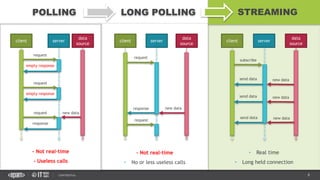
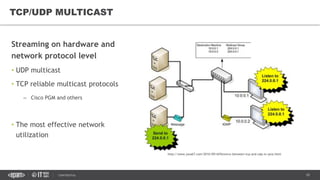
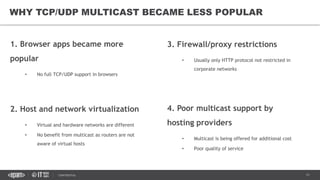
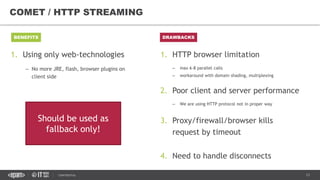
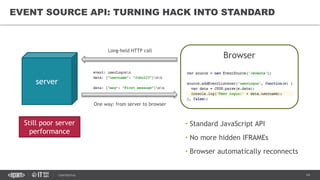
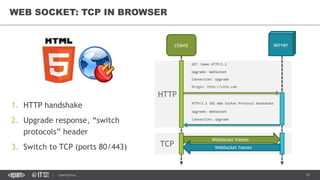
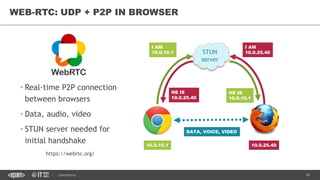
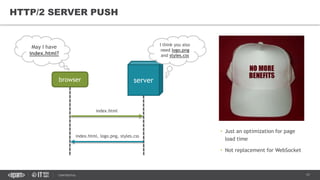
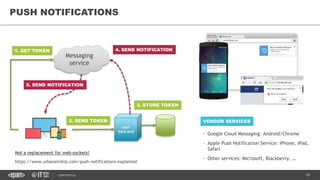
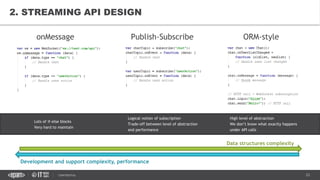
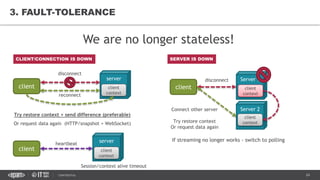
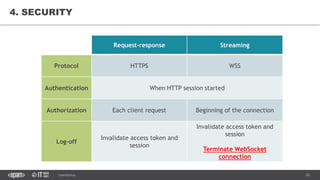
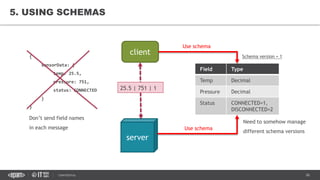
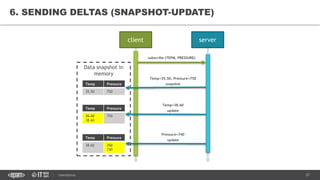
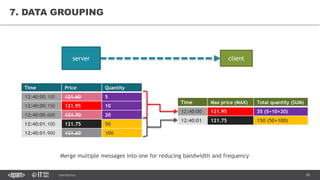
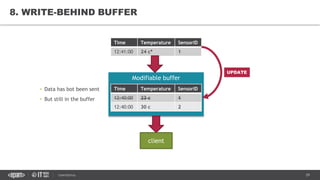
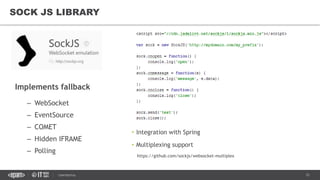
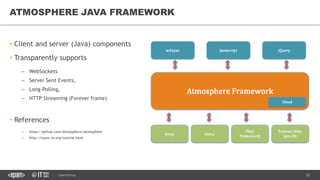
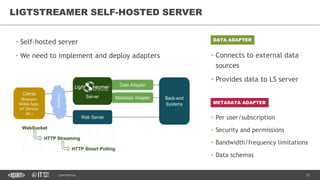
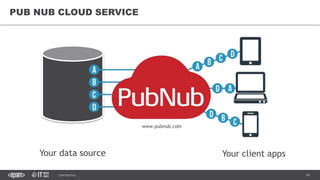
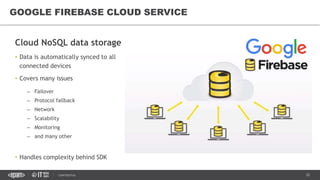
This document provides an overview of best practices for building data streaming APIs. It discusses various techniques for implementing streaming such as TCP/UDP multicast, HTTP streaming, WebSocket, and push notifications. It also covers challenges like protocol fallback, API design, fault tolerance, security, and data optimization. Finally, it lists several streaming libraries, tools and cloud services that can be used to build streaming applications and APIs.