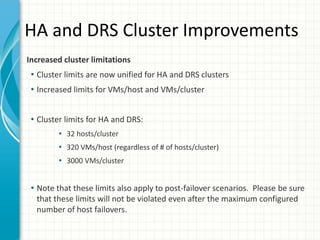
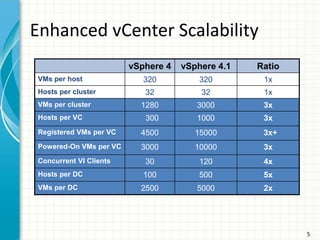
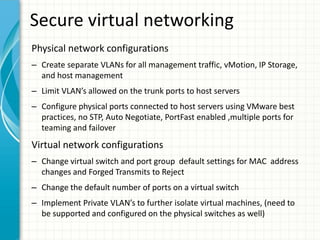
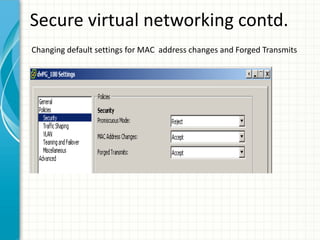
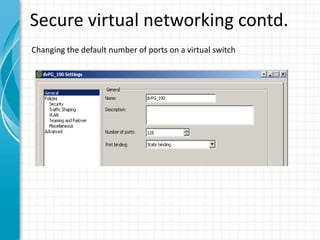
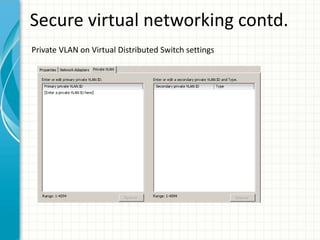
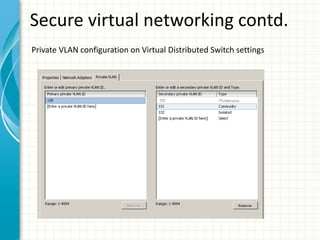
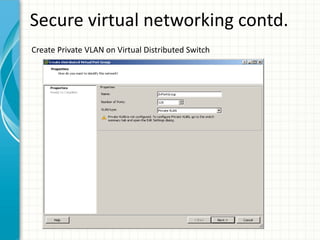
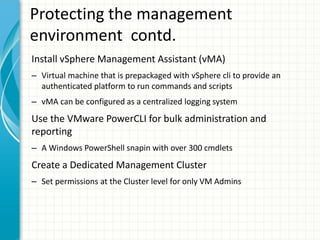
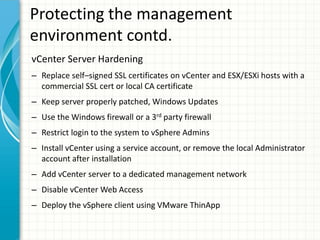
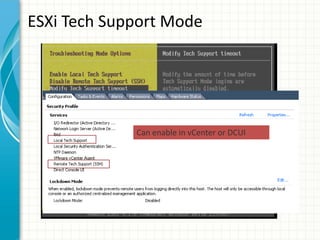
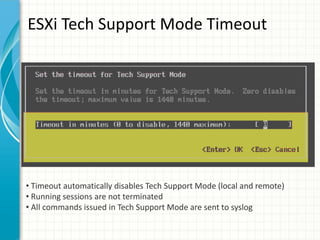
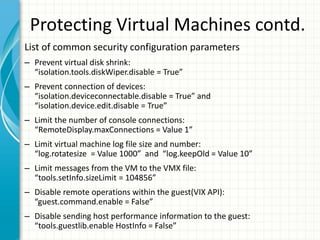
The document provides tips for improving performance and security in a vSphere 4.1 environment. It discusses new features in vSphere 4.1 related to networking, storage, memory compression, and management. It then outlines best practices for securing the virtual infrastructure, including using virtual networking segmentation, hardening ESXi hosts, protecting the vCenter management environment, and securing individual virtual machines. The document recommends configuration changes, tools, and resources to improve the security of the virtualization platform.