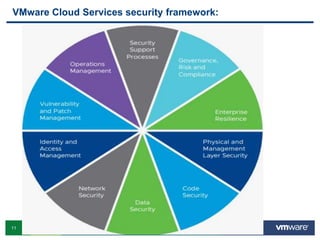
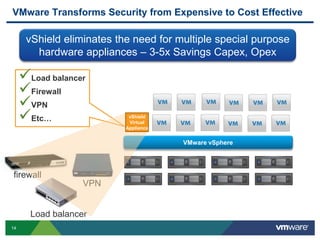
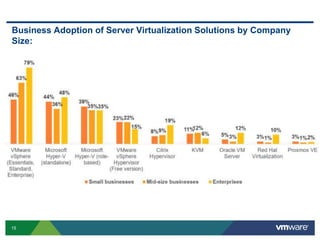
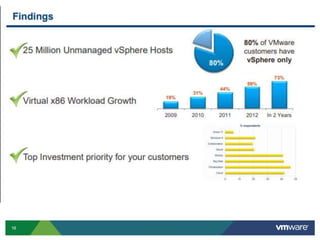
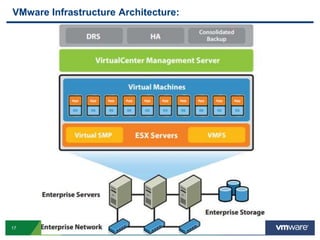
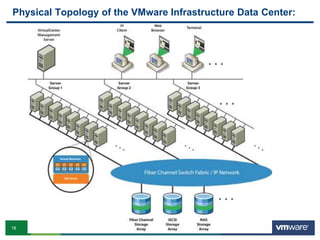
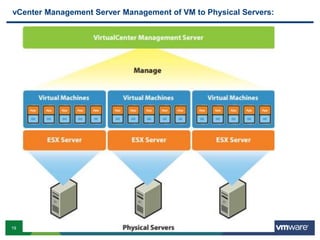
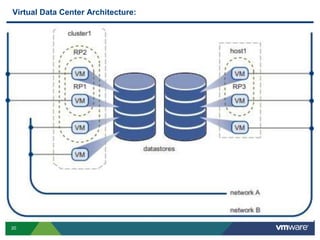
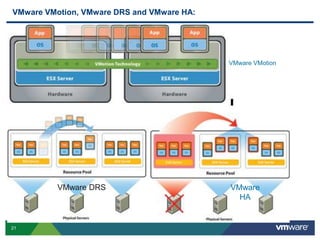
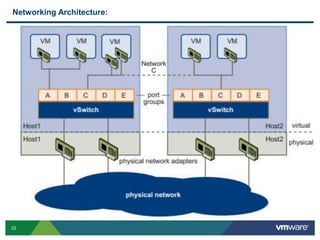
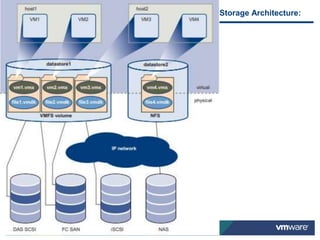
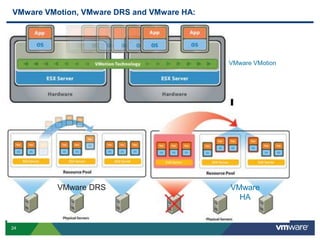
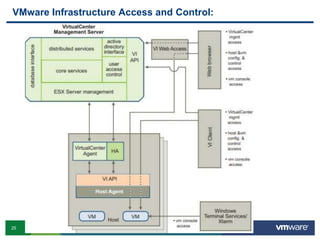
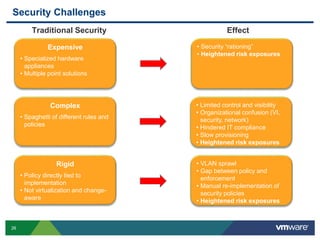
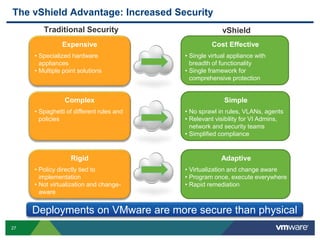
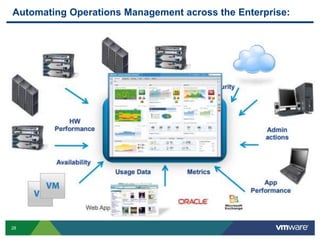
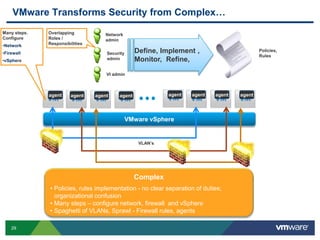
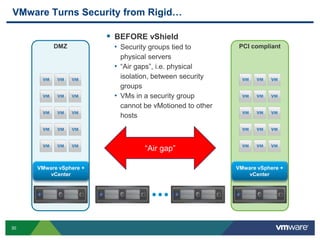
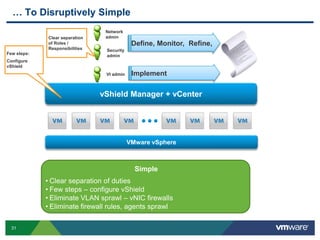
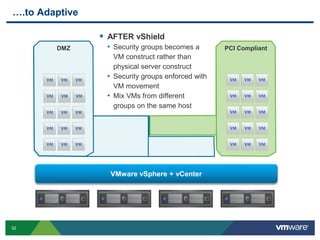
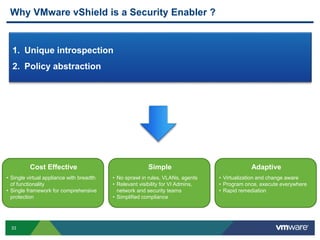
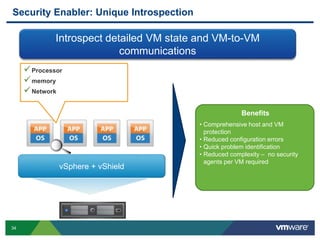
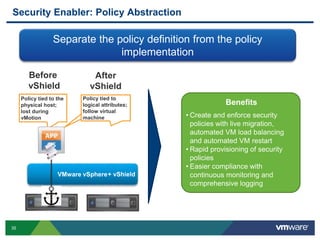
VMware is a global leader in cloud infrastructure and digital workspace technology. It offers various virtualization products including vSphere for server virtualization, NSX for network virtualization, and Horizon for desktop and application virtualization. VMware's virtualization software allows multiple operating systems to run on a single physical host. VMware vShield provides security advantages over traditional hardware-based security appliances by offering a single virtual appliance with comprehensive protection capabilities that is cost-effective, simple to use, and adaptive to virtualized environments.