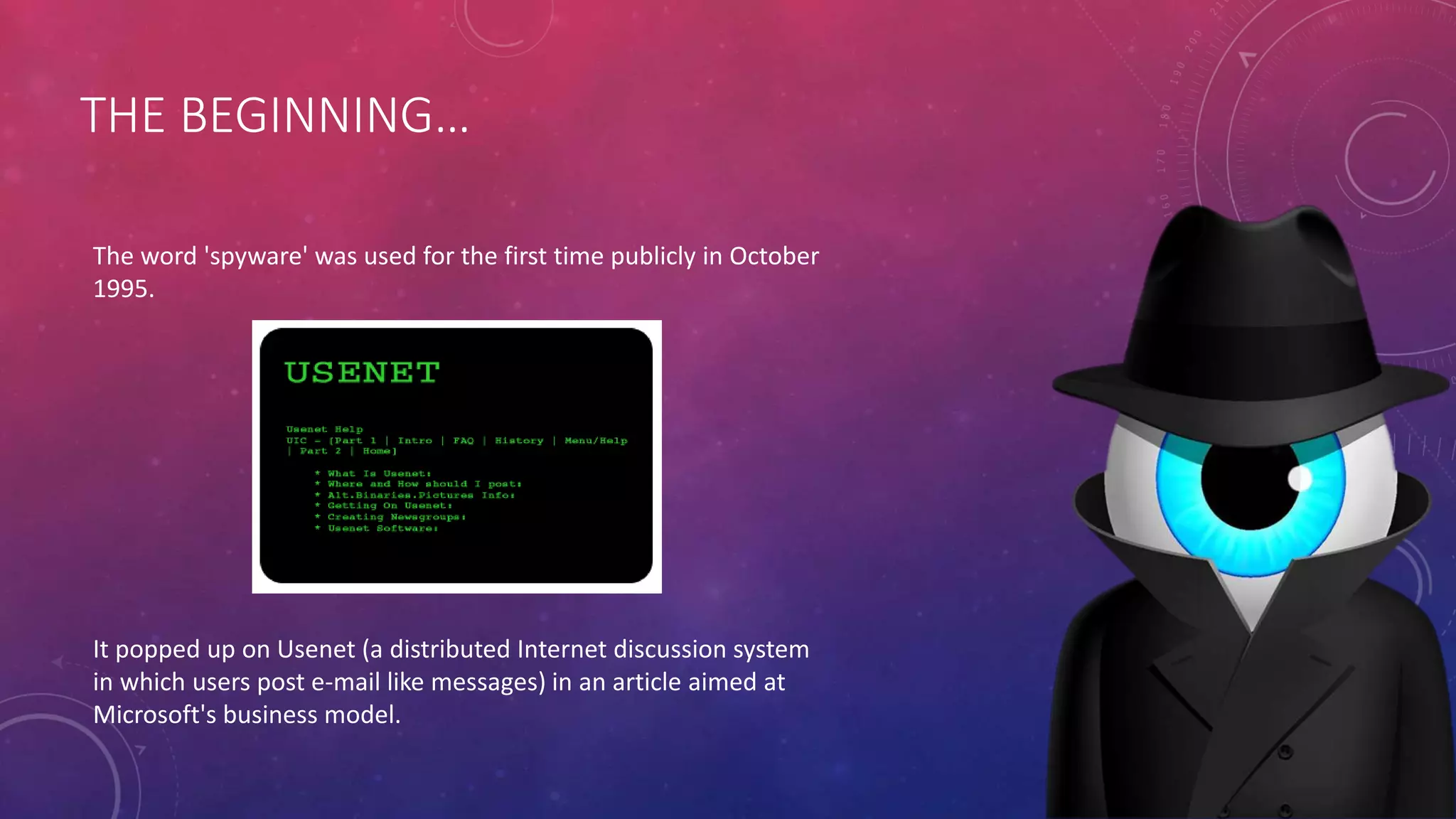
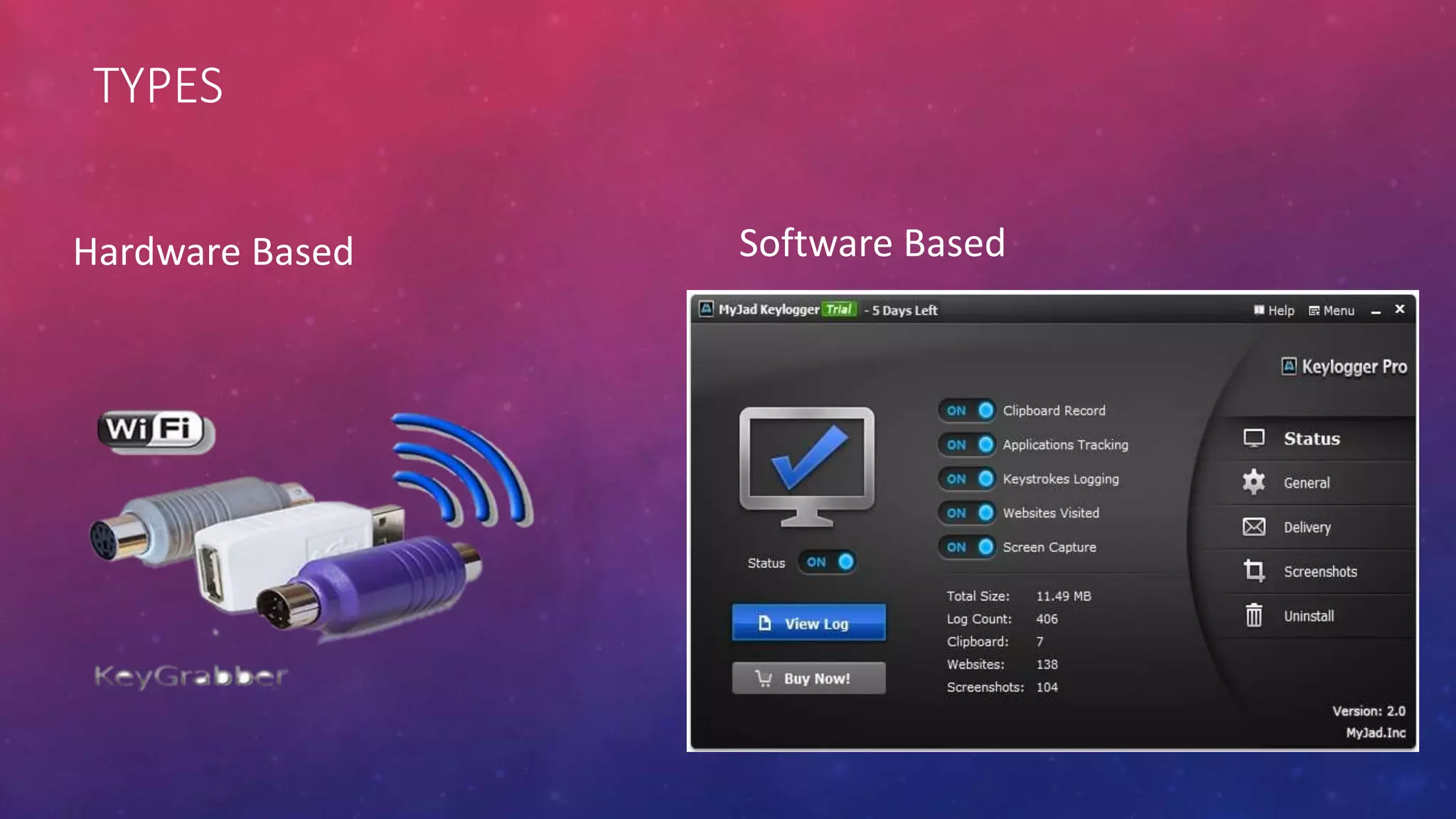
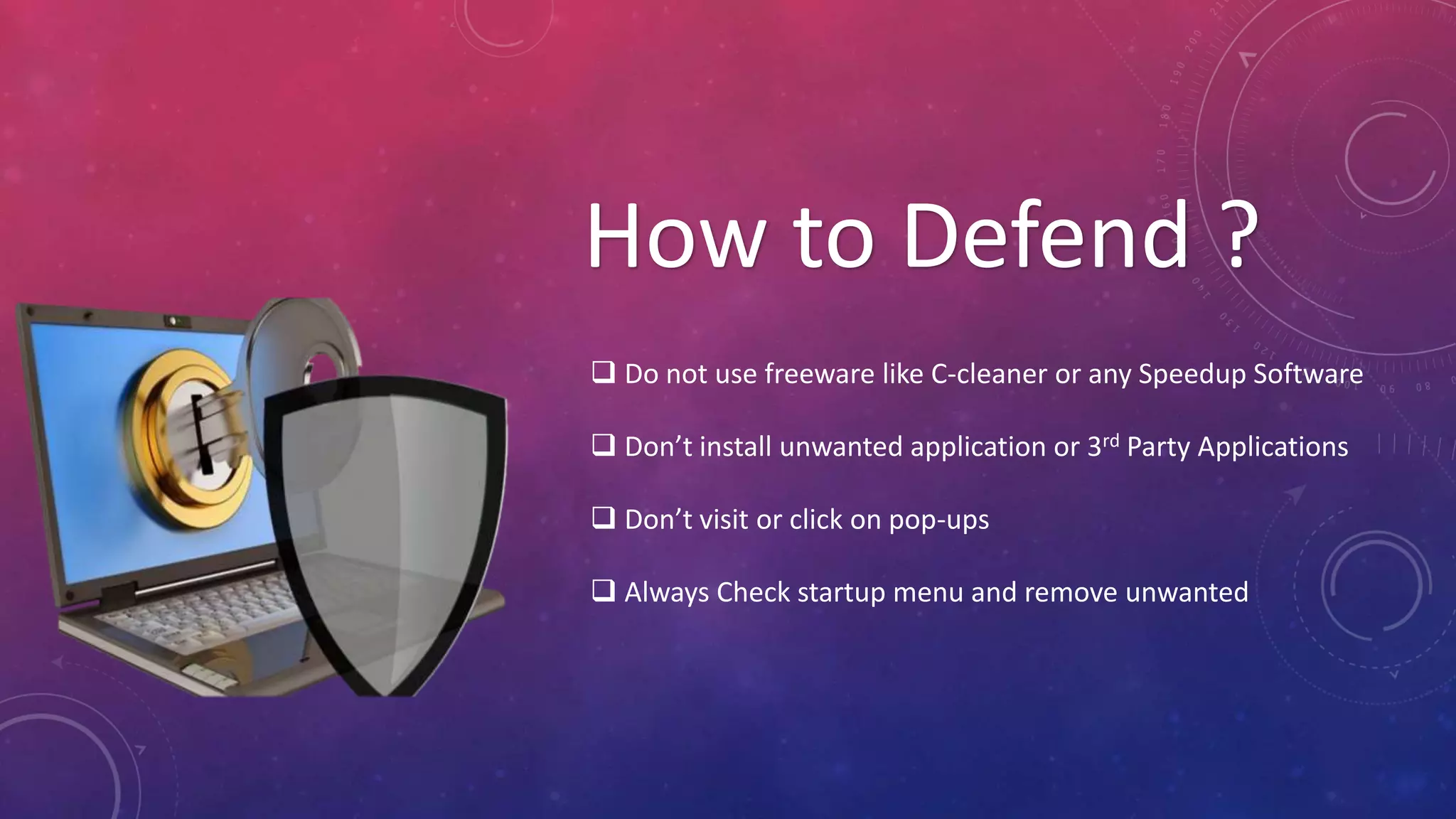
This document summarizes information about spyware and keyloggers. It begins with an agenda that outlines topics to be covered, including definitions of spyware and keyloggers, types of each, examples and uses, and how to detect and defend against them. The document then defines spyware as software used to spy on computer users without their knowledge, typically to track internet usage and serve pop-up ads. It notes that the term "spyware" was first used publicly in 1995. Methods for detecting spyware like increased loading times and unwanted pop-ups are listed. Both advantages and disadvantages of spyware are mentioned. Keyloggers are defined as hardware-based or software-based tools for logging keyboard inputs. Specific keylogger examples and