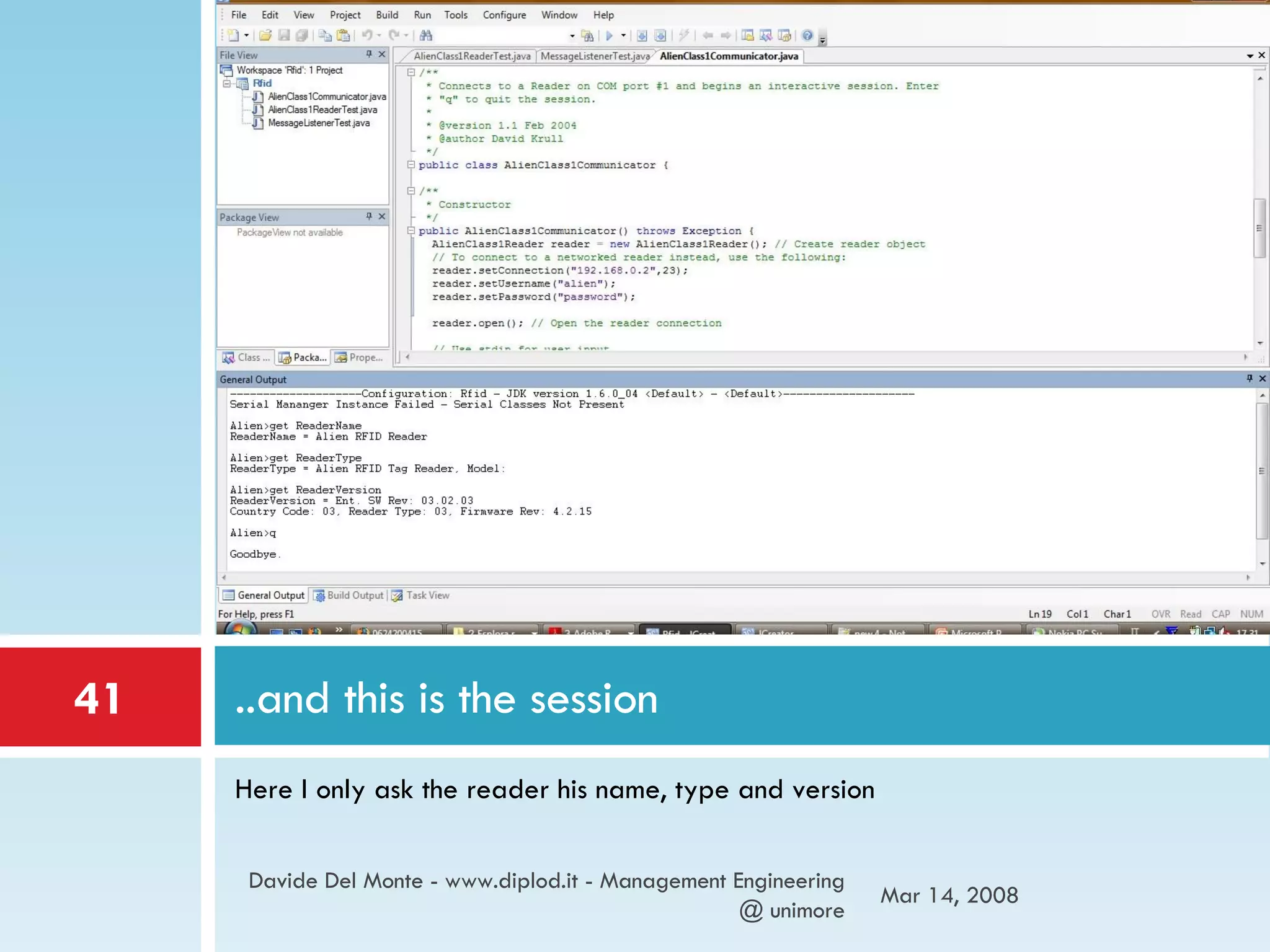
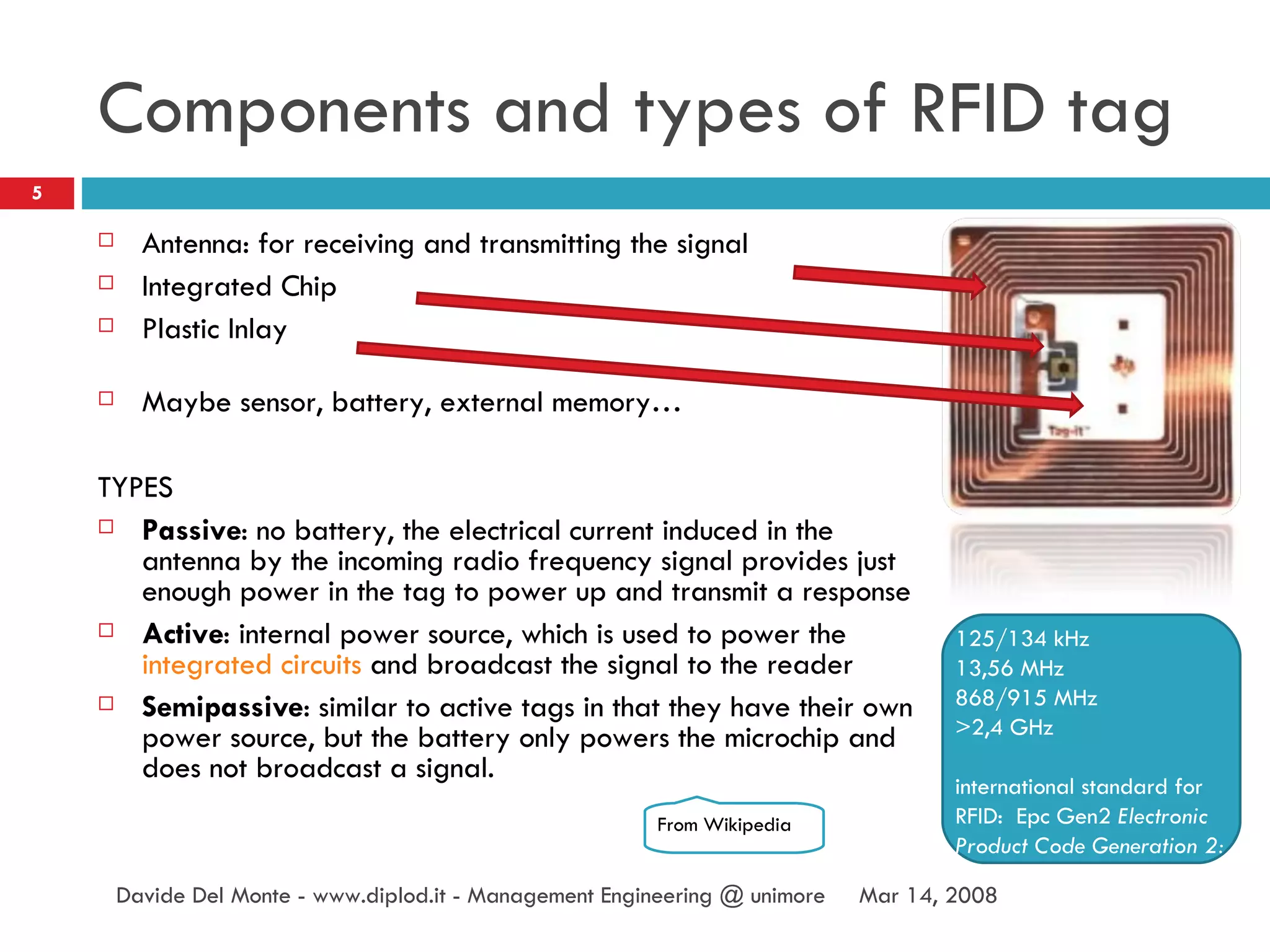
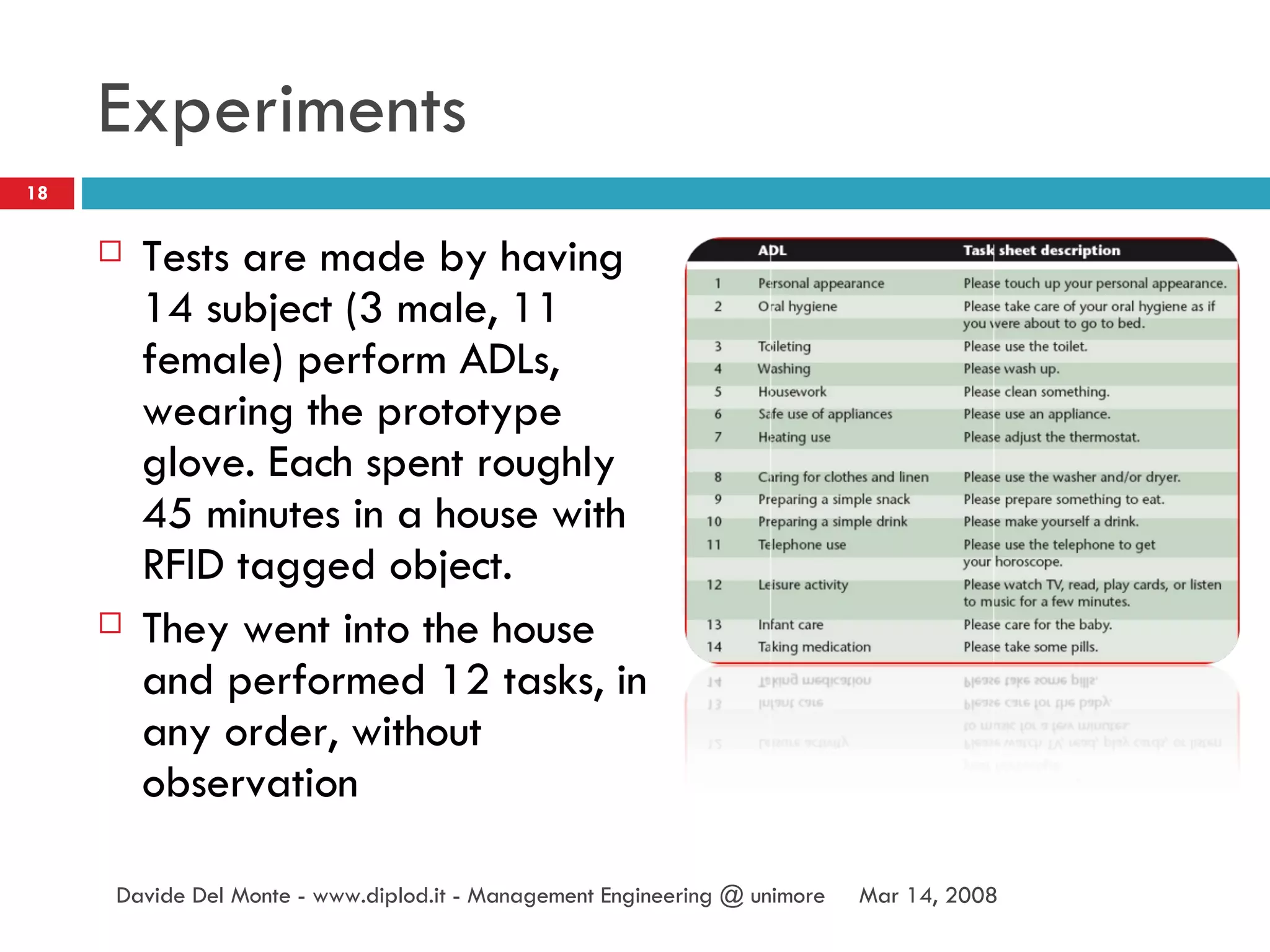
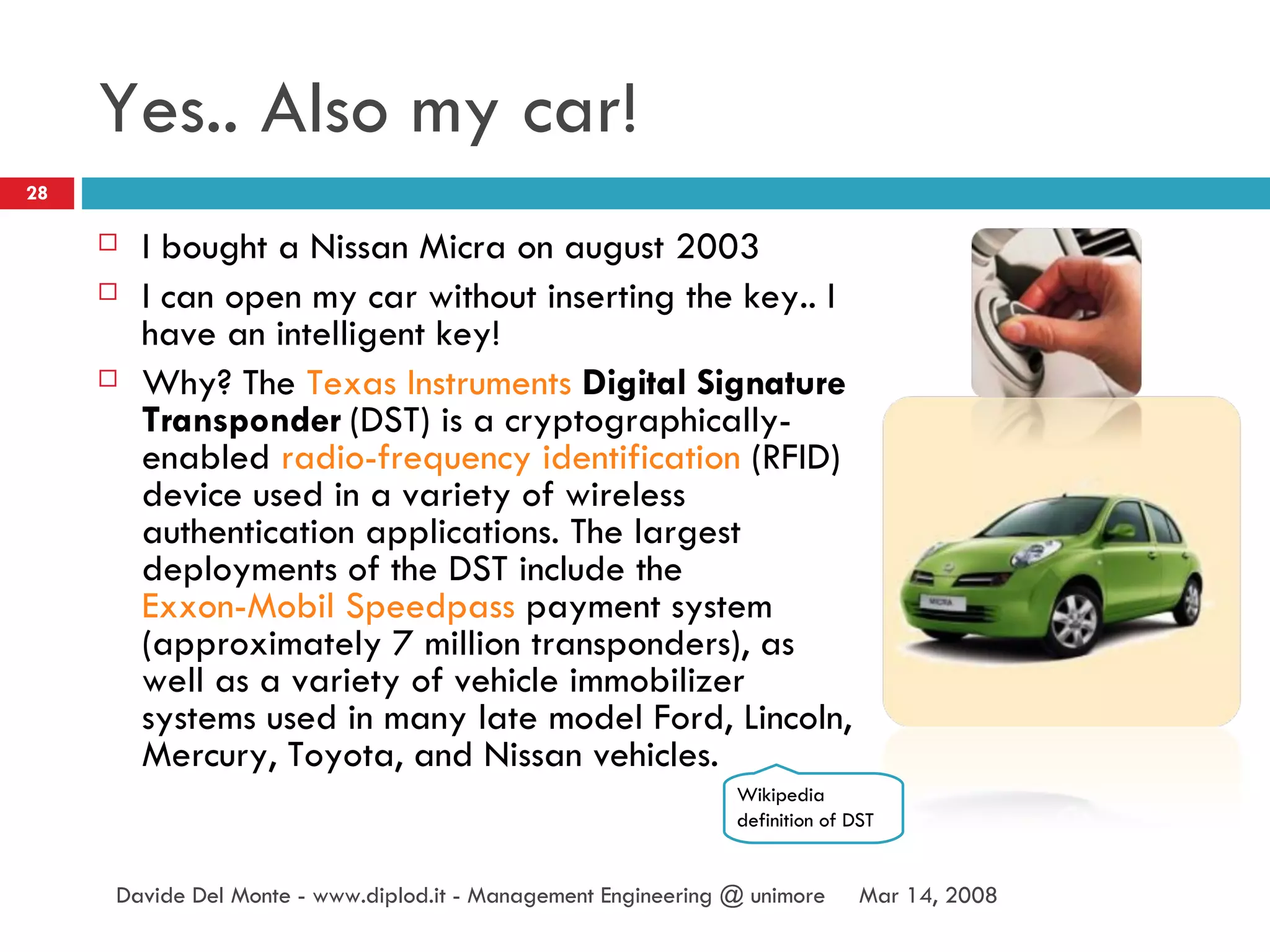
The document discusses RFID (radio-frequency identification) technology and its applications. It describes what RFID is, how RFID tags work, and examples of RFID being used for identification of objects, tracking objects in supply chains, access control, contactless payment, and inferring human activities through interactions with tagged objects. The document also provides an example of using an RFID reader and tags in a Java program to detect tagged objects.







![Tagged objects and movements Existing readers support a “poll” command, wherein the reader transmits N poll commands per second to tags and reports the number of received responses for each tag. We therefore define a response rate α as the ratio of responses to polls. α C [0..1] When 0, the tag cannot be seen at all. When 1, the tag is always seen. The response rate can be used to approximate the RF signal strength The algorithm detect interaction reliably, and as quickly as possible after the event has occurred Jun 2, 2009 Davide Del Monte - www.diplod.it - Management Engineering @ unimore](https://image.slidesharecdn.com/rfid-tag-technology-and-scenarios-1205515112289479-5/75/RFID-tag-technology-and-scenarios-10-2048.jpg)













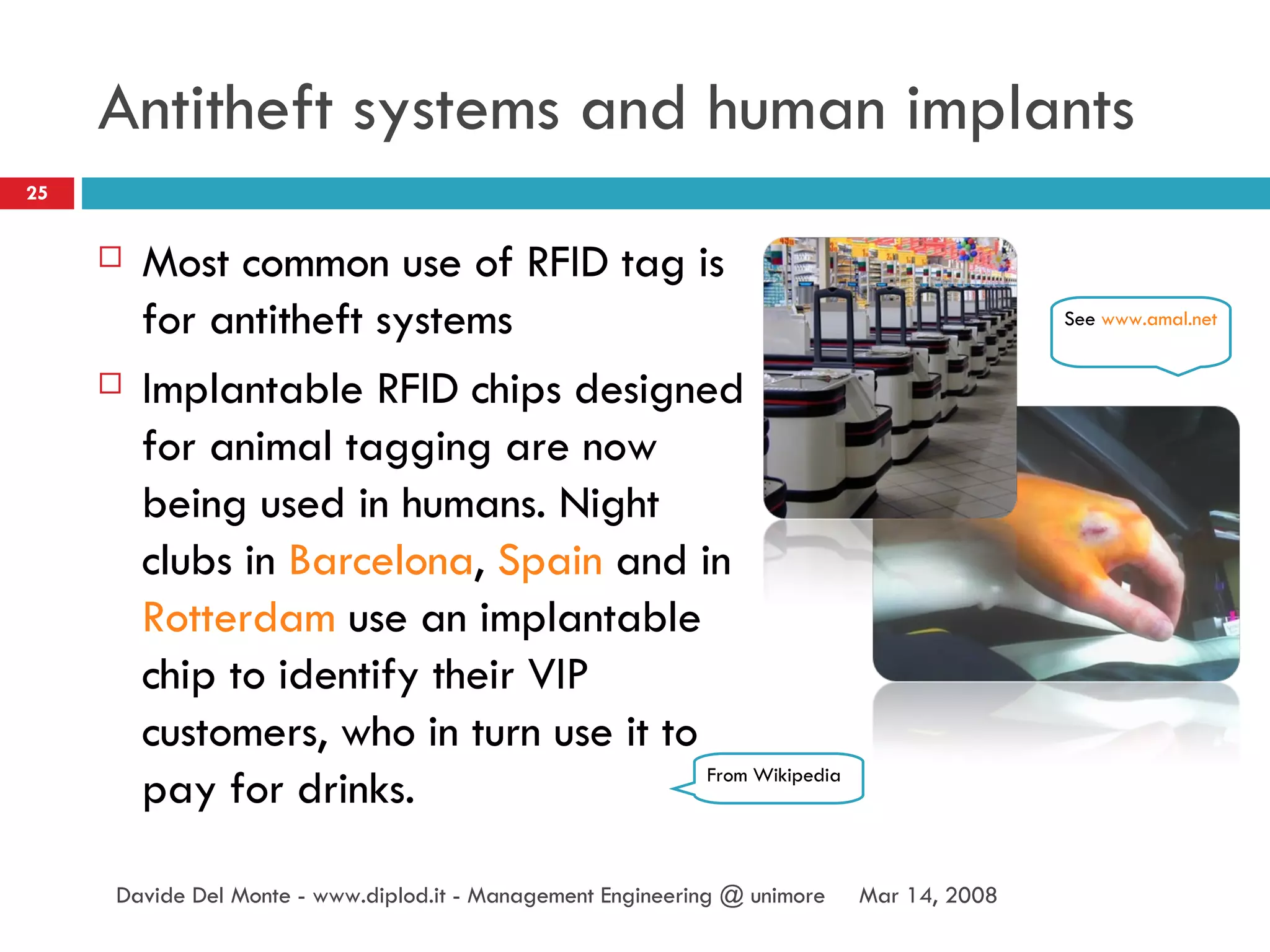
![Logistic and Domotic Inventory systems: in an academic study [19] performed at Wal-Mart, RFID reduced Out-of-Stocks by 30 percent for products selling between 0.1 and 15 units a day. Product Tracking: integrated supply chain from warehouse to consumer. See the story “ How and why you will talk to your tomatoes ” Domotic systems for findind object Tag environments, question tags for environmental conditions ( ubiquity of RFID tags) Jun 2, 2009 Davide Del Monte - www.diplod.it - Management Engineering @ unimore](https://image.slidesharecdn.com/rfid-tag-technology-and-scenarios-1205515112289479-5/75/RFID-tag-technology-and-scenarios-27-2048.jpg)




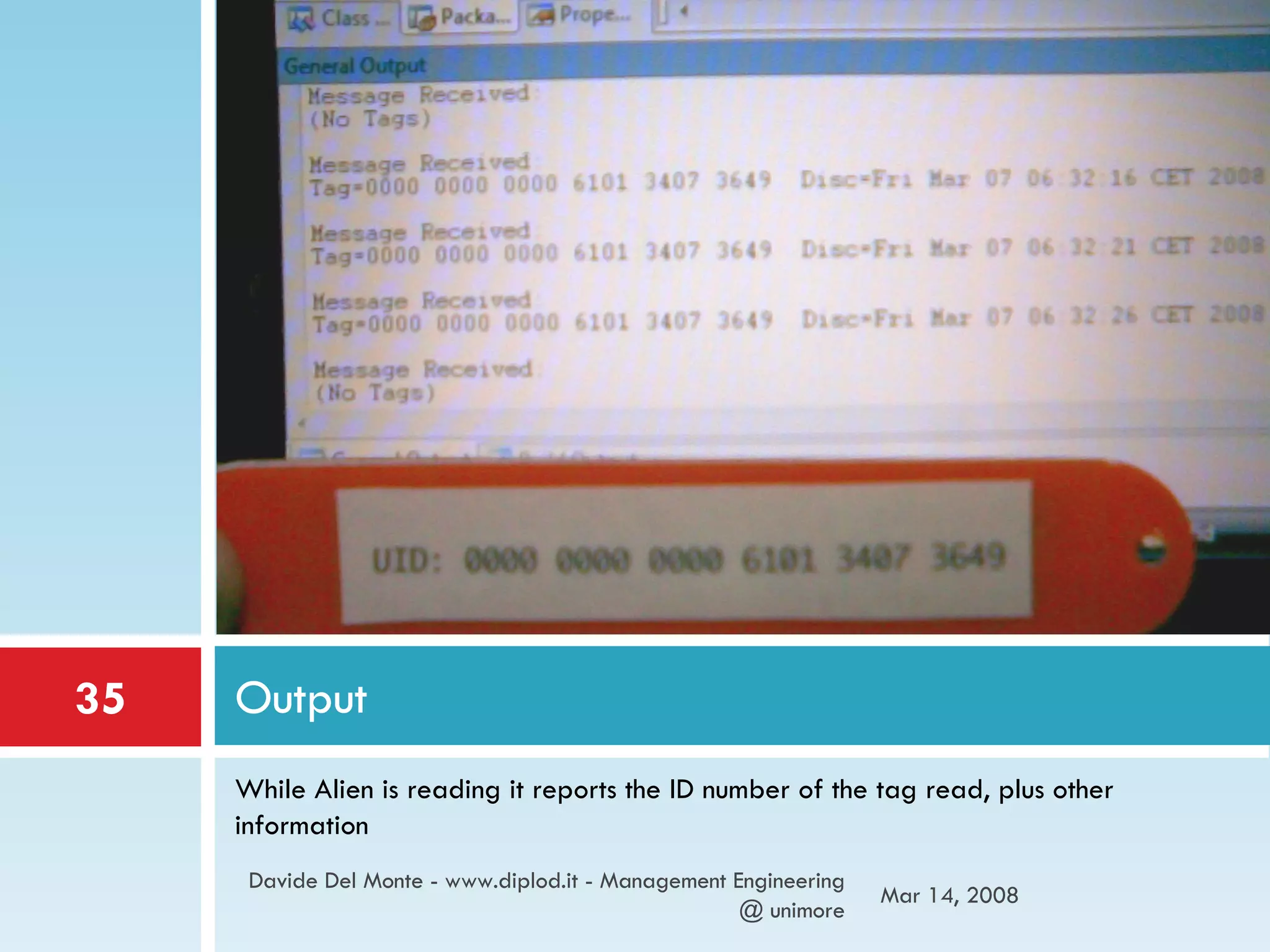
![MessageReceived If there are tags in the antenna’s area, the system reports a message with the tag’s identification number, the time when the tag was discovered, and last time the tag was seen. The main method only initializes the class MessageListenerTest public void messageReceived(Message message){ System.out.println("\nMessage Received:"); if (message.getTagCount() == 0) { System.out.println("(No Tags)"); } else { for (int i = 0; i < message.getTagCount(); i++) { Tag tag = message.getTag(i); System.out.println(tag.toLongString()); } } } //Main metod public static final void main(String args[]){ try { MessageListenerTest test = new MessageListenerTest(); } catch (Exception e) { System.out.println("Error:" + e.toString()); } } Jun 2, 2009 Davide Del Monte - www.diplod.it - Management Engineering @ unimore](https://image.slidesharecdn.com/rfid-tag-technology-and-scenarios-1205515112289479-5/75/RFID-tag-technology-and-scenarios-34-2048.jpg)