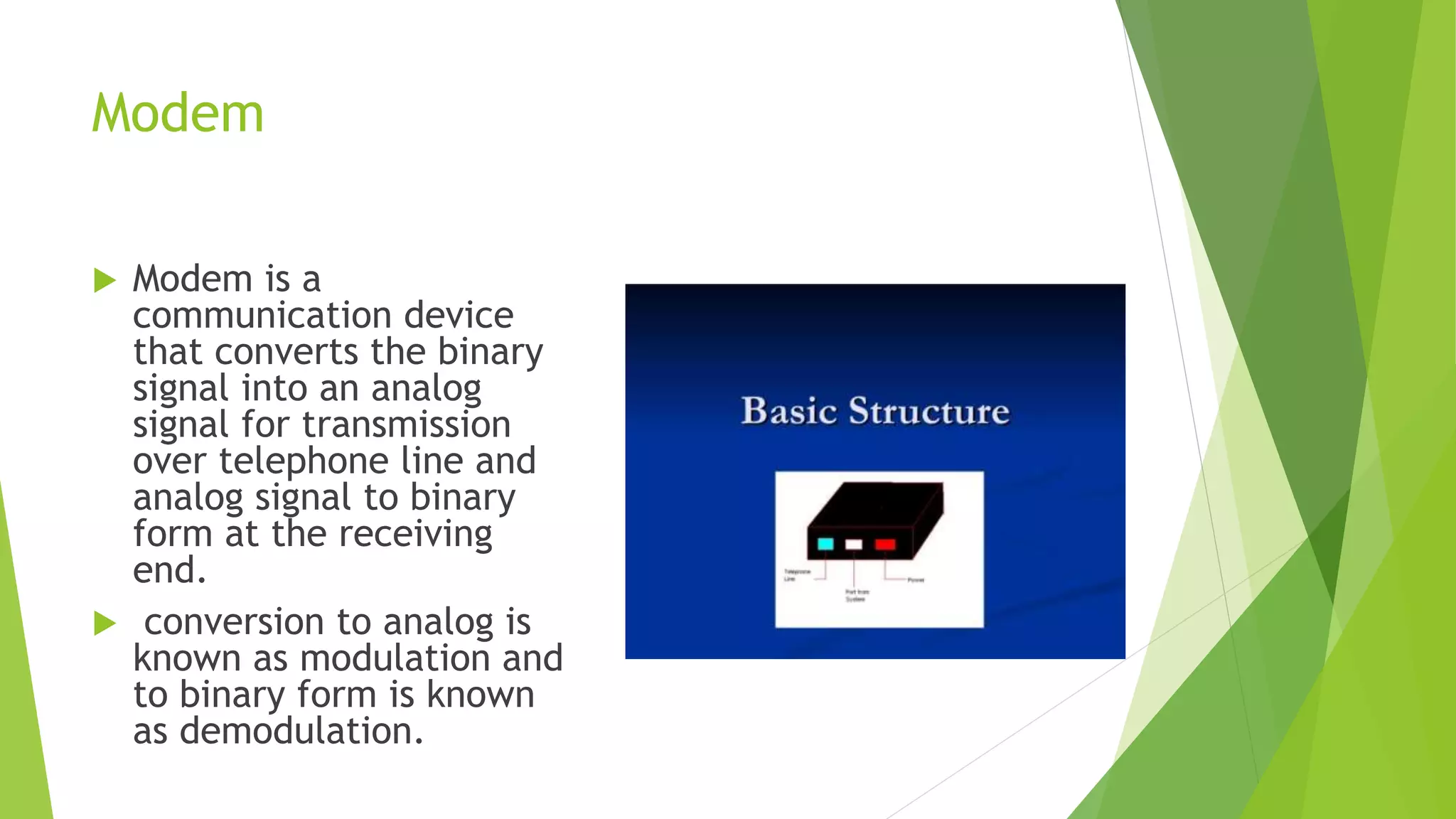
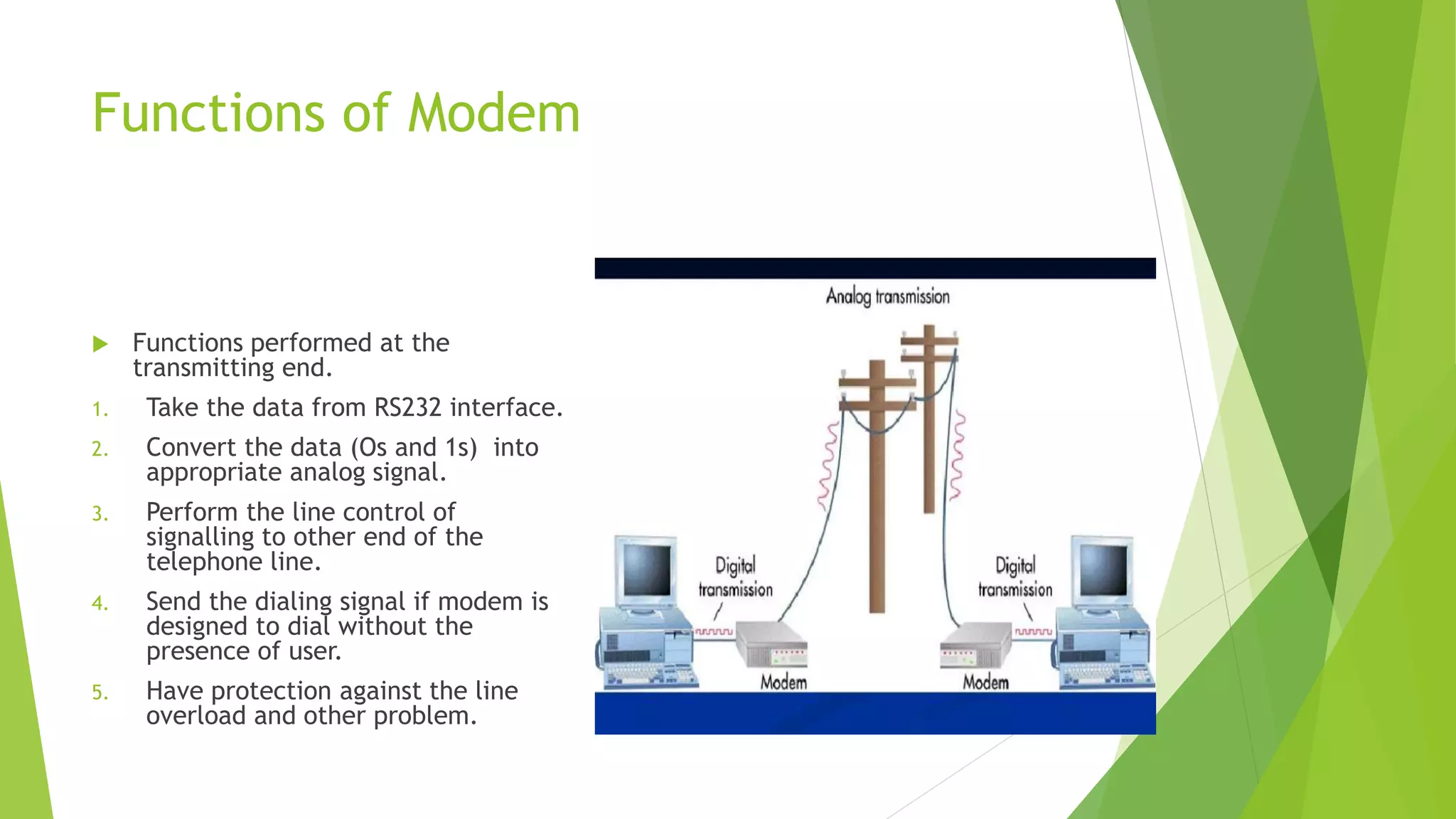
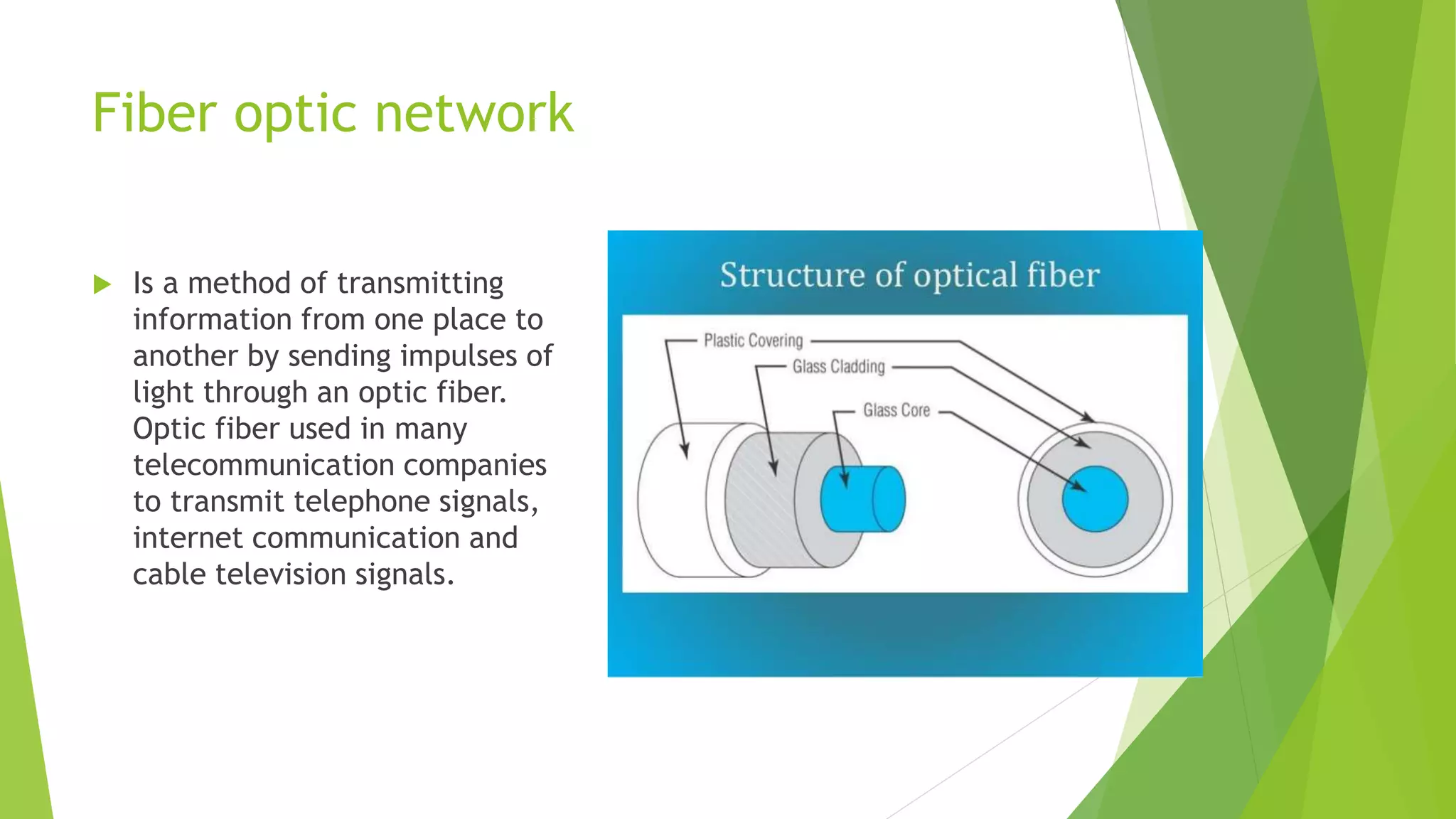
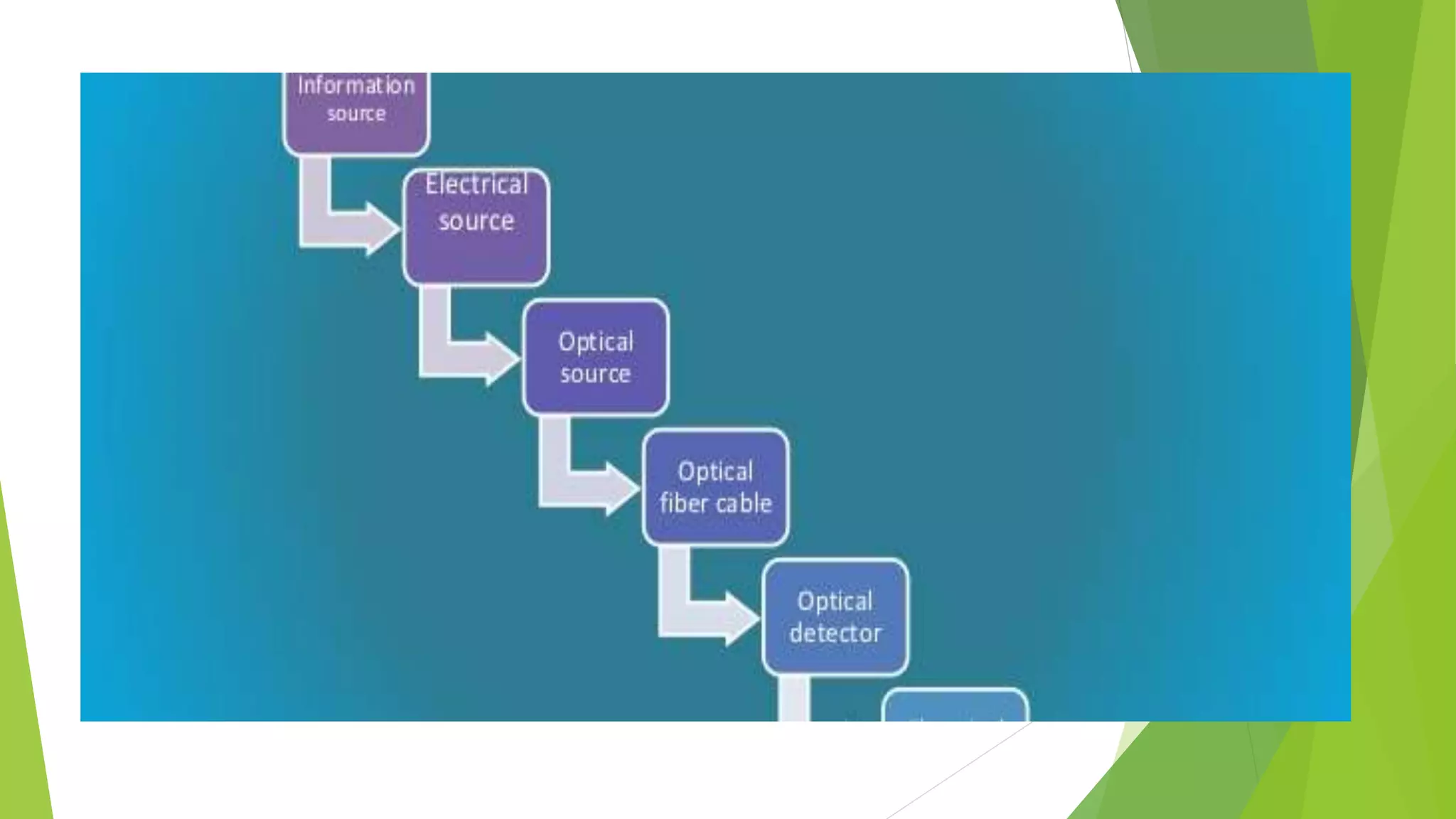
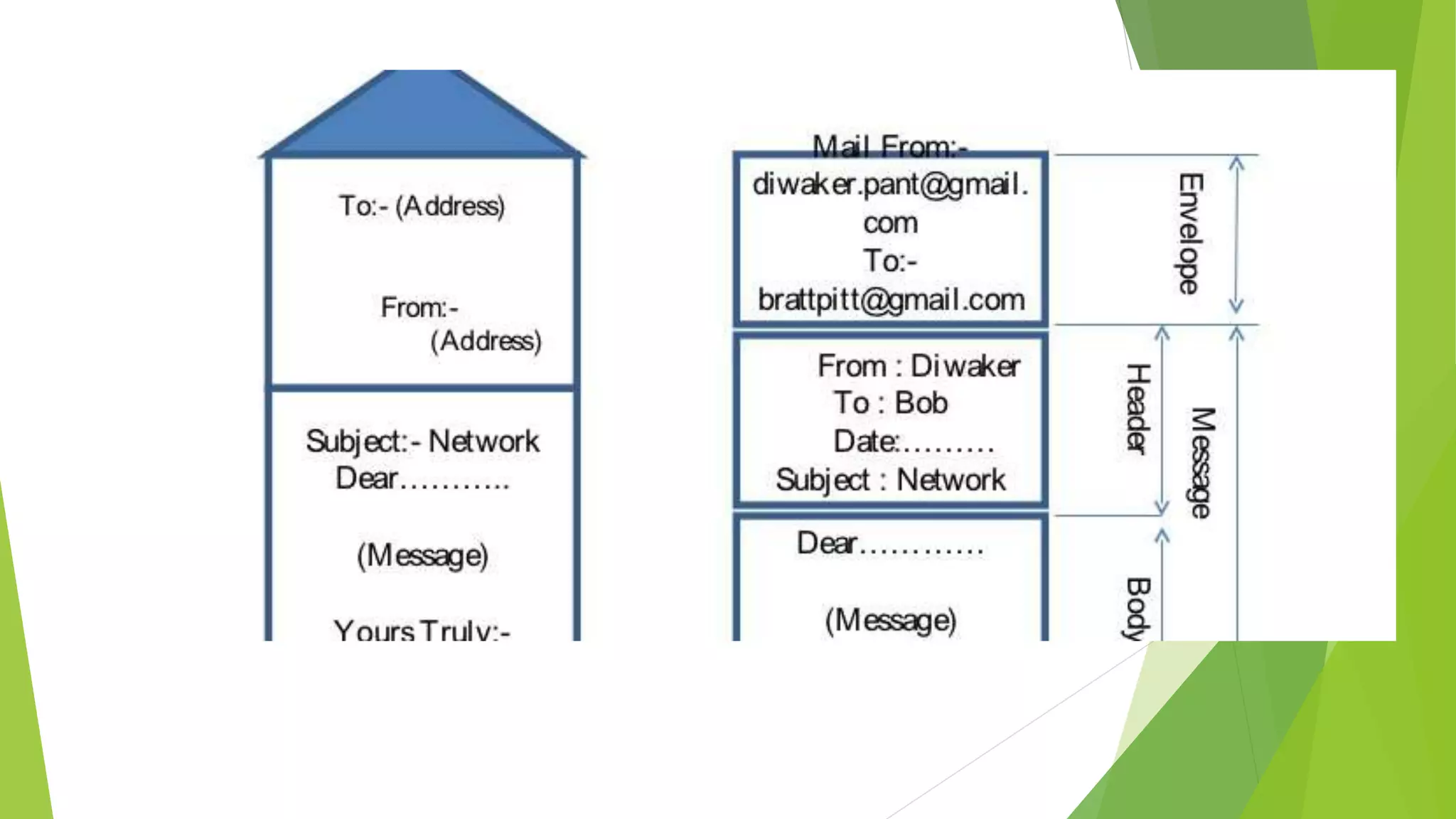
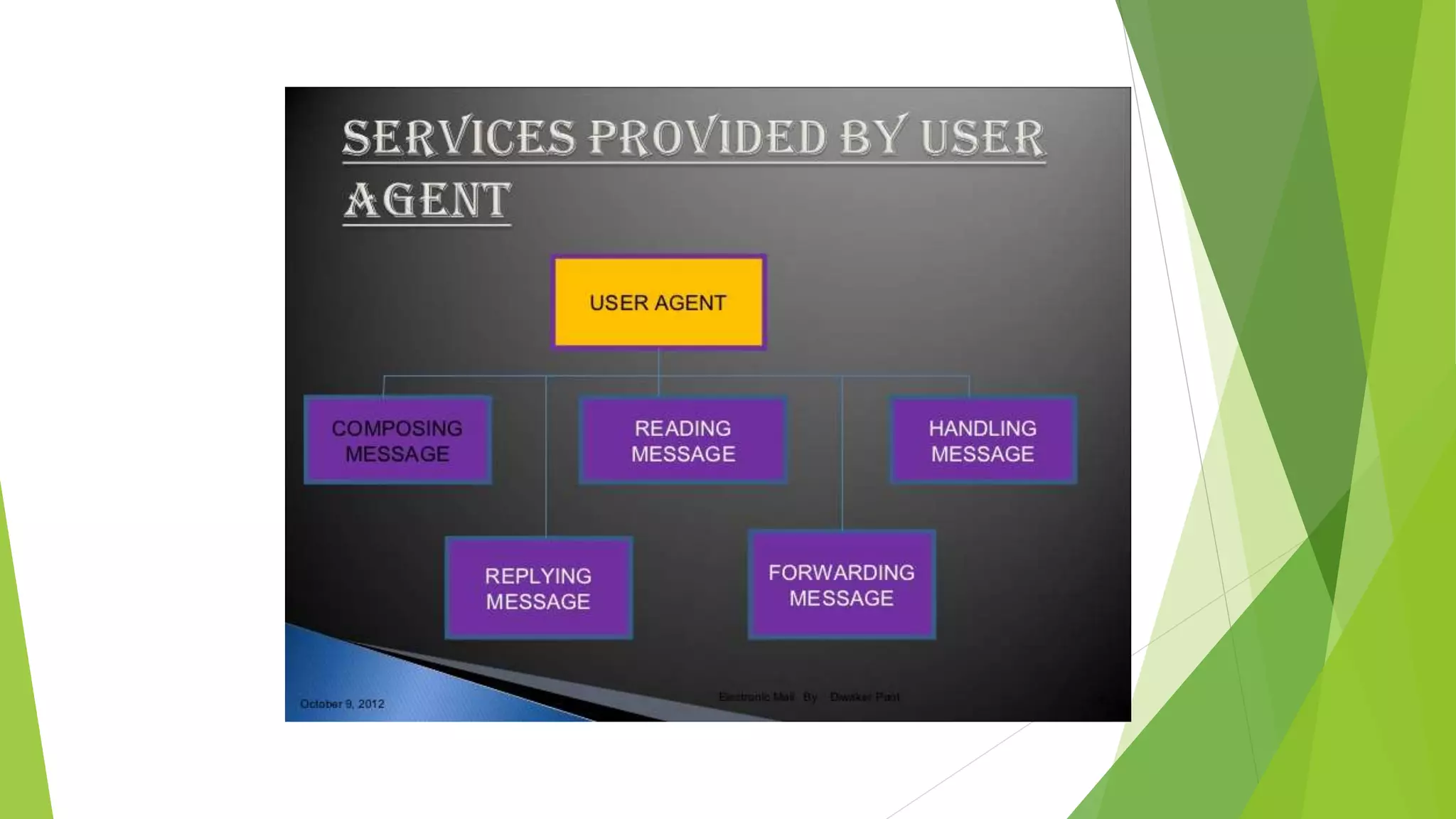
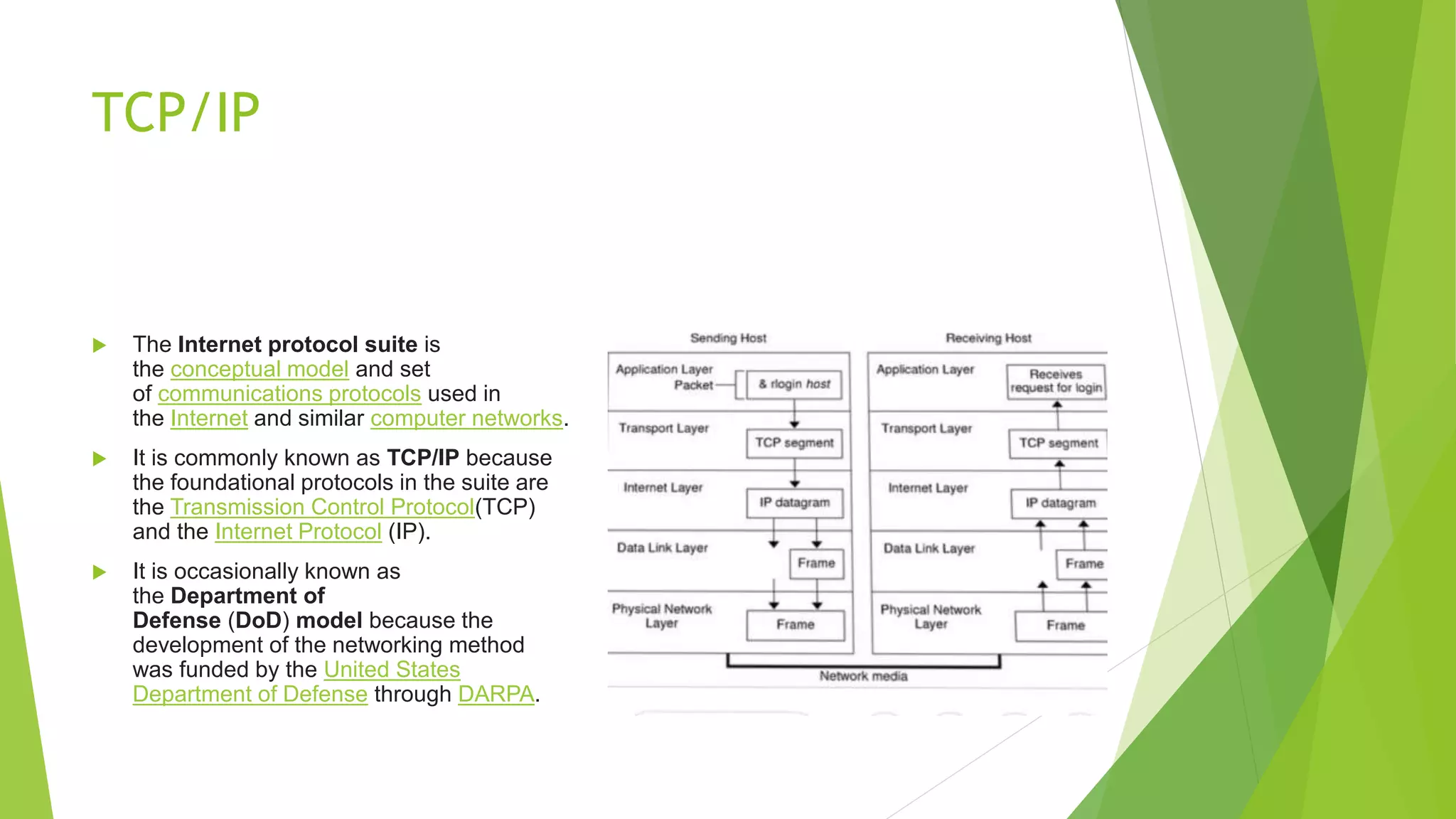
Modems convert digital signals to analog signals for transmission over phone lines and vice versa. They are classified by connection type and transmission mode. Functions include data compression, error correction, and flow control. TCP/IP is the standard communication protocol for the Internet and networks. It has application, transport, internet, and link layers. The World Wide Web is a system of interlinked hypertext documents accessed via the Internet using browsers. It allows information sharing through URLs and hyperlinks.