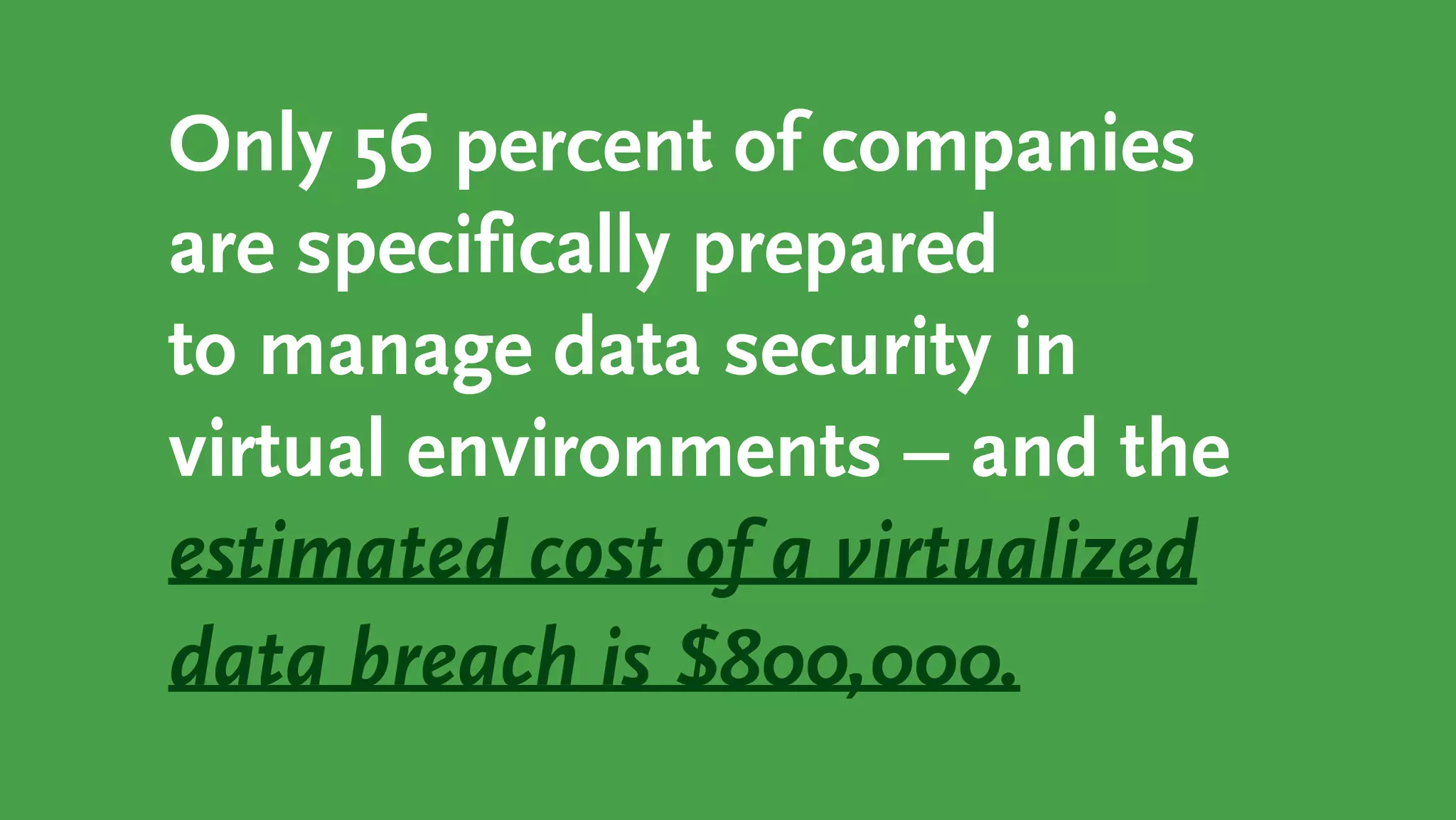
The document discusses the importance of securing virtualized data, likening sensitive company information to valuable possessions that require added protection. It highlights the increased risks and costs associated with data breaches in virtual environments, emphasizing the need for employee training and tailored security strategies. Key recommendations include educating staff on safe practices and proactively protecting data at its core, regardless of its environment.