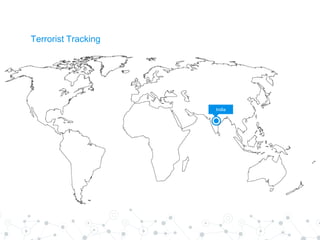
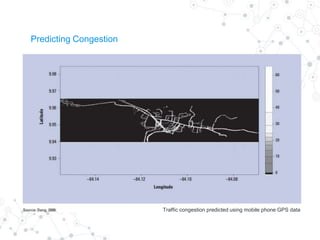
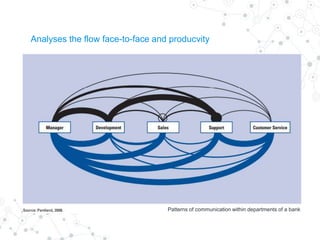
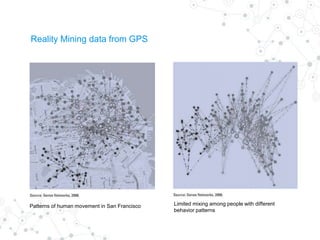
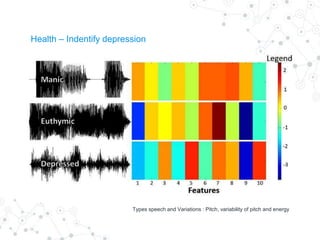
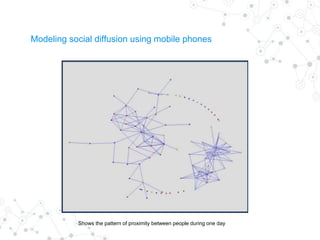
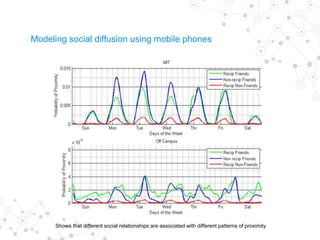
Reality mining is defined as the quantification and modeling of long-term human behavior and social interactions through mobile and wearable technology. The document explores the motivation, examples, research applications, and challenges related to reality mining, emphasizing its implications for privacy and data analysis. It concludes with the need for collaboration between social and computer scientists to harness the potential of large-scale data while safeguarding individual privacy.