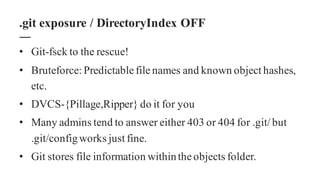
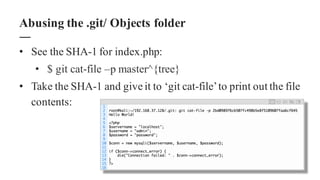
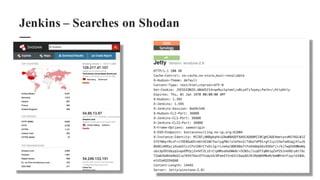
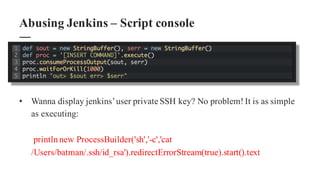
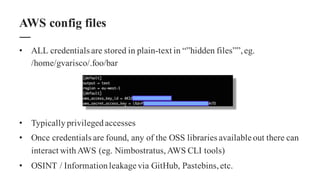
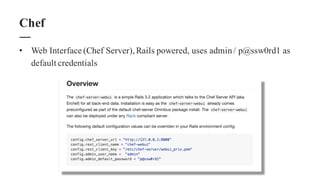
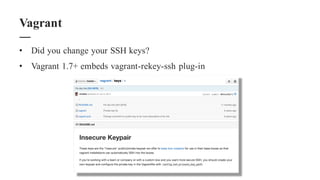
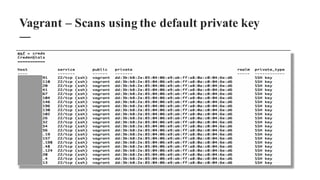
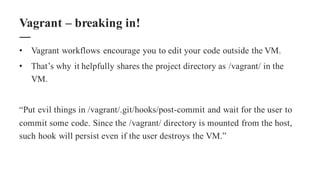
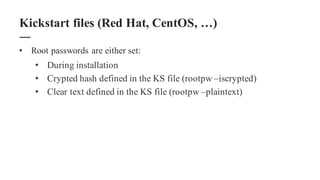
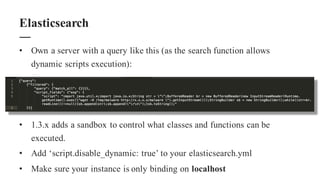
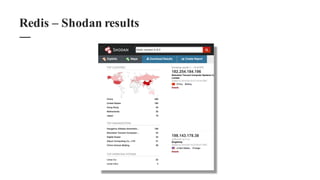
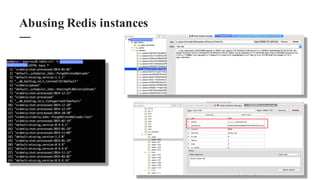
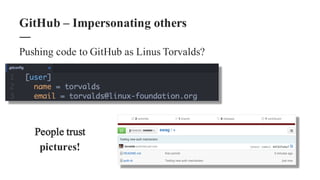
The document discusses the importance of integrating security within DevOps practices, highlighting various vulnerabilities that can arise from configuration errors, coding mistakes, and human errors. It outlines specific tools and techniques, such as GitHub, Jenkins, and AWS, that can be exploited if security measures are not properly implemented, and emphasizes the need for constant vigilance and best practices in security. Recommendations include encrypting sensitive data, implementing access controls, and regularly auditing systems to mitigate risks associated with DevOps environments.











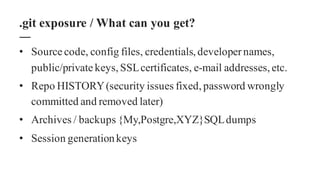
![• $ mkdir website-source-code
• $ cd website-source-code
• $ wget –mirror –include-directories=/.git
http://www.example.com/.git
• $ cd www.example.com
• $ git reset –hard
HEAD is now at […]
.git exposure / DirectoryIndex ON](https://image.slidesharecdn.com/opscon-devooops-151015101501-lva1-app6892/85/Road-to-Opscon-Pisa-15-DevOoops-17-320.jpg)