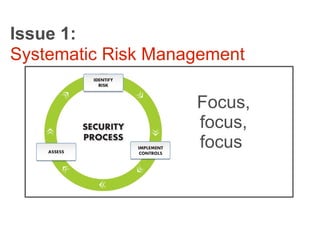
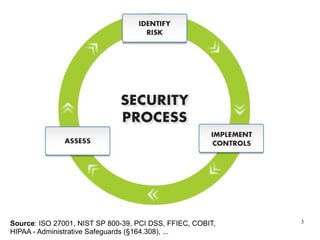
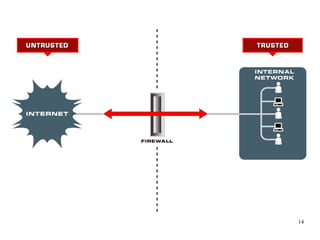
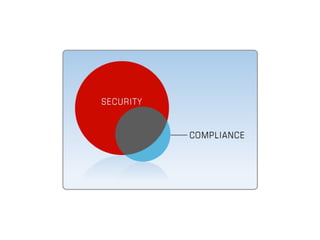
The document outlines the top IT security risks for financial institutions in 2011, highlighting issues such as mobile devices, wireless security, social media risks, and vendor management. It emphasizes the importance of systematic risk management and cites examples of recent breaches to illustrate vulnerabilities. Additionally, it stresses the need for robust mobile device security policies and effective testing programs.