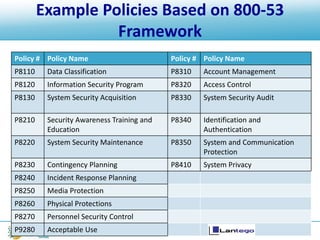
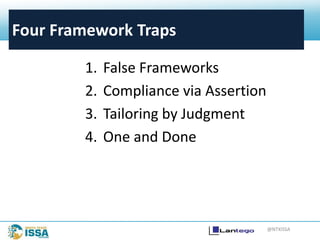
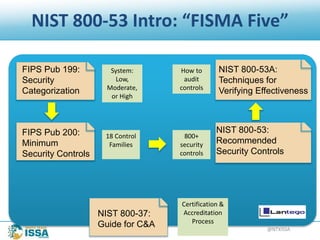
The document discusses information security frameworks, specifically focusing on the NIST 800-53 framework, outlining its structure, control families, and management of security controls. It identifies four common pitfalls when using frameworks: false frameworks, compliance via assertion, tailoring by judgment, and treating it as a one-time effort. The conclusion emphasizes the need for ongoing maintenance and adaptation of frameworks to ensure effective information security management.







![@NTXISSA
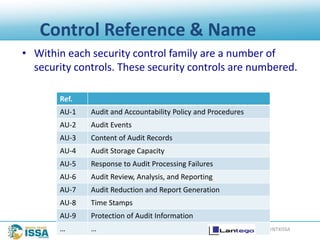
Control Enhancements
• Control enhancements provide statements of security capability to:
• Add function/specificity to the control, or
• Increase the strength of the control.
Control Enhancements:
(1) CONTENT OF AUDIT RECORDS | ADDITIONAL AUDIT INFORMATION
The information system generates audit records containing the following additional
information: [Assignment: organization-defined additional, more detailed information].
(2) CONTENT OF AUDIT RECORDS | CENTRALIZED MANAGEMENT OF PLANNED AUDIT
RECORD CONTENT
The information system provides centralized management and configuration of the
content to be captured in audit records generated by [Assignment: organization-defined
information system components].](https://image.slidesharecdn.com/landolldoug-frameworktraps-150502080952-conversion-gate01/85/NTXISSACSC2-Four-Deadly-Traps-in-Using-Information-Security-Frameworks-by-Doug-Landoll-11-320.jpg)


![@NTXISSA
Control Assignment
• Controls may be augmented through assignment and
selection options within control statements.
• Assignment: Organizationally defined
AU-2 AUDIT EVENTS
The organization:
…
(3) AUDIT EVENT | REVIEWS AND UPDATES
The organization reviews and updates the audited events
[Assignment: organization-defined frequency].
800-53
Example](https://image.slidesharecdn.com/landolldoug-frameworktraps-150502080952-conversion-gate01/85/NTXISSACSC2-Four-Deadly-Traps-in-Using-Information-Security-Frameworks-by-Doug-Landoll-14-320.jpg)
![@NTXISSA
Control Selection
• Controls may be augmented through assignment and
selection options within control statements.
• Selection: Organizationally defined
IA-3 DEVICE IDENTIFICATION AND AUTHENTICATION
Control: The information system uniquely identifies and authenticates [Assignment:
organizational defined specific and/or types of devices] before establishing a
[Selection (one or more): local, remote, network] connection.
800-53
Example](https://image.slidesharecdn.com/landolldoug-frameworktraps-150502080952-conversion-gate01/85/NTXISSACSC2-Four-Deadly-Traps-in-Using-Information-Security-Frameworks-by-Doug-Landoll-15-320.jpg)