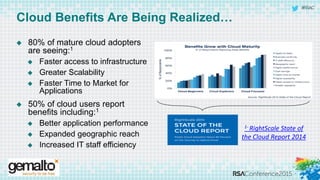
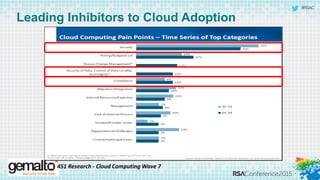
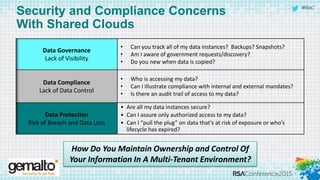
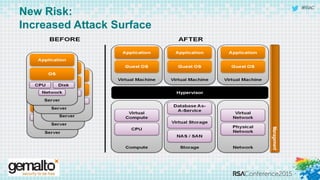
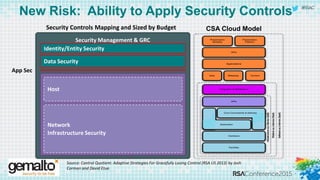
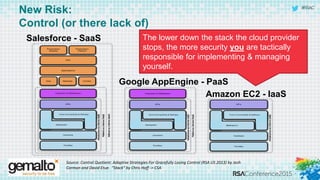
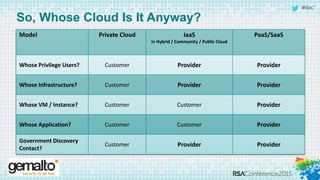
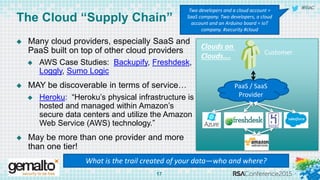
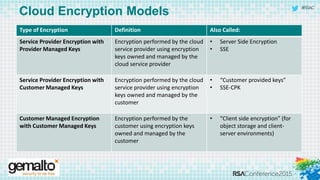
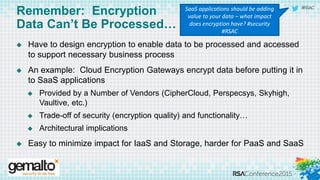
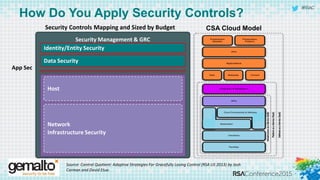
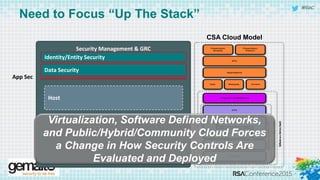
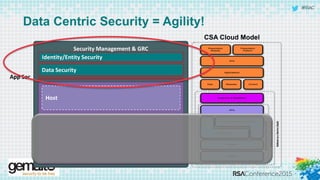
The document discusses the evolving landscape of cloud computing, highlighting its benefits such as faster access, scalability, and improved application performance while also addressing significant concerns around data security, ownership, and compliance in multi-tenant environments. It emphasizes the challenges organizations face in maintaining control over their data, including the increased attack surface and the complexities of managing security within shared cloud services. The presentation suggests that adopting data-centric security measures and encryption strategies is crucial for safely navigating these challenges in cloud environments.