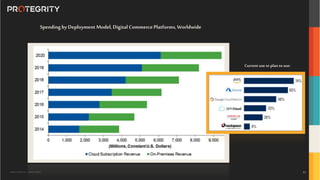
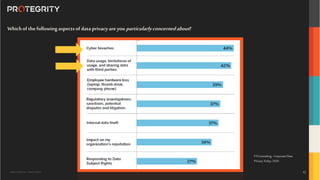
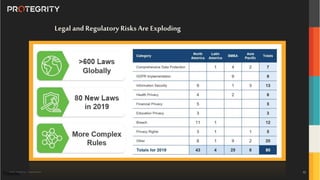
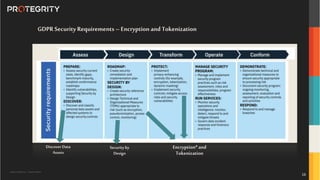
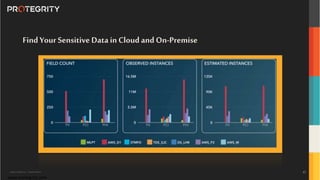
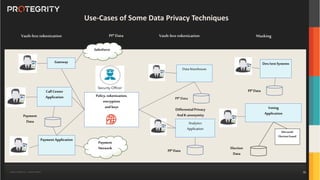
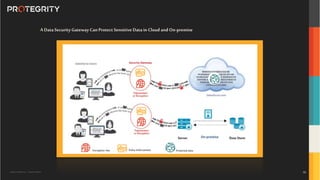
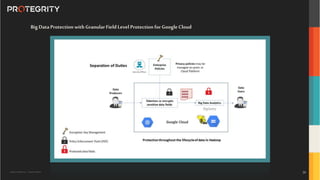
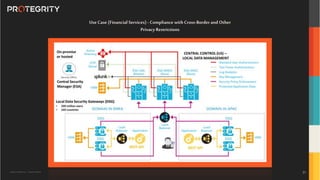
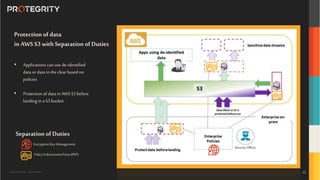
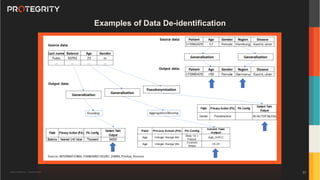
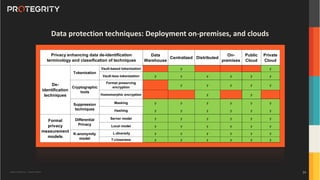
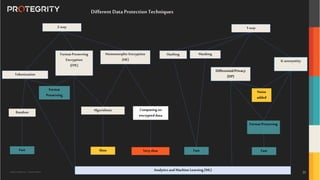
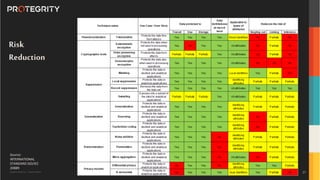
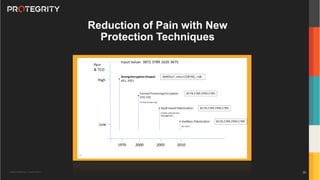
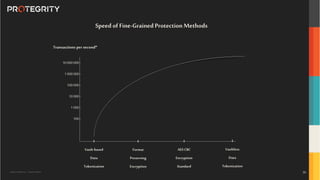
The document outlines the expertise of Ulf Mattsson, Chief Security Strategist at Protegrity, and discusses various data security solutions including encryption and tokenization. It highlights the importance of compliance with regulations such as GDPR and CCPA while addressing risks related to data breaches and legal issues that businesses face. Additionally, it covers data protection techniques, cloud security considerations, and emerging privacy standards in managing sensitive information.