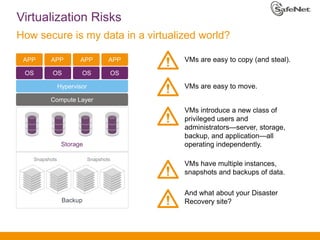
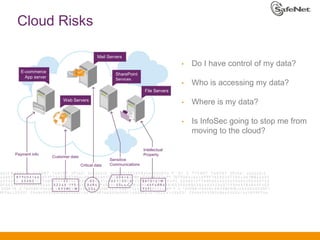
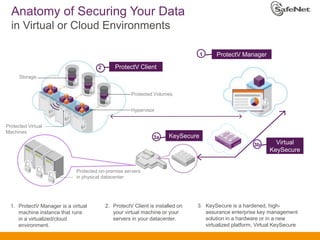
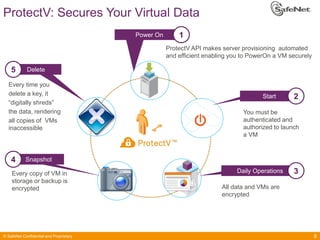
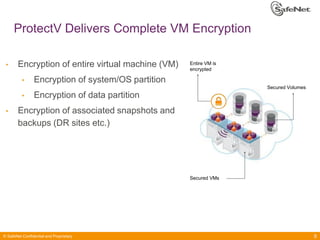
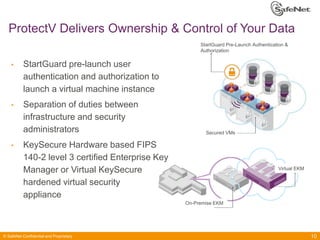
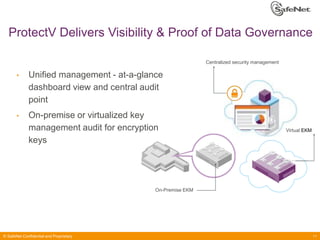
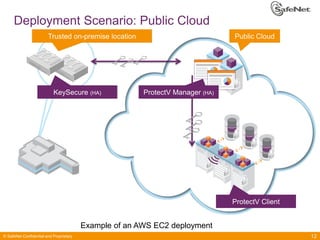
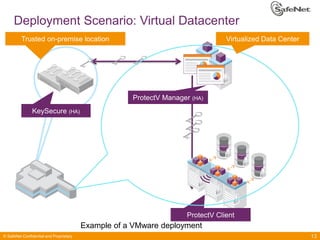
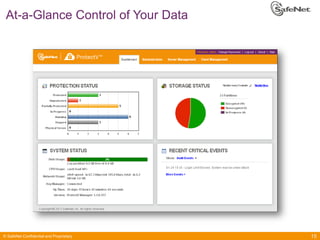
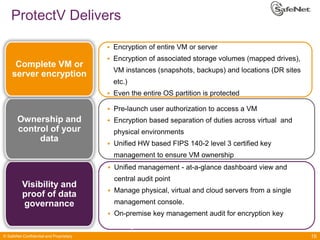
The document outlines SafeNet ProtectV, a comprehensive solution for data protection in virtual infrastructure, addressing risks associated with virtualization such as data accessibility and control. ProtectV enables isolation, secure migration, and encrypts entire virtual machines while managing authentication and providing an audit trail for data governance. It supports various environments, including AWS and VMware, and adds minimal performance impact of 10-15%.