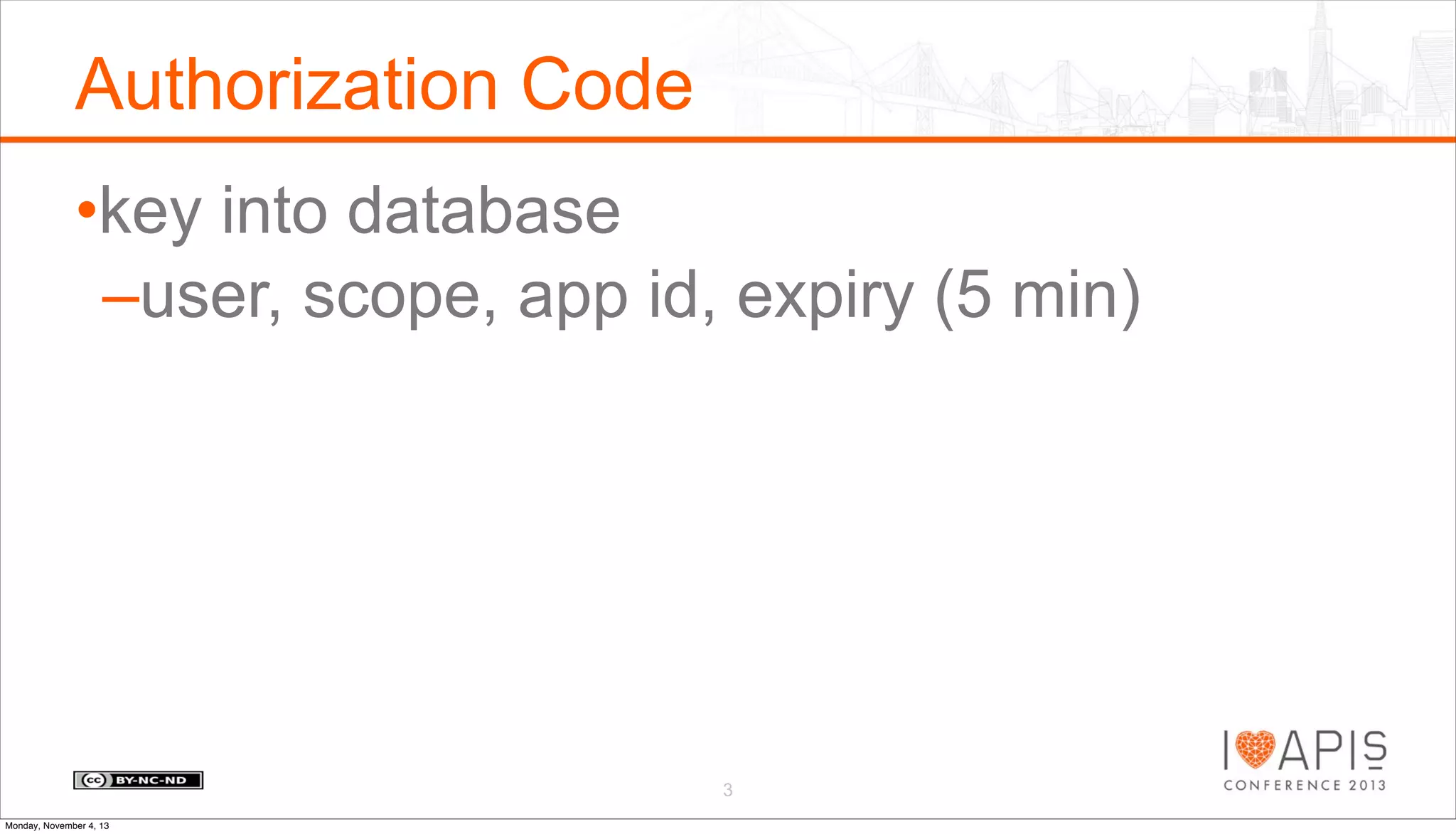
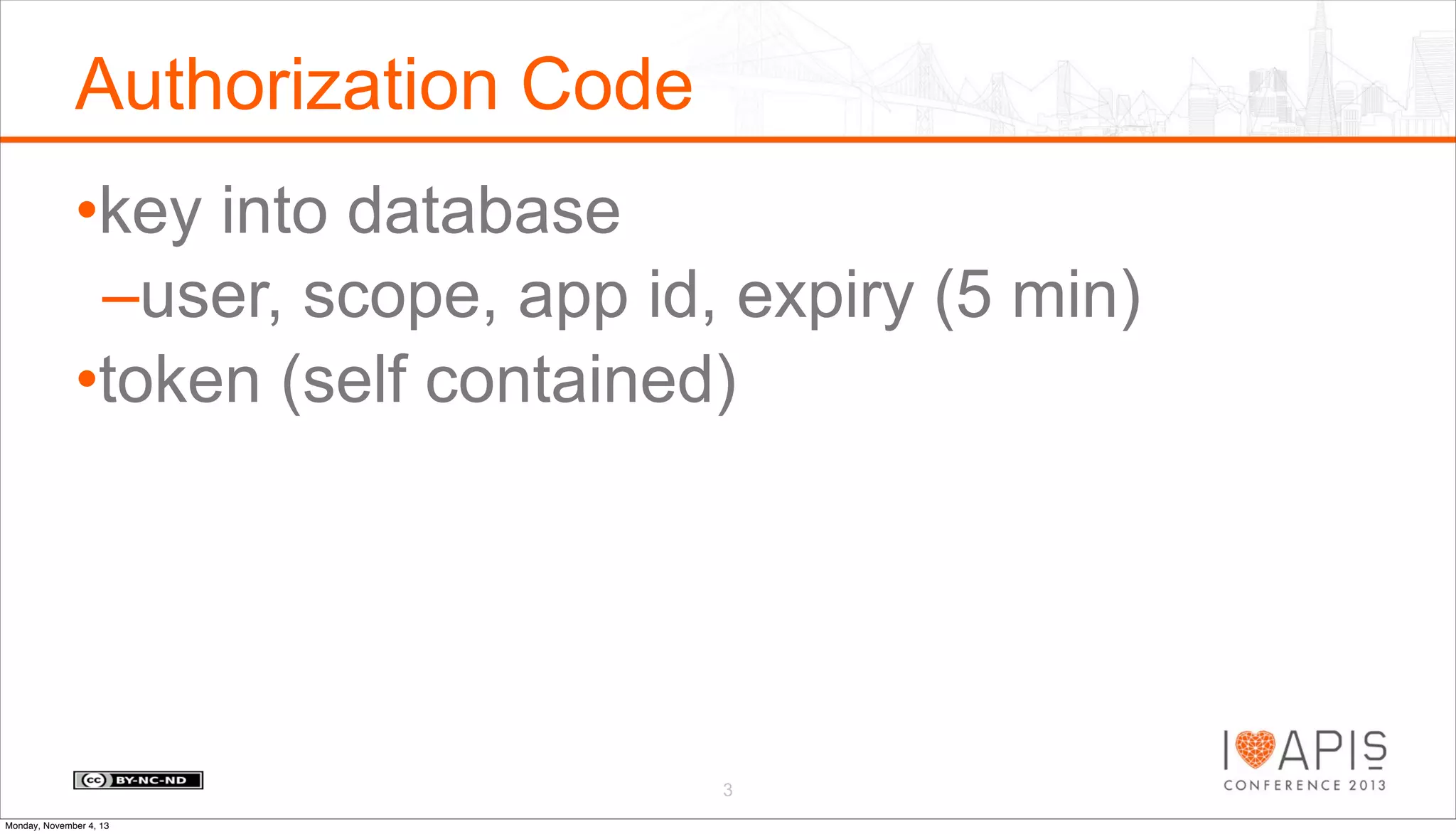
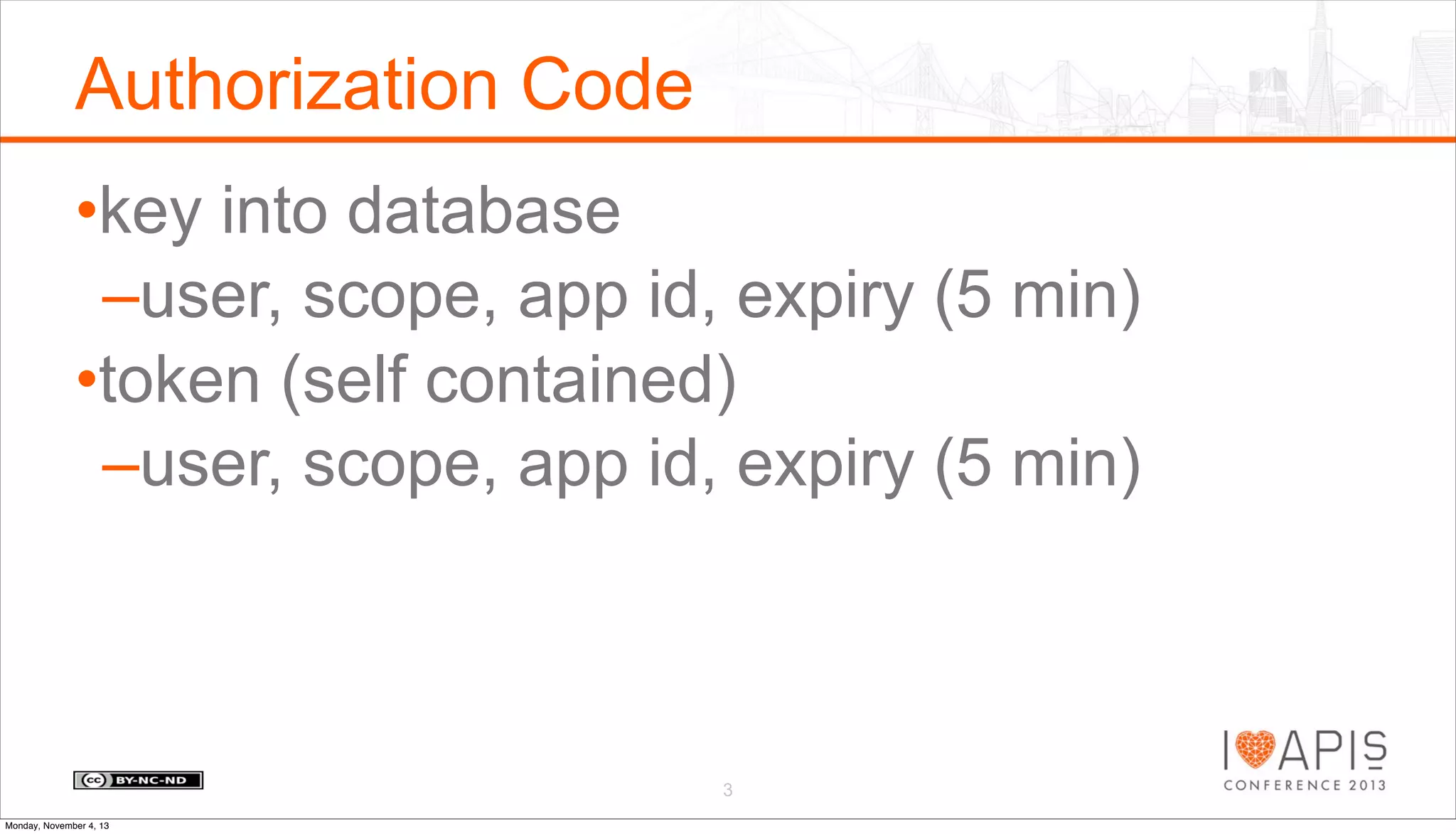
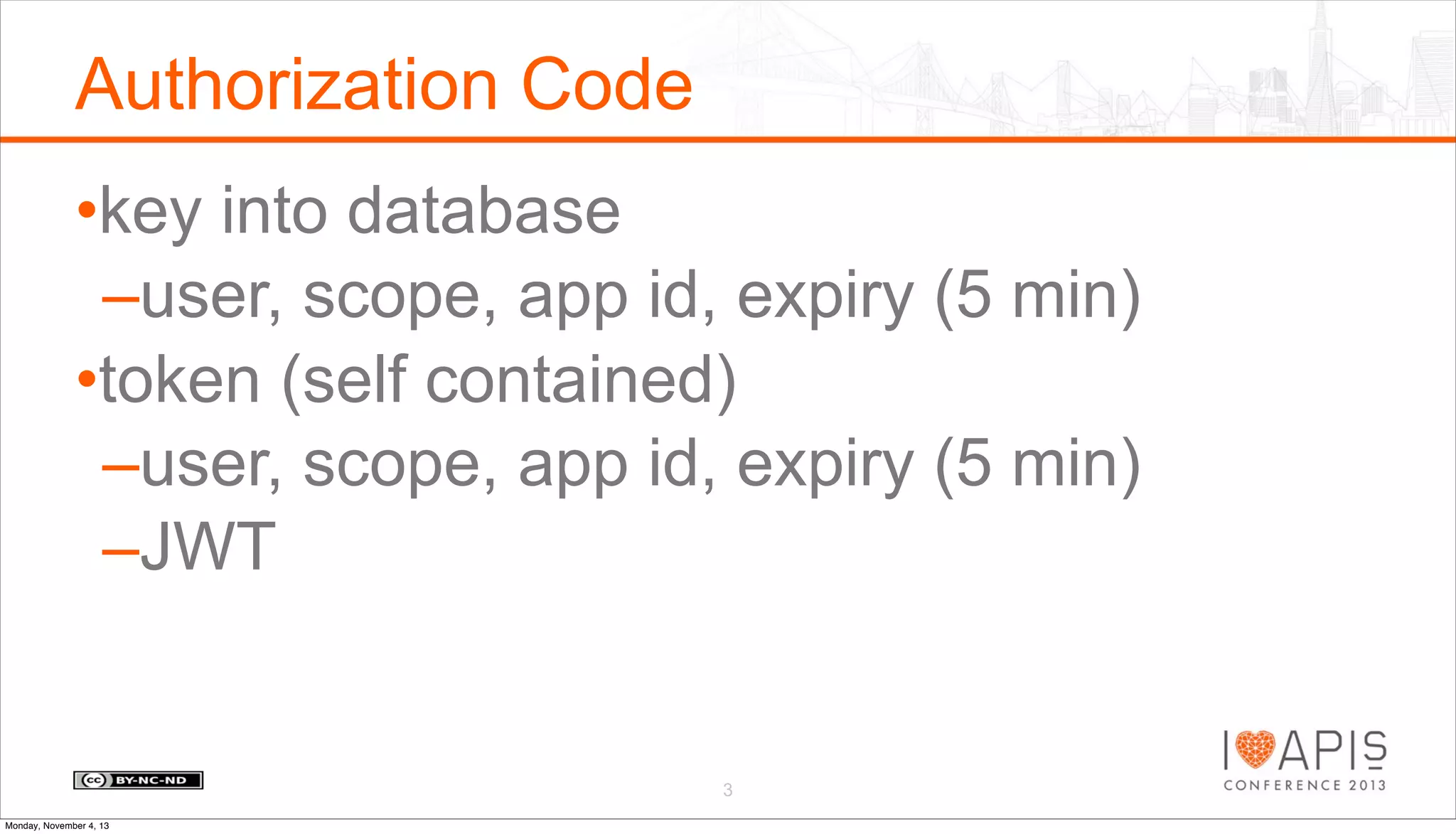
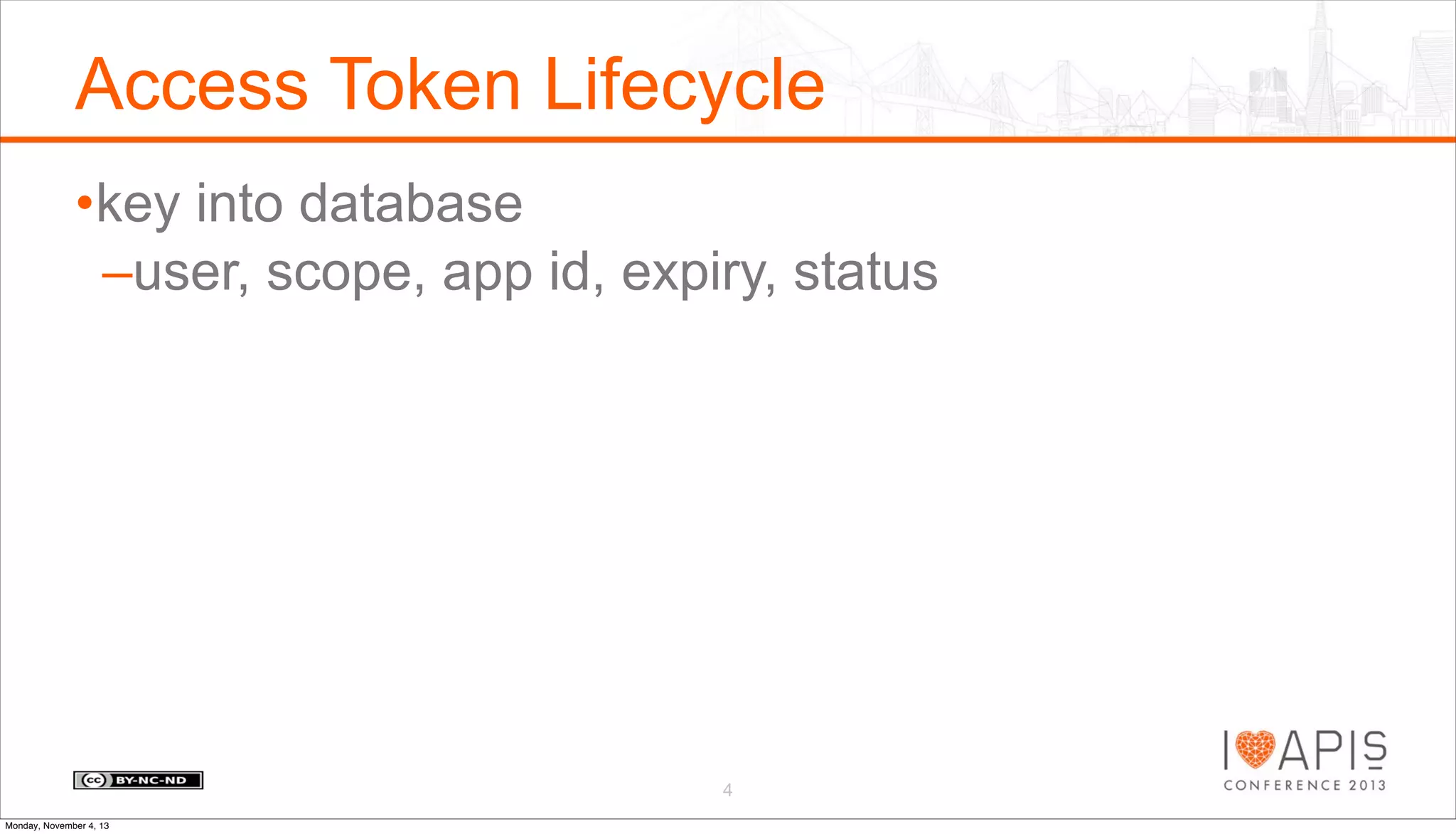
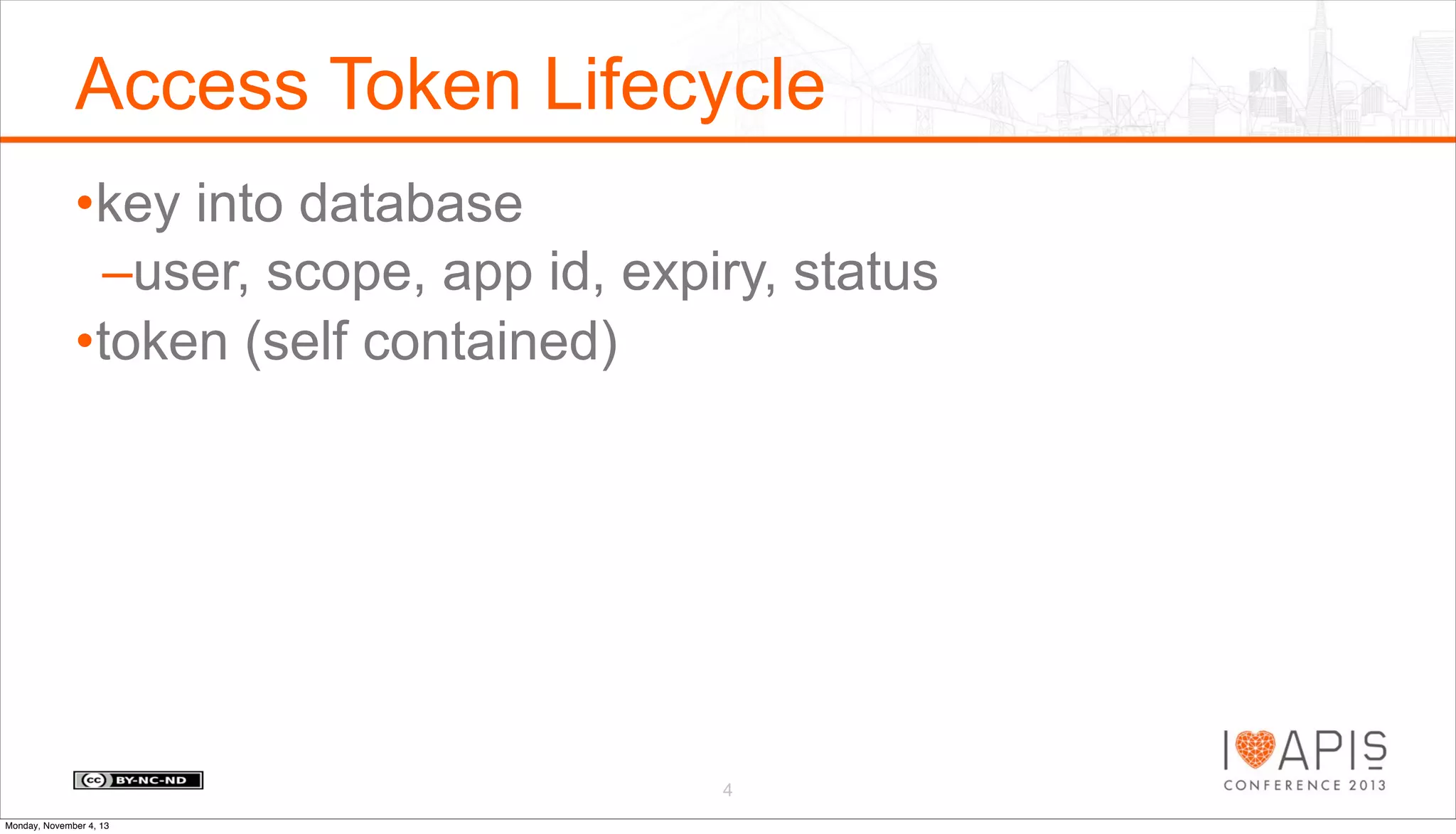
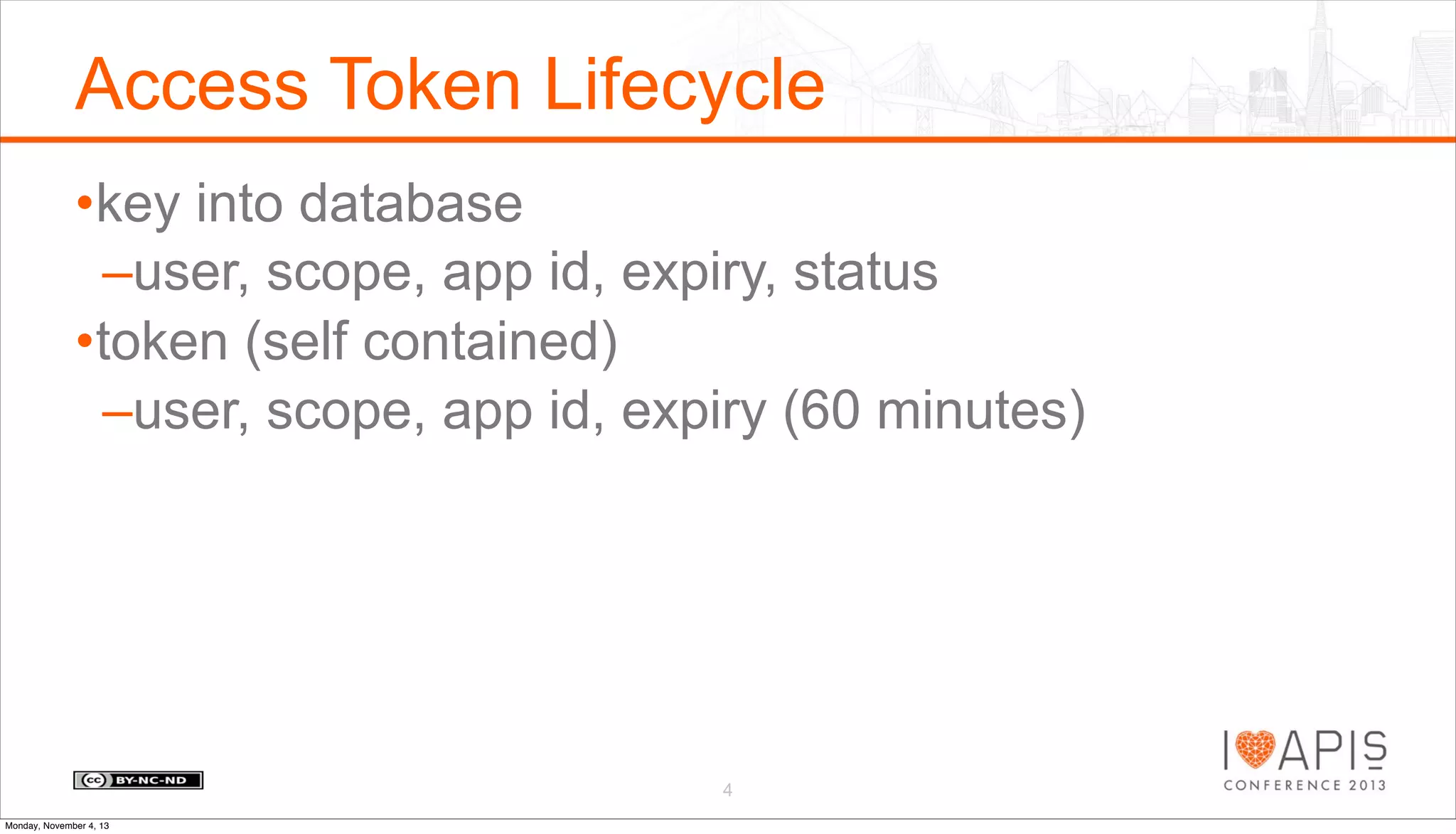
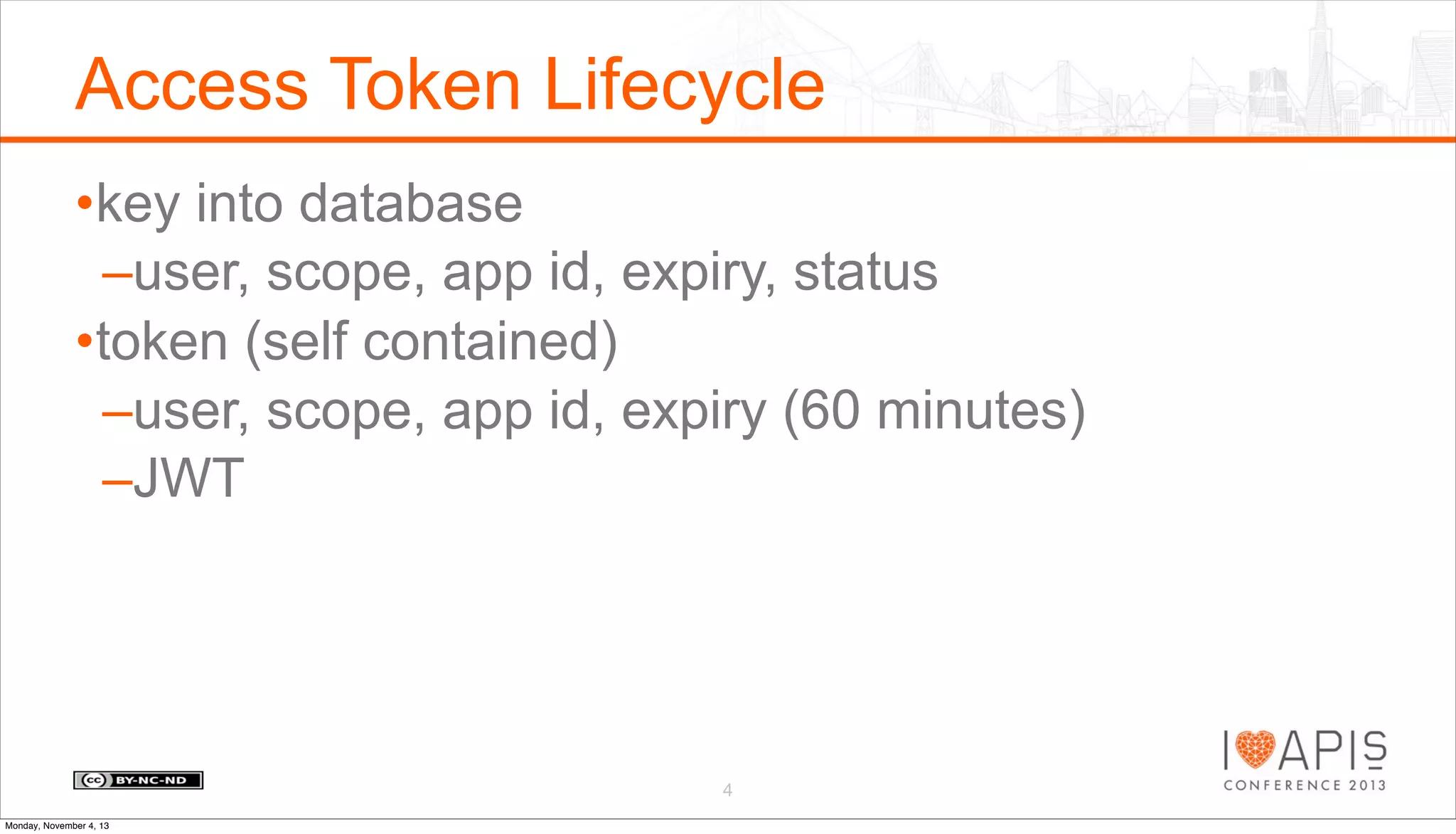
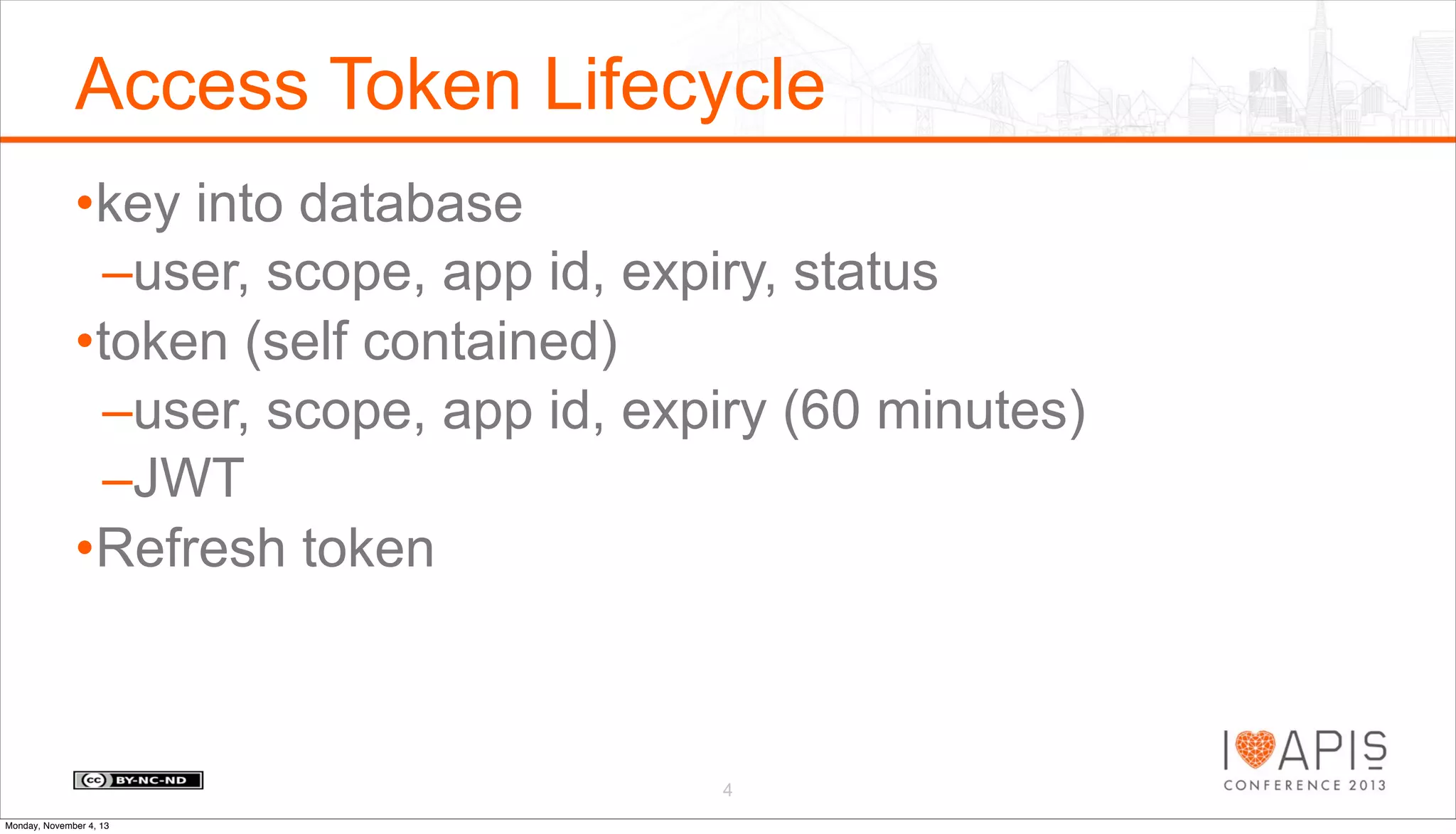
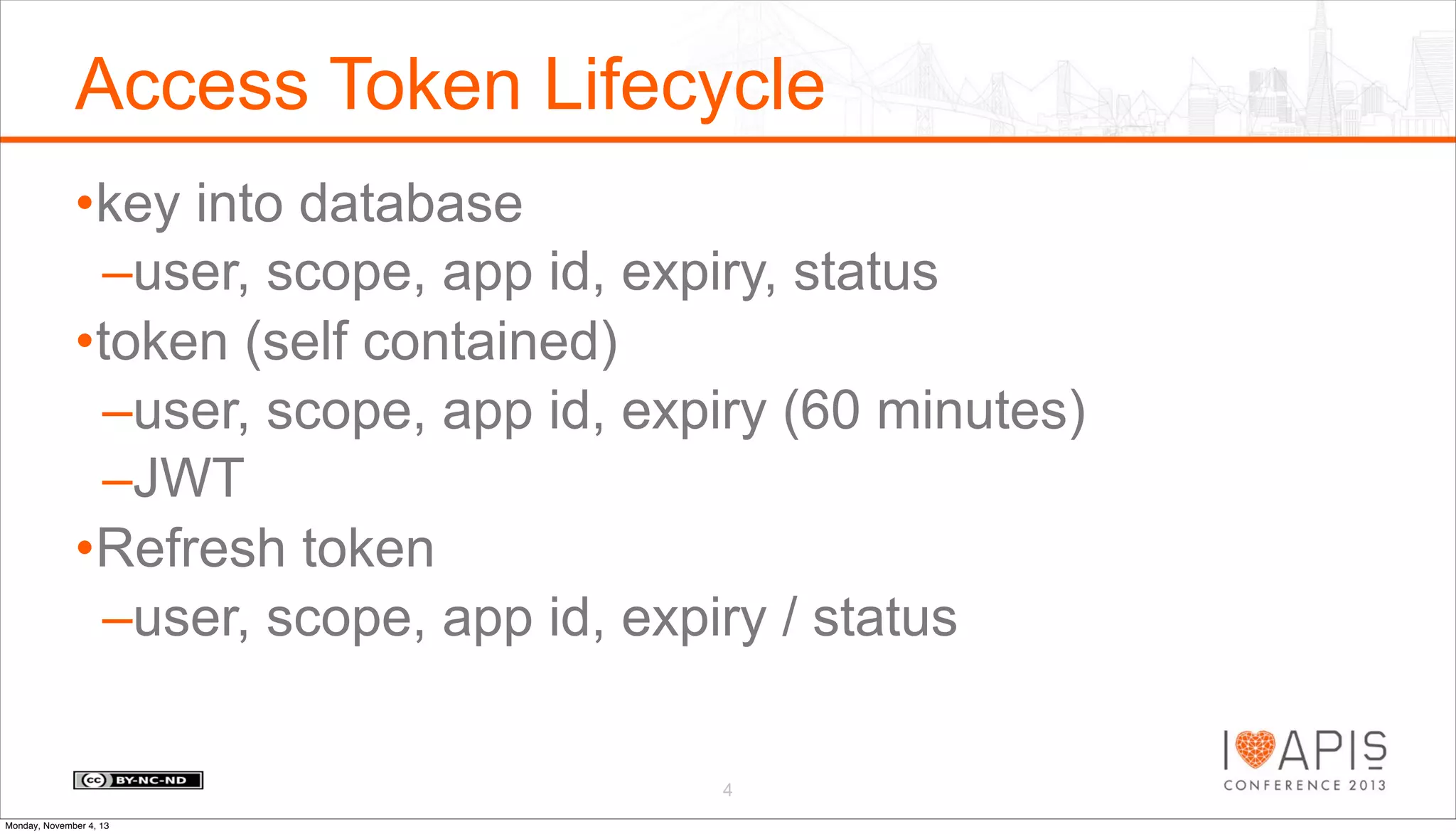
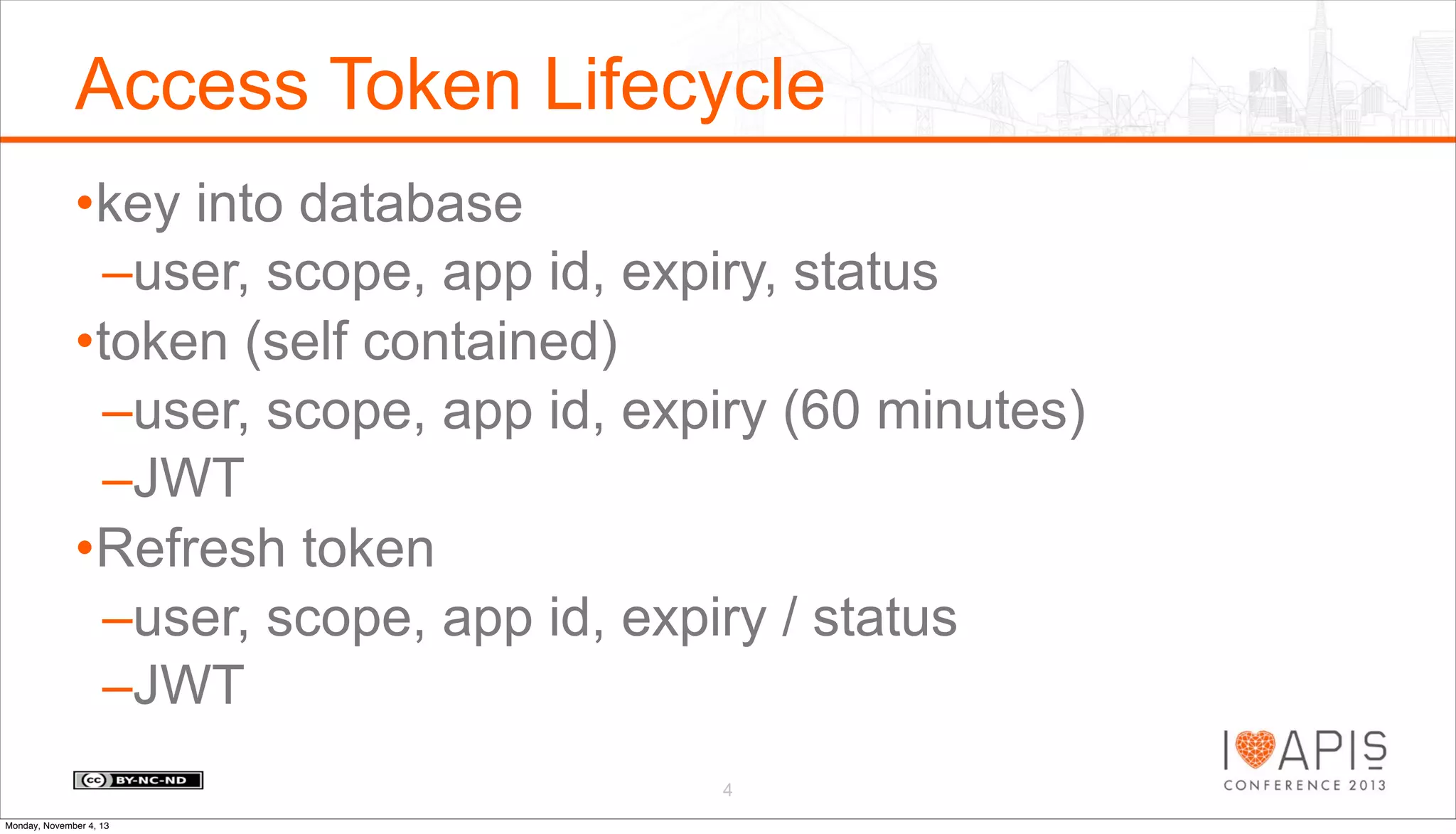
The document outlines a presentation agenda covering access control, OAuth history, OAuth flows, implementation steps, and potential issues that may arise. It details the lifecycle of authorization codes and access tokens, including database keying and JWT considerations. Additionally, it addresses common problems such as client secret compromises, access token vulnerabilities, and user revocation of authorization.