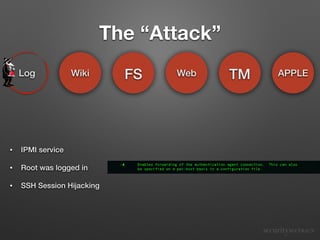
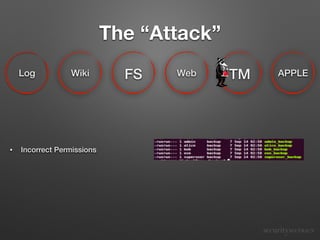
The document describes a "candy shell" security assessment performed by CandyShell Security on an example infrastructure. It identifies numerous common security problems found in the target infrastructure such as privileged accounts, weak passwords, lack of logging and monitoring. It then details how an attacker could potentially compromise various systems by exploiting these issues and gain escalating levels of access. Finally, it discusses some high-level solutions that could help strengthen security.