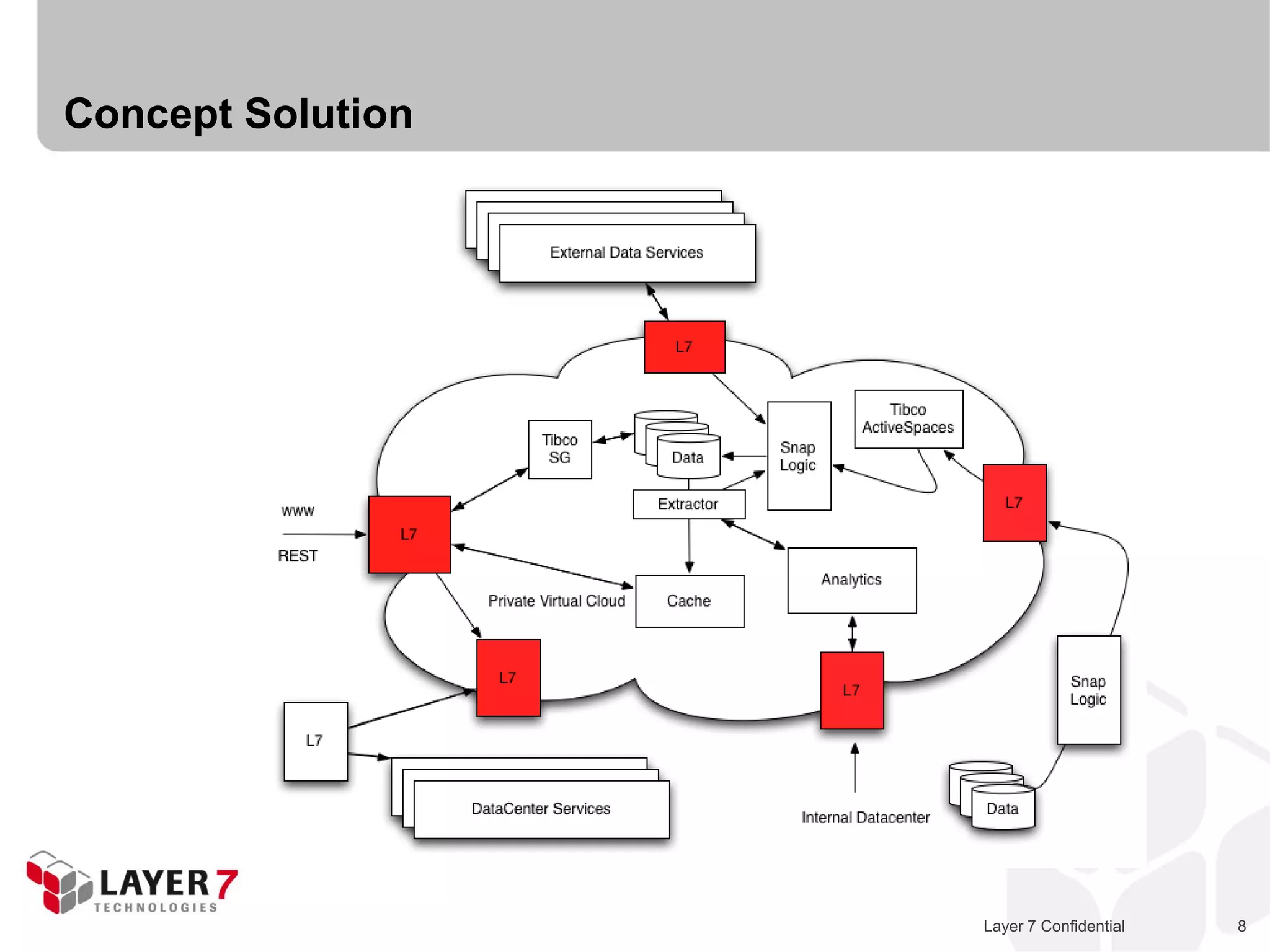
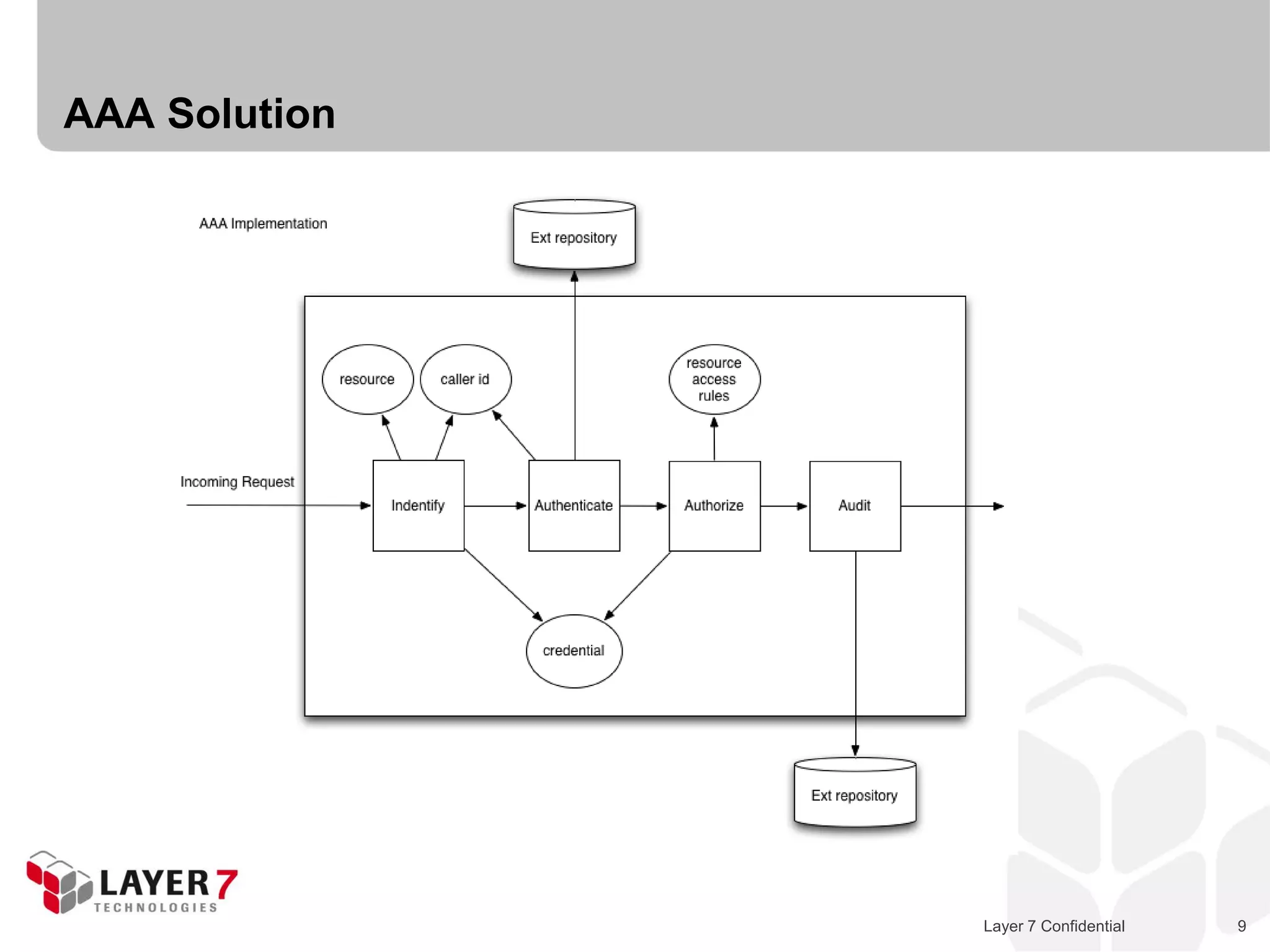
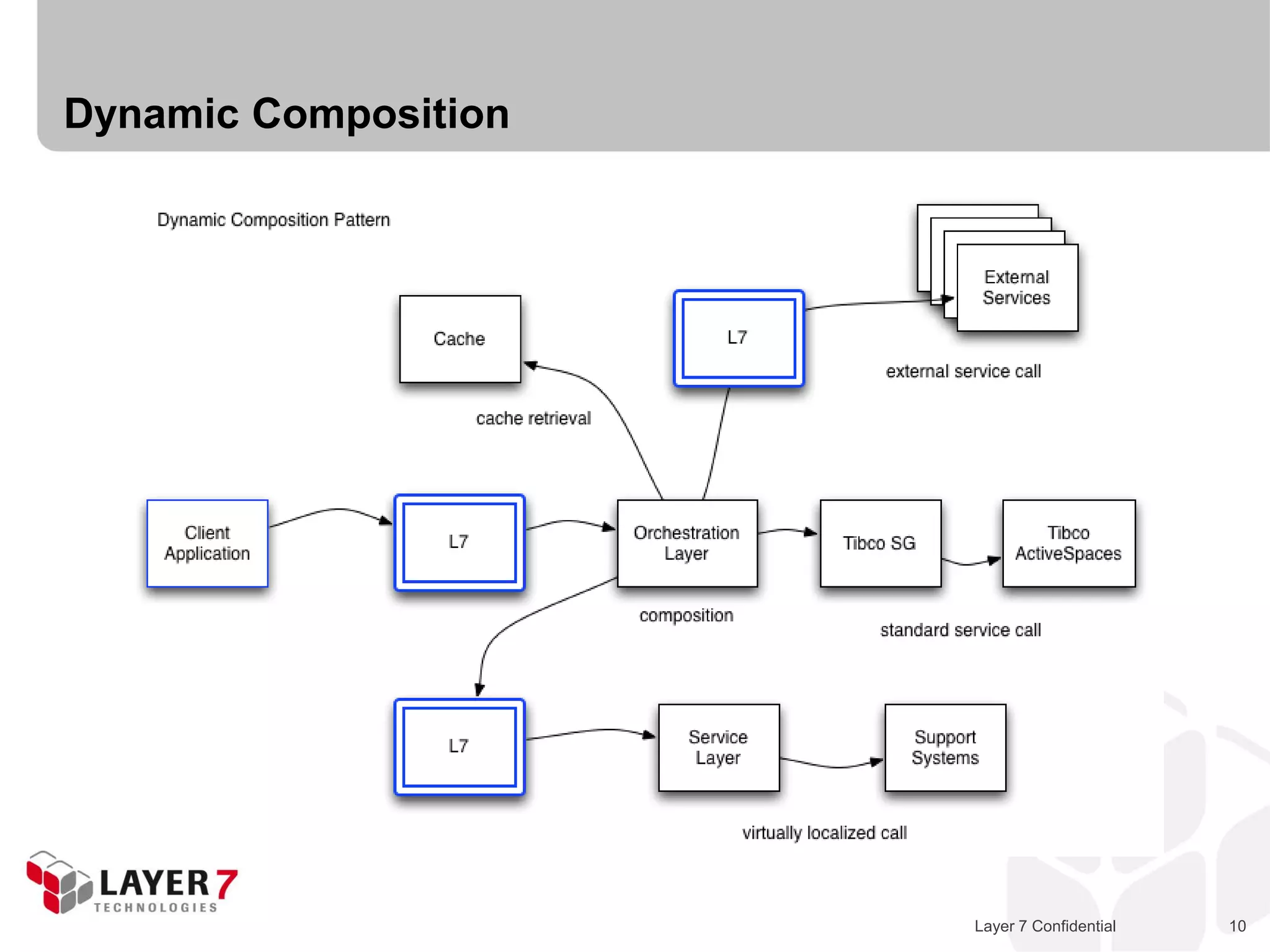
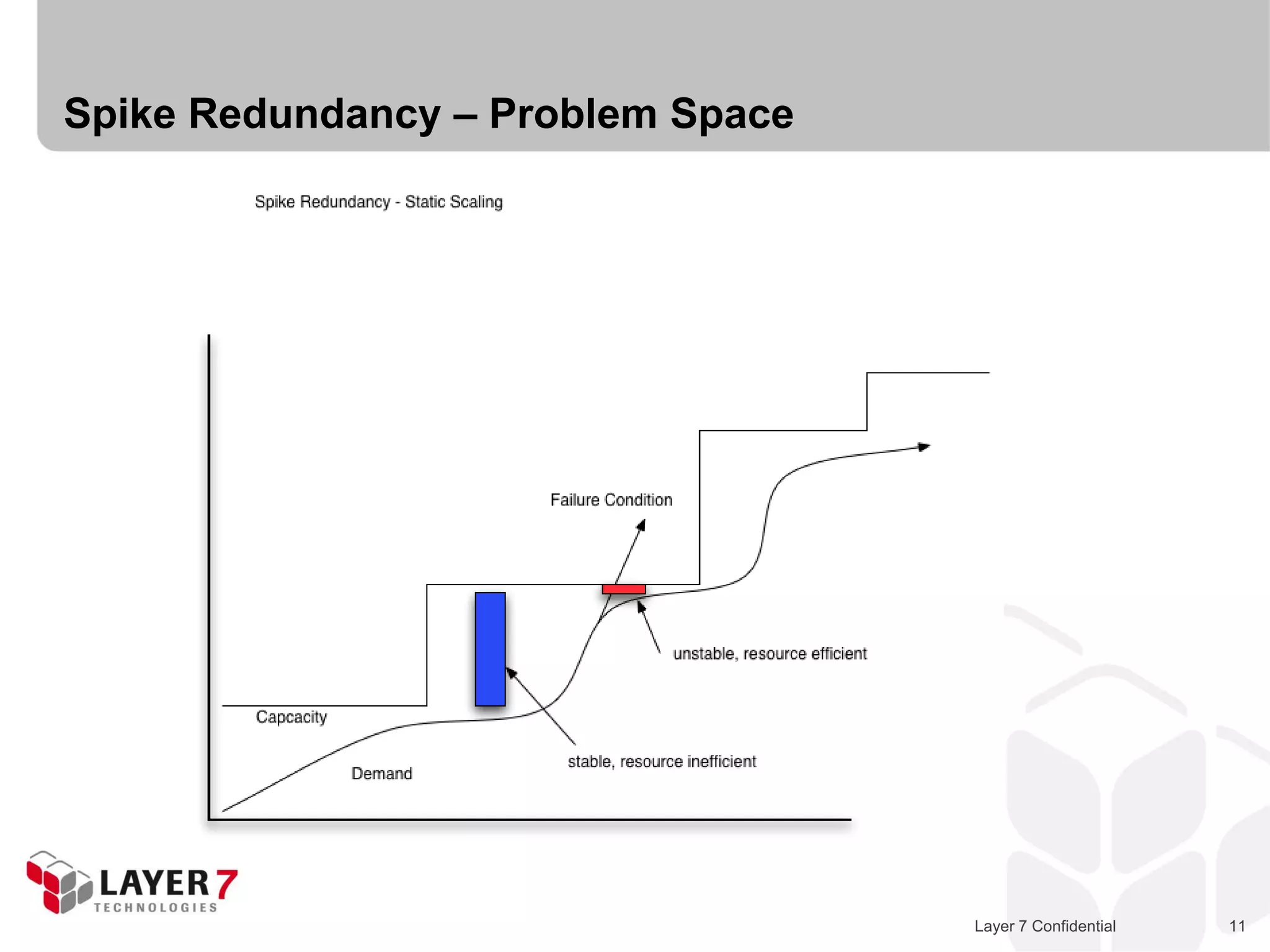
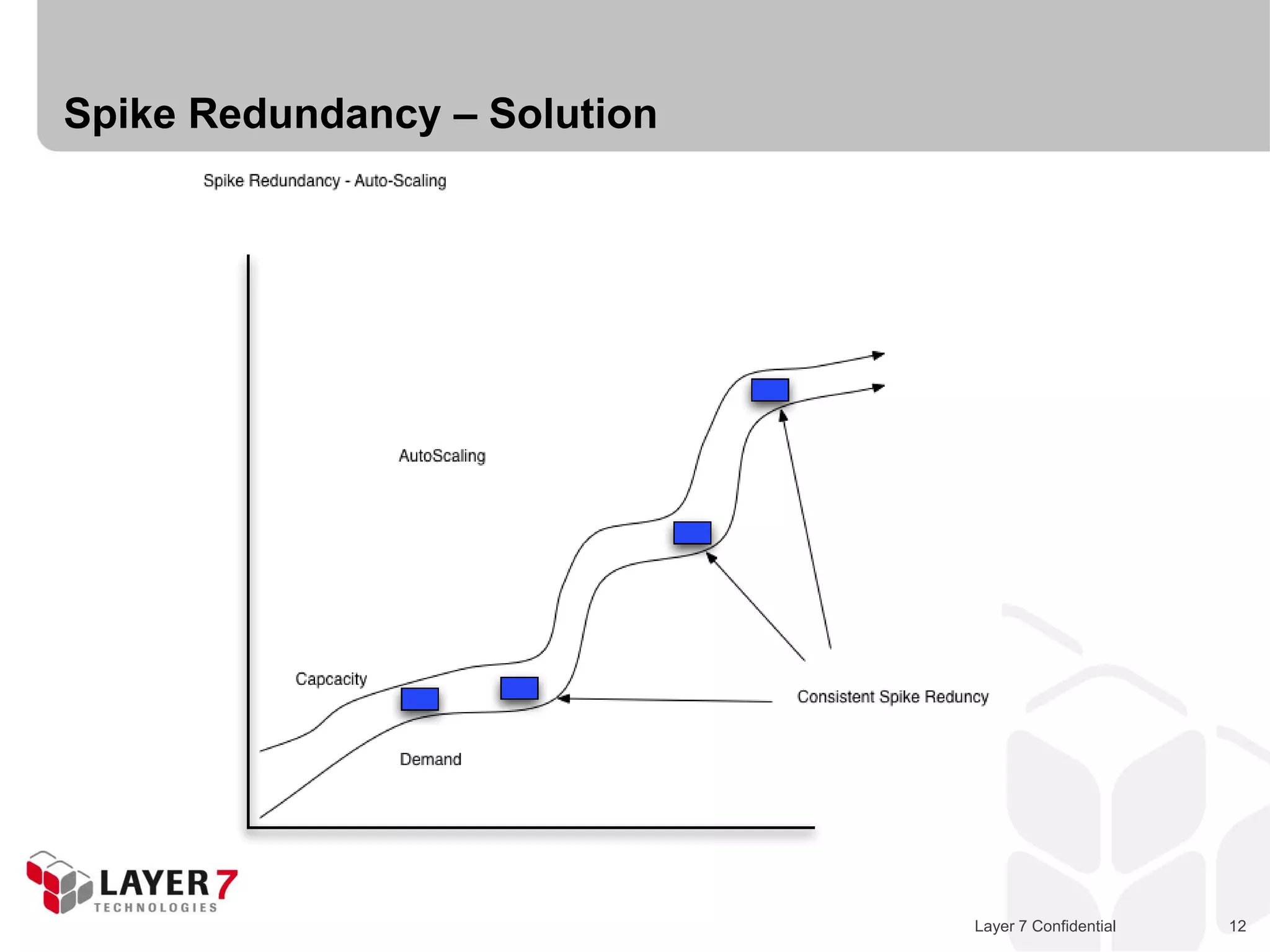
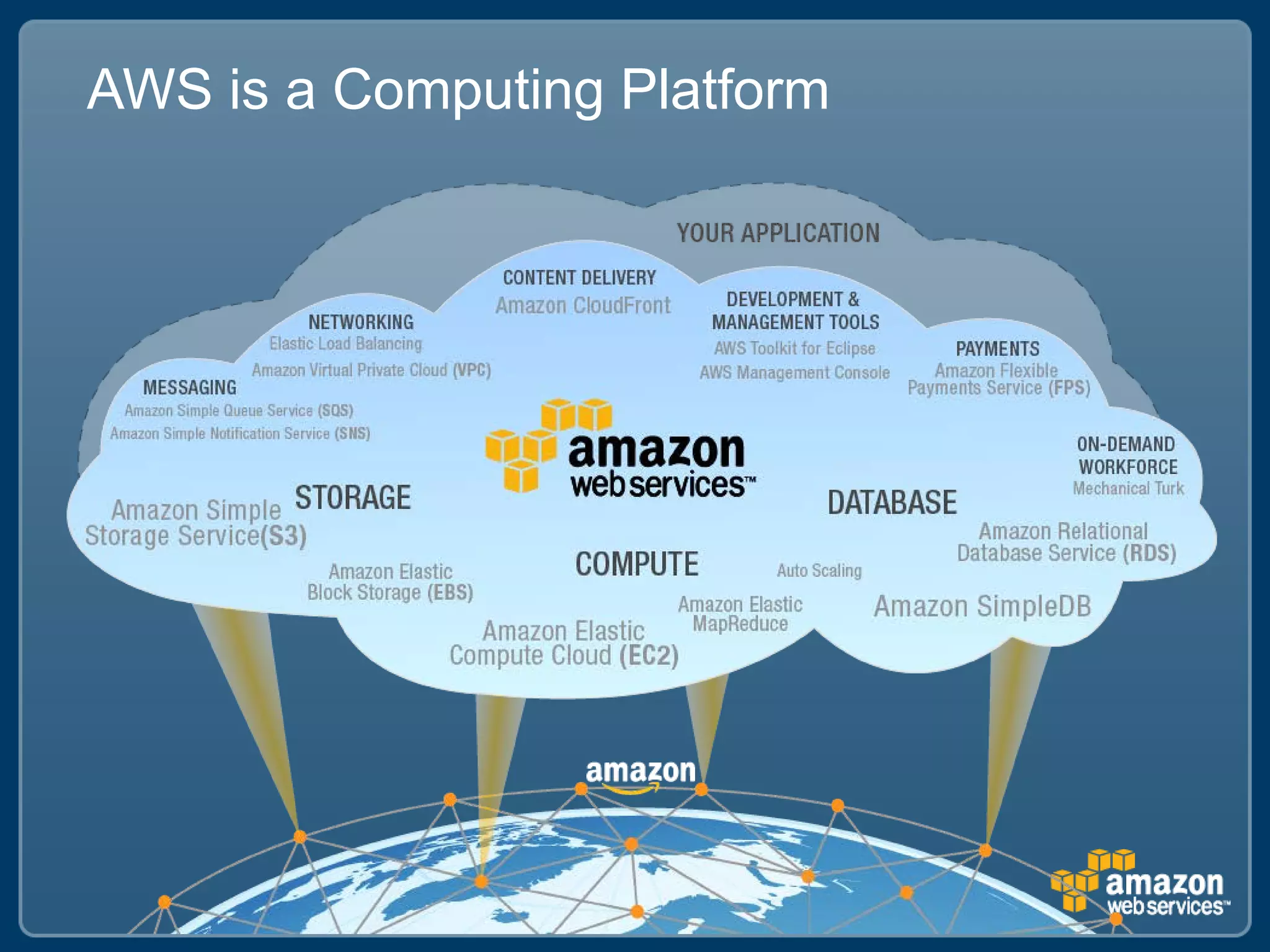
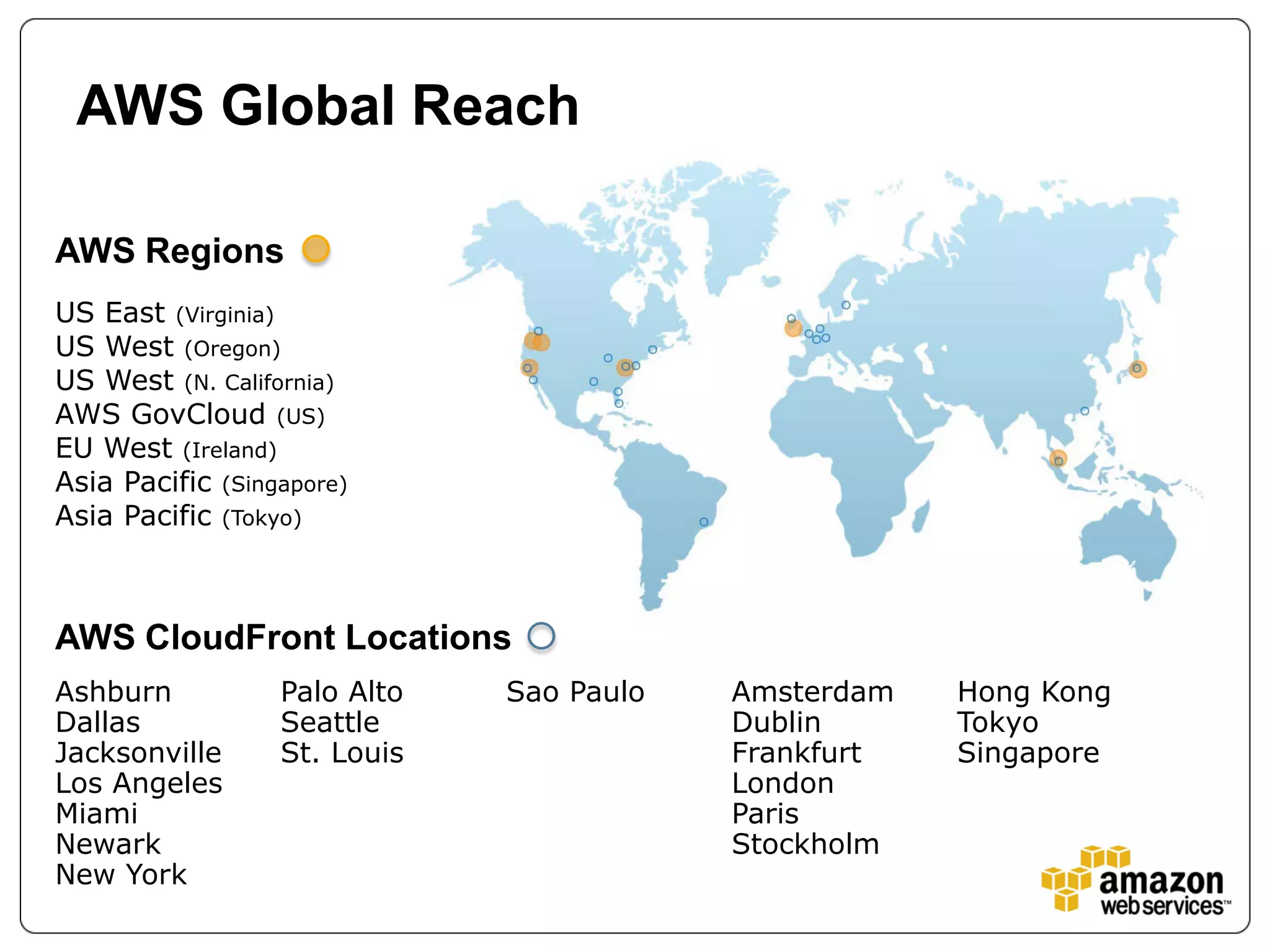
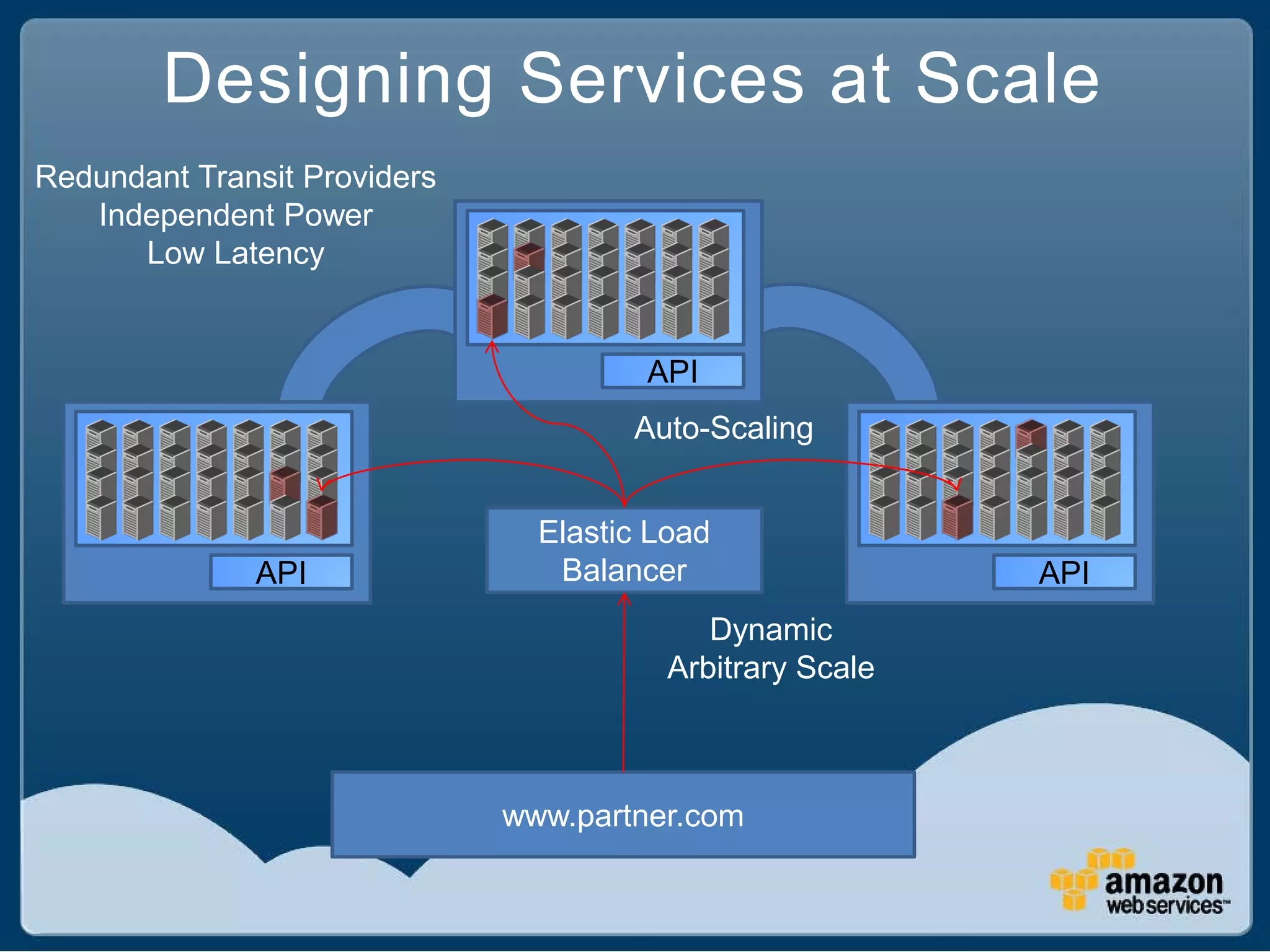
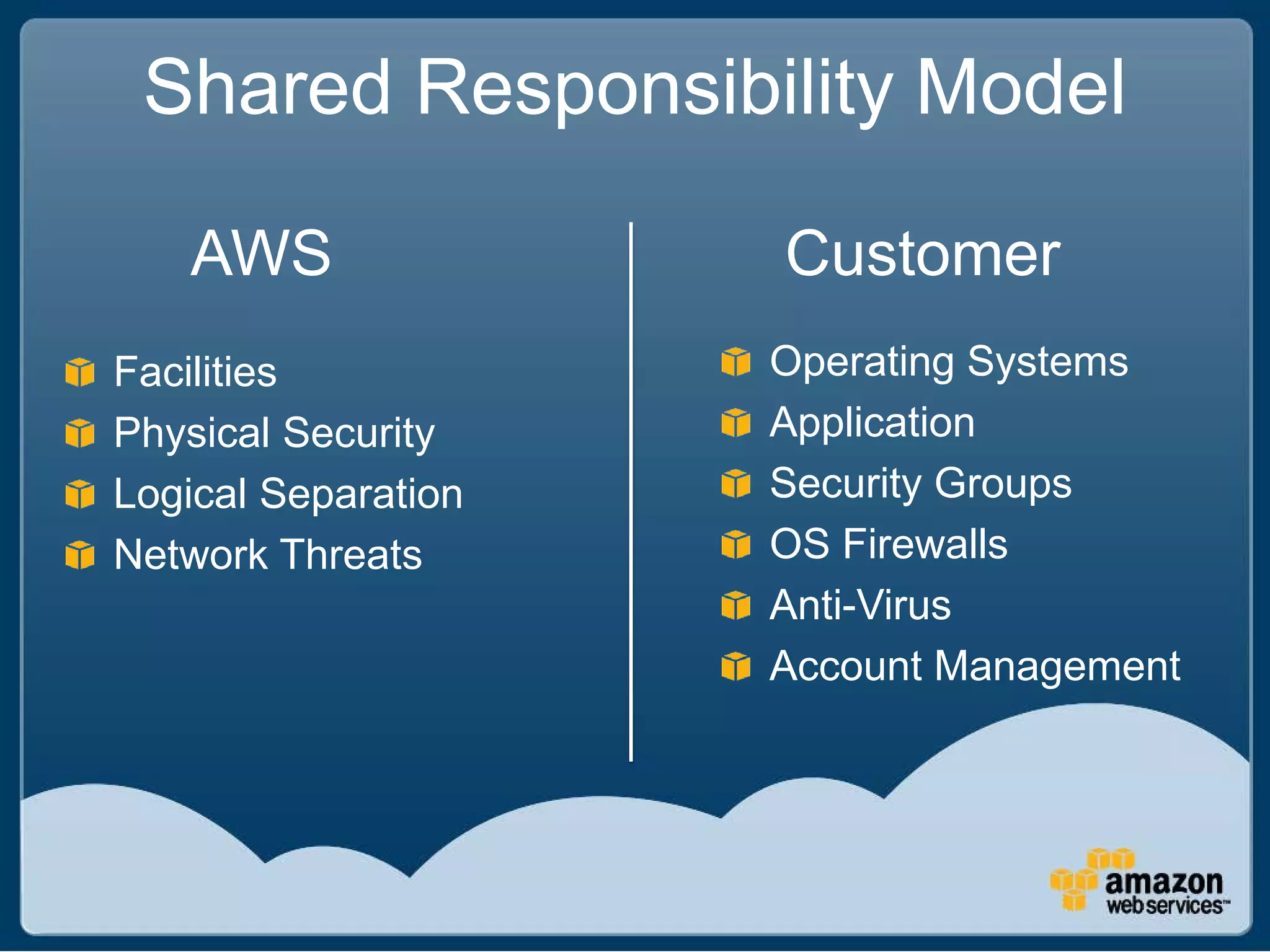
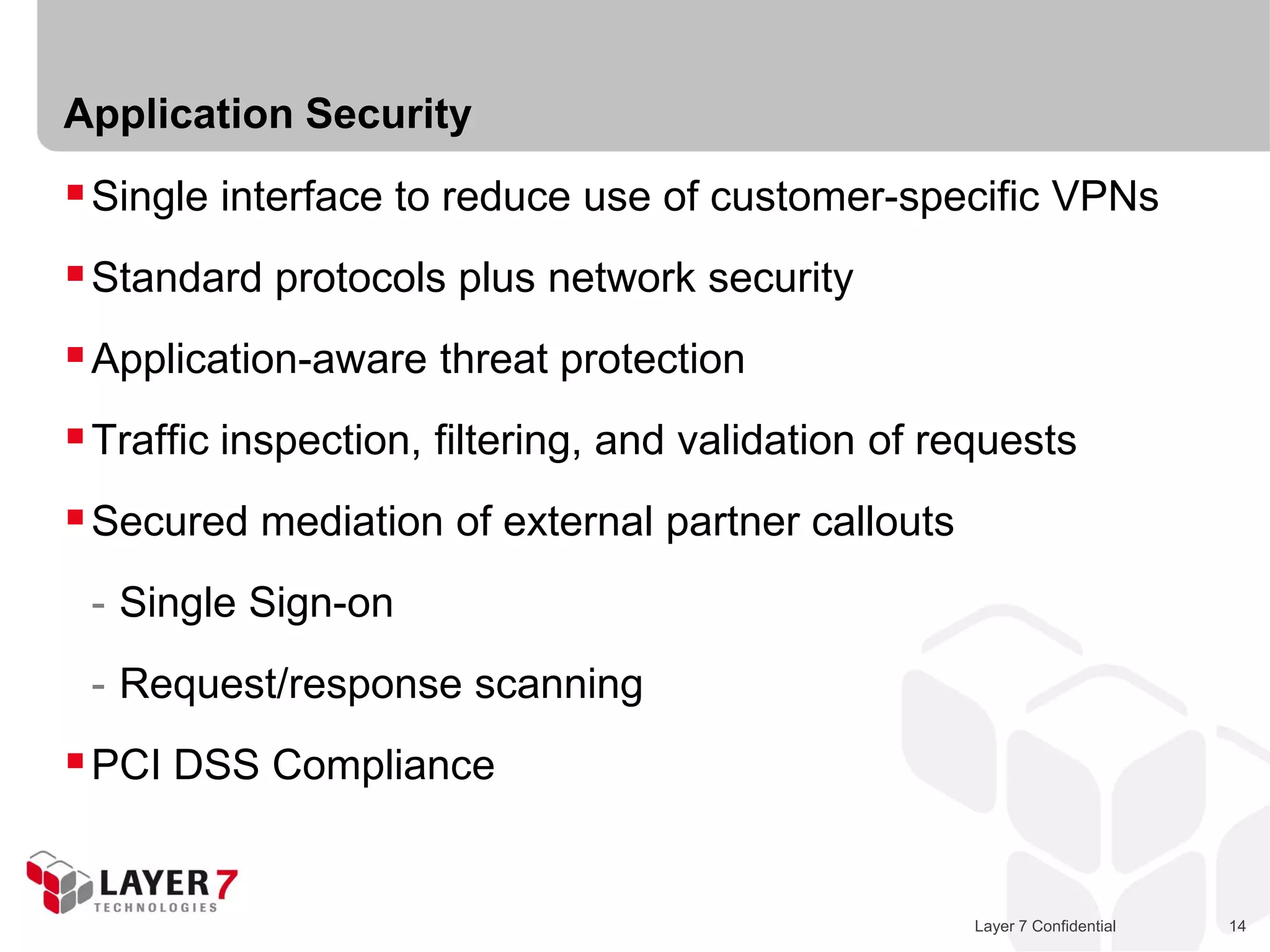
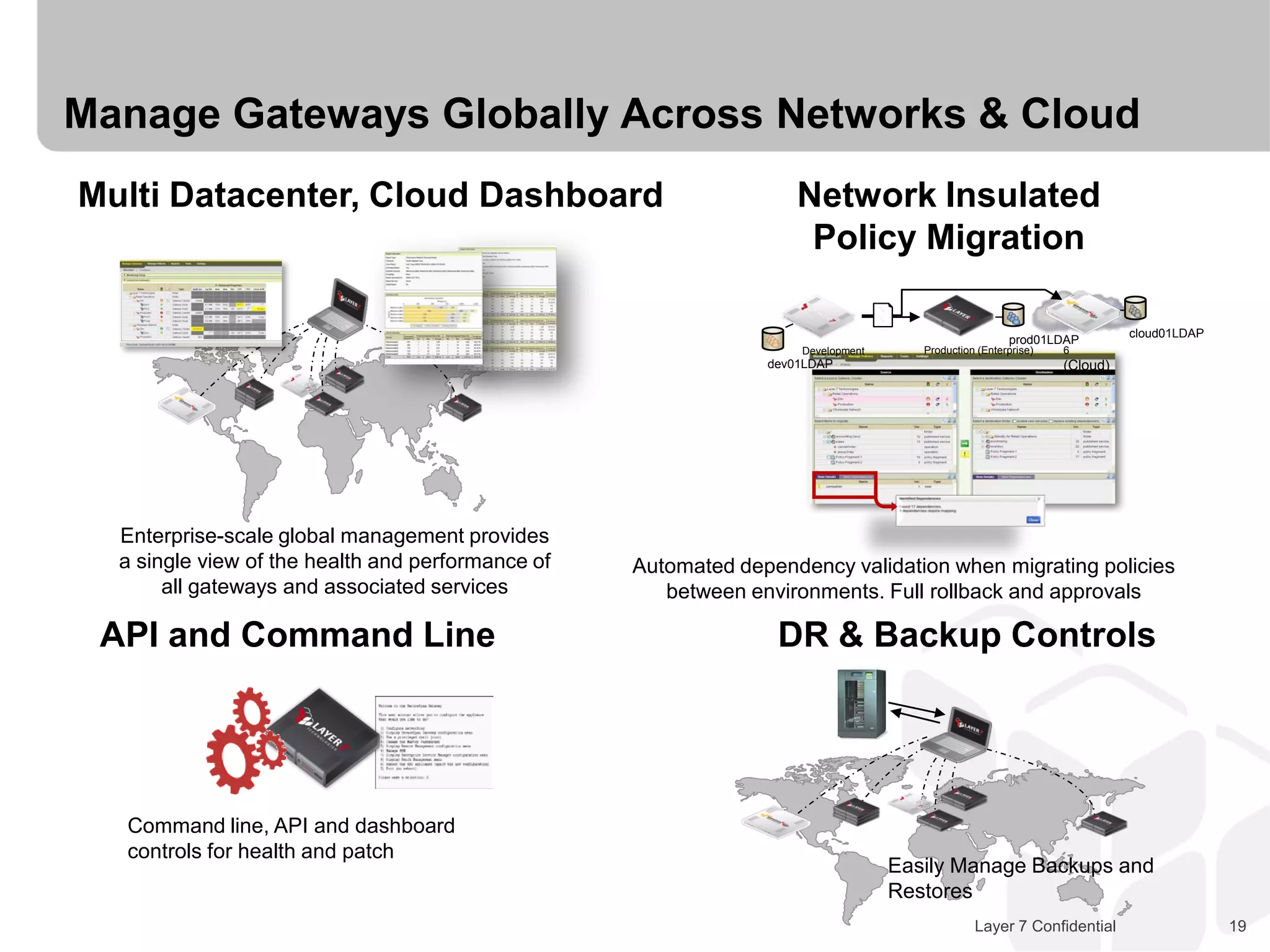
The document discusses Best Buy's integration with cloud services through their BBYOPEN API, emphasizing the importance of scalability, security, and performance. It details the architectural challenges faced, the technologies utilized, and solutions for secure cloud integration and application management. The presentation also highlights compliance with security standards like PCI DSS and the shared responsibility model for governance in cloud environments.