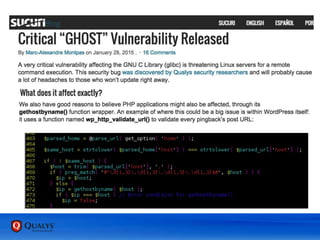
The February 2015 patch overview highlights a significant increase in updates for Adobe Flash due to multiple critical vulnerabilities, including 0-day exploits detected in January and February. Microsoft also released nine bulletins addressing vulnerabilities in Internet Explorer, Windows, and Office, prioritizing critical patches for remote code execution risks. The document discusses a critical vulnerability known as 'Ghost' in glibc, with potential exploits affecting various Linux distributions and other systems.