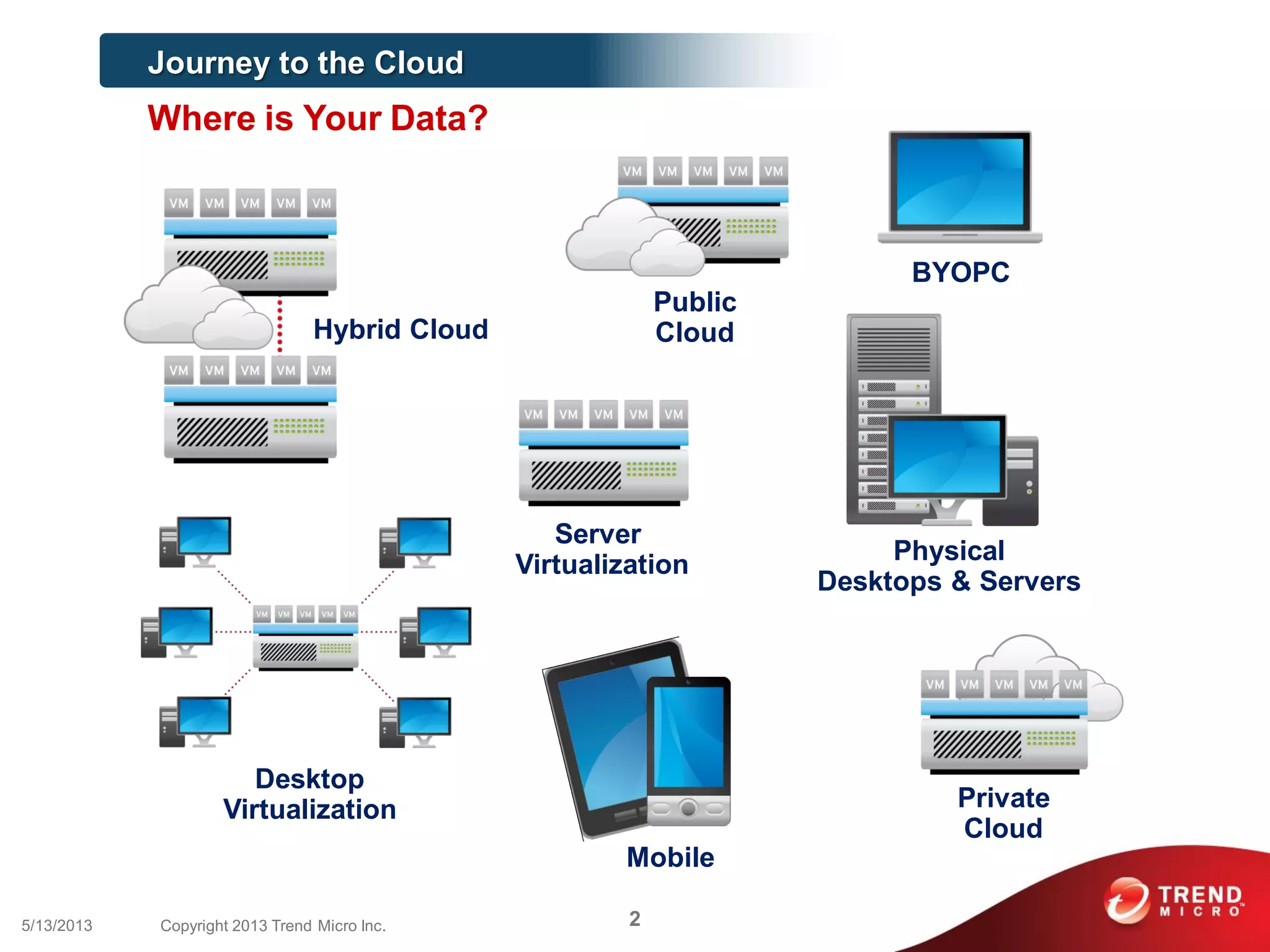
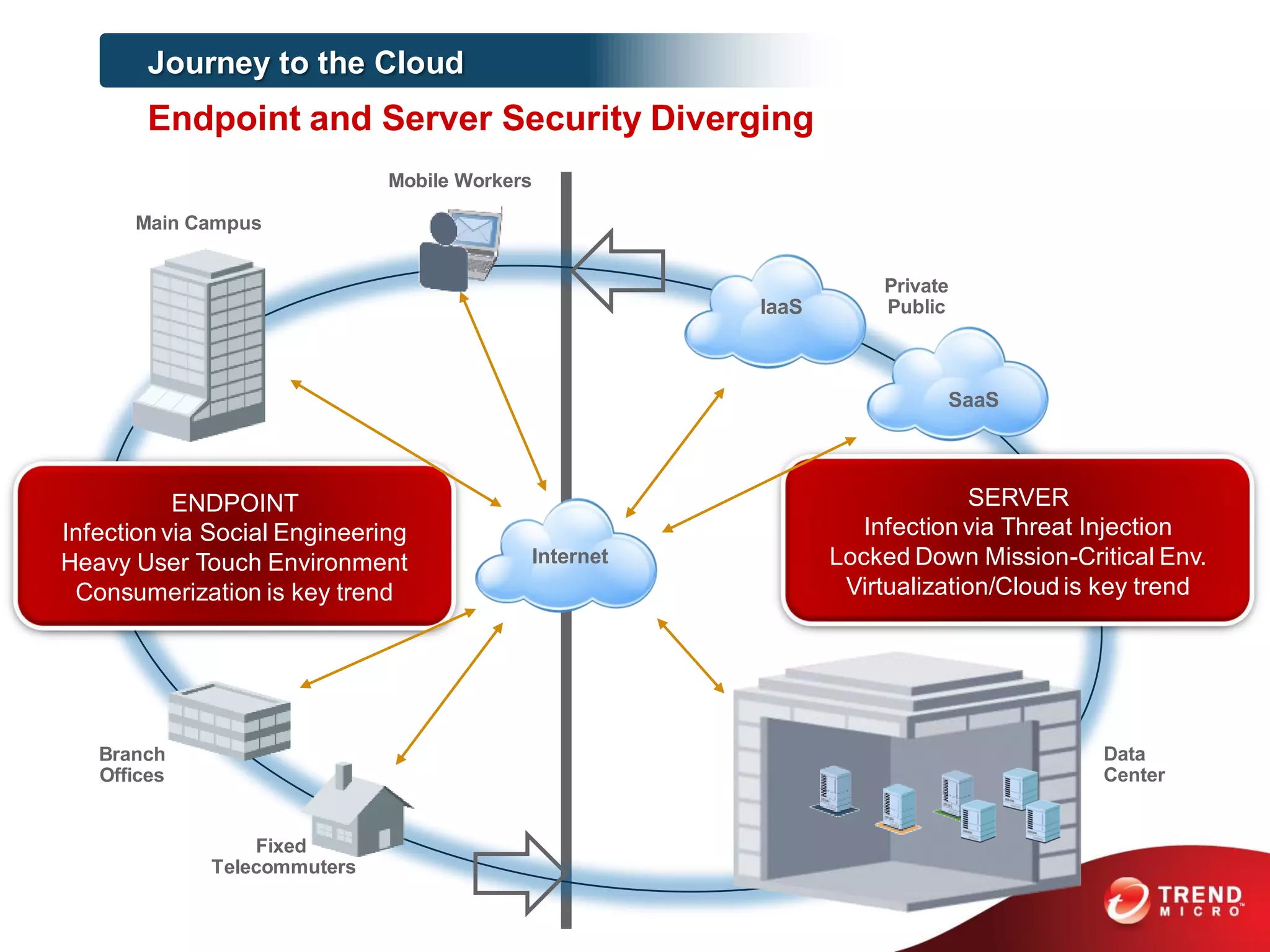
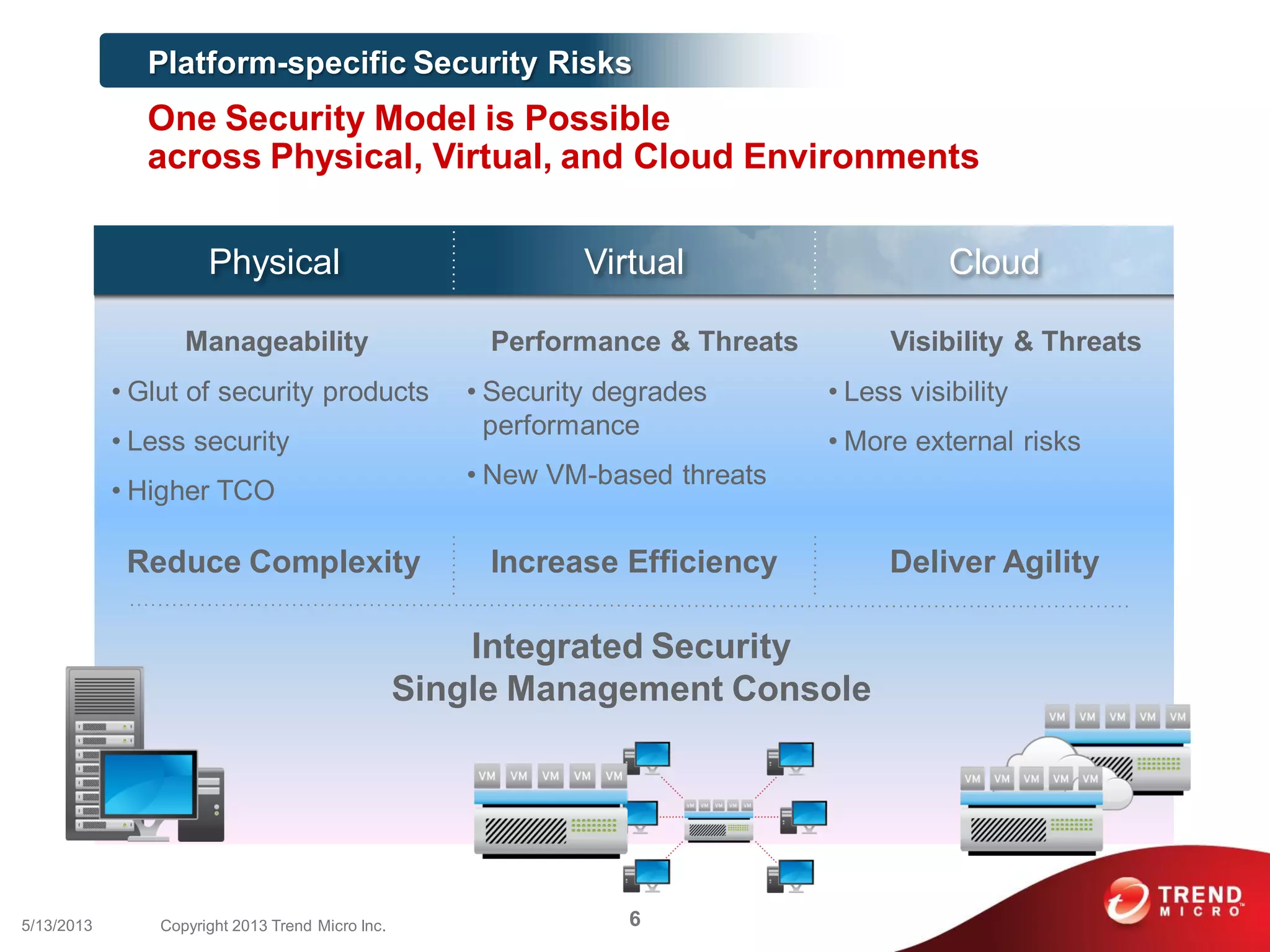
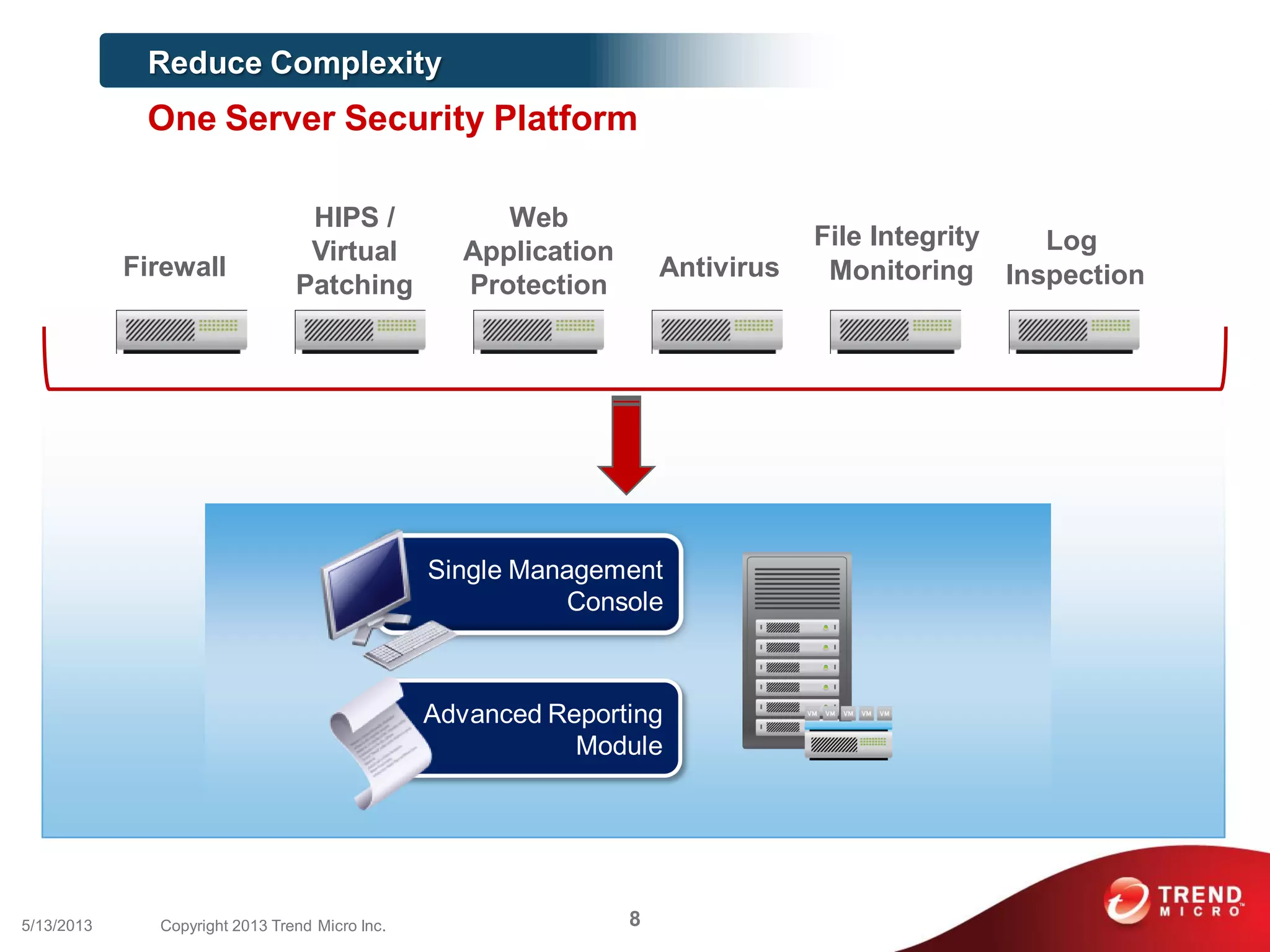
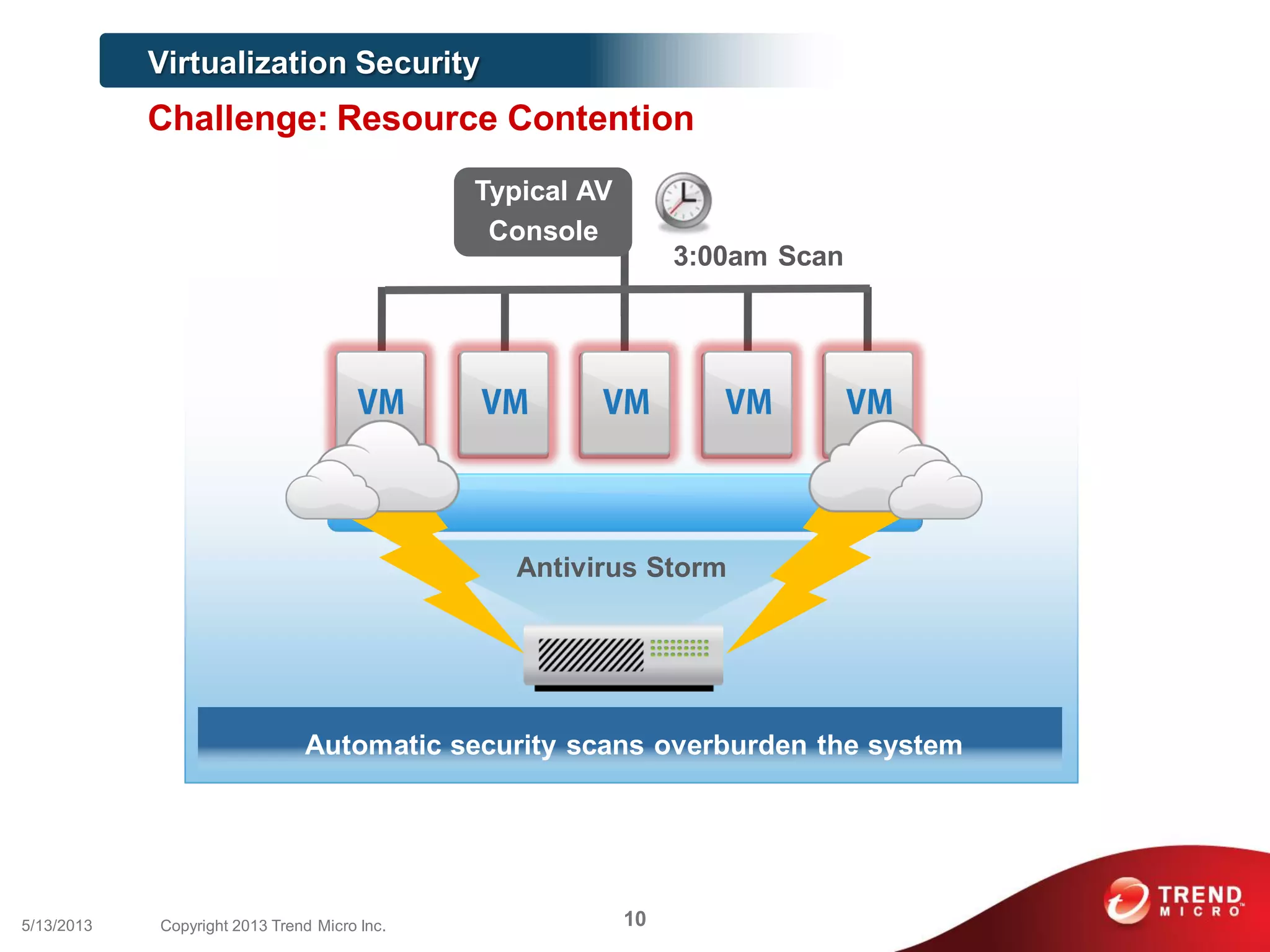
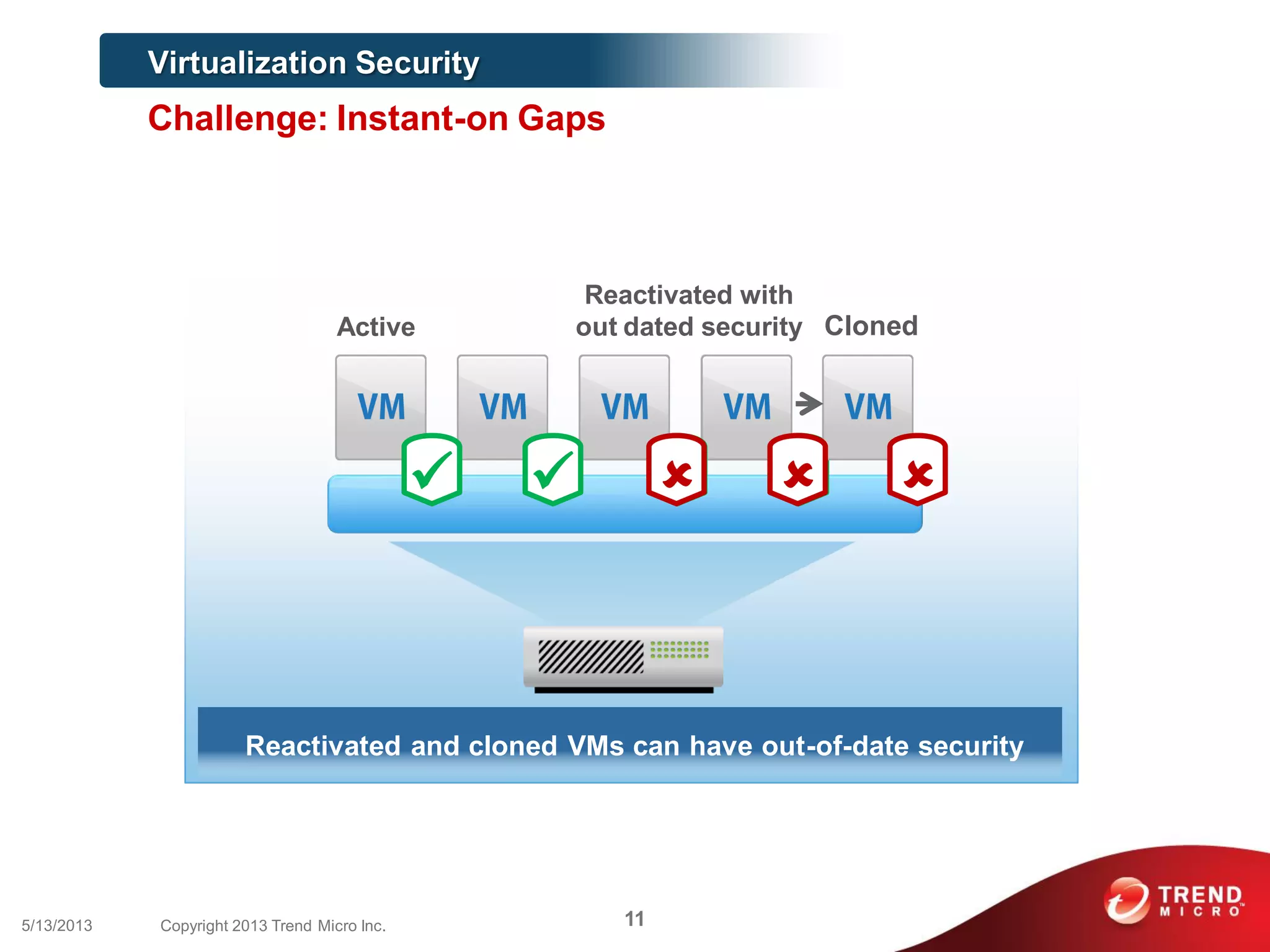
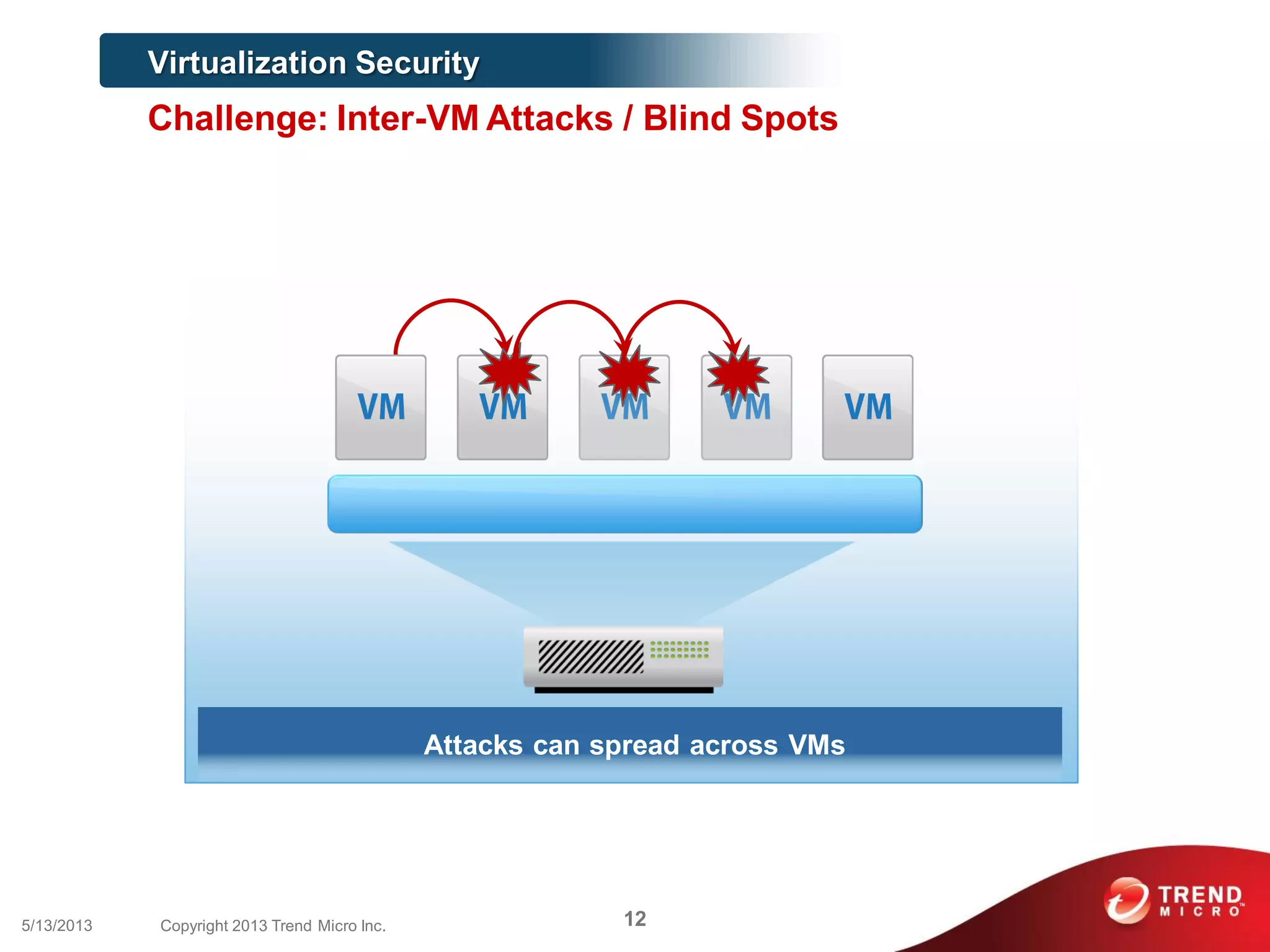
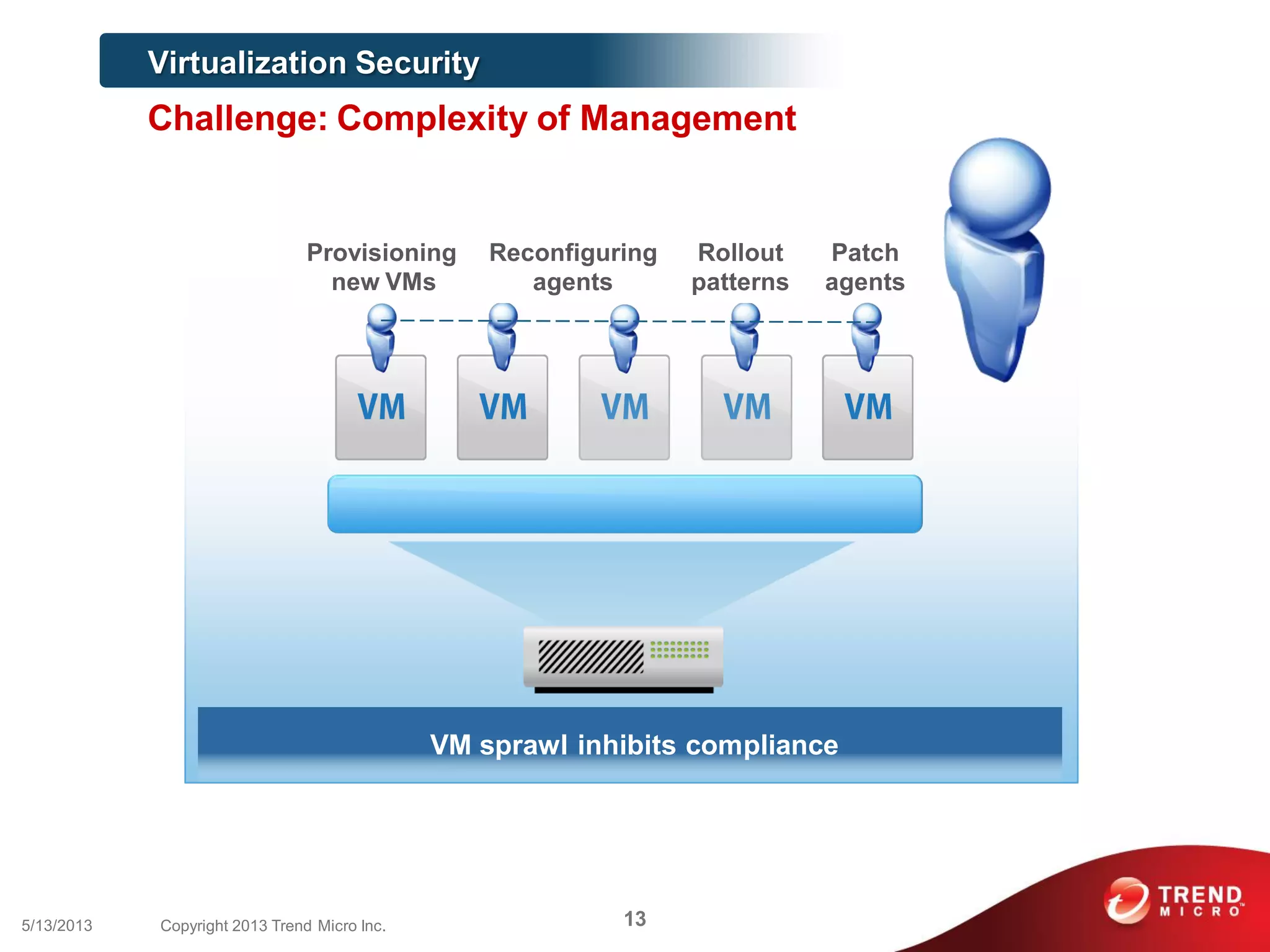
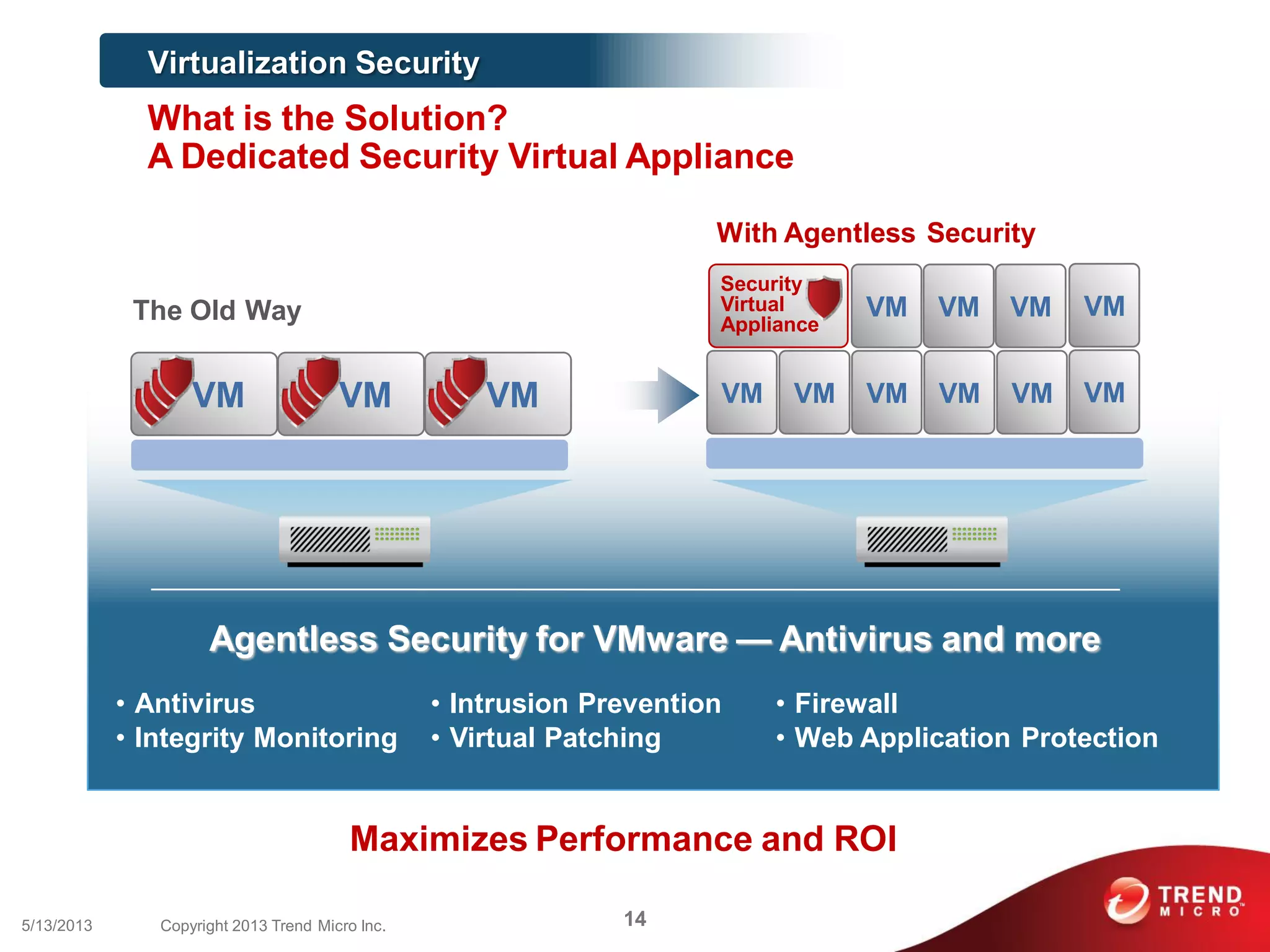
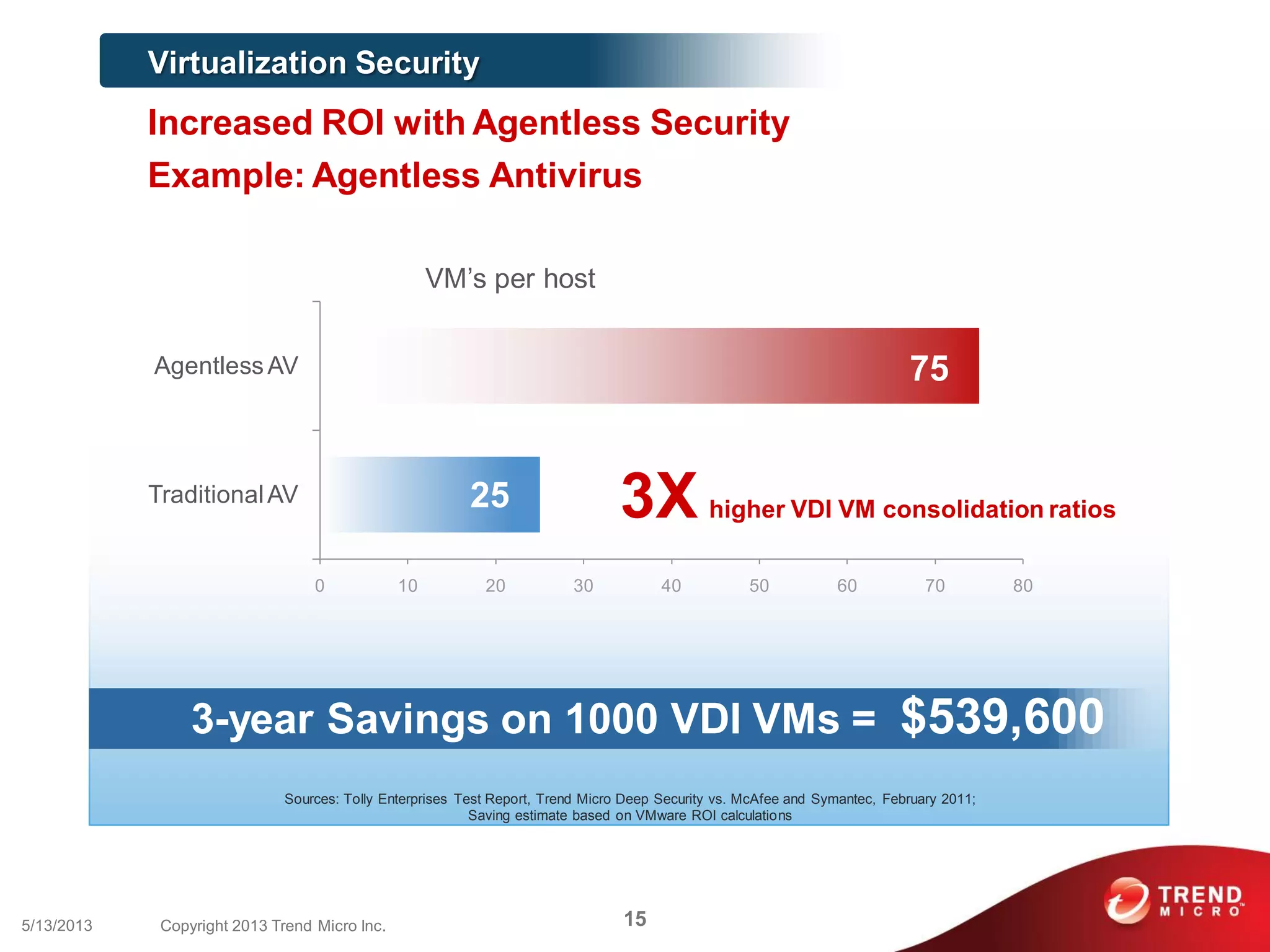
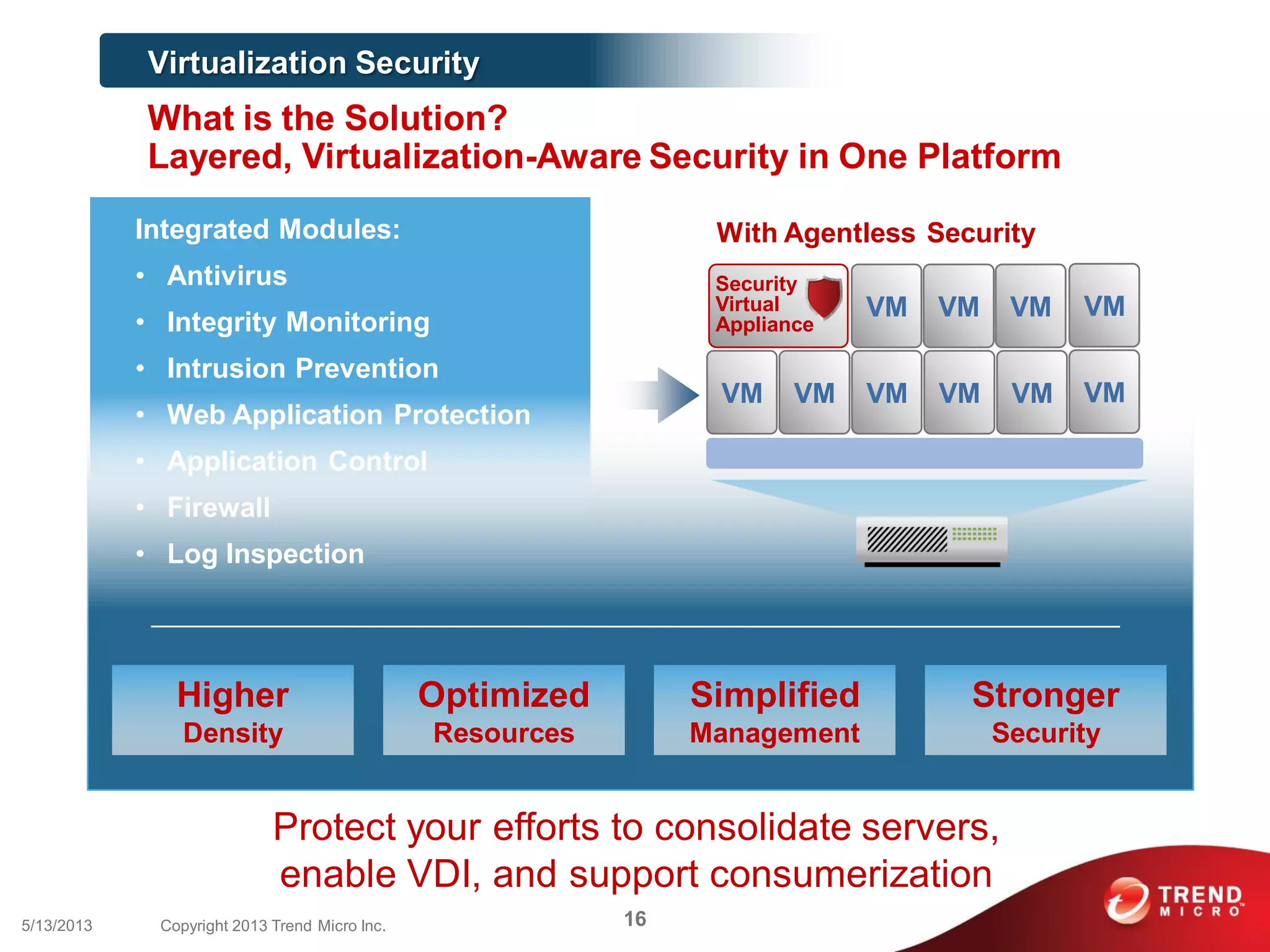
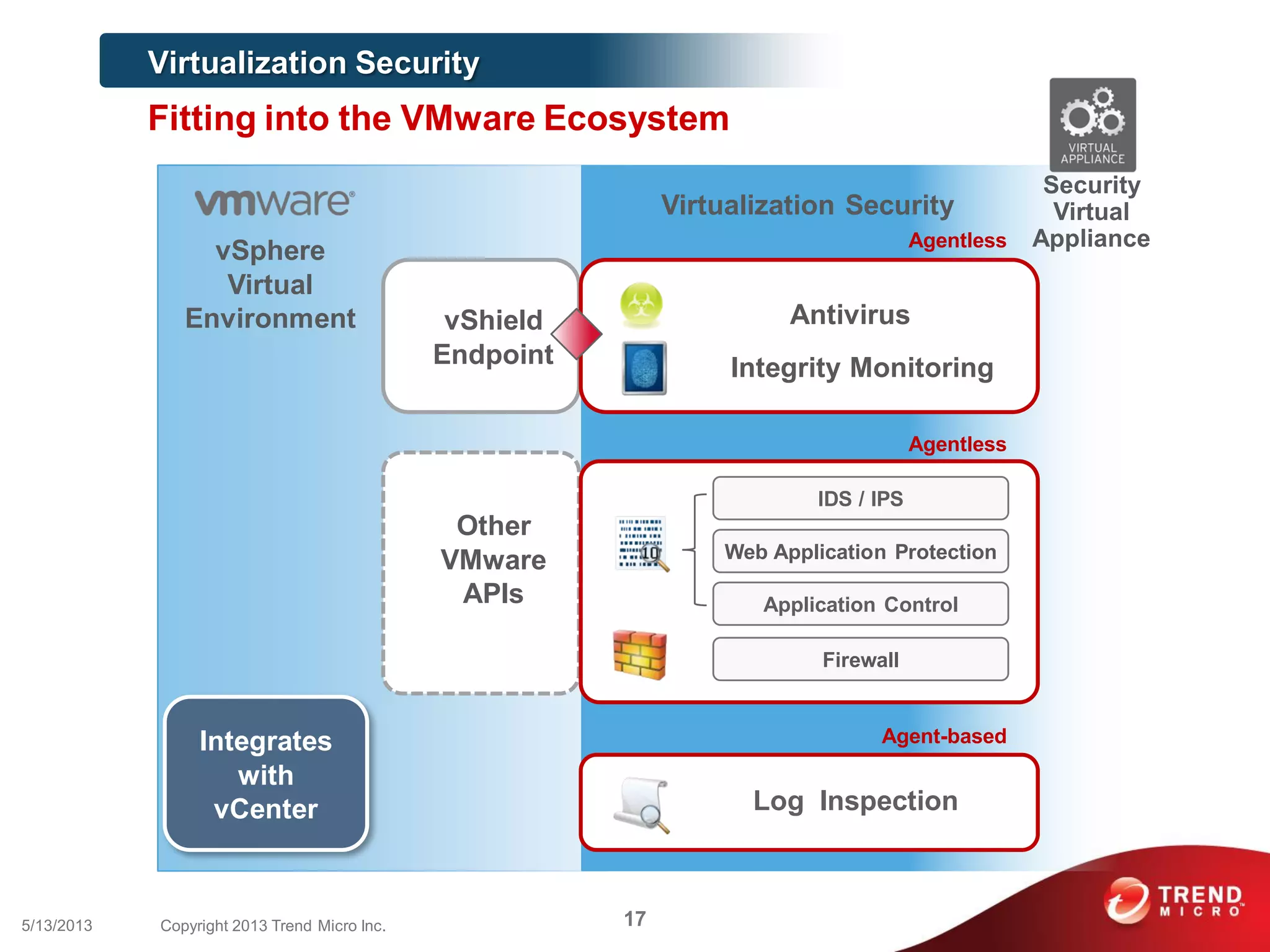
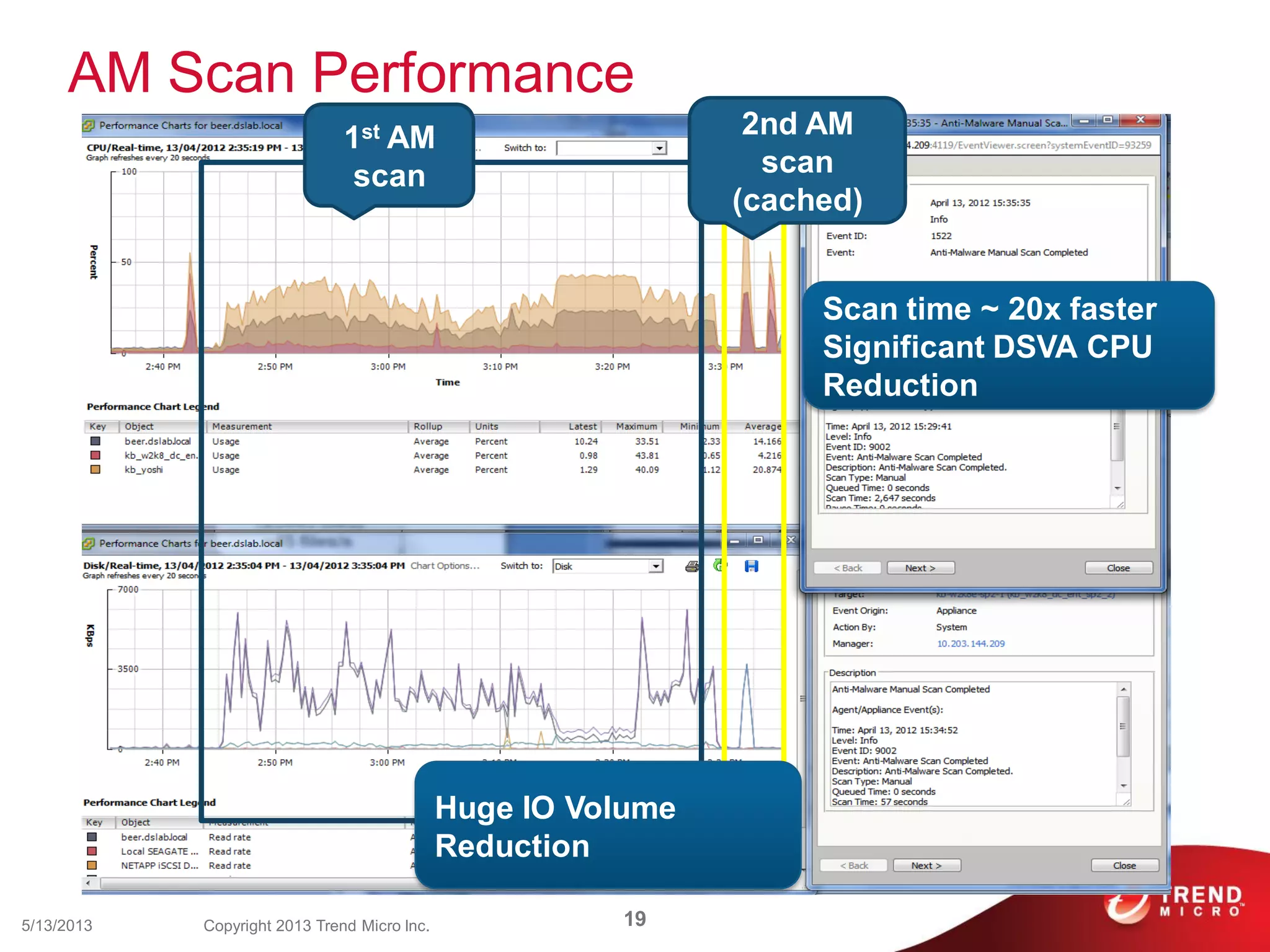
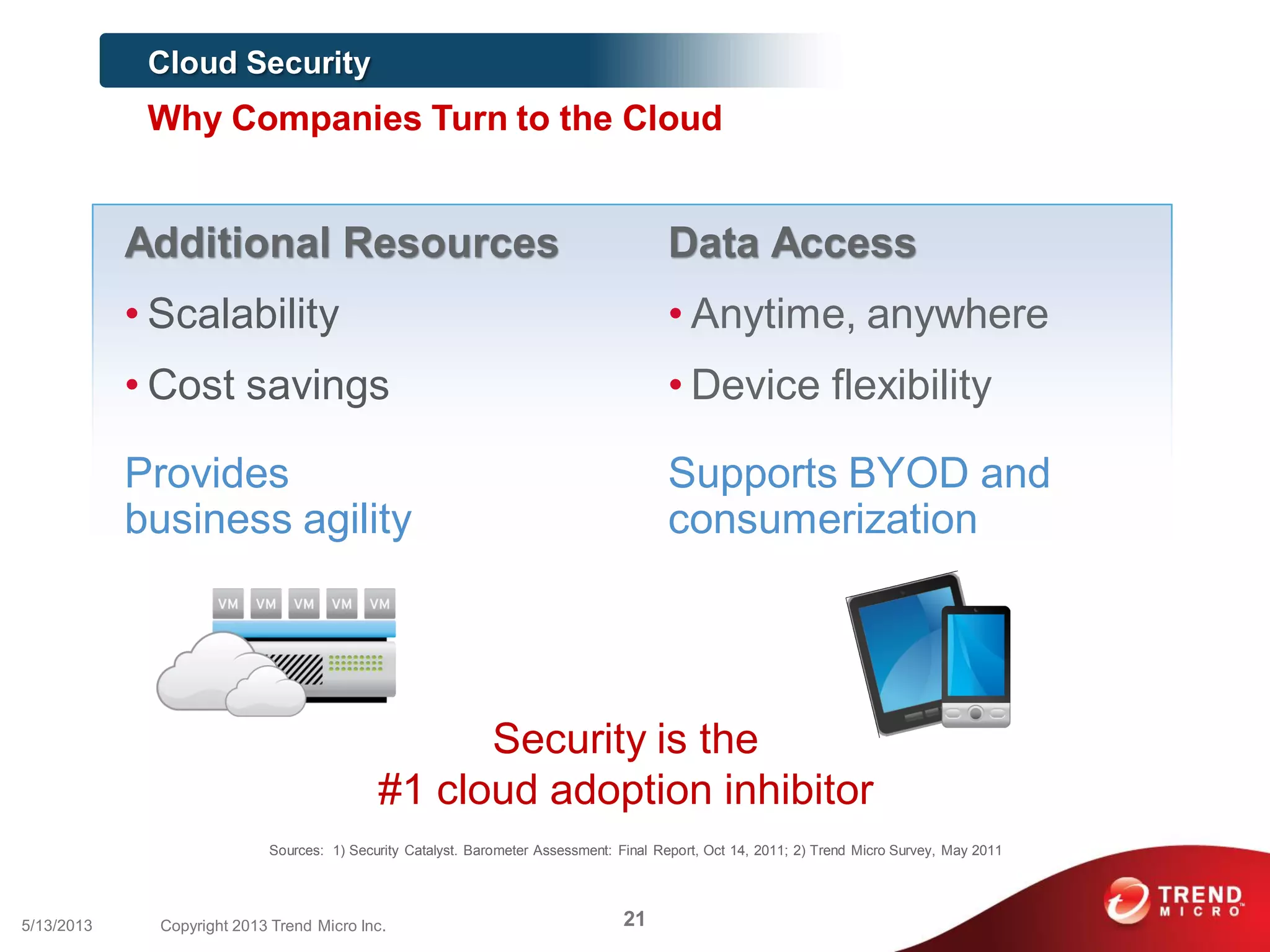
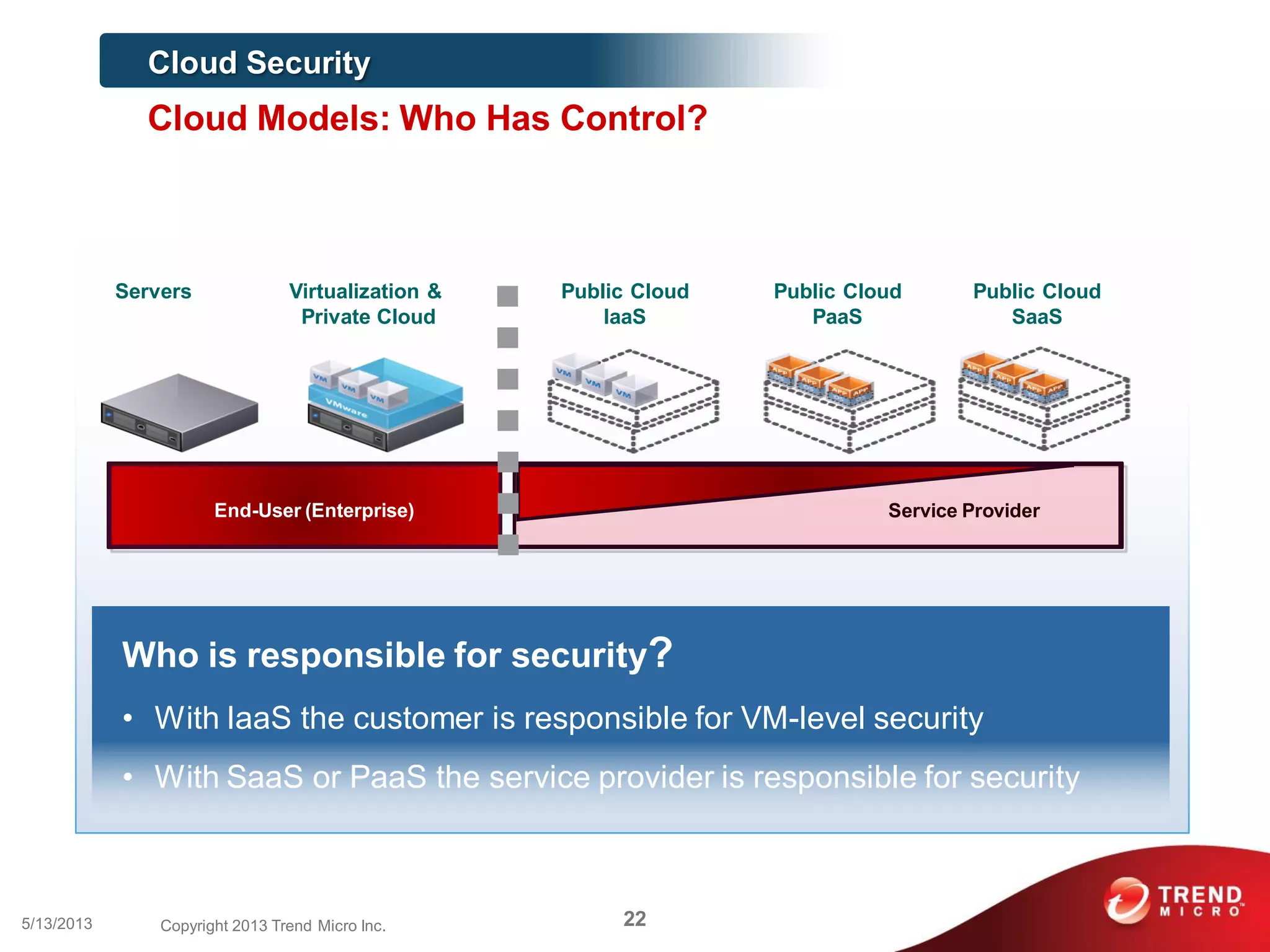
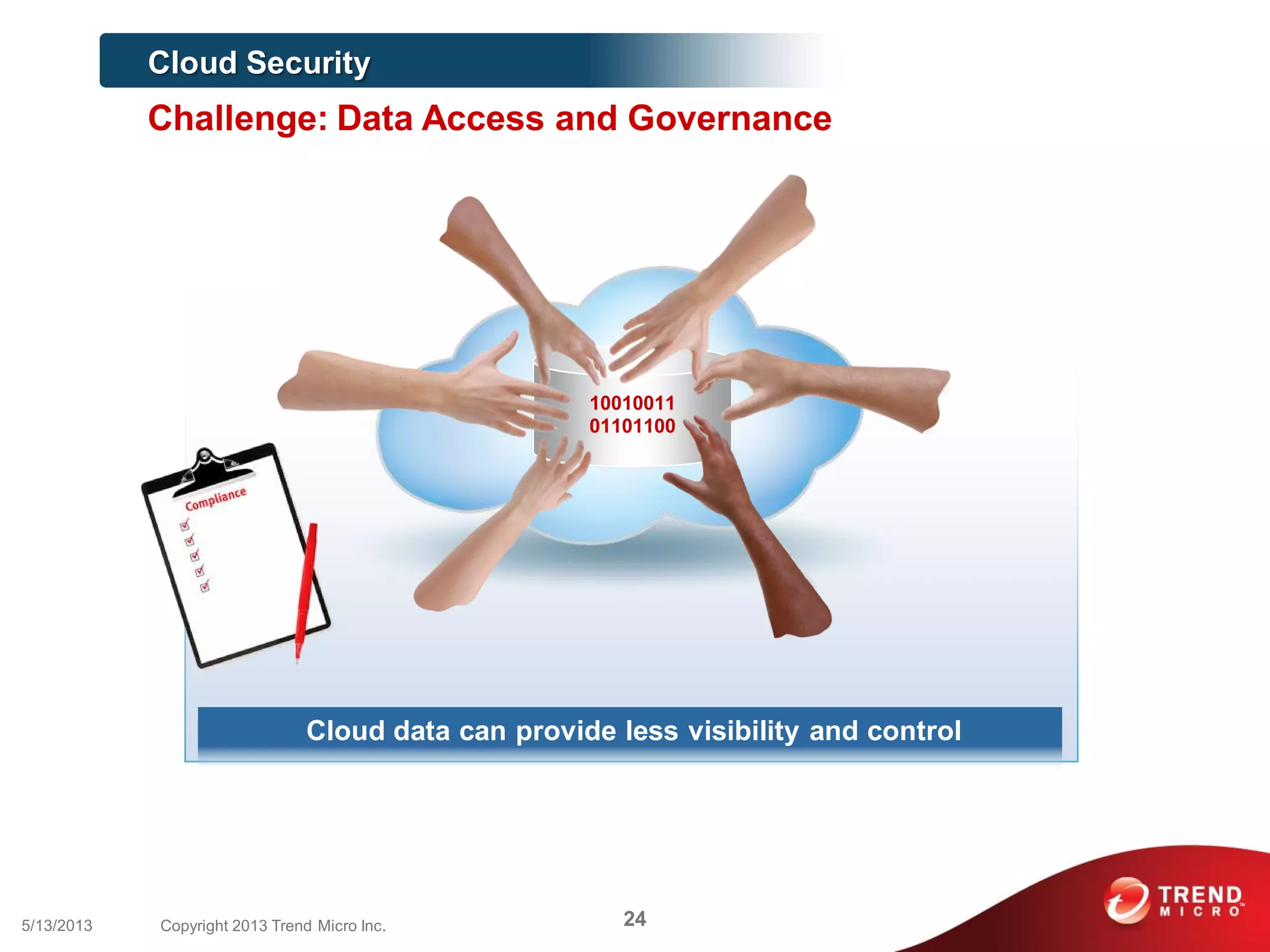
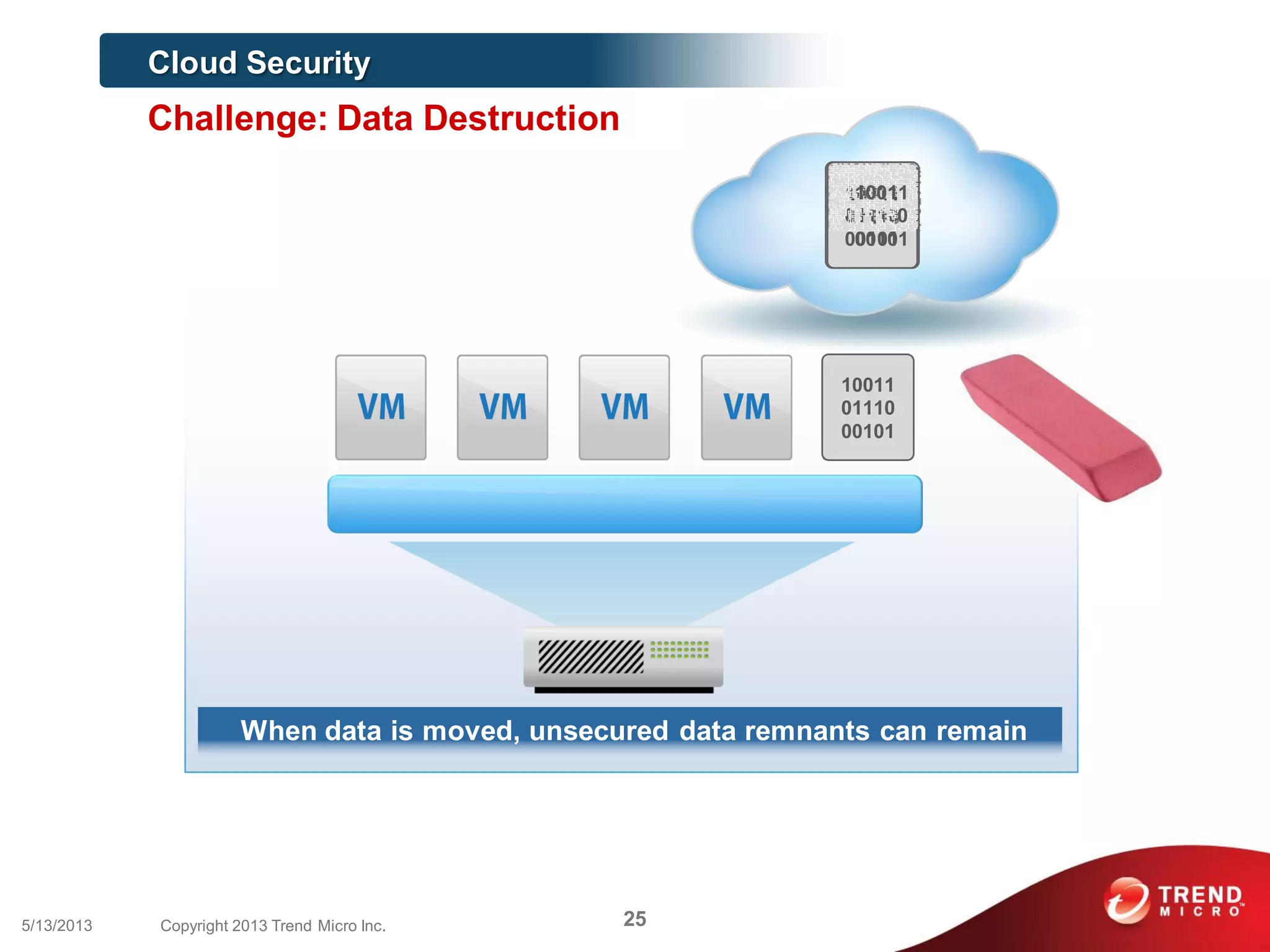
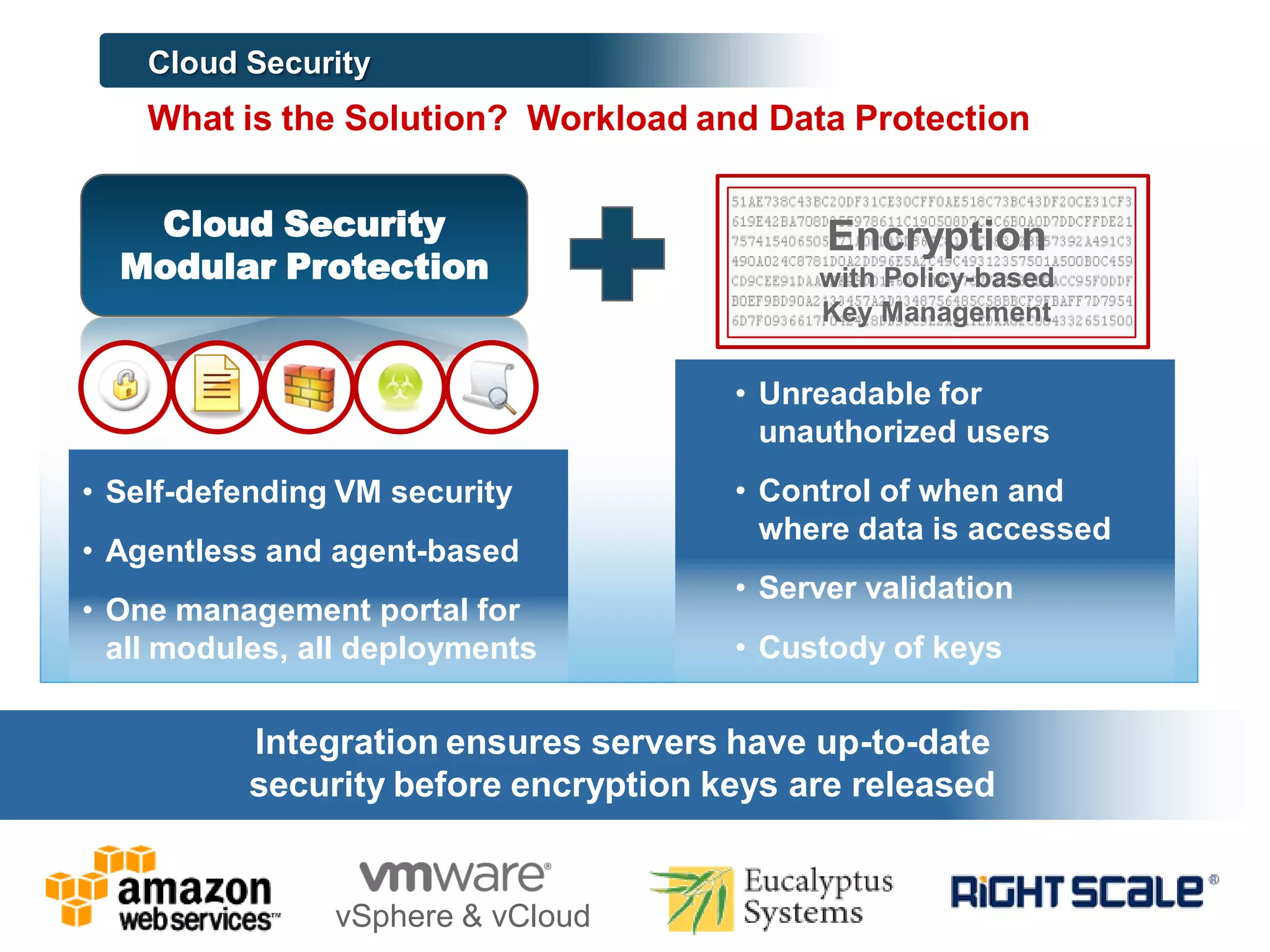
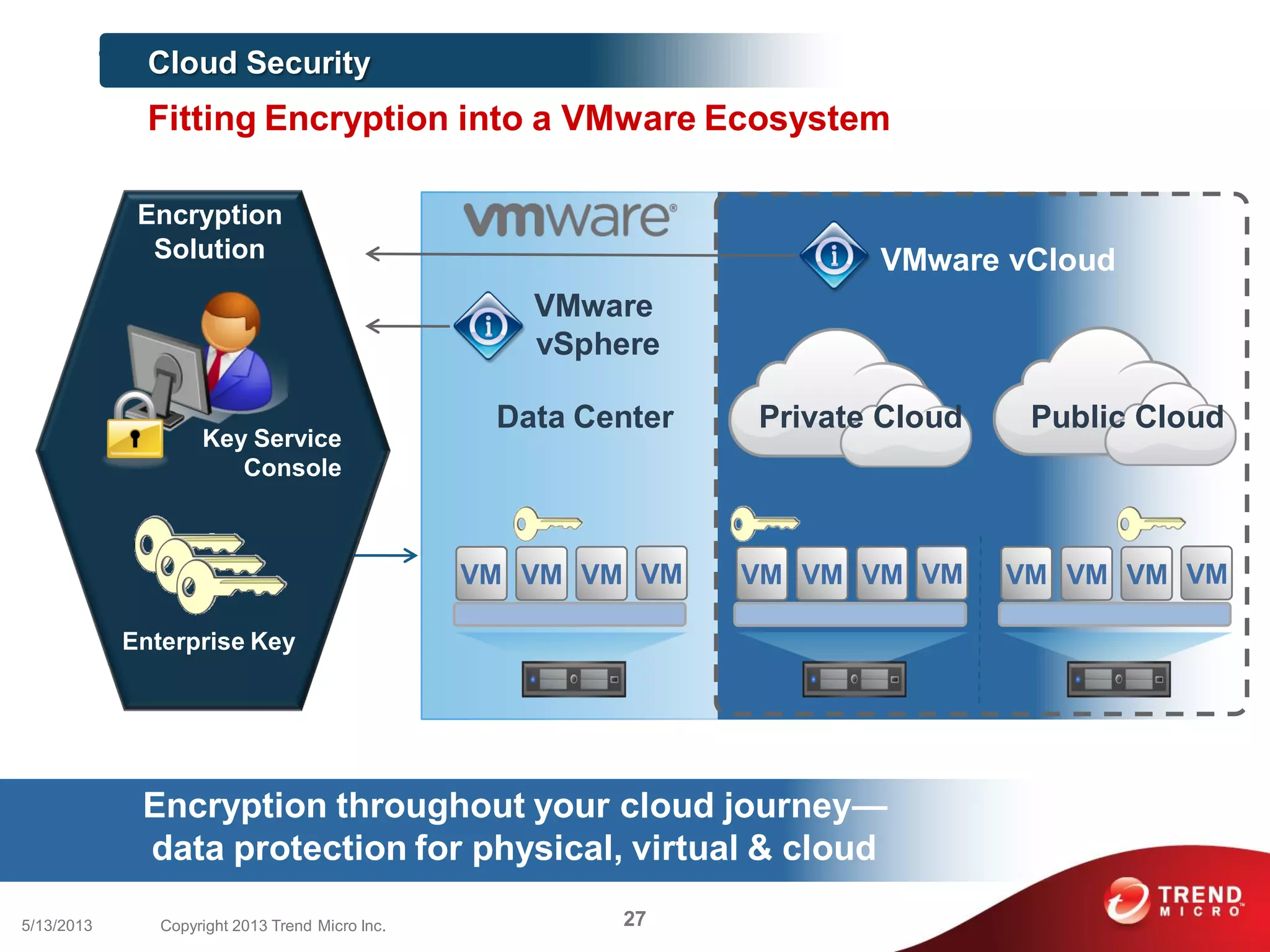
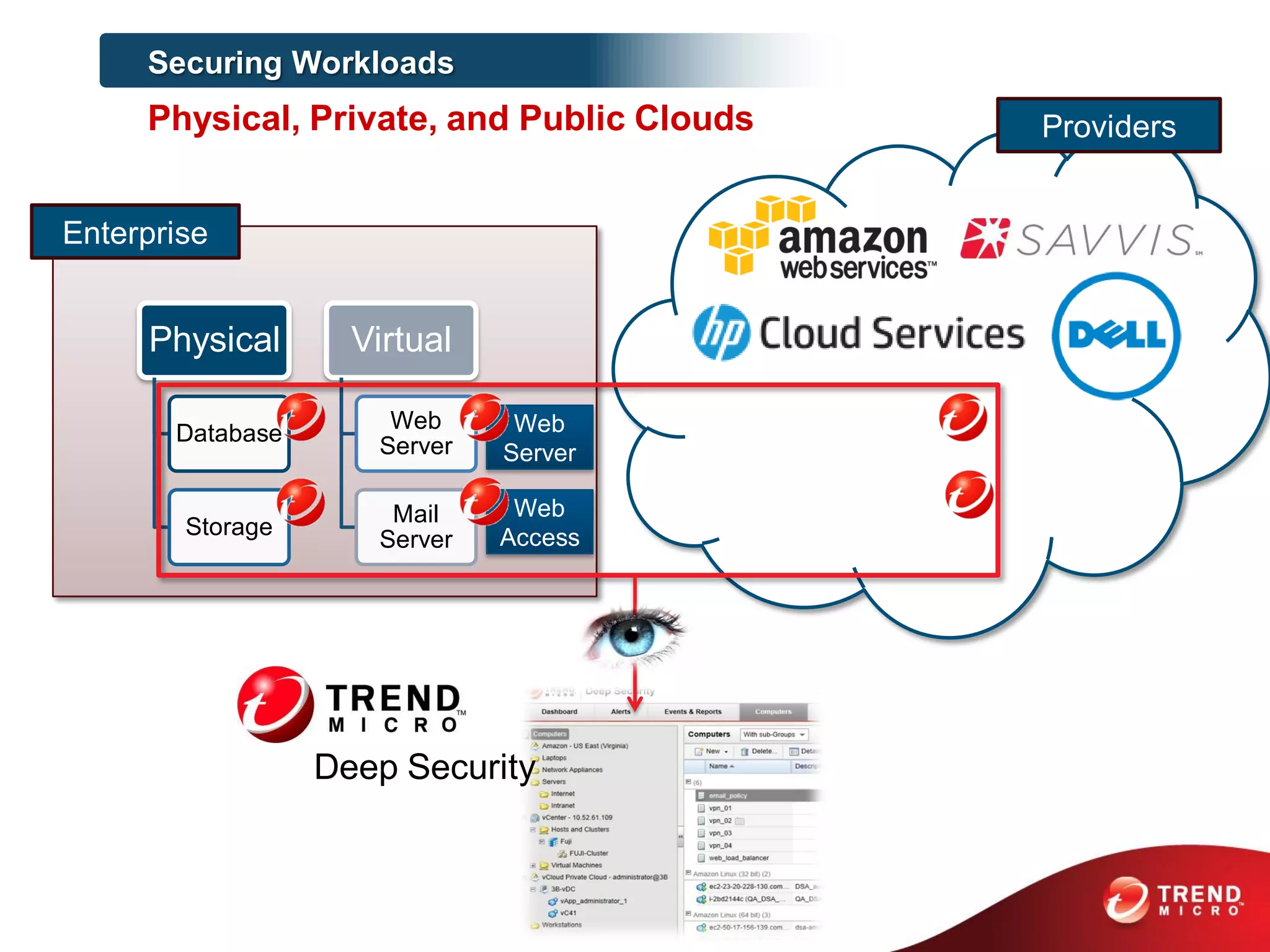
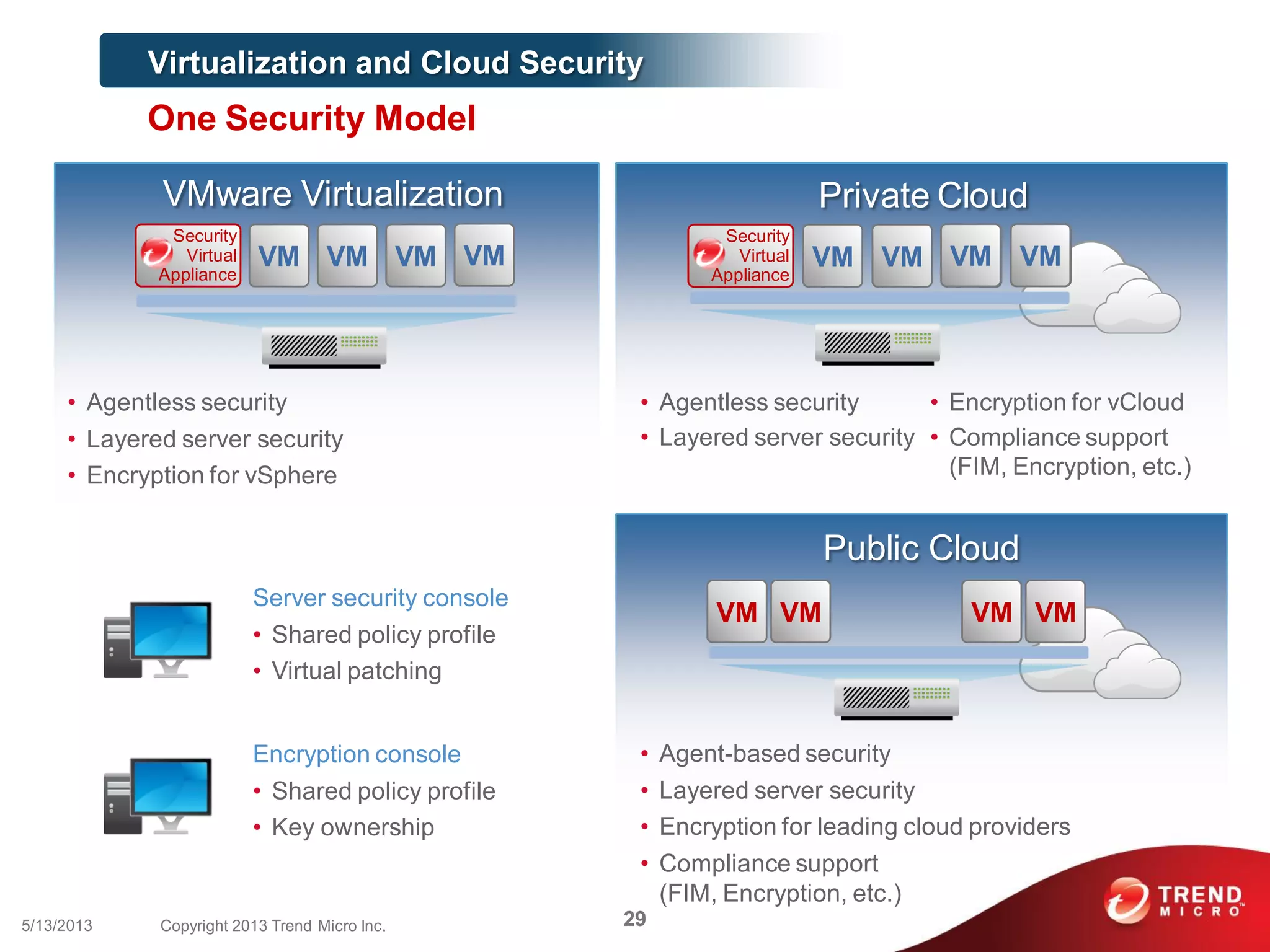
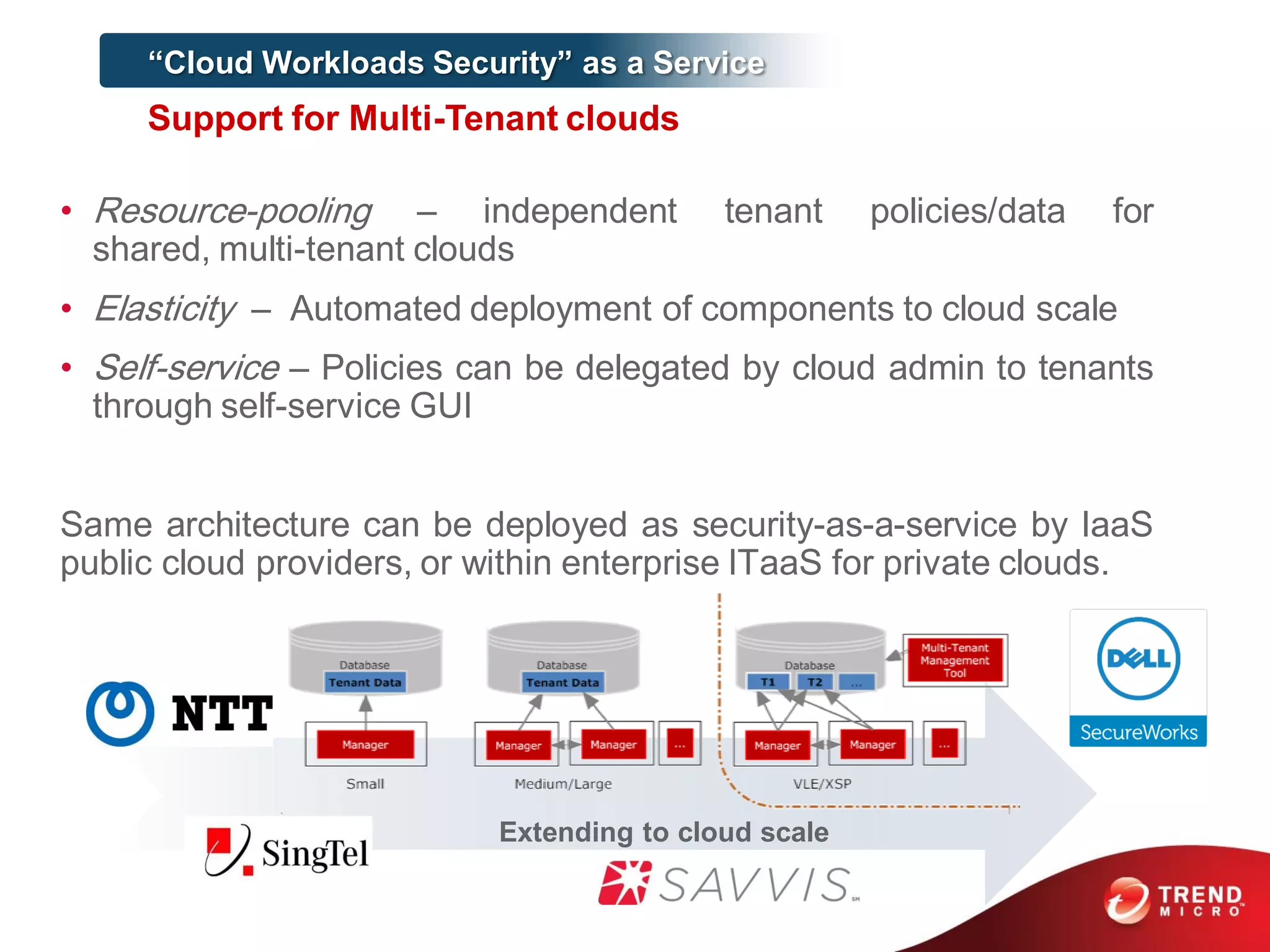
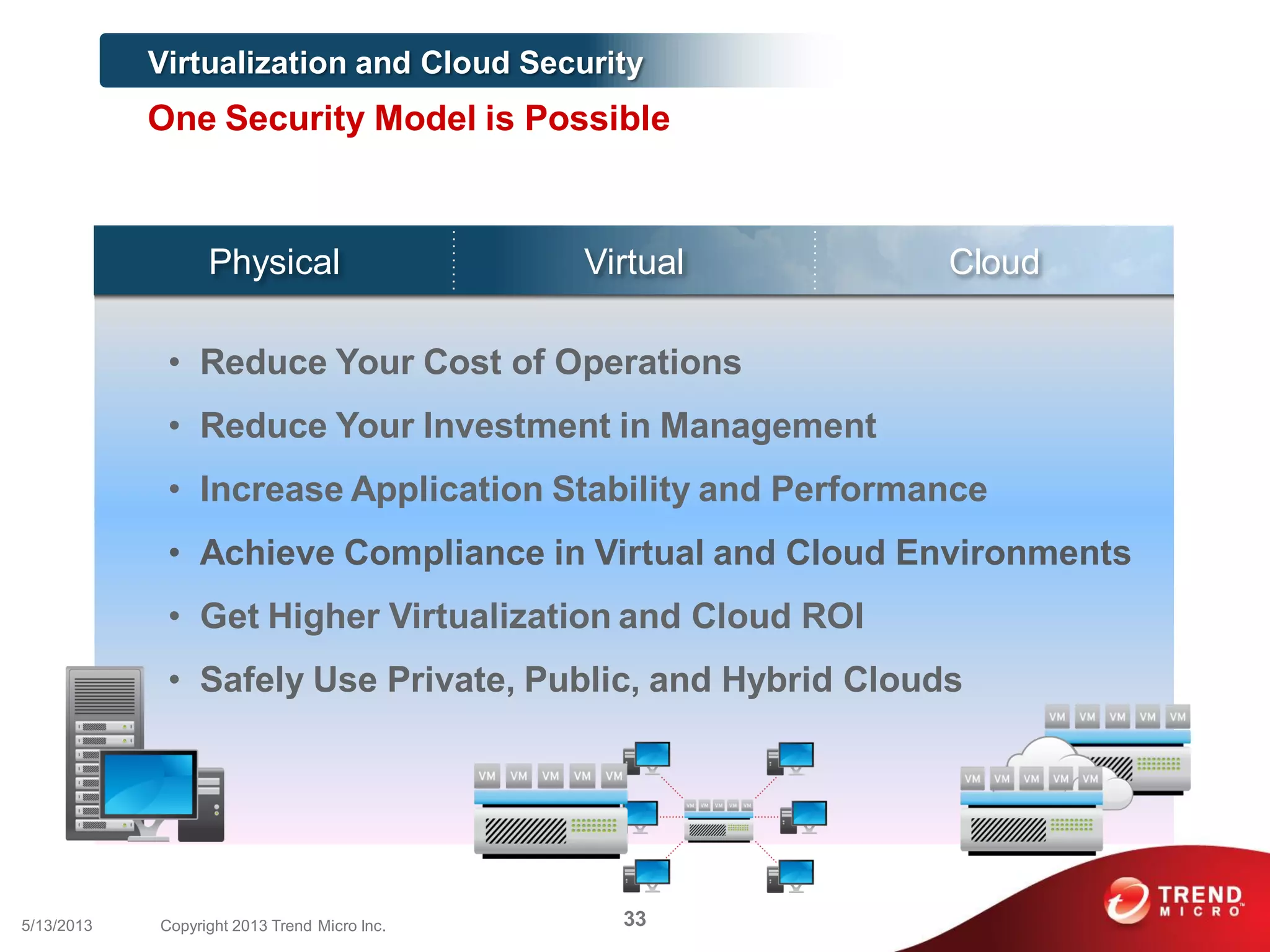
This document discusses securing workloads across physical, virtual, and cloud environments using Trend Micro's security solutions. It outlines the challenges of securing virtual and cloud environments, including less visibility, new threats, performance impacts, and complex management. The document proposes using Trend Micro's integrated security platform to provide a single security model across physical, virtual and cloud with benefits like reduced complexity, increased efficiency, and delivered agility. It provides examples of Trend Micro's virtualization and cloud security capabilities and success in the market.