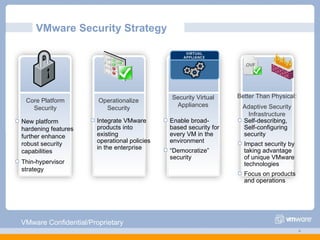
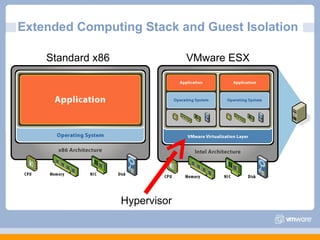
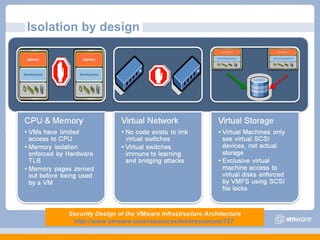
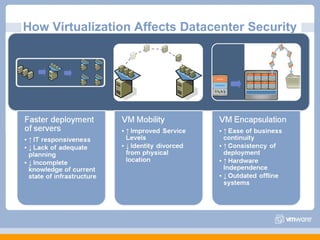
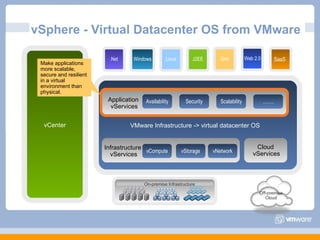
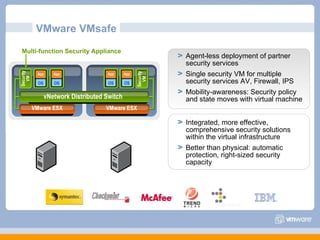
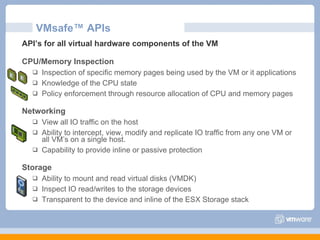
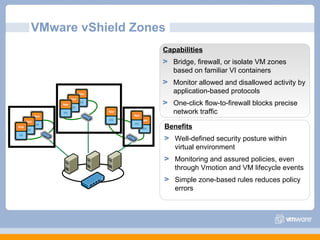
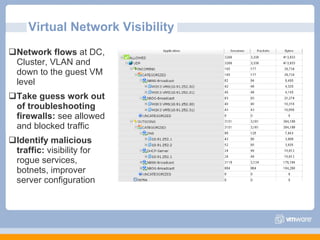
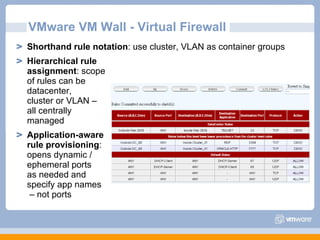
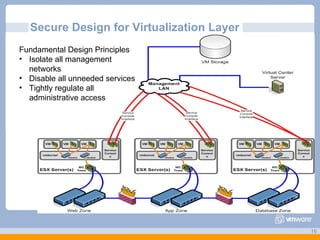
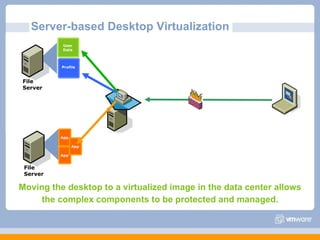
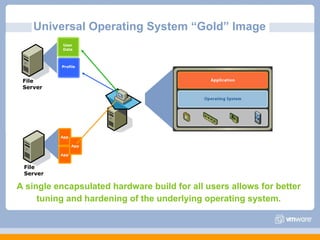
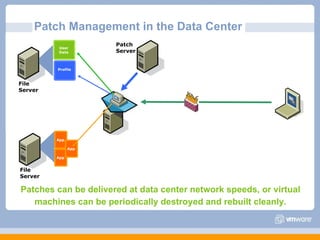
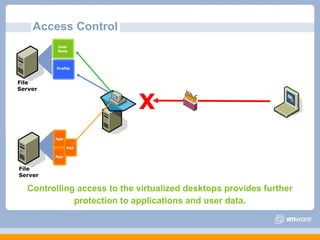
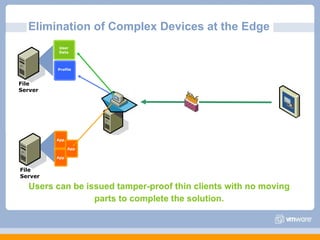
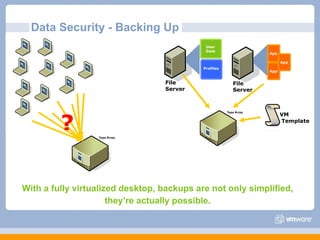
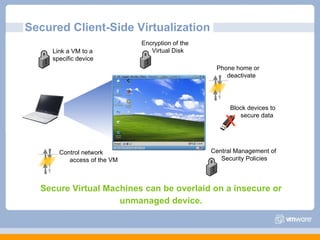
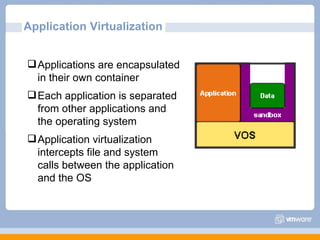
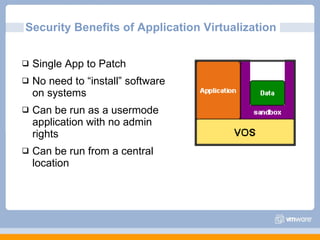
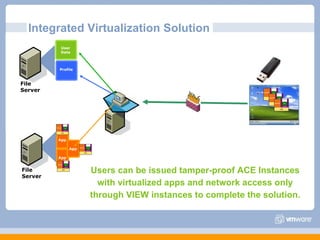
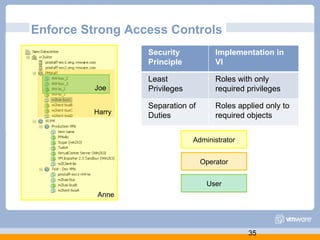
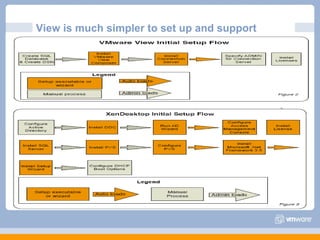
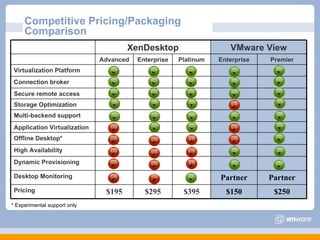
The document discusses VMware's security strategy and how virtualization provides security benefits. It outlines how virtualization allows automation of manual security processes, improves forensics capabilities, and makes patching and recovery faster. VMware focuses on integrating products into existing security policies while enabling broad security for all VMs. Features like vShield Zones and VMsafe appliances provide centralized security management and protection of virtual environments. Virtualization also extends these security advantages from the datacenter to endpoint devices through portable client-side virtual machines.