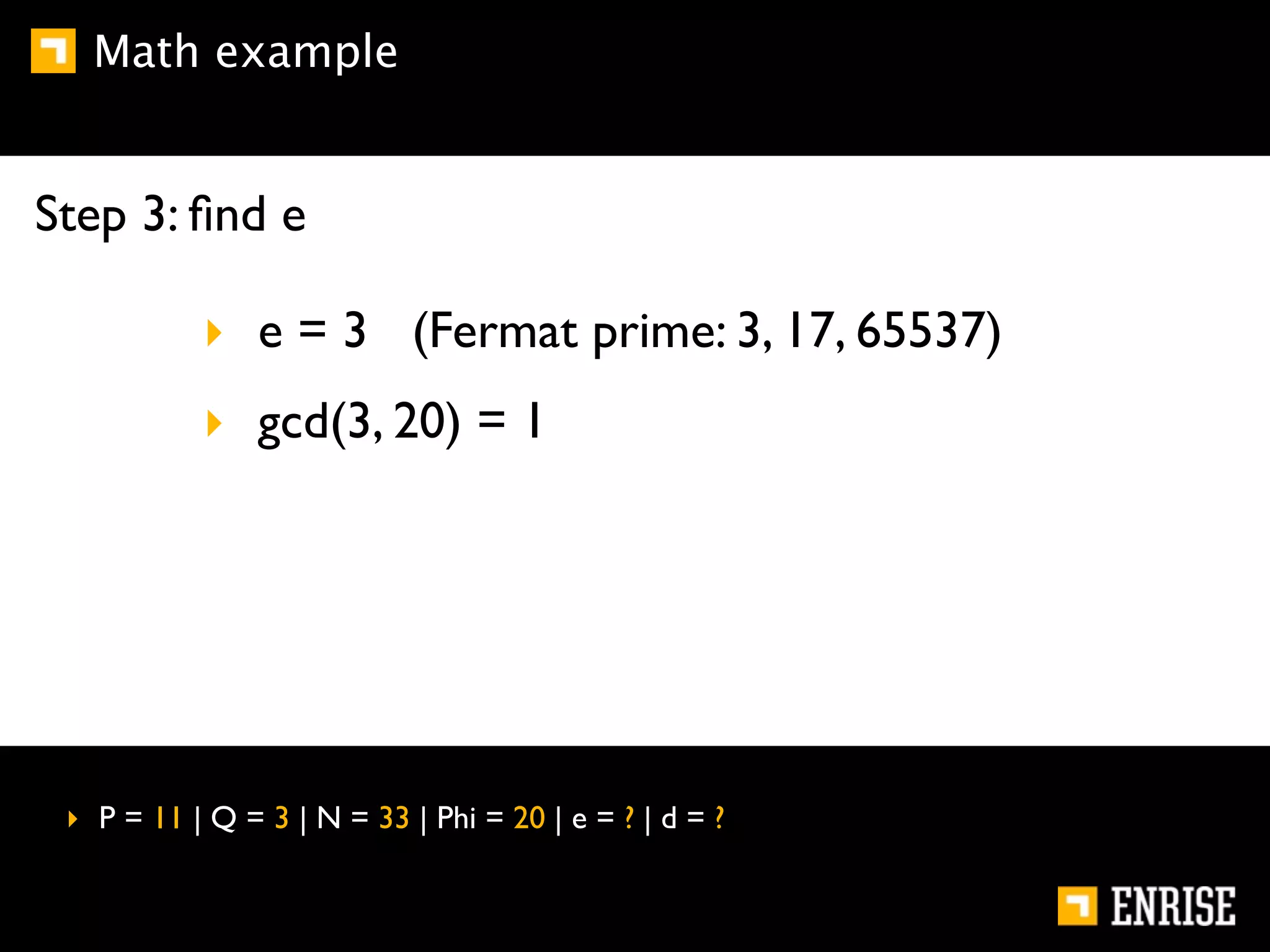
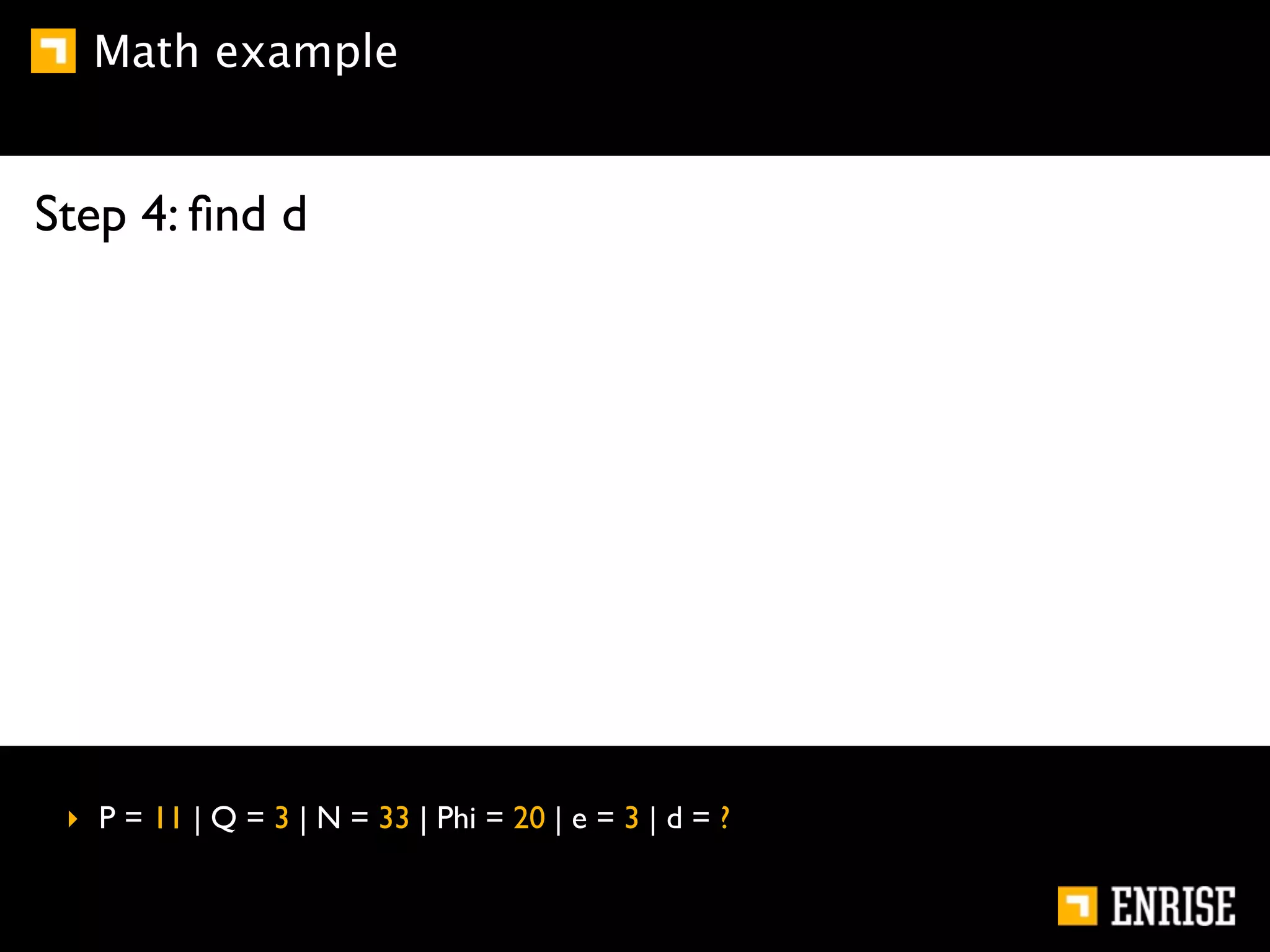
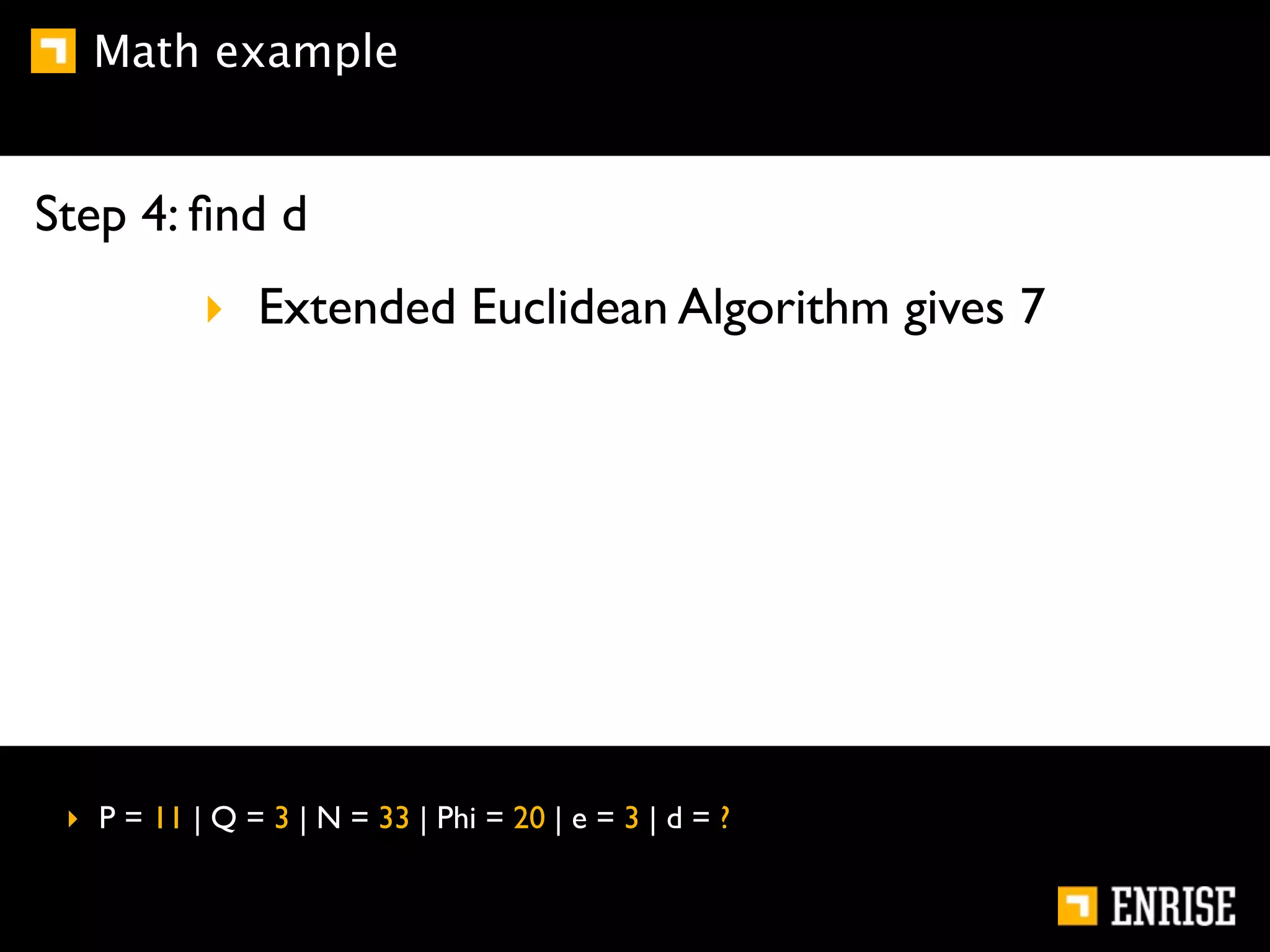
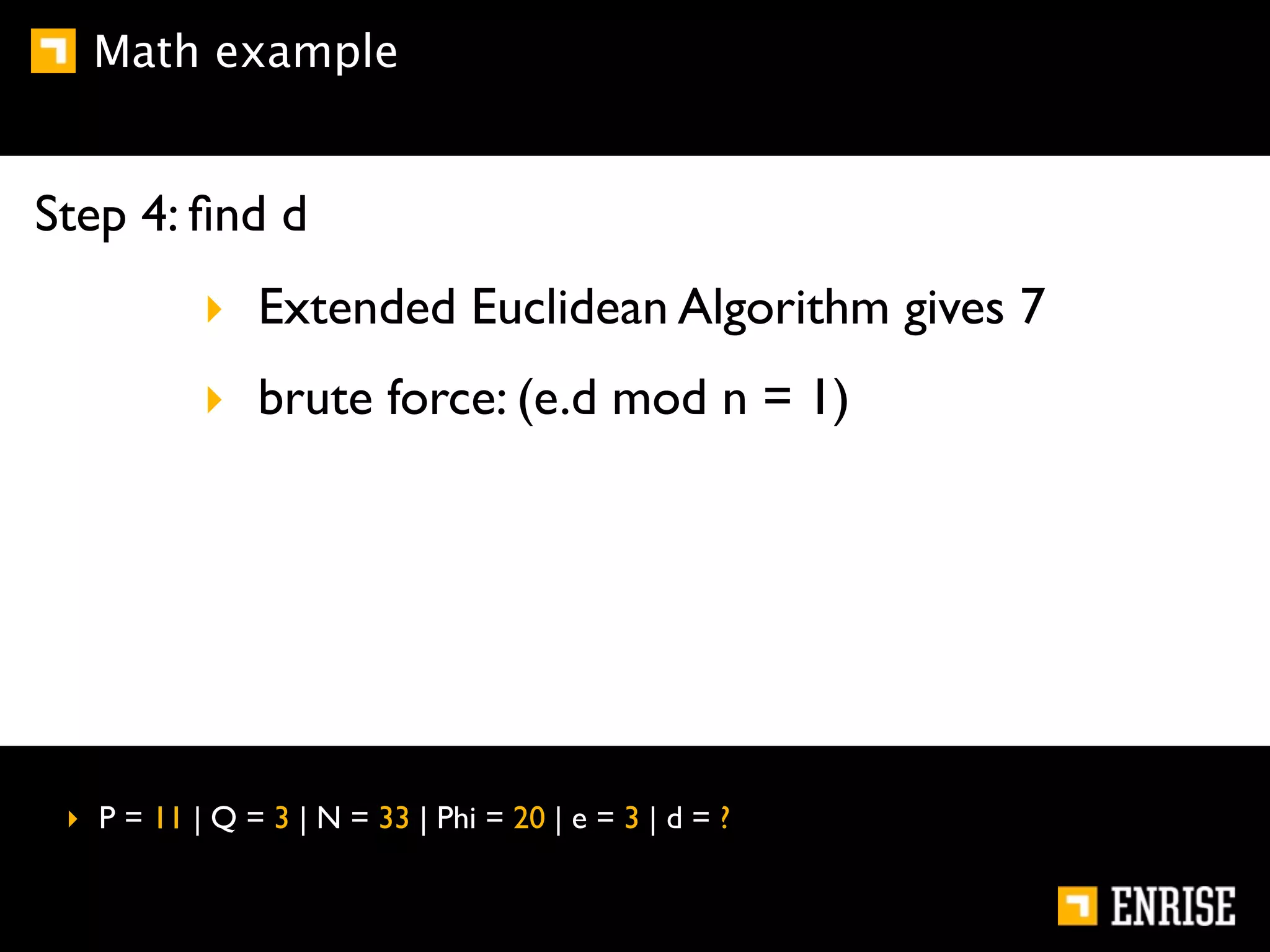
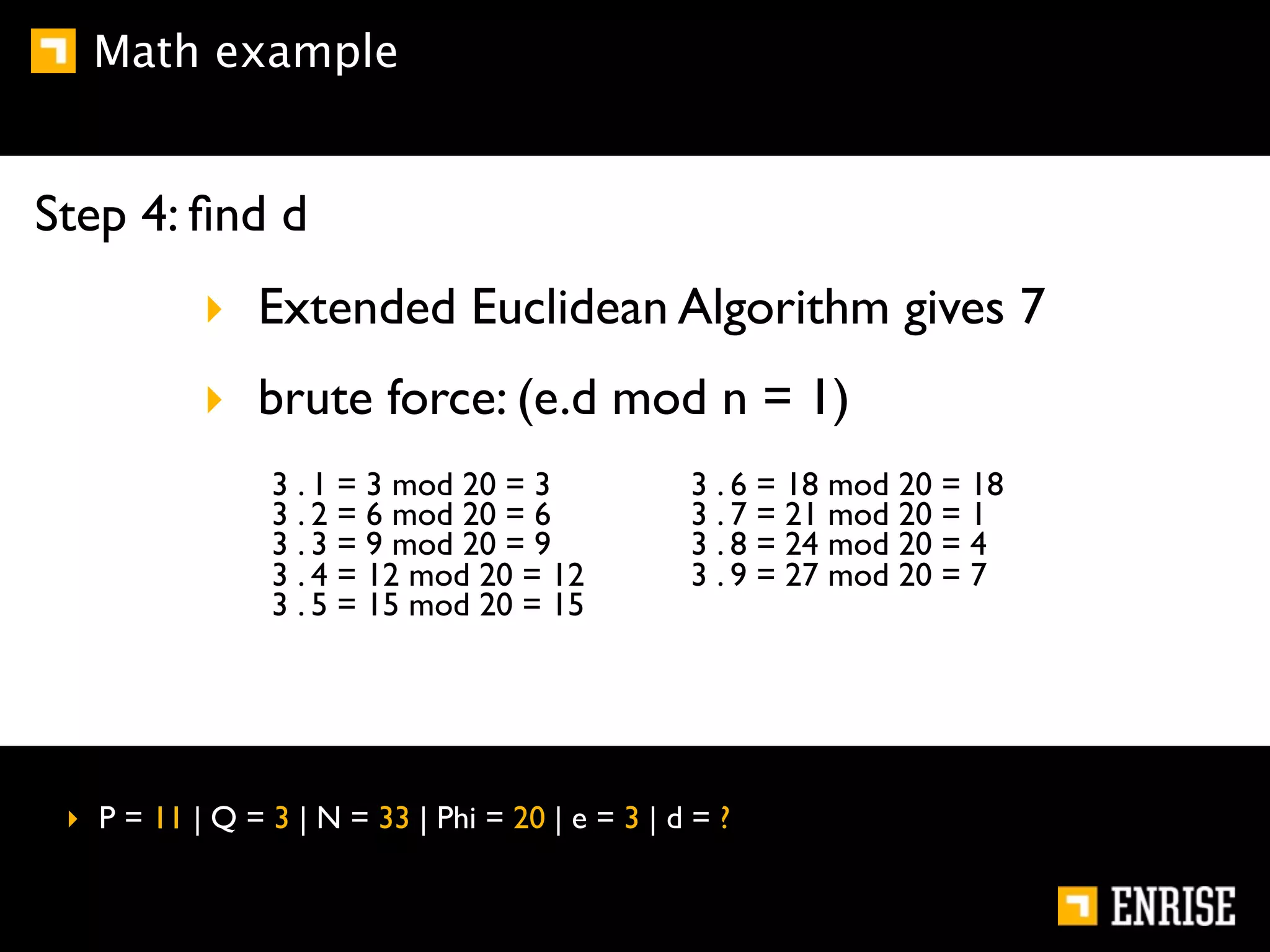
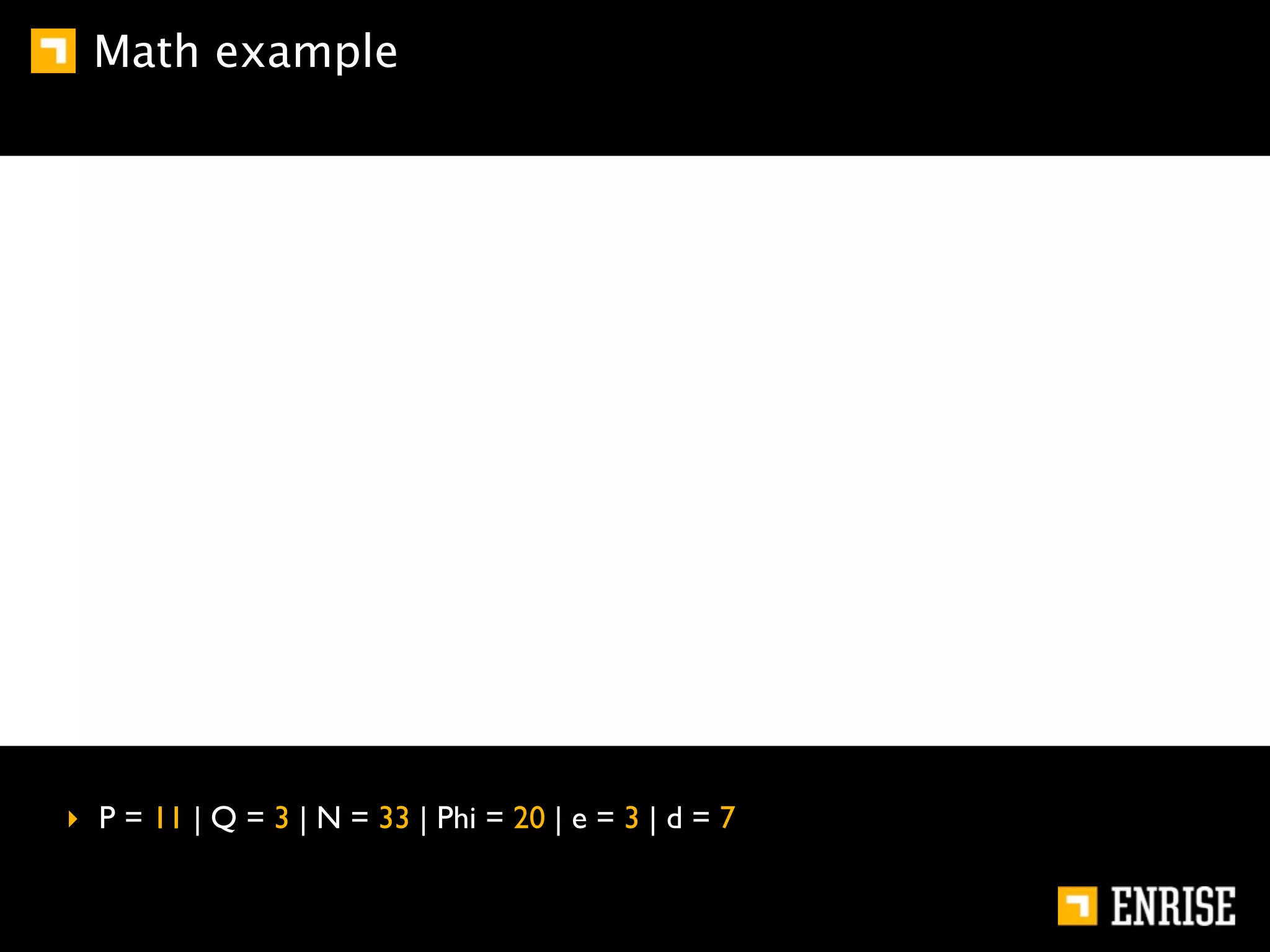
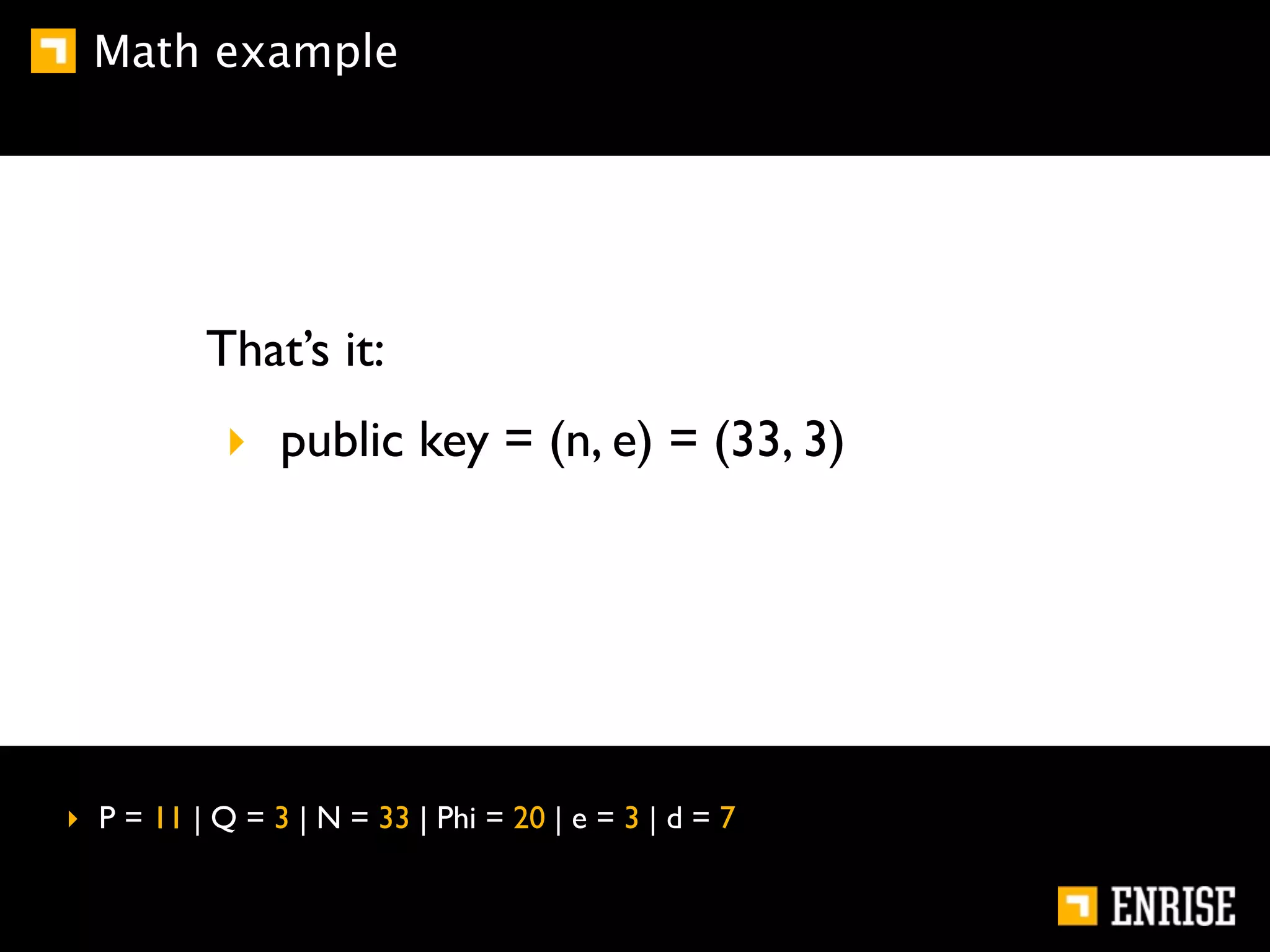
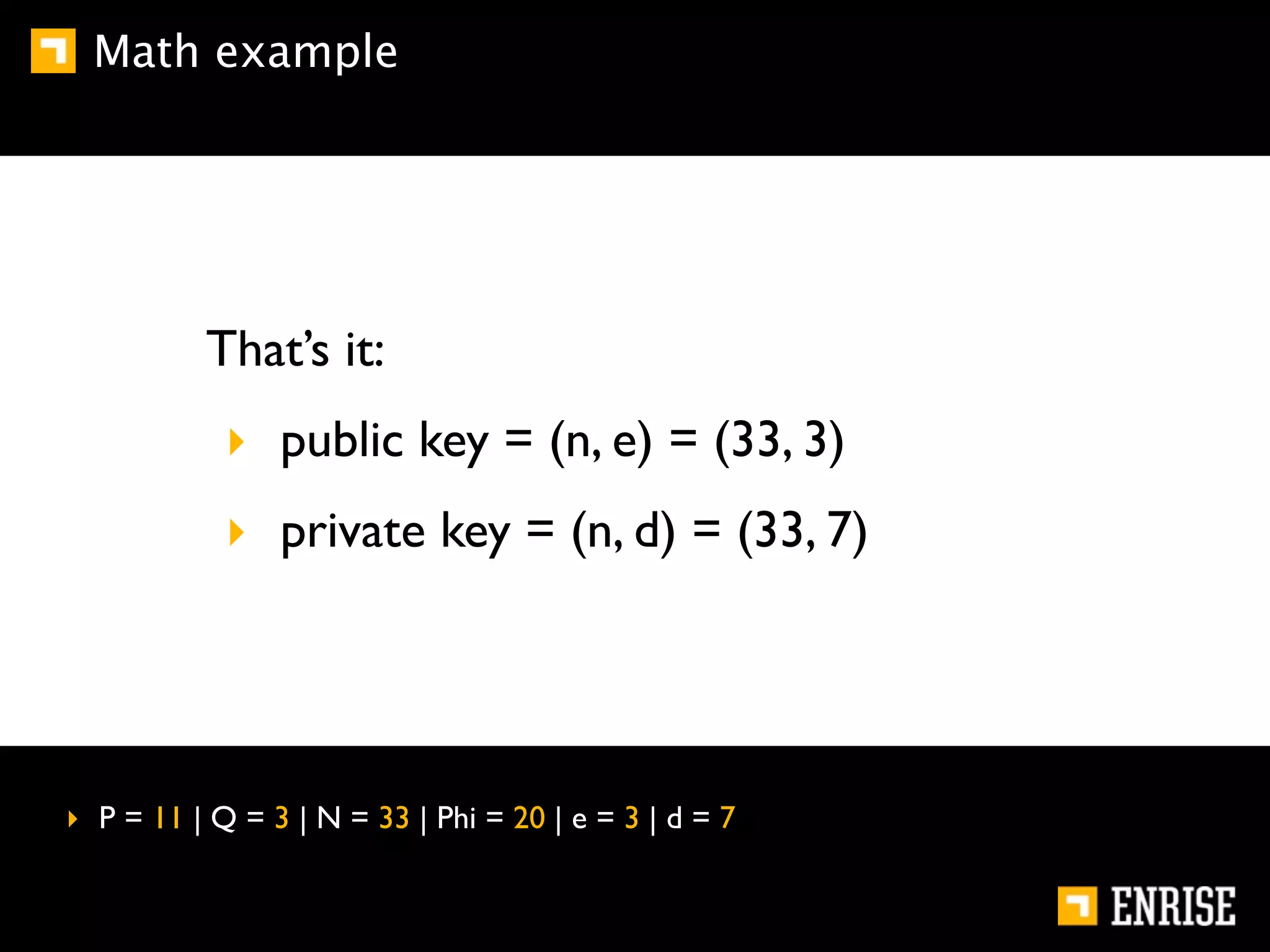
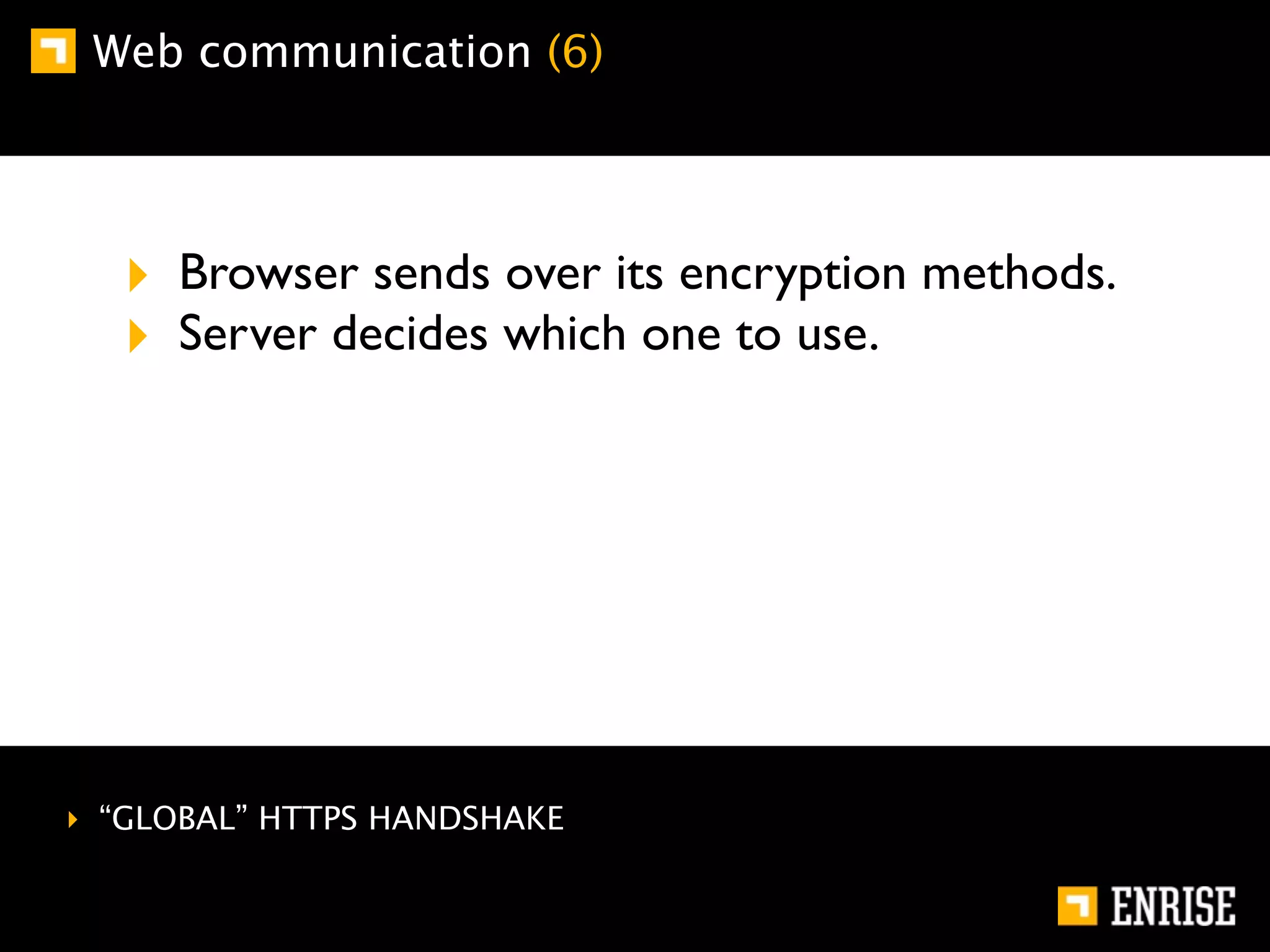
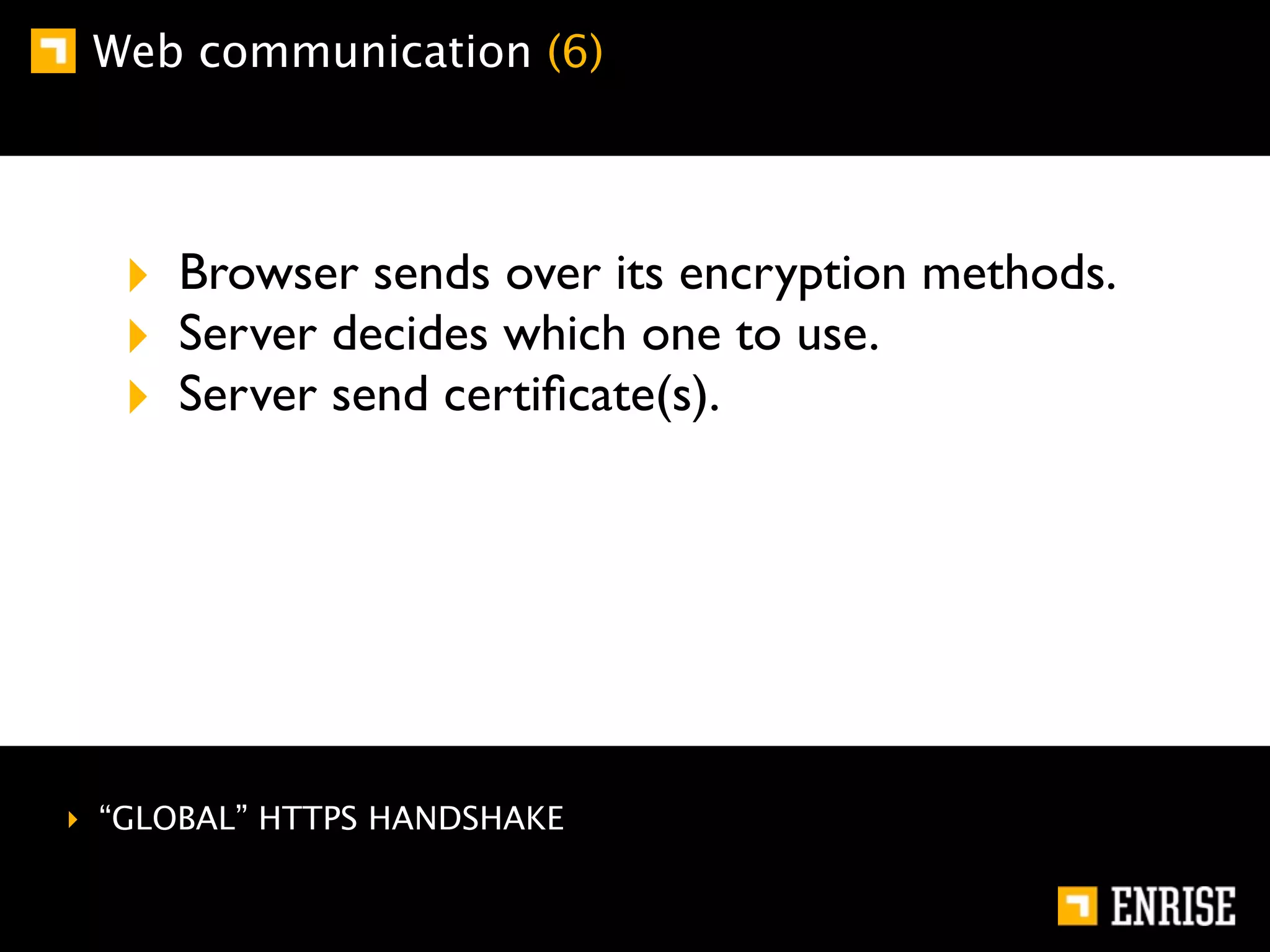
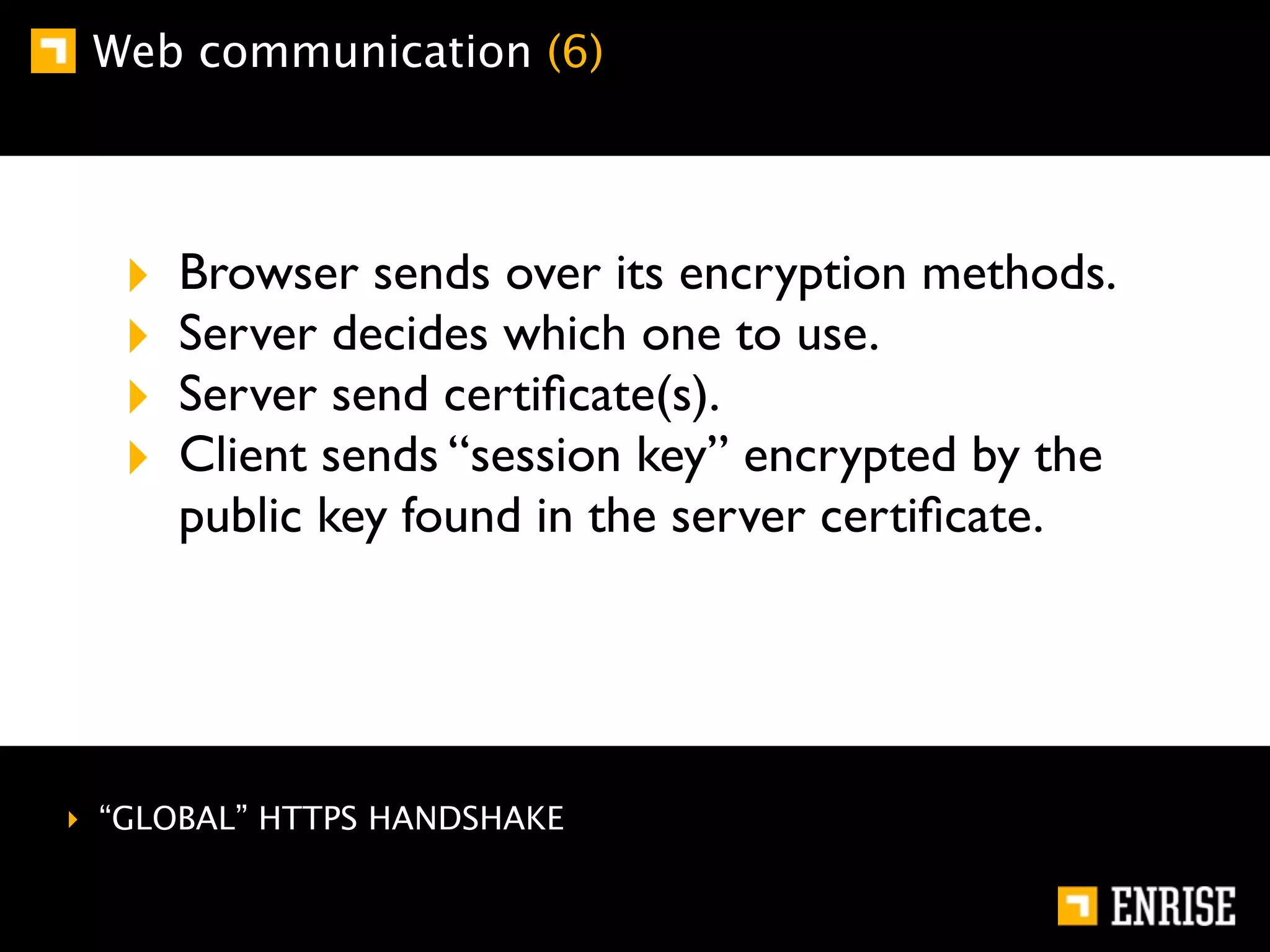
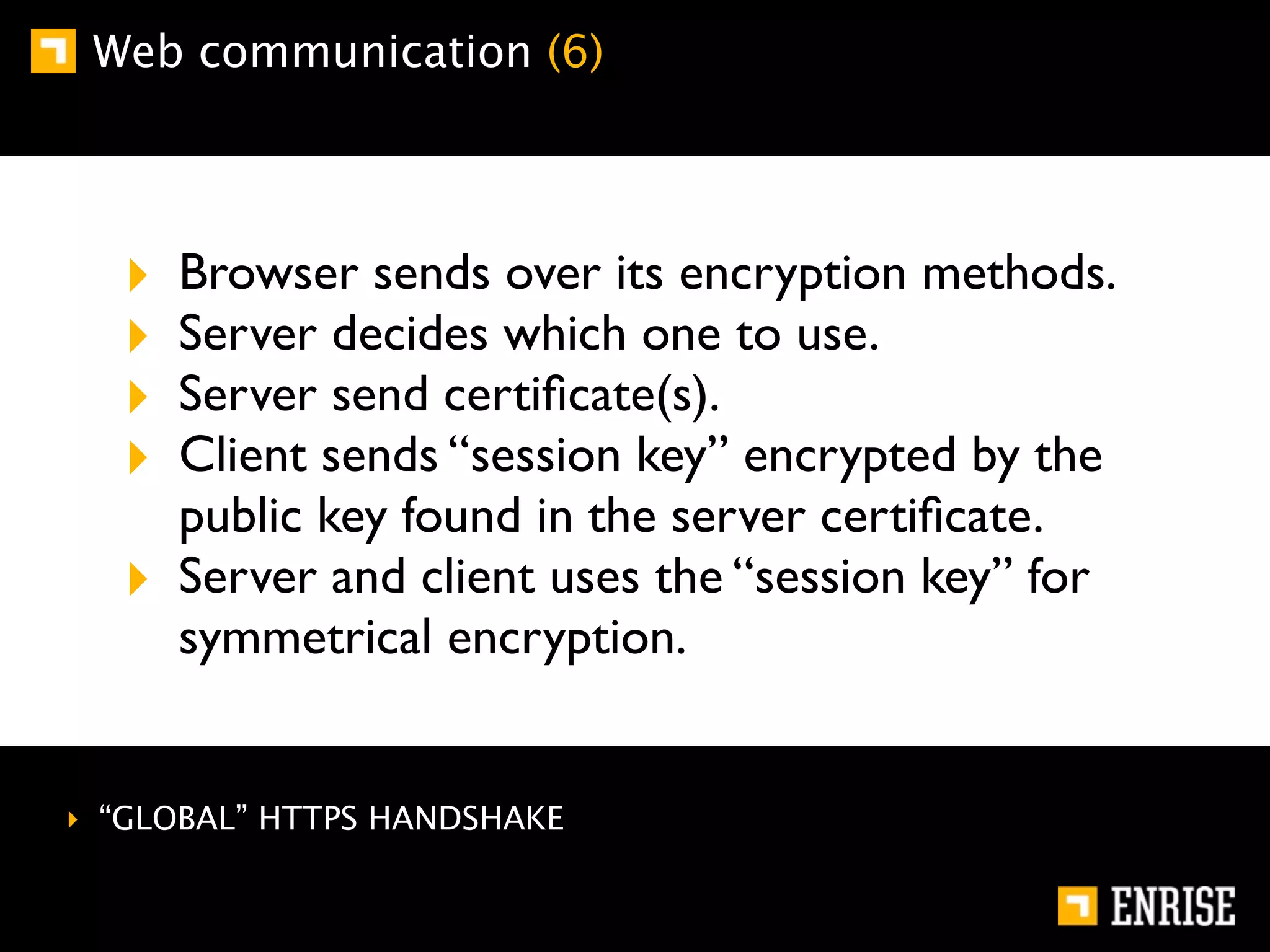
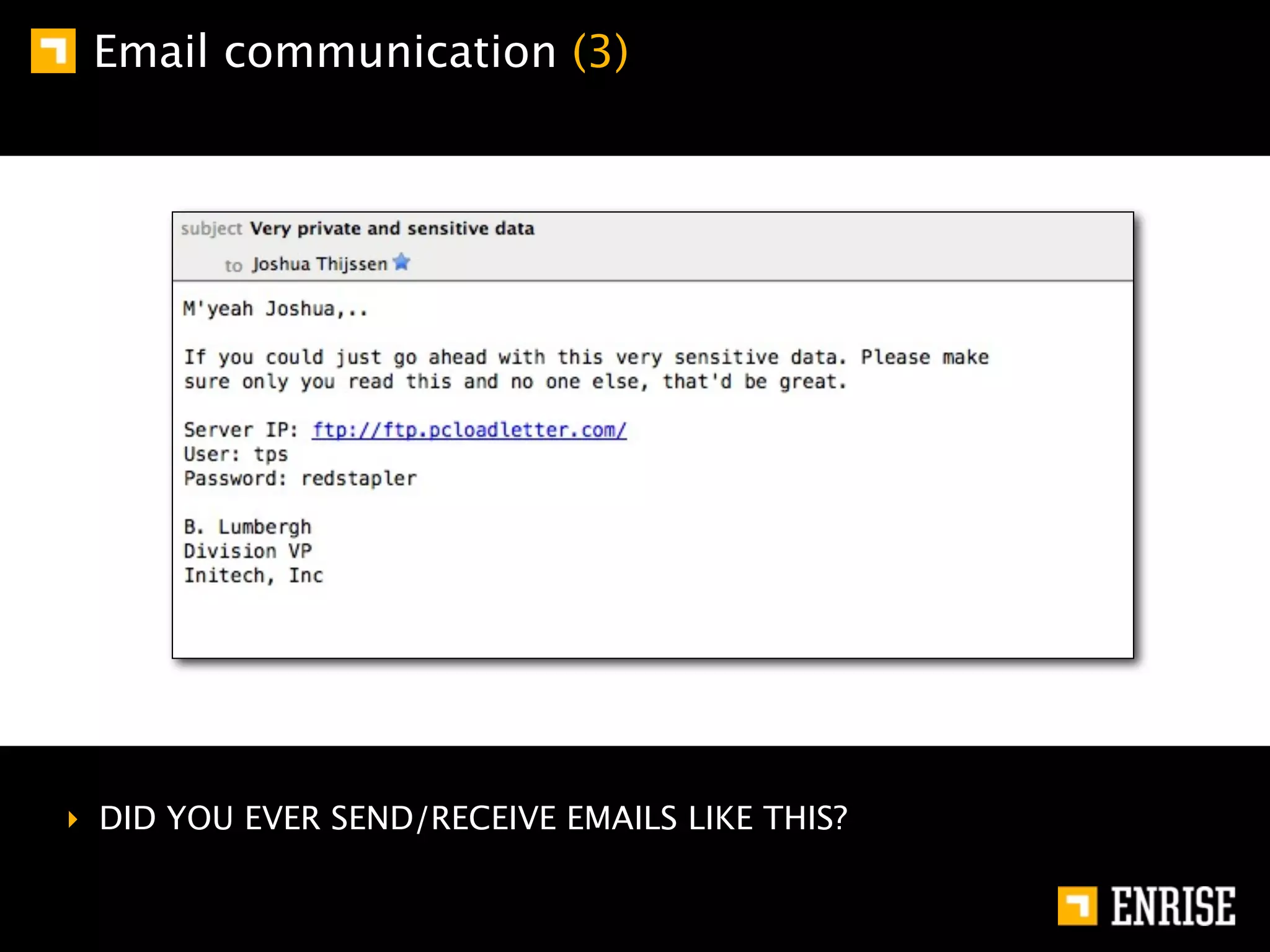
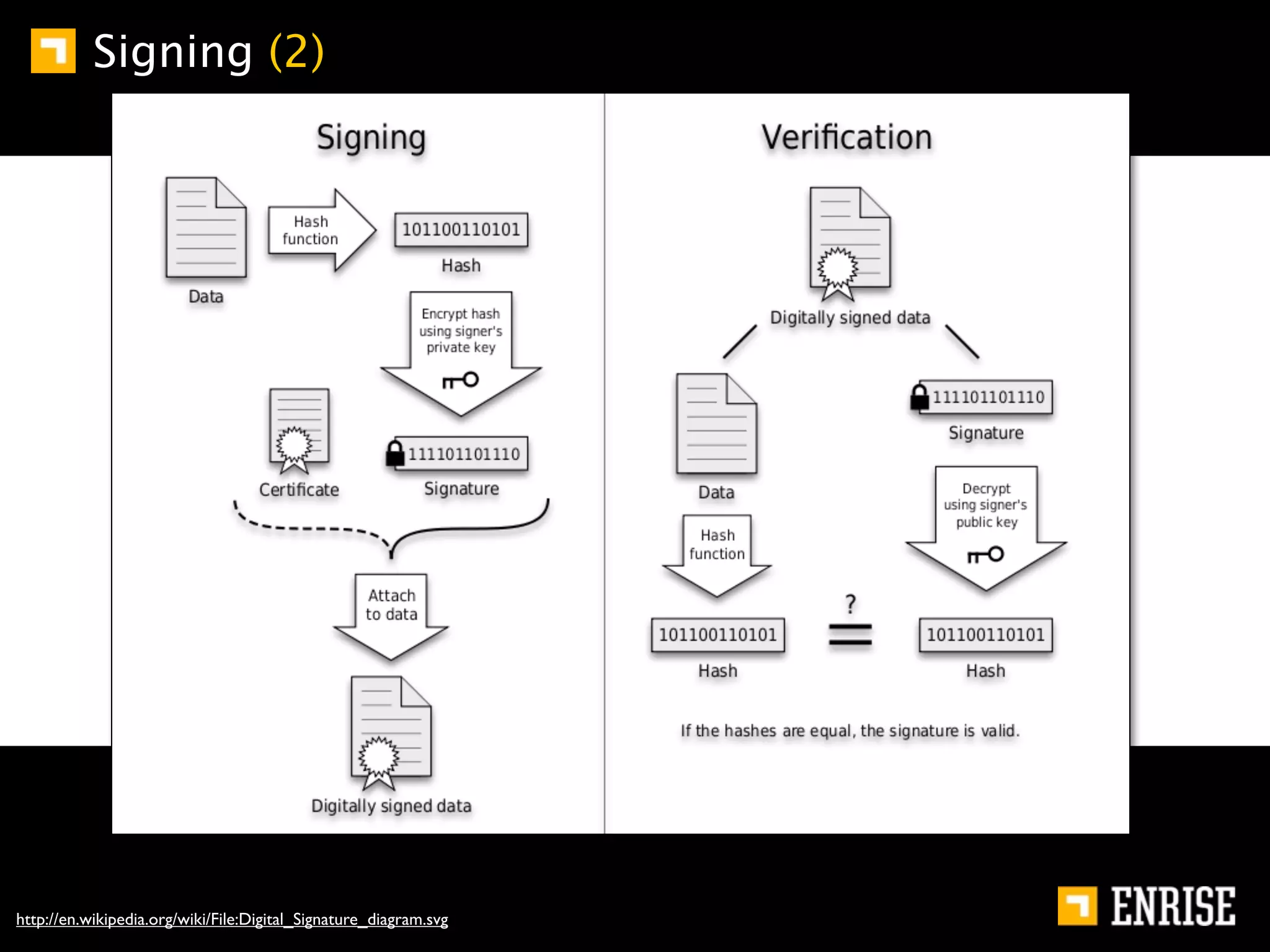
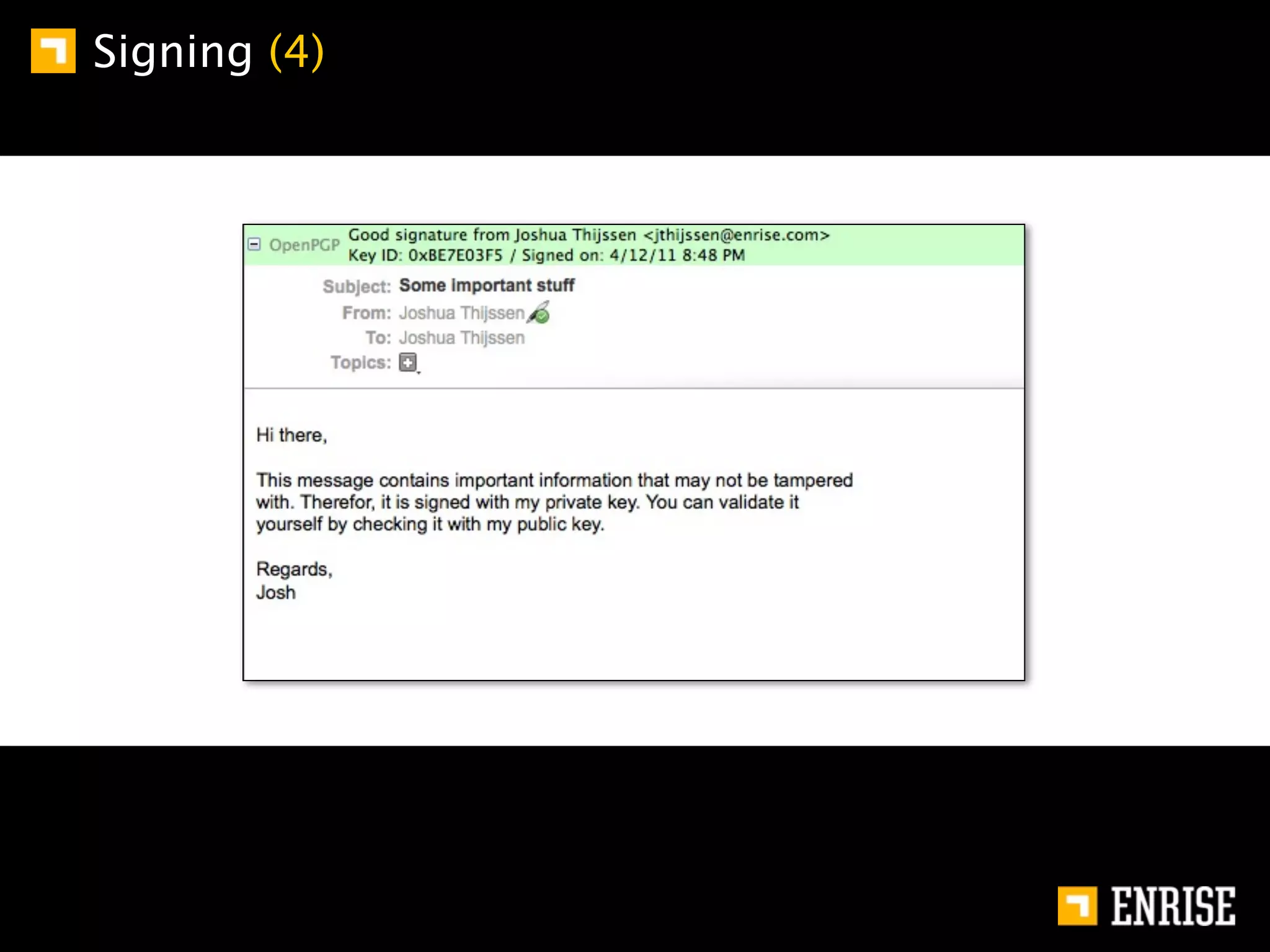
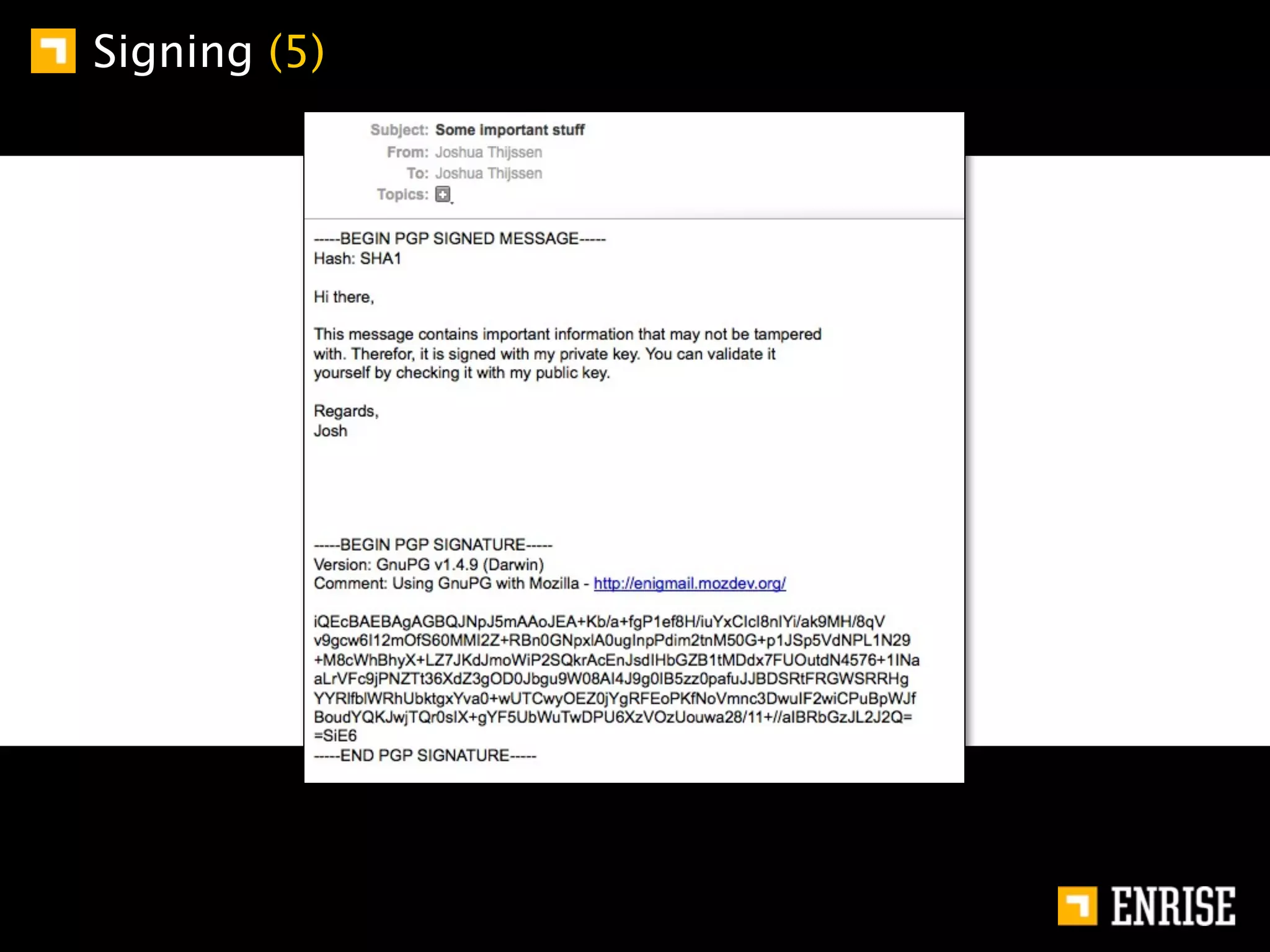
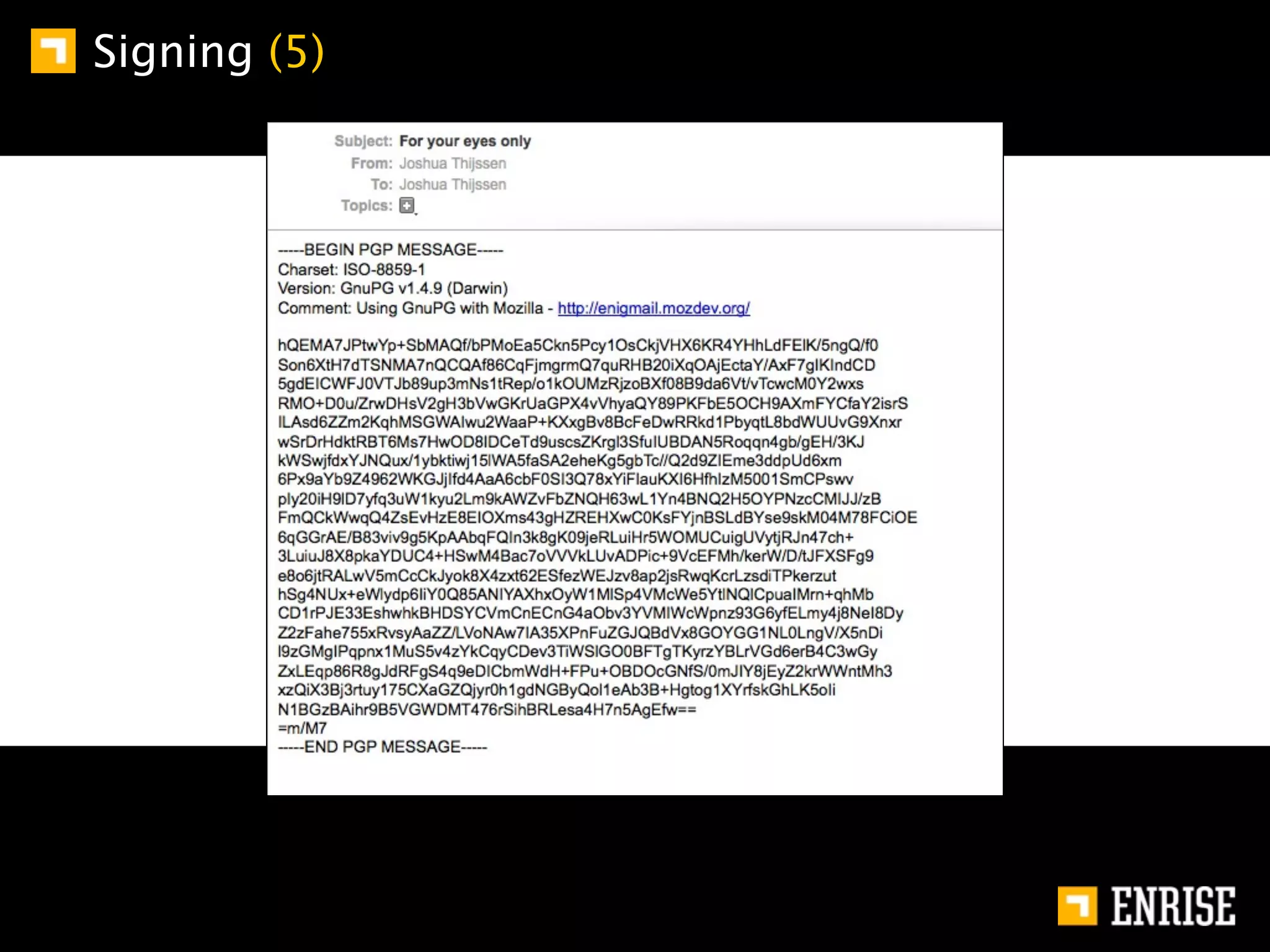
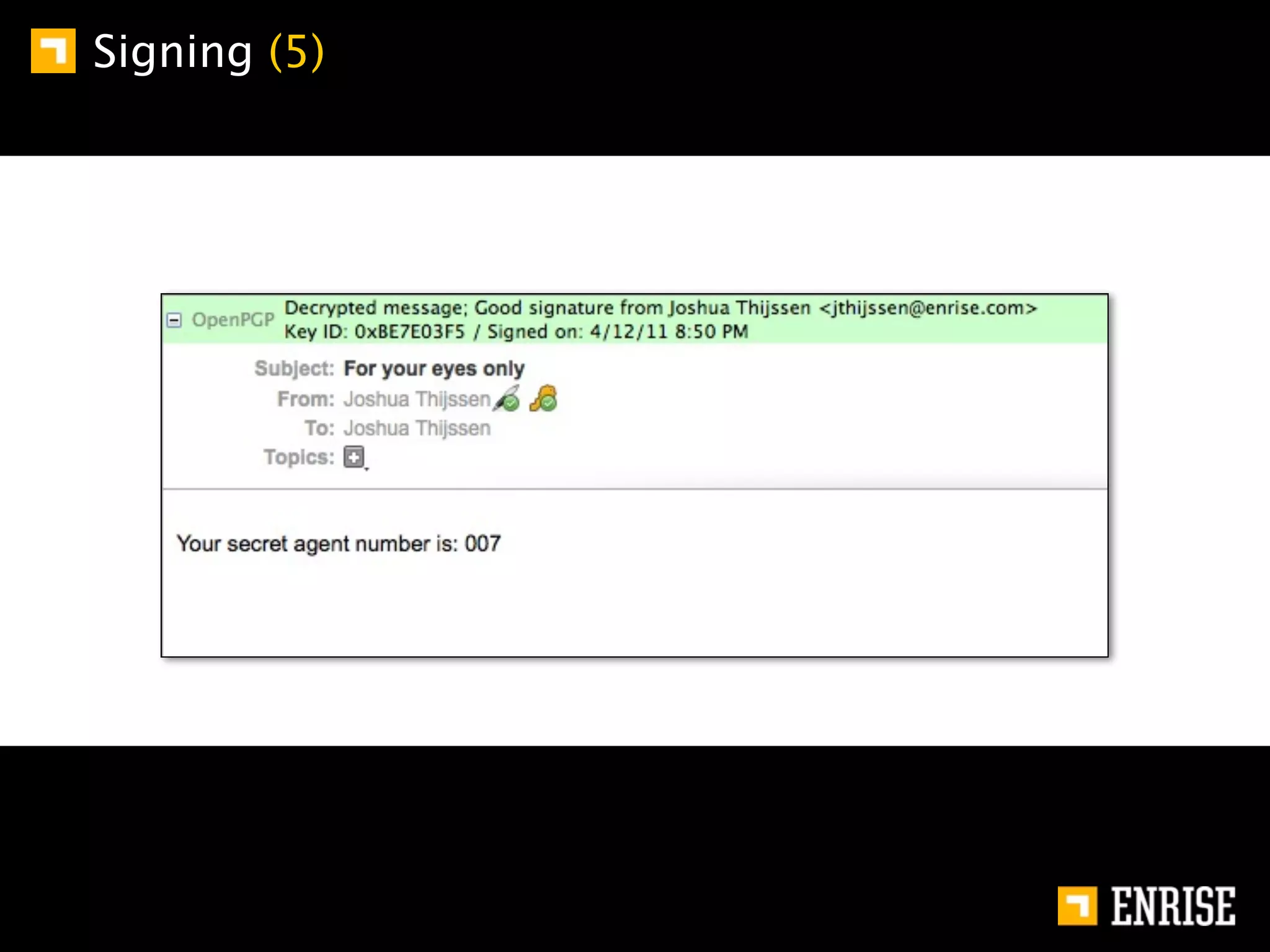
This document provides an introduction to public key cryptography. It begins with an overview of Alice and Bob, who represent communication parties. It then discusses the history of encryption, including flaws in early substitution and Caesar ciphers. Frequency analysis is introduced as a way to break these simple ciphers. The document concludes by explaining the advantages of public key encryption over symmetric encryption, such as not requiring secure key exchange.