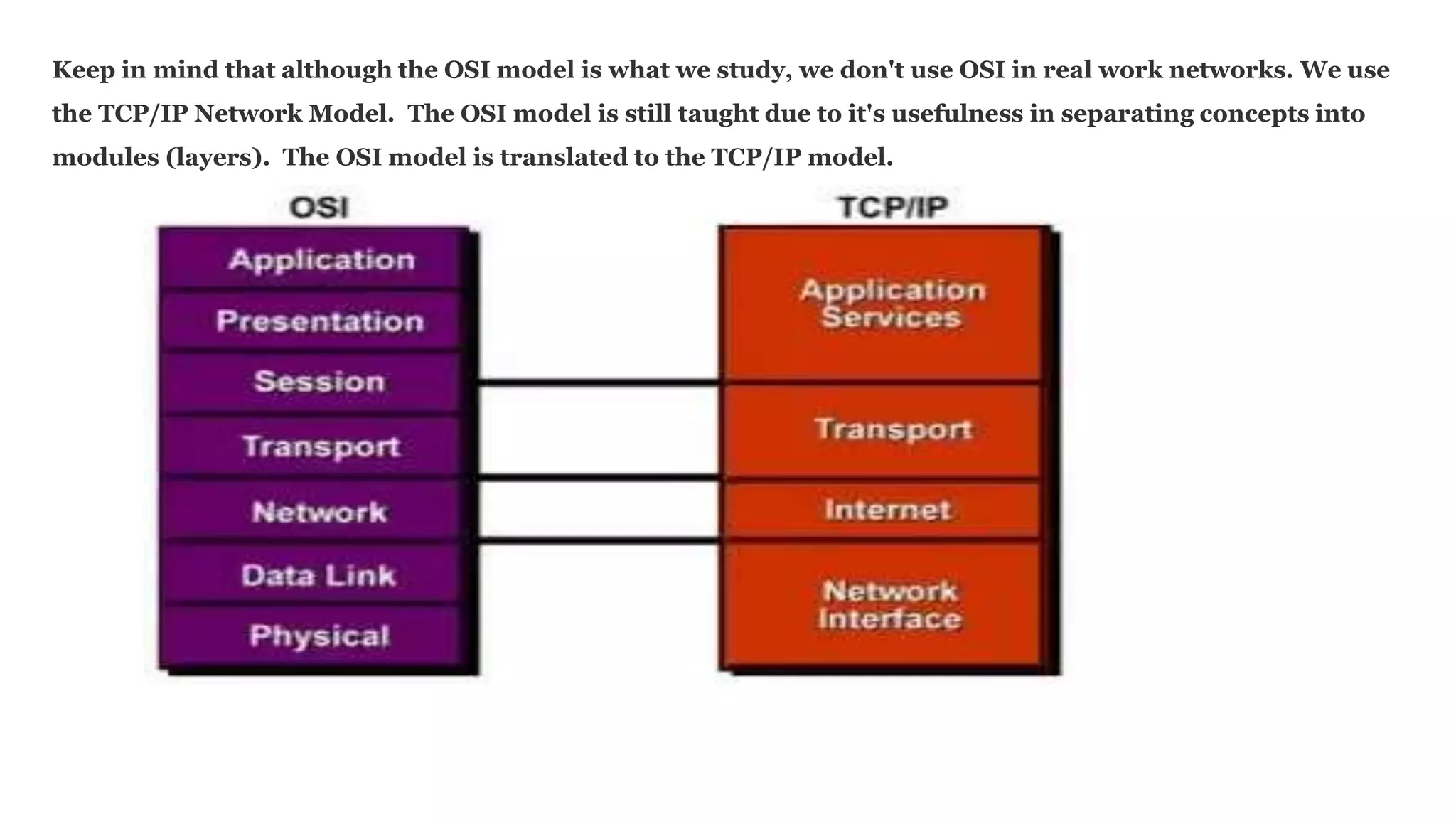
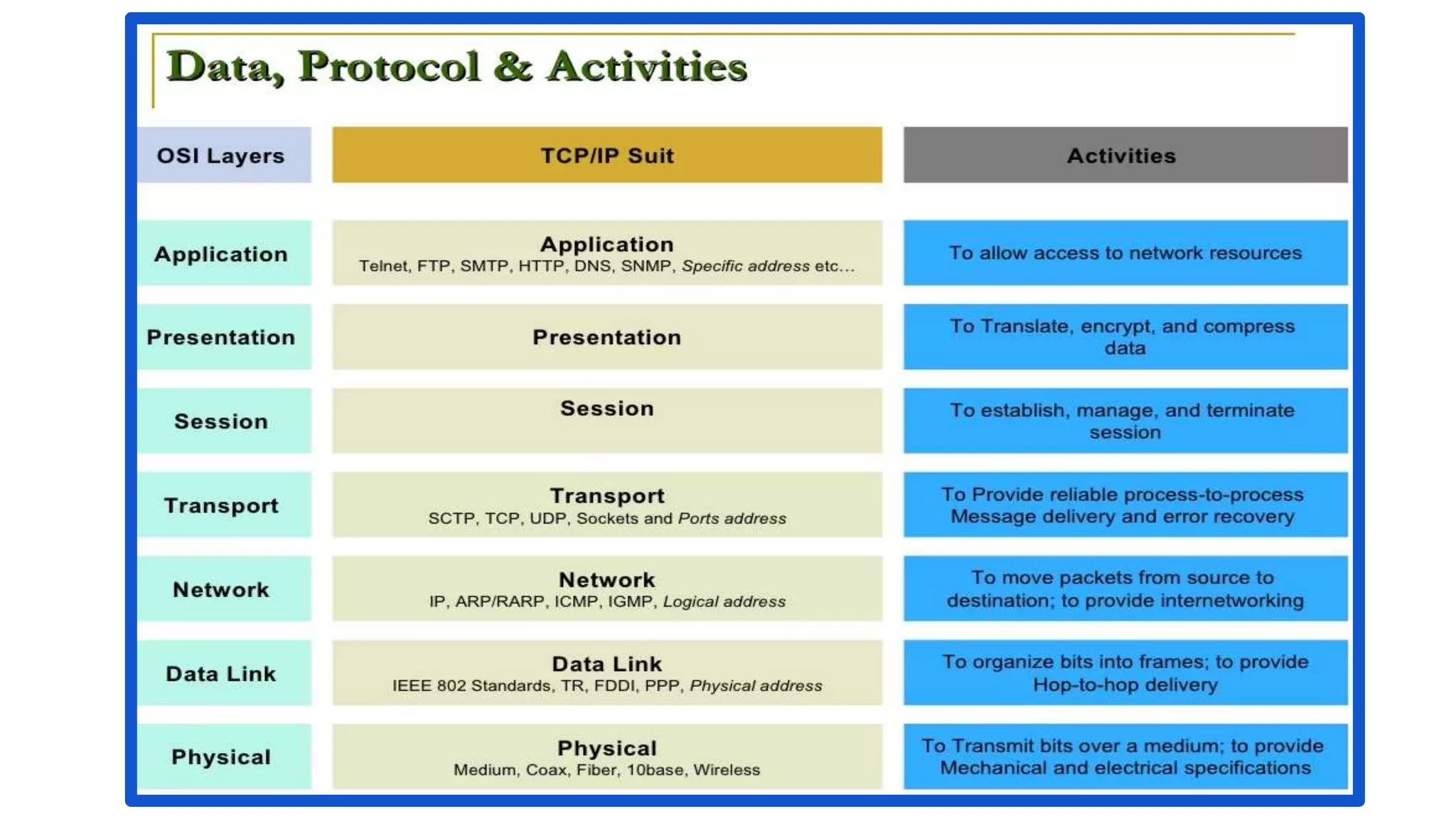
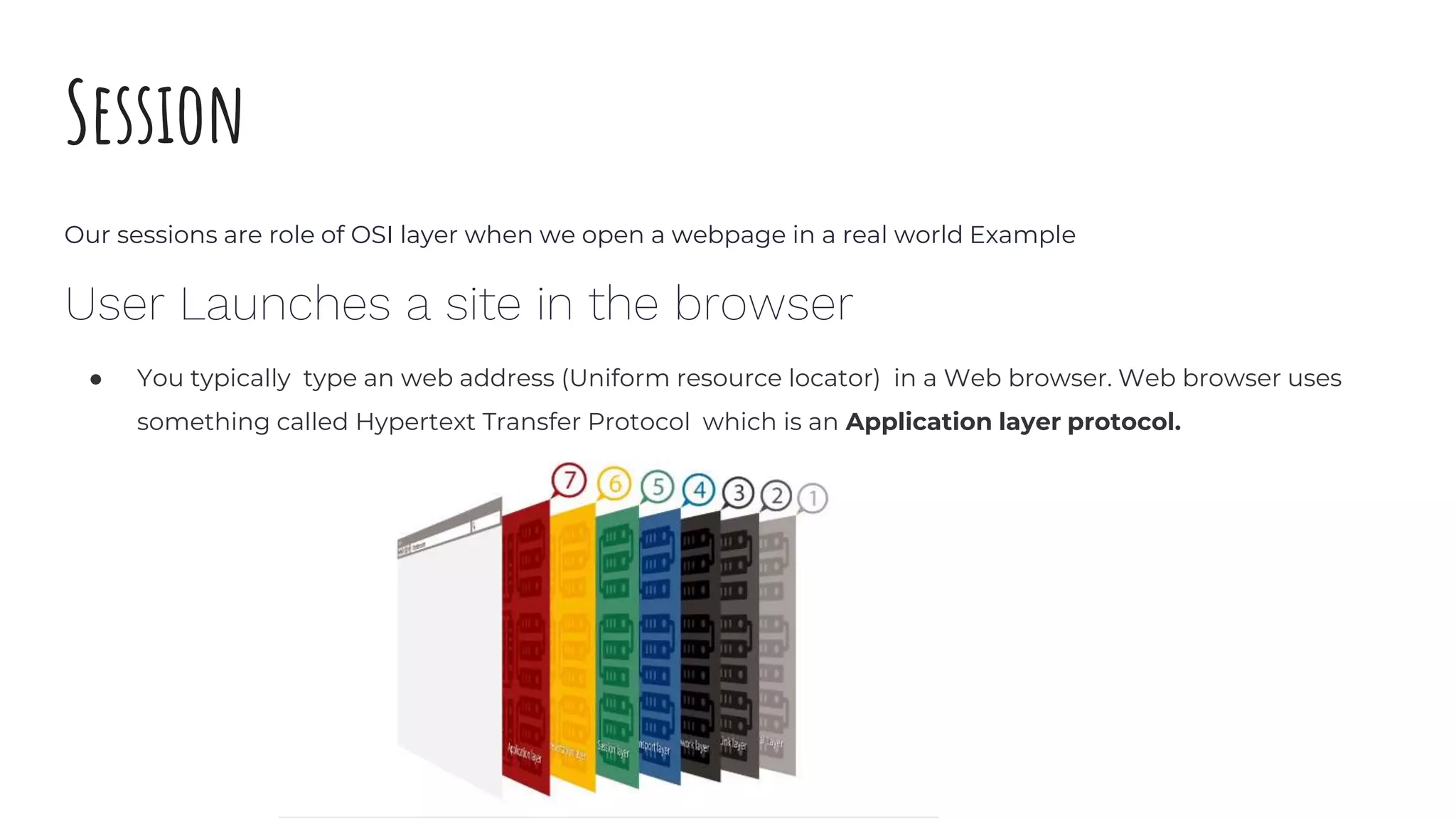
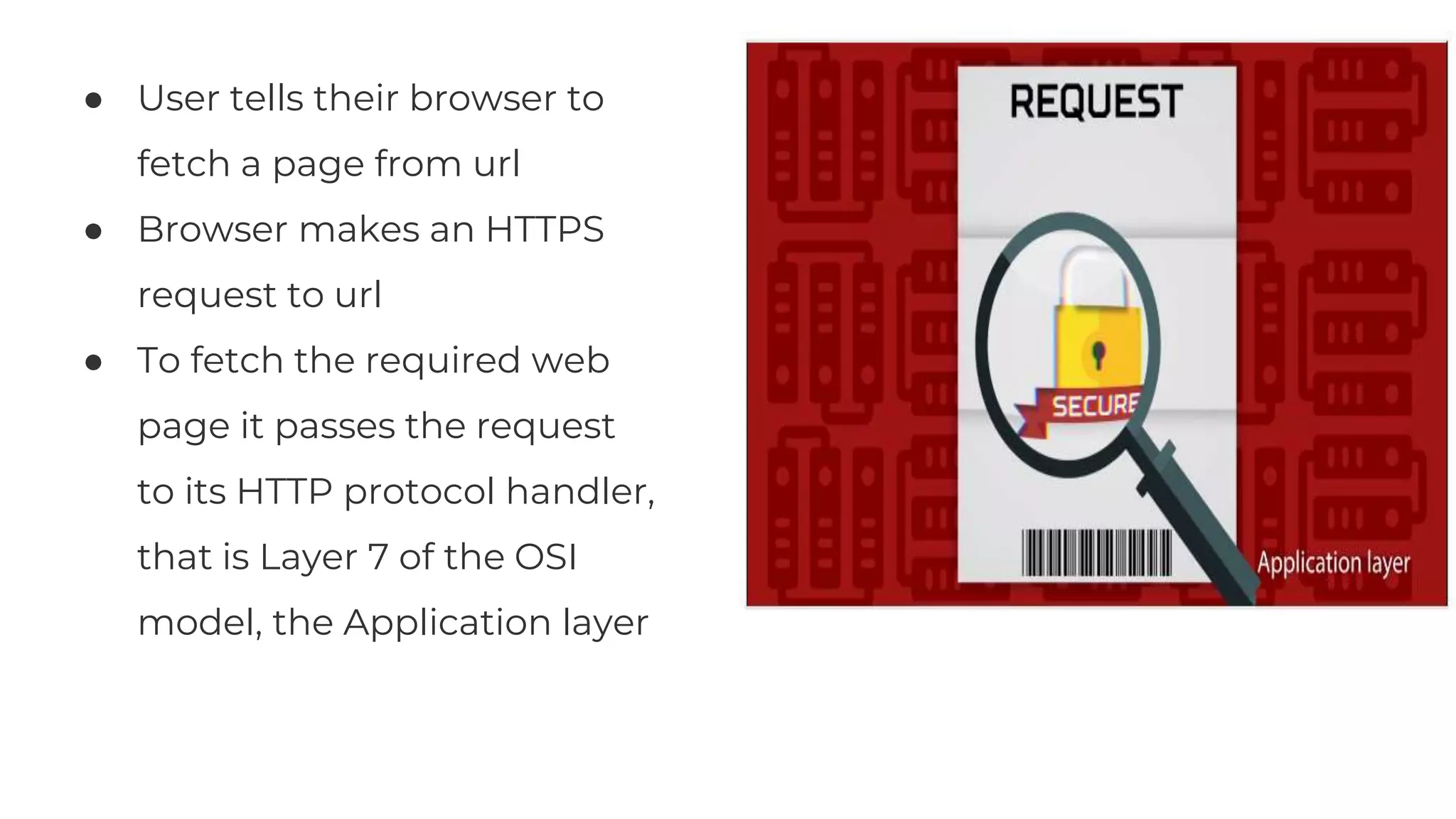
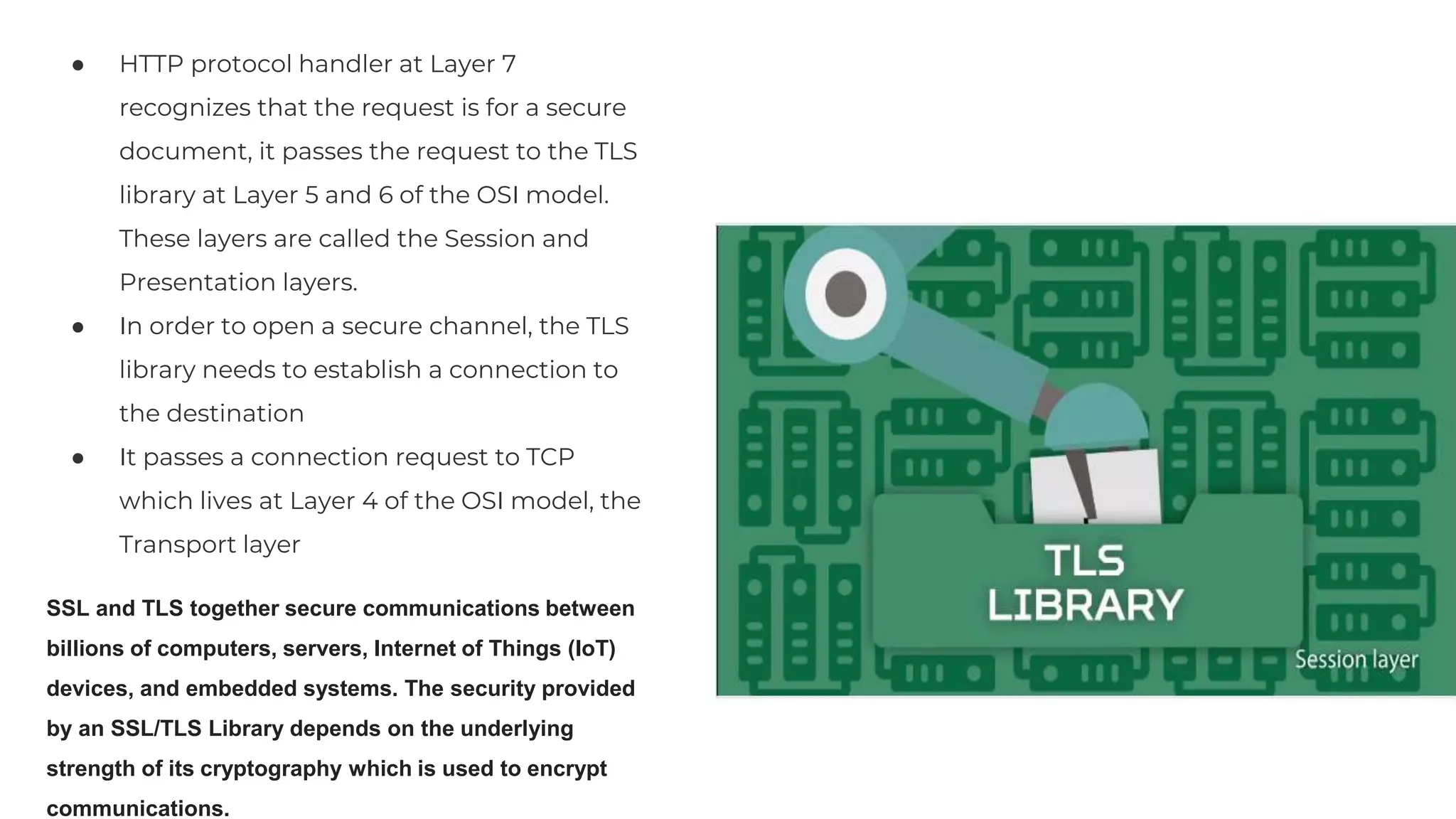
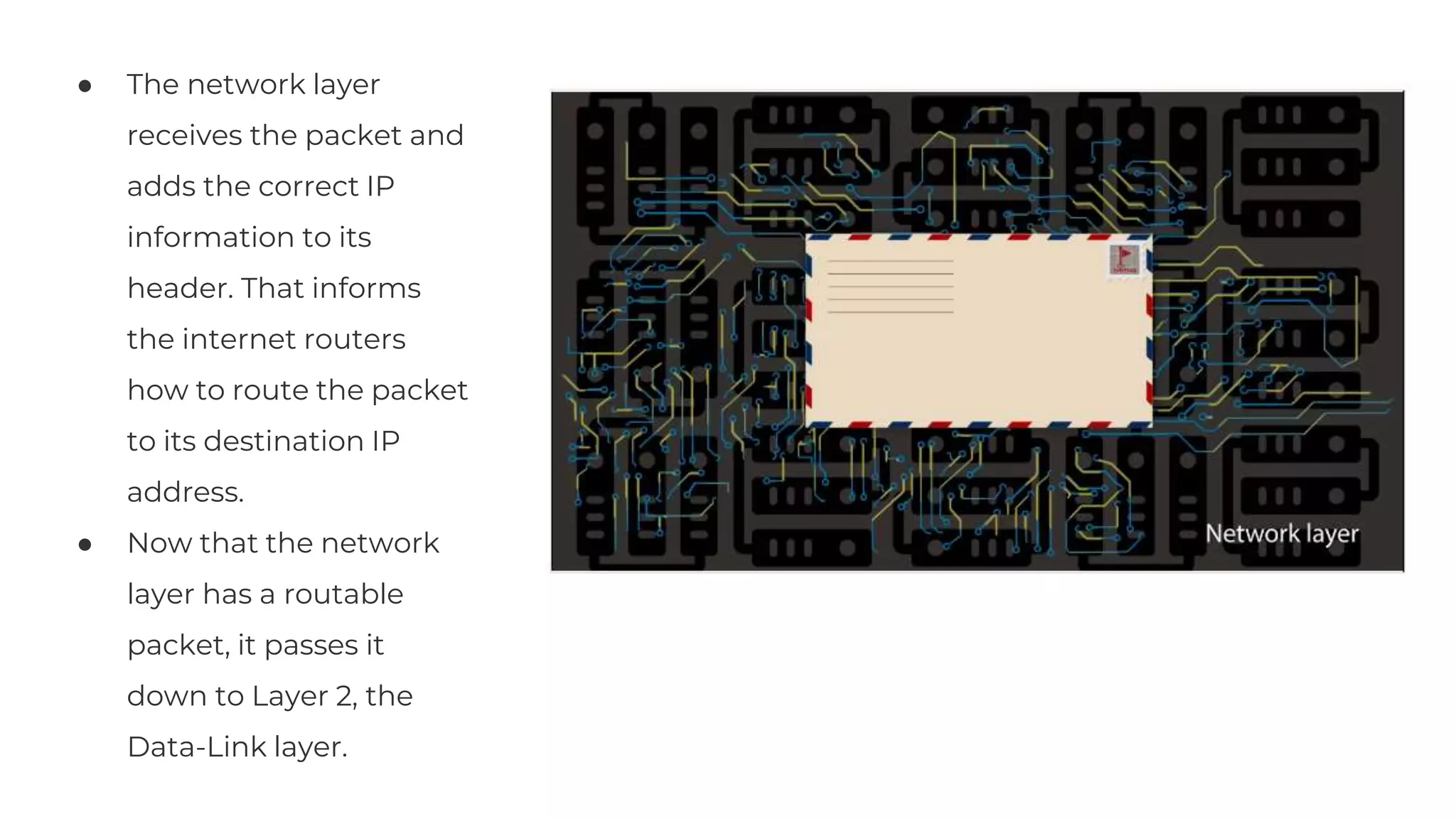
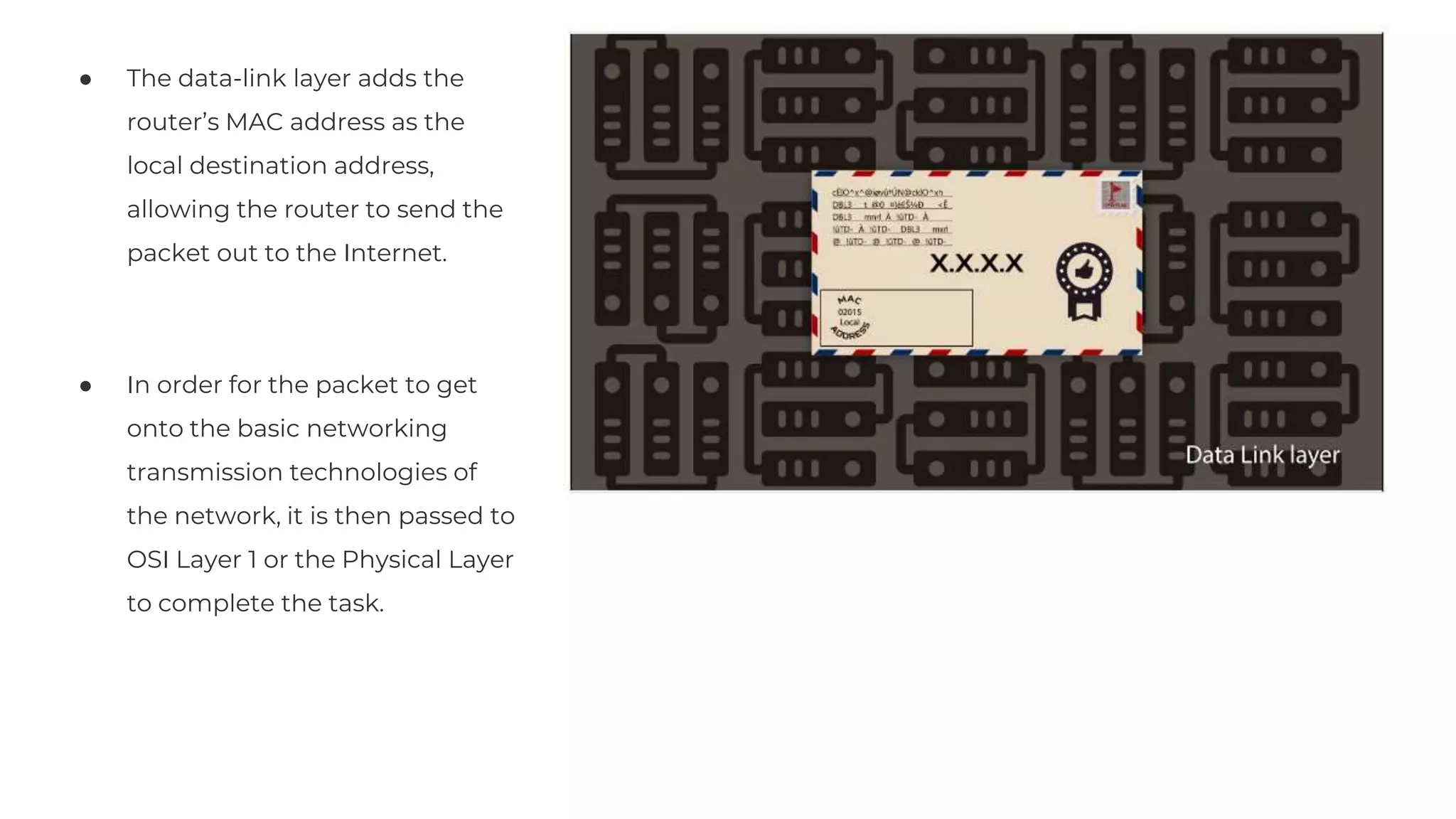
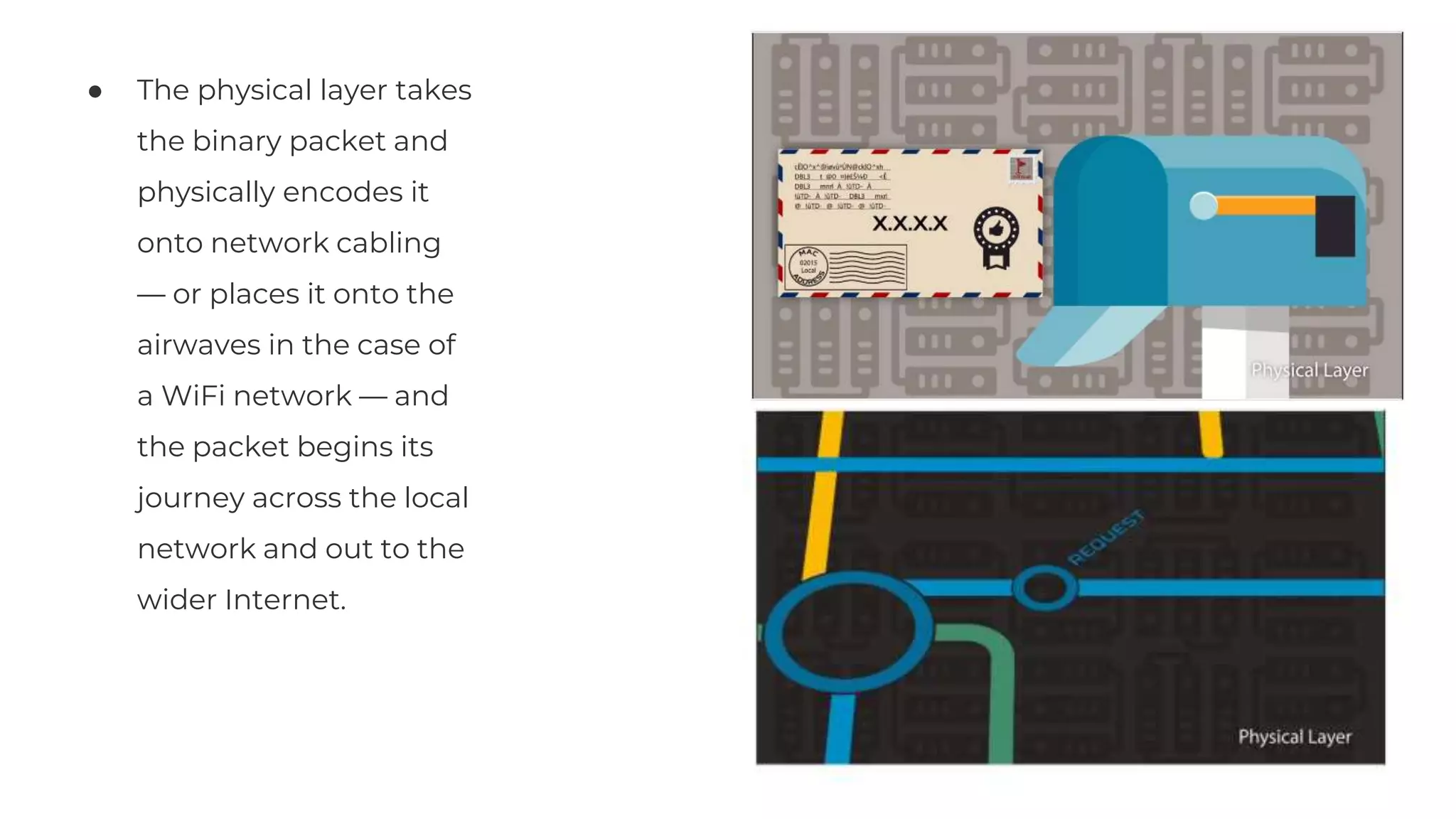
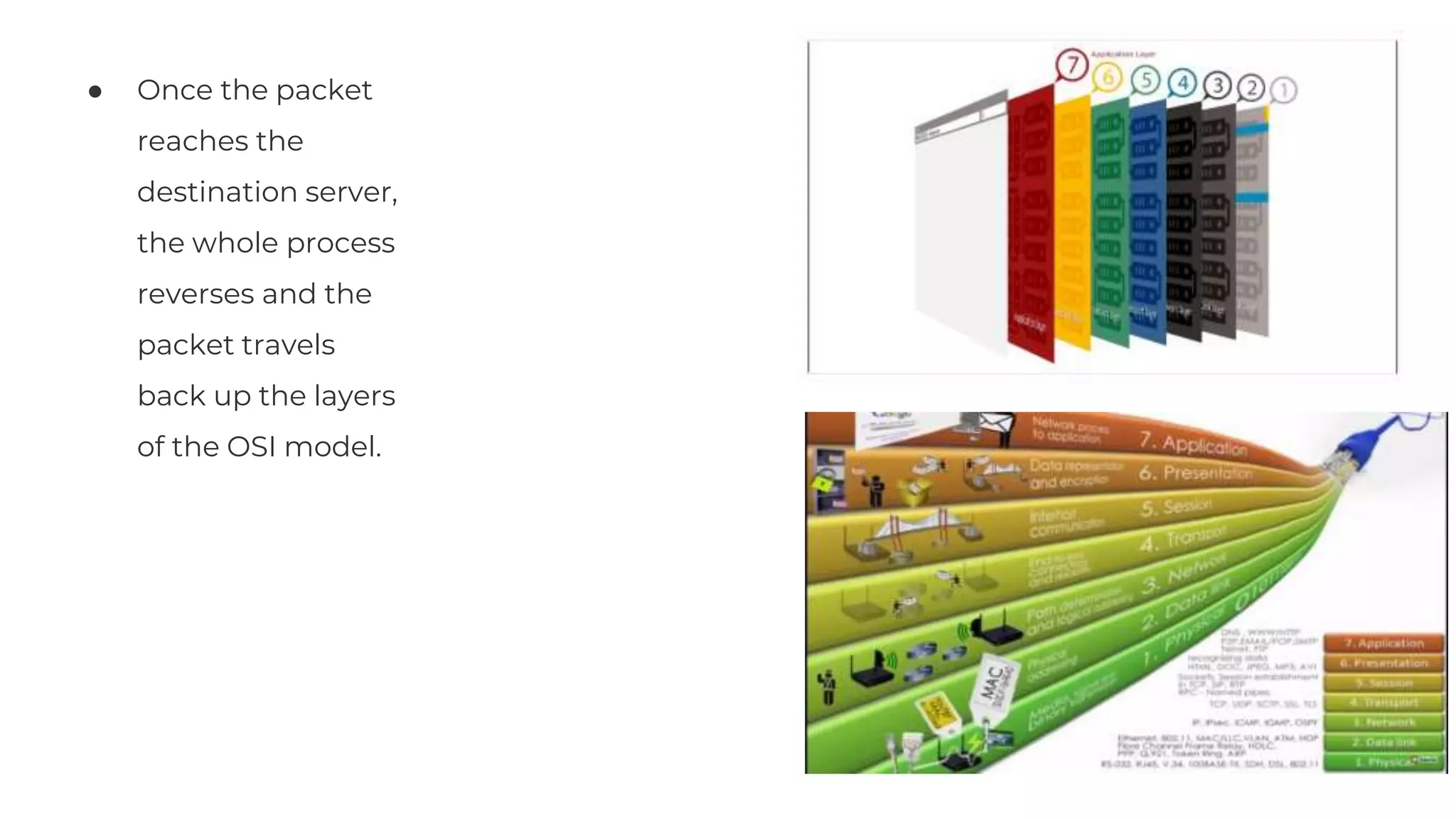
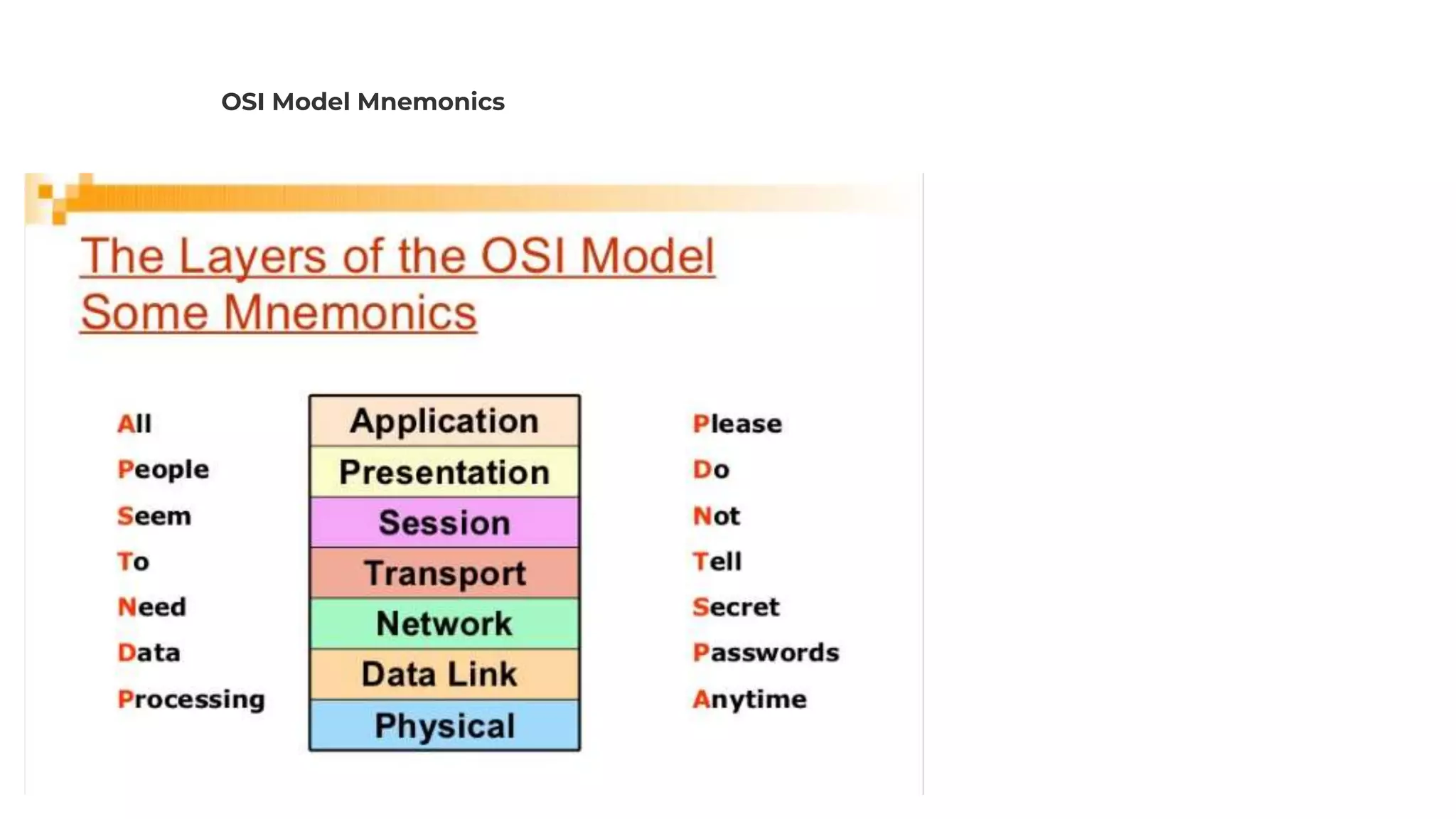
The document discusses the OSI model's relevance to web application functioning, highlighting its role in the browsing process despite the prevalence of the TCP/IP model in real-world networks. It outlines how a web request is processed through various OSI layers, starting from the application layer to establish secure communication via SSL/TLS and culminating in the physical transmission of data. The document also notes the reverse process when packets reach their destination, emphasizing the modular approach of the OSI model in understanding network interactions.