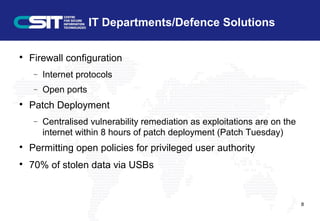
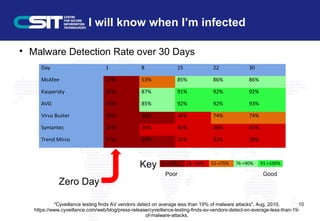
This document outlines effective habits for safe internet use. It discusses the key players in cybersecurity including attackers, IT departments, and end users. It explains common attack methods like exploiting vulnerabilities in browsers or apps. While reputable sites can still be hacked, following best practices like keeping software updated, using browsers safely, and being wary of external devices can help reduce risks. The main message is that everyone needs to be cyber aware to protect themselves and their information online.