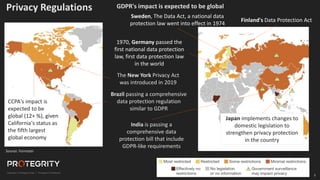
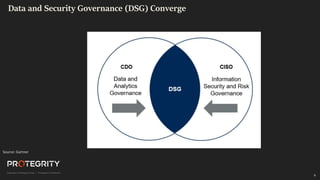
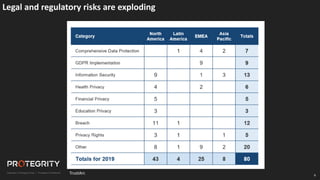
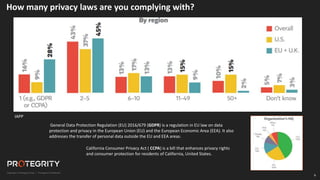
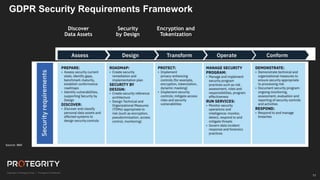
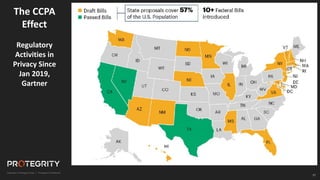
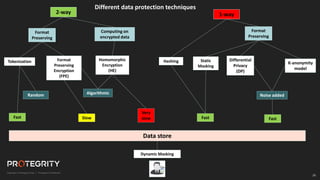
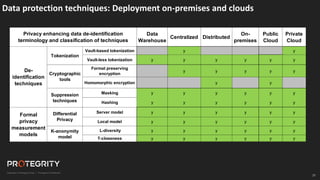
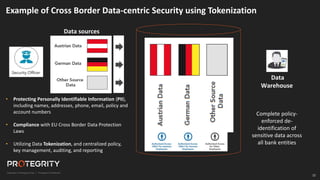
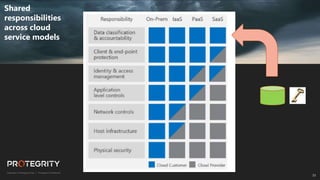
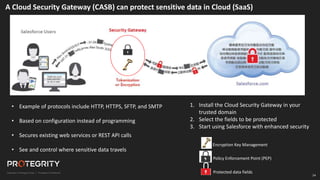
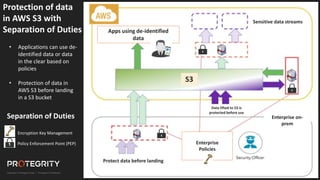
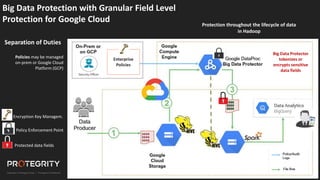
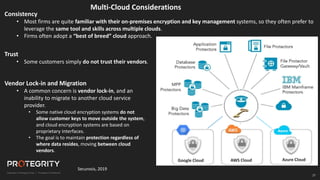
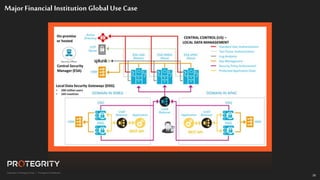
The document discusses evolving international privacy regulations, focusing on the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA). It notes that many countries are passing new privacy laws influenced by GDPR. Technologies like data tokenization, encryption, and anonymization play an important role in complying with these regulations by protecting personal data throughout its lifecycle. The document provides examples of how technologies can be deployed across on-premises and cloud environments to ensure consistent privacy protection of data.