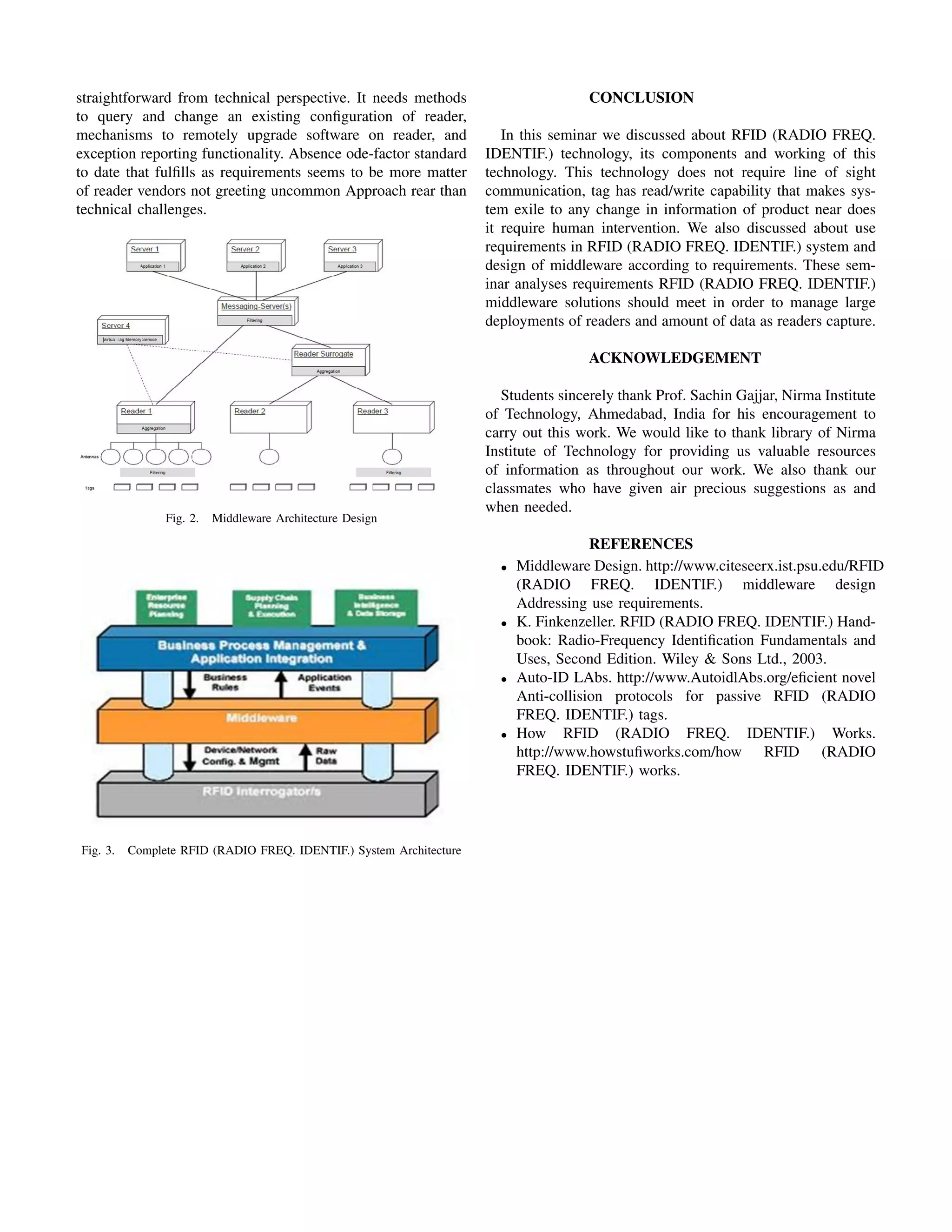
This document discusses Radio Frequency Identification (RFID) technology. It describes the key components of an RFID system, including RFID tags, RFID readers, and middleware. It explains the different types of RFID tags such as passive tags, active tags, and semi-passive tags. The document also provides a brief history of RFID technology and discusses some of its common uses in areas like retail and transportation.