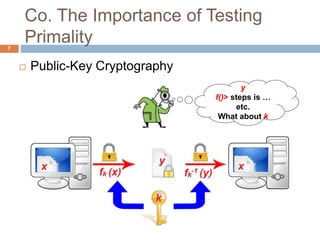
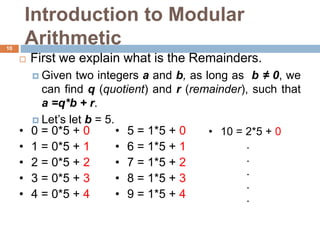
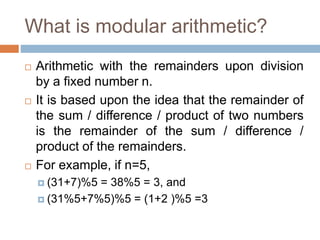
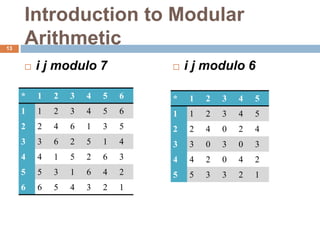
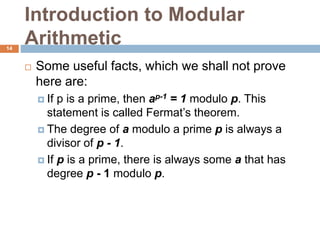
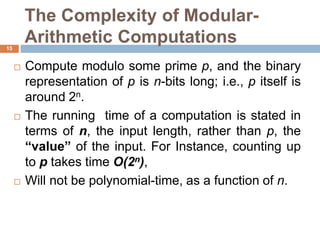
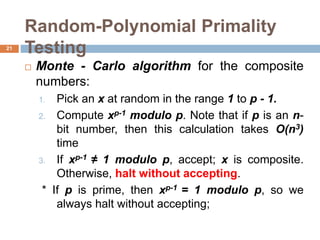
This document discusses the complexity of primality testing. It begins by explaining what prime and composite numbers are, and why primality testing is important for applications like public-key cryptography that rely on the assumption that factoring large composite numbers is computationally difficult. It then covers algorithms for primality testing like the Monte Carlo algorithm and discusses their runtime complexities. It shows that while testing if a number is composite can be done in polynomial time, general number factoring is believed to require exponential time, making primality testing an important problem.