The document discusses techniques for bypassing binary shell uploads during penetration tests, primarily focusing on the use of the psexec Metasploit module and its capabilities for executing Windows commands, dumping password hashes, and extracting Active Directory information without the need for traditional shells. It emphasizes the vulnerabilities associated with binary shells and presents methods for achieving remote command execution while minimizing detection by antivirus systems. The document also introduces tools like smbexec and psexec_ntdsgrab for efficient pentesting operations, including offline password hash dumping and database extraction from domain controllers.

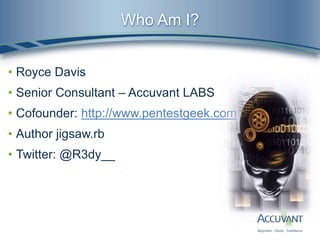







![lpBinaryPathName MSDN Definition
• lpBinaryPathName [in, optional]
• The fully qualified path to the service binary file. If the path contains a space, it must be quoted
so that it is correctly interpreted. For example, "d:my sharemyservice.exe" should be
specified as ""d:my sharemyservice.exe"".
• The path can also include arguments for an auto-start service. For
example, "d:mysharemyservice.exe arg1 arg2". These arguments are passed to the service
entry point (typically the main function).
• If you specify a path on another computer, the share must be accessible by the computer
account of the local computer because this is the security context used in the remote call.
However, this requirement allows any potential vulnerabilities in the remote computer to affect
the local computer. Therefore, it is best to use a local file.
• psexec.rb looks like this:
• C:HjeKOplsYutVmBWn.exe Probably a Meterpreter payload
• What if we tried this instead:
• C:windowssystem32cmd.exe /C echo dir C: ^> outputfile.txt > launchfile.bat &
C:windowssystem32cmd.exe /C launchfile.bat”](https://image.slidesharecdn.com/owningcomputerswithoutshellaccess-2-130423130048-phpapp02/85/Owning-computers-without-shell-access-2-11-320.jpg)
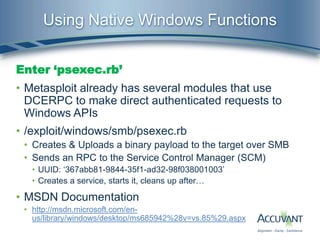
![The Psexec Mixin
In order to provide accessibility to this functionality for other modules we
created a mixin which has been graciously accepted into the MSF.
lib/msf/core/exploit/smb/psexec.rb
• Slightly modified version of the original psexec.rb code wrapped in a
function which excepts a Windows command in the following format:
• [PATH TO cmd.exe] [/C] [INSERT WINDOWS COMMAND]
• The method is called like so ‘return psexec(command)’
• Returns ‘true’ if execution was successful
• Major difference is it does not try to delete cmd.exe after execution
• Also contains a ‘smb_read_file(smbshare, host, file)’ method for
convenient retrieval of command output](https://image.slidesharecdn.com/owningcomputerswithoutshellaccess-2-130423130048-phpapp02/85/Owning-computers-without-shell-access-2-12-320.jpg)