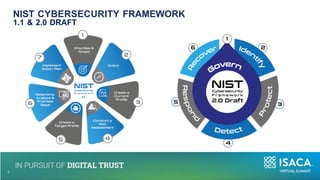
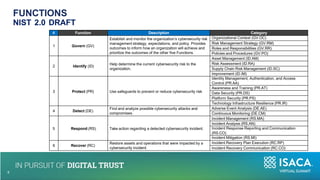
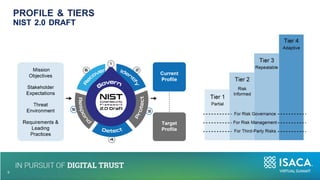
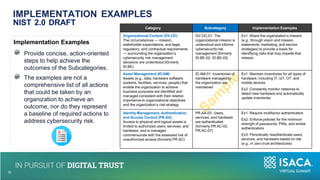
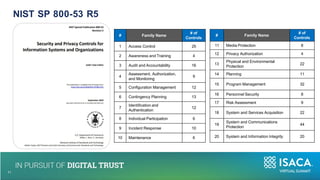
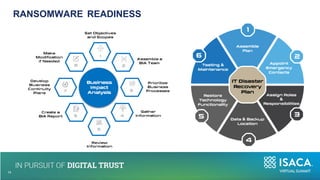
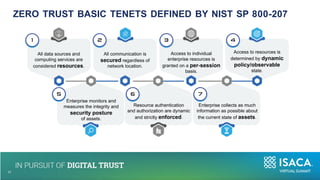
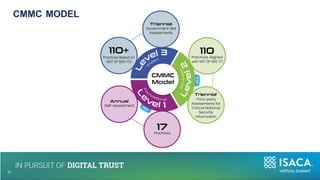
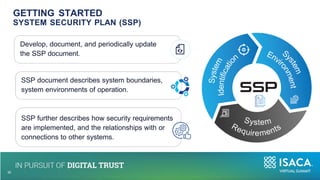
The document discusses the importance of NIST standards, particularly NIST SP 800-171R3, and the Cybersecurity Maturity Model Certification (CMMC) in mitigating cybersecurity risks, especially in critical infrastructure and supply chains. It outlines the evolving landscape of cyber and biological threats, emphasizing the need for organizations, notably in healthcare, to enhance their cyber defenses. Furthermore, it highlights new trends in medical technology and provides detailed guidance on implementing NIST frameworks to improve cybersecurity practices.