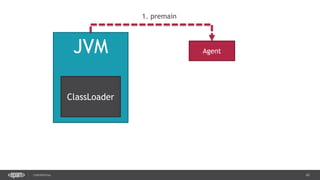
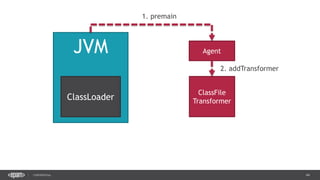
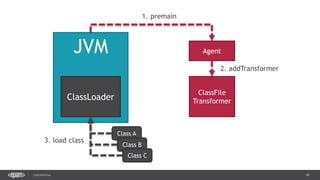
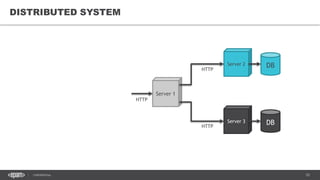
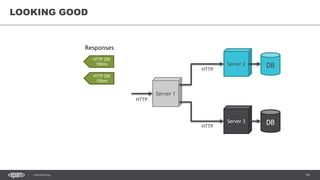
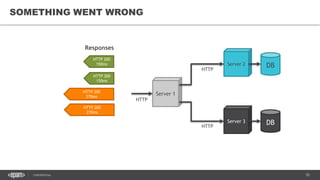
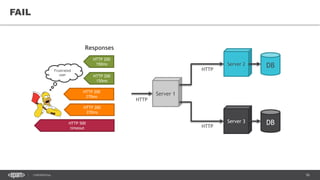
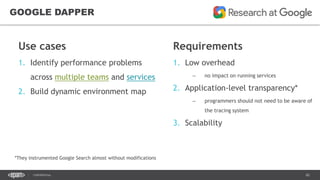
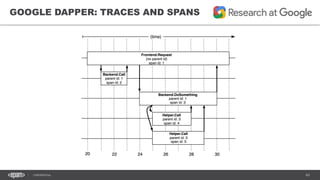
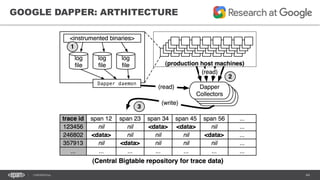
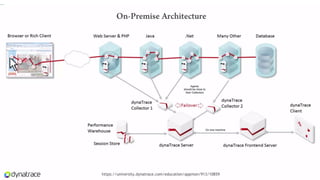
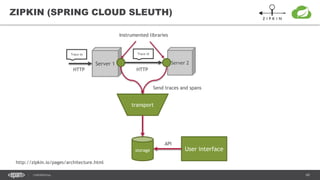
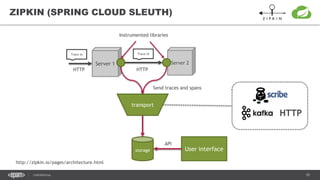
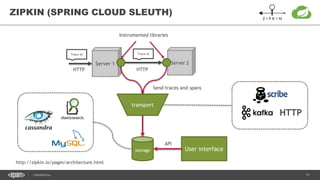
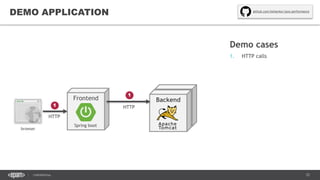
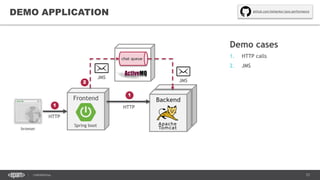
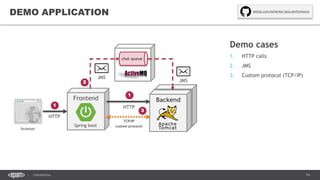
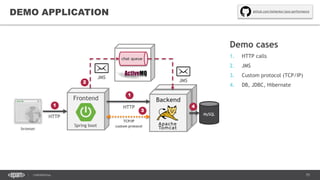
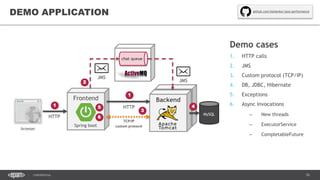
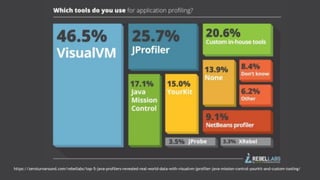
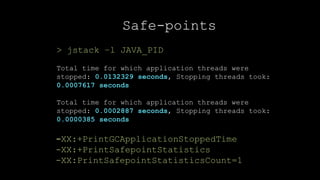
The document outlines techniques and tools for profiling Java applications, focusing on both single JVM and distributed systems. It discusses the importance of accurately measuring application performance, various Java profiling methodologies, and frameworks such as Google Dapper for performance tracing across systems. The presentation includes live demos and examples of profiling tools, Java agents, and instrumentation methods to improve performance diagnostics.








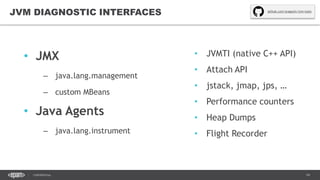
![16CONFIDENTIAL
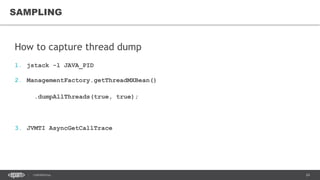
ThreadMXBean threadMBean =
ManagementFactory.getThreadMXBean();
System.out.println("Thread count = " +
threadMBean.getThreadCount());
ThreadInfo[] threads = threadMBean
.dumpAllThreads(true, true);
for (ThreadInfo thread : threads) {
System.out.println(thread);
}](https://image.slidesharecdn.com/profilingdistributedjavaapps-170526112108/85/Profiling-distributed-Java-applications-16-320.jpg)
![17CONFIDENTIAL
ThreadMXBean threadMBean =
ManagementFactory.getThreadMXBean();
System.out.println("Thread count = " +
threadMBean.getThreadCount());
ThreadInfo[] threads = threadMBean
.dumpAllThreads(true, true);
for (ThreadInfo thread : threads) {
System.out.println(thread);
}](https://image.slidesharecdn.com/profilingdistributedjavaapps-170526112108/85/Profiling-distributed-Java-applications-17-320.jpg)
![18CONFIDENTIAL
ThreadMXBean threadMBean =
ManagementFactory.getThreadMXBean();
System.out.println("Thread count = " +
threadMBean.getThreadCount());
ThreadInfo[] threads = threadMBean
.dumpAllThreads(true, true);
for (ThreadInfo thread : threads) {
System.out.println(thread);
}](https://image.slidesharecdn.com/profilingdistributedjavaapps-170526112108/85/Profiling-distributed-Java-applications-18-320.jpg)
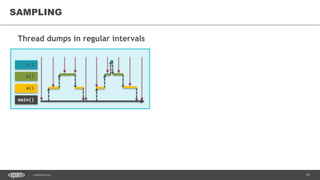
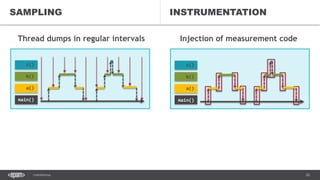


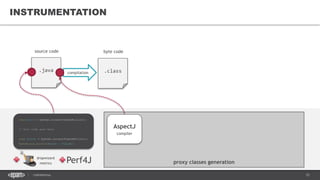
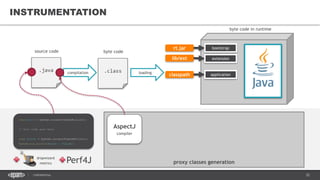
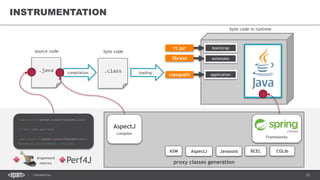
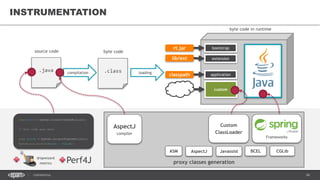
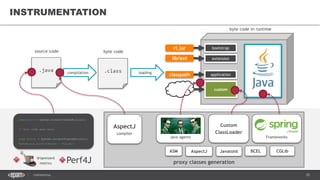

![37CONFIDENTIAL
AGENT EXAMPLES
HPROF Java profiler
JDWP Java debugger
JRebel/XRebel
• https://zeroturnaround.com/software/jrebel/
-agentlib:hprof[=options] ToBeProfiledClass
-agentlib:jdwp=transport=dt_socket,address=localhost:9009,server=y,suspend=y](https://image.slidesharecdn.com/profilingdistributedjavaapps-170526112108/85/Profiling-distributed-Java-applications-37-320.jpg)
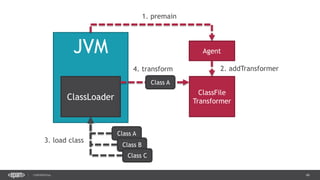
![38CONFIDENTIAL
public class DemoAgent() {
public static void premain(String args, Instrumentation instr) {
instr.addTransformer(new ClassLoadingLogger());
}
}
public class ClassLoadingLogger implements ClassFileTransformer {
public byte[] transform(ClassLoader loader, String className,
Class<?> classBeingRedefined, ProtectionDomain protectionDomain,
byte[] classfileBuffer) throws IllegalClassFormatException {
System.out.println(className);
return classfileBuffer;
}
}
Manifest-Version: 1.0
Agent-Class: com.example.DemoAgent
Premain-Class: com.example.DemoAgent
> java –jar –agentlib:agent.jar app.jar](https://image.slidesharecdn.com/profilingdistributedjavaapps-170526112108/85/Profiling-distributed-Java-applications-38-320.jpg)
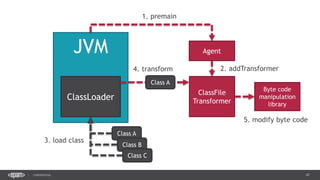
![39CONFIDENTIAL
public class DemoAgent() {
public static void premain(String args, Instrumentation instr) {
instr.addTransformer(new ClassLoadingLogger());
}
}
public class ClassLoadingLogger implements ClassFileTransformer {
public byte[] transform(ClassLoader loader, String className,
Class<?> classBeingRedefined, ProtectionDomain protectionDomain,
byte[] classfileBuffer) throws IllegalClassFormatException {
System.out.println(className);
return classfileBuffer;
}
}
Manifest-Version: 1.0
Agent-Class: com.example.DemoAgent
Premain-Class: com.example.DemoAgent
> java –jar –agentlib:agent.jar app.jar](https://image.slidesharecdn.com/profilingdistributedjavaapps-170526112108/85/Profiling-distributed-Java-applications-39-320.jpg)
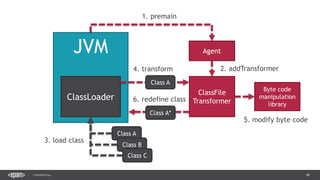
![40CONFIDENTIAL
public class DemoAgent() {
public static void premain(String args, Instrumentation instr) {
instr.addTransformer(new ClassLoadingLogger());
}
}
public class ClassLoadingLogger implements ClassFileTransformer {
public byte[] transform(ClassLoader loader, String className,
Class<?> classBeingRedefined, ProtectionDomain protectionDomain,
byte[] classfileBuffer) throws IllegalClassFormatException {
System.out.println(className);
return classfileBuffer;
}
}
Manifest-Version: 1.0
Agent-Class: com.example.DemoAgent
Premain-Class: com.example.DemoAgent
> java –jar –agentlib:agent.jar app.jar](https://image.slidesharecdn.com/profilingdistributedjavaapps-170526112108/85/Profiling-distributed-Java-applications-40-320.jpg)
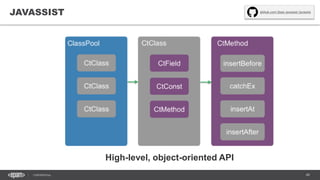
![41CONFIDENTIAL
public class DemoAgent() {
public static void premain(String args, Instrumentation instr) {
instr.addTransformer(new ClassLoadingLogger());
}
}
public class ClassLoadingLogger implements ClassFileTransformer {
public byte[] transform(ClassLoader loader, String className,
Class<?> classBeingRedefined, ProtectionDomain protectionDomain,
byte[] classfileBuffer) throws IllegalClassFormatException {
System.out.println(className);
return classfileBuffer;
}
}
Manifest-Version: 1.0
Agent-Class: com.example.DemoAgent
Premain-Class: com.example.DemoAgent
> java –jar –agentlib:agent.jar app.jar](https://image.slidesharecdn.com/profilingdistributedjavaapps-170526112108/85/Profiling-distributed-Java-applications-41-320.jpg)