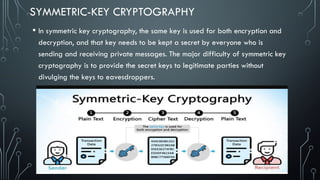
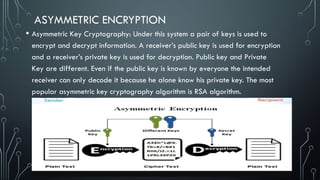
Quantum networking is an emerging field that combines quantum mechanics with networking technology to facilitate secure communication and computation. Key components include qubits, quantum processors, and entangled states, which are essential for applications such as secure quantum key distribution and quantum teleportation. While promising increased efficiencies and computing power, challenges such as the fragile nature of quantum information and high costs remain barriers to commercial viability.