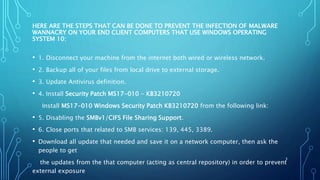
The document provides technical guidance to prevent the WannaCry ransomware attack, outlining essential steps for protecting Windows operating system clients. Key preventive actions include disconnecting from the internet, backing up files, updating antivirus definitions, installing the MS17-010 security patch, disabling SMBv1/CIFS file sharing, and blocking specific ports using Windows Firewall. Detailed instructions for downloading security patches, updating antivirus software, and configuring firewall settings are also included.