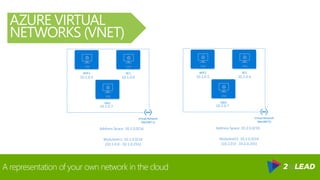
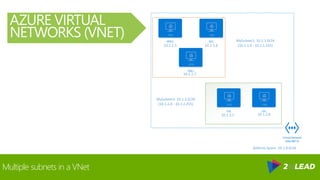
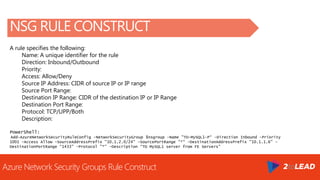
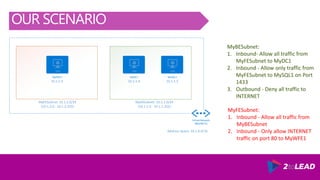
The document covers an overview of Azure security, specifically focusing on Azure Network Security Groups (NSGs) and their configuration for managing inbound and outbound traffic in virtual networks. It details the importance of cloud security, customer expectations from cloud providers, and provides examples and PowerShell commands to create and manage NSGs effectively. Key points include the construction of NSGs, default rules, and best practices for applying NSGs to subnets, virtual machines, and network interfaces.













![ARCHITECT | CONSULTANT | GENEROUS
Appendix B
Run to listen to a port on a server A:
$Listener = [System.Net.Sockets.TcpListener]1433
$Listener.Start()
$Listener.AcceptTcpClient()
Run on Server B to connect client to server A:
(new-object Net.Sockets.TcpClient).Connect(“SERVERBIP", 1433)](https://image.slidesharecdn.com/azure-nsg-151008162809-lva1-app6892/85/Azure-Network-Security-Groups-NSG-22-320.jpg)