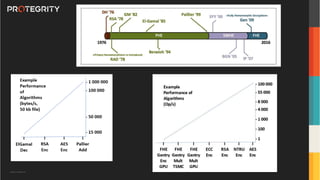
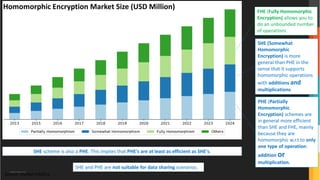
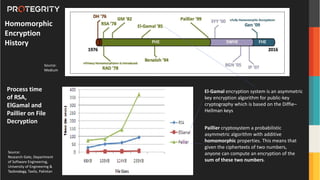
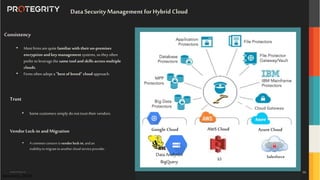
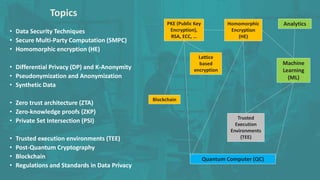
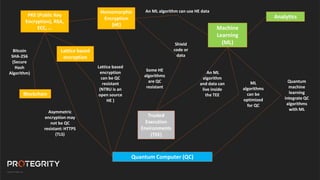
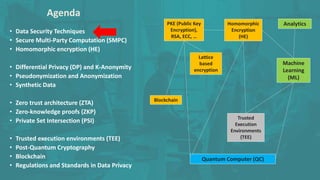
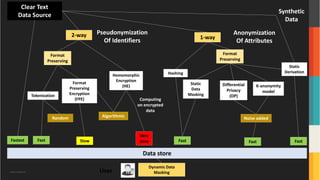
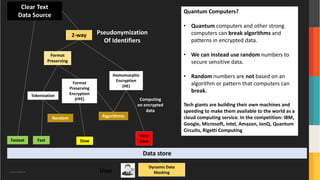
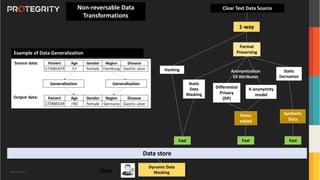
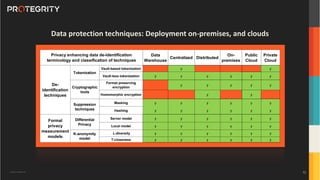
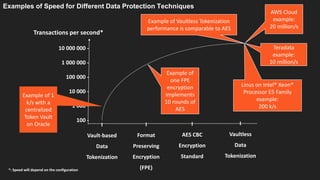
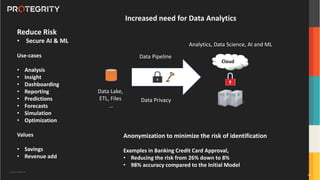
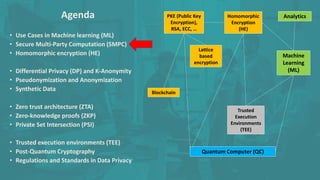
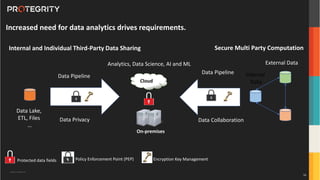
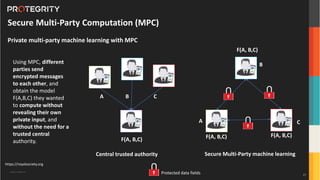
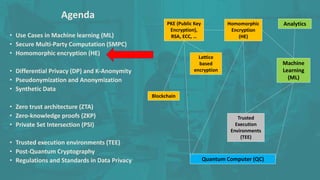
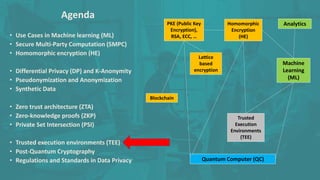
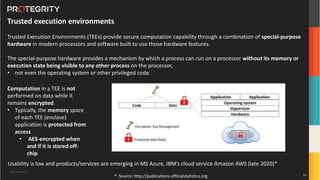
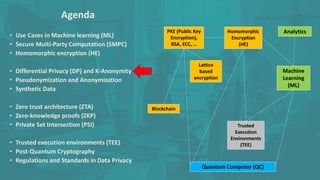
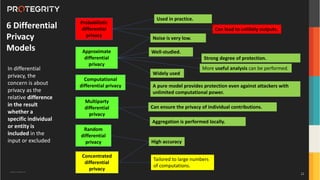
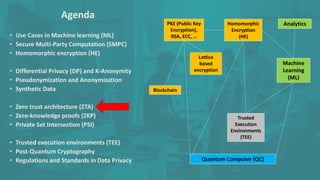
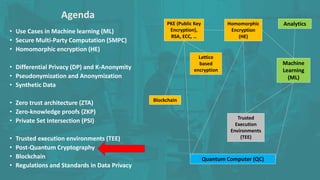
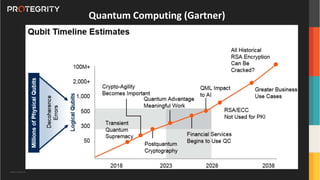
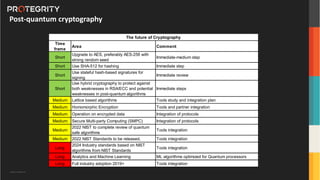
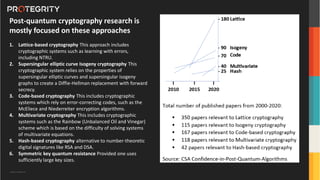
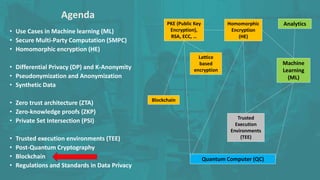
The document discusses advanced data security technologies, including post-quantum cryptography, secure multi-party computation, and homomorphic encryption. It highlights the significance of data privacy techniques such as differential privacy and zero trust architecture in the context of machine learning and blockchain applications. Additionally, it addresses the emerging need for quantum-resistant encryption methods and compliance with international regulations in data privacy.









![Copyright ©Protegrity Corp.
If there is a Picasso’s painting valued at $50
million, it can be tokenized.
• The same applies to gold and
diamonds.
Company stocks are more complicated
because in most jurisdictions it is
prohibited to sell fractional parts of
company shares.
• Bankex — “Bankex provides the universal solution which can transform different asset classes to a digital
system/field/economy/area providing it with liquidity, flexibility, and safety for asset owners and investors
like never before”
• Maecenas — “Maecenas is a new online marketplace promises to give art lovers the chance to buy shares
in famous paintings.[The Telegraph]”
• LaToken — “LATOKEN’s mission is to make capital markets and trading available 24/7 T+0, with a broader
range of asset classes. We aim to facilitate capital reallocation into promising businesses, which will foster
job creation with higher productivity.”
Transform different asset classes](https://image.slidesharecdn.com/thefutureofdatasecurityandblockchain-210426075348/85/The-future-of-data-security-and-blockchain-44-320.jpg)